Our lives are now intrinsically entangled with mobile apps. Mobile app pentesting tools ensure that these apps are secure and protected against cyber threats. It employs white-hat hacking methods to sift through mobile applications, hunting for weak spots and security lapses that could become targets for malicious hackers.
The importance of mobile application pentesting tools is multi-layered – it’s about securing user data, preserving the app’s integrity, and defending the reputation of businesses that could potentially suffer huge blows from security breaches.
6 Best Mobile App Penetration Testing Software
- Astra Security
- ZAP (Zed Attack Proxy)
- Burp Suite
- Mobile Security Framework (MobSF)
- Kali Linux NetHunter
- Data Theorem
The Best Mobile Pentesting Tools
1. Astra Security
Astra Security is your go-to cybersecurity platform when you need a wide-ranging, efficient, and result-oriented vulnerability assessment and penetration testing (VAPT) solution for your mobile apps. It’s one of the major mobile app pentesting tools providing a two-in-one deal that blends the speed of automation with the meticulousness of manual testing for thorough security audits and compliance checks.
Peeking at its key features, you can see that Astra Security has its net cast wide. From web and mobile applications to cloud configurations and even APIs, it offers extensive security coverage. Its VAPT approach employs both manual and automated techniques, examining more than 8000 vulnerabilities.
Astra Security prides itself on a no-nonsense approach with zero false positives. This means you can trust the results it churns out. And if you’re concerned about staying in line with regulations such as HIPAA, SOC2, PCI-DSS, ISO 27001, or GDPR, Astra’s got you covered. Its VAPT contributes to maintaining compliance, which is a big win.
What about integrating with your tech stack? Well, Astra does that too. It offers an integration that’s so smooth you’d hardly know it’s there. And its user-friendly features, like a collaborative dashboard, make it even easier to use. Plus, you get real-time expert support, which means you’re never left hanging if you hit a snag.
So, in a nutshell, Astra Security is a reliable choice for businesses that value accurate vulnerability assessments and compliance. Its user-friendly nature and prompt support make it even more appealing. And did we mention the zero false positives? Now that’s what we call a confidence booster!
Cons:
- Might be expensive
2. ZAP (Zed Attack Proxy)

Next, we have ZAP, also known as the Zed Attack Proxy. ZAP hails from the stables of OWASP. It’s not only free and open-source but also hailed as one of the most widely used mobile app pentesting tools for web applications, inclusive of mobile apps.
ZAP packs a punch with its array of features and simplicity of use. And did we mention its bustling community? It has one of the best communities amongst the other mobile application pentesting tools.
Under the hood, ZAP is armed with an automated scanner. While this doesn’t mean you can ditch manual testing, it does quicken the testing process and zooms in on potential vulnerabilities. It’s like a helper bot pointing out where you need to focus.
ZAP also doubles up as a man-in-the-middle proxy. This lets it keep an eye on the back-and-forth between your browser and the application you’re testing, even letting it tweak requests and responses as needed.
For those with specific needs, ZAP offers scripting capabilities in various languages. This means you can tailor your tests to your unique requirements.
Pros:
- Scripting capabilities in various languages
- Best community support
- It is free to use for everybody
Cons:
- Can be weigh down resources during extensive scans
3. Burp Suite
Stepping into the sphere of web and mobile app pentesting tools, Burp Suite positions itself as an invaluable resource. Brought into existence by PortSwigger, it unfurls an expansive feature set focused on security testing. Paralleling ZAP, it functions as a proxy server, giving testers the power to investigate and amend the data exchange between the browser and the chosen application.
Turning our gaze to its key offerings, the Intercepting Proxy stands out as one of the best mobile app pentesting tools. It equips you with the ability to delve into and adjust the data stream between your browser and the application. This mobile app pentesting tools, paves the way for gaining deep insights into the application’s functionality and the nature of the data it transmits and collects.
In the lineup is also the Automated Scanning feature. The Burp Scanner is engineered to work in tandem with manual methods, featuring automated scanning functionality that identifies various vulnerabilities.
Then we have Intruder. This takes charge of executing automated attacks on web applications. It comes into play for tasks such as identifying identifiers, extracting useful data, and fuzz testing for standard injection attacks.
Another tool is the Repeater. This is utilized to manually alter and reissue individual HTTP and WebSocket messages while also evaluating the responses from the application.
Not to forget the Sequencer. This steps up to examine the quality of randomness in an application’s session tokens or any other significant data points that need to remain unpredictable.
It is highly adaptable nature and design for aiding seasoned testers in manual penetration testing make it shine. This is one of the major mobile app pentesting tools that brings to the table various features that can be deployed separately or collectively to conduct exhaustive tests.
Pros:
- Adaptable and scalable
- Provides deep insights
- Expansive features
Cons:
- Learning curve is slightly steeper than other tools
4. Mobile Security Framework (MobSF)
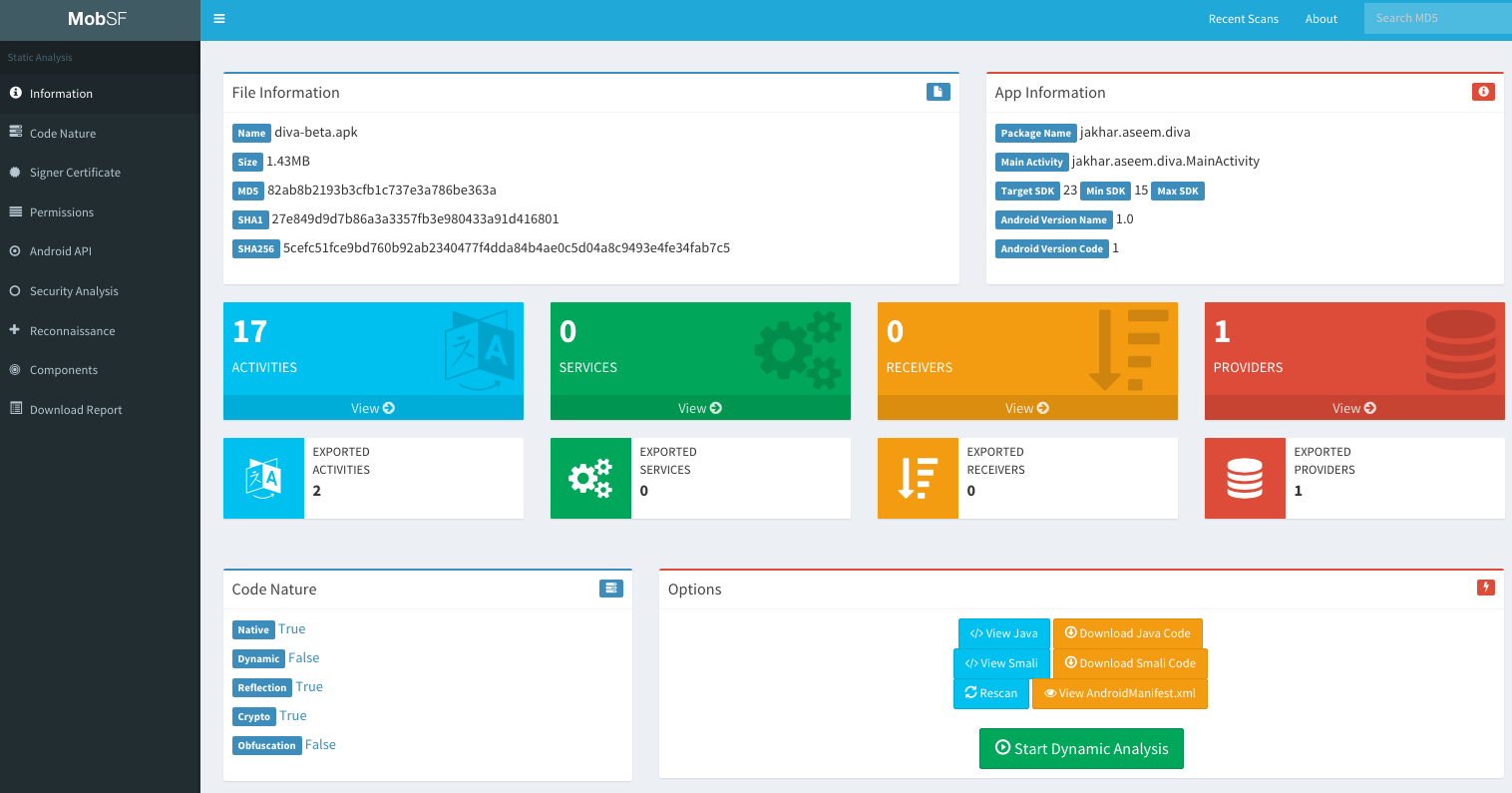
MobSF, short for Mobile Security Framework, emerges as one of the major versatile and automated mobile application pen testing tools dedicated to the realm of mobile penetration testing. This is another major mobile app security testing tool that embrace Android and iOS platforms and is proficient in executing static, dynamic, and malware analysis. As an open-source tool, it promises accessibility and customization opportunities.
On the front lines of mobile app pentesting tools that offers Static Analysis. MobSF flexes its muscle in performing static analysis of Android APK and iOS IPA files. It delves into the code to scout for possible security issues and vulnerabilities in libraries and examines insecure permissions and configurations.
Next in line is Dynamic Analysis. This is one of the mobile app pentesting tools that brings to the table dynamic analysis, also known as runtime analysis, for Android apps. The testing encompasses insecure network communications, file system interactions, and inter-process communications.
Lastly, it is one of the mobile app pentesting tools that is armed with Report Generation. Following the analysis, MobSF puts together a comprehensive report that includes potential security issues and remediation suggestions.
Despite its strengths, MobSF isn’t without limitations. It has garnered widespread praise for its concentrated attention on mobile platforms, automated analysis, and the ease of use. Its ability to conduct both static and dynamic analysis provides a more well-rounded perspective of possible vulnerabilities in mobile apps.
Pros:
- Easy to use
- Conducts both static and dynamic analysis
- Comprehensive reports
Cons:
- Automated analysis is not enough
- Only for Android
5. Kali Linux NetHunter
Kali Linux NetHunter is a public, open-source platform engineered for penetration testing, running on an Android-based operating system. It is one of the mobile app pentesting tools that serves as an enhancement to Kali Linux and can morph a compatible device into an impressive penetration testing instrument, making it apt for mobile apps. The brains behind the well-respected Kali Linux, a Linux distribution heavily relied upon by cybersecurity professionals, also designed and maintain NetHunter.
The key offerings of NetHunter are:
- Comprehensive Kali Linux Toolset: NetHunter brings the might of Kali Linux to your mobile gadget, boasting a wide range of penetration testing tools. These tools span different sectors from data collection to vulnerability examination, exploitation, and follow-up activities.
- 802.11 Wireless Injections: Provided you have the right hardware, NetHunter enables WiFi injections, a crucial feature when testing wireless network vulnerabilities.
- HID Keyboard: NetHunter can mimic a keyboard and mouse, enabling it to carry out attacks recognized as “HID attacks.”
- BadUSB MITM Attacks: Utilizing the USB port, NetHunter can also launch Man-in-the-Middle (MITM) attacks.
- Software Defined Radio Support (SDR): For seasoned users, it delivers SDR support, unlocking avenues for a broad spectrum of intriguing attacks.
NetHunter’s strengths and limitations are equally noteworthy. On one hand, it provides the complete might of Kali Linux tools on a mobile gadget, making it a strong contender for fieldwork. Furthermore, it is one of the mobile app pentesting tools that enables more complex networking attacks, such as MITM and wireless injections.
Pros:
- Enables complex networking attacks
- Adaptable and scalable
- Broad spectrum of intriguing attacks
Cons:
- Is not one of the dedicated mobile app pentesting tools
- Too complex for beginners
6. Data Theorem
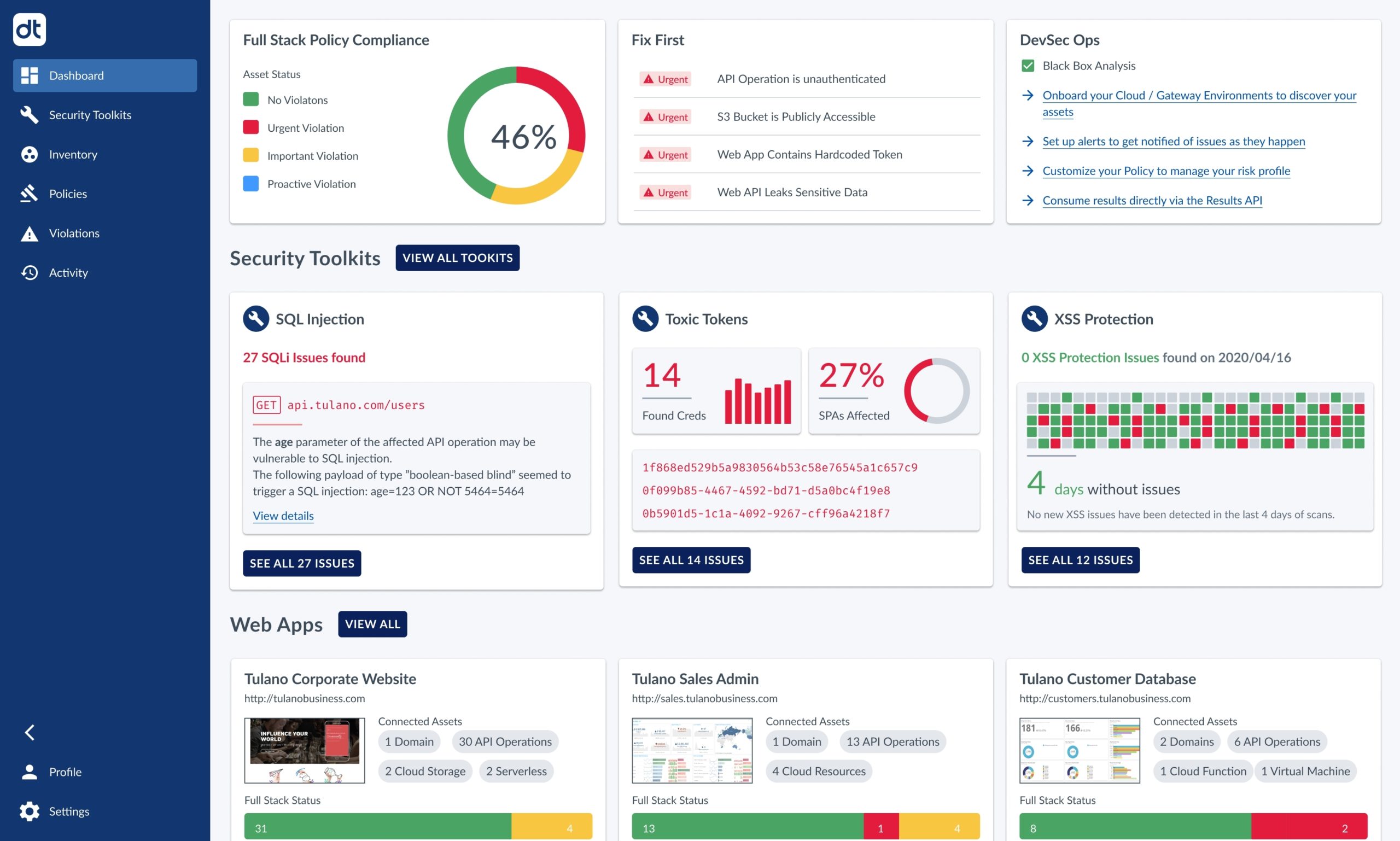
Data Theorem is a contemporary security platform that equips users with a formidable toolkit to safeguard their applications, with an emphasis on mobile apps. As a commercial solution, it is one of the mobile app pentesting tools that offers continuous automated security analysis and secures data whether it’s in transit, at rest, or being used.
Key Takeaways:
1. Automated Security Analysis: Data Theorem actively scans and scrutinizes mobile applications to spot security weak points and privacy issues. It also automatically checks fixes to ensure that the same problems don’t recur.
2. Privacy Compliance Checks: Data Theorem assists organizations in meeting compliance demands by detecting potential privacy risks and offering remediation advice.
3. API Discovery & Security Inspection: It uncovers unknown APIs and conducts ongoing security inspections to identify potential vulnerabilities.
4. Real-time Attack Surface Management: Data Theorem aids in managing the application’s attack surface in real-time to pinpoint changes that could usher in new risks.
5. Data Protection: Data Theorem ensures that data at rest, in transit, and in use is correctly protected and encrypted.
Data Theorem provides a comprehensive security solution, particularly potent in ensuring data security and privacy compliance. Its ability to carry out continuous security analysis and to manage the real-time attack surface differentiates it from many other tools on the market.
Pros:
- Comprehensive security solution
- Continuous security analysis
- Real-time attack surface
Cons
- Expensive subscription
- Does not offer low-level control
- Not enough customizations
Understanding Mobile App Penetration Testing Tools
When it comes to bolstering cybersecurity measures, mobile app penetration testing plays a vital role. It zeroes in on assessing the safety of mobile apps. This process is all about putting the app through its paces to spot any frailties, loopholes, or imperfections that could be a goldmine for cyber attackers. The aim is to button up the app by actively hunting down and fixing these security issues, ensuring user data stays under lock and key, and keeping the app’s wholeness intact.
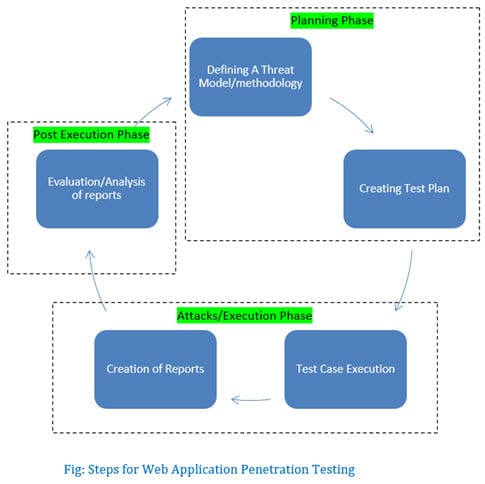
Penetration testing usually follows a clear-cut process. It all begins with collecting info about the app and its underpinnings, followed by pinpointing possible weak links and security gaps. The next move is to try and take advantage of these weak points to gain entry or inflict harm – mirroring what a genuine attacker would do. The insights gained from this are then put down in black and white and examined, leading to suggested strategies to mend the gaps.
Mobile apps can be susceptible to a myriad of security risks and threats. They can span from insecure data storage, shaky encryption procedures, and shoddy session management to weak spots in the server-side APIs the app interacts with. Given the wide scope of potential mobile app threats, penetration testing needs to be a fundamental part of any mobile app development endeavor, no matter the app’s size or purpose. It’s an irreplaceable weapon in our arsenal against cybercrime and holds immense significance in maintaining a safe digital space.
Conclusion
Ensuring the security of your mobile applications is paramount, and penetration testing is a vital part of that process. The array of mobile app pentesting tools we’ve explored offer an assortment of unique features and advantages. But keep in mind, the secret to superior results lies in the blend of using these tools, conducting hands-on testing, and sticking to robust security measures.
Hunting for a wide-ranging, easy-to-use solution? Give the Astra Security Vulnerability Scanner a whirl. It’s expert at digging up concealed vulnerabilities and fortifying your mobile application’s security. With Astra Security, keep potential threats at arm’s length and stay one stride ahead!
FAQs
1. What is the timeline for mobile application penetration testing?
A mobile application penetration testing takes 7-10 days. The rescans take half as much time.
2. How much does penetration testing cost?
The cost of mobile penetration testing depends on the scope of the test along with some other factors. Hence, it is difficult to provide a definitive figure. It can cost anywhere from $4,000-$100,000. Read about Penetration Testing Cost.
3. Why choose Astra for Pentesting?
The security engineers at Astra perform extensive manual pentest on top of machine learning-driven automated scans. The vulnerability reports appear on your dashboard with detailed remediation guides. You will have access to a team of 2 to 10 security experts to help you with the fixes. Know about Astra’s hacker-style pen-testing.
















