PCI DSS (Payment Card Industry Data Security Standard) is a set of rules and security requirements that organizations that handle credit card information must follow to protect their sensitive data and prevent breaches in order to protect cardholders from fraud.
With transactions increasingly shifting online and increasing cyber threats, PCI vulnerability scans play a crucial role in today’s digital environment by offering a systematic and effective means for detecting potential security gaps within the payment network infrastructure and mitigating them systematically and quickly.
However, starting the path toward PCI compliance may feel intimidating, particularly with all its rules and guidelines governing PCI vulnerability scans.
With this guide, we aim to:
- PCI DSS mandates secure handling of credit card data for all organizations, regardless of size, fostering trust and guarding against breaches.
- PCI vulnerability scans are vital for maintaining security and compliance by identifying weaknesses and preventing data breaches.
- PCI vulnerability scans mandate quarterly scans, third-party external providers, prompt remediation, and one-year report retention.
- Prepare for a PCI Vulnerability Scan by updating your cardholder data inventory and working with ASVs.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Understanding PCI Compliance
PCI DSS outlines the principles and strategies designed to reduce credit card fraud associated with its exposure. Now, let’s examine who must comply with these standards in greater depth: this requires compliance from an impressive array of entities.
PCI DSS compliance extends not just to large corporations or retail giants; rather it encompasses any organization handling cardholder data – from small e-commerce setups to expansive business networks. Adherence to PCI DSS helps foster consumer trust while protecting businesses against breaches that could incur substantial financial losses.
When businesses embrace these standards, not only are their defenses strengthened against cyber threats, but they can also establish themselves as reliable players within their market. When we delve further into PCI vulnerability scans in later sections, you will gain more insights into how to effectively navigate this path toward protecting your digital business frontier.
Diving into PCI Vulnerability Scans
PCI vulnerability scans are diagnostic tools and systematic processes designed to identify vulnerabilities within an organization’s payment card infrastructure. ASV scans perform remote evaluation of networks to pinpoint operating systems, services, and devices that might compromise cardholder data – providing valuable insight into areas for further security improvements within your company.
Examining the benefits of vulnerability scans demonstrates their value as an effective defense against data breaches and unauthorized access. Regular PCI vulnerability scans help you stay ahead of potential security flaws by preemptively recognizing security gaps before being exploited – safeguarding sensitive client data while upholding client trust.
PCI DSS requires vulnerability scans to be conducted at least quarterly to maintain an ongoing level of security, with auditing service vendors certified by the PCI Security Standards Council carrying them out.
After significant system modifications or significant occurrences such as system upgrades or downgrades, additional scans may also be conducted to maintain network protection and compliance with changing cyber threats.
PCI Vulnerability Scan Requirements
PCI DSS (Payment Card Industry Data Security Standard) requires regular vulnerability scanning as part of its security requirements to protect cardholder data. Here are five key PCI vulnerability scan requirements:
1. Regular Scanning
Perform quarterly scans, both internally and externally, on all relevant systems to identify new and evolving vulnerabilities.
2. Qualified Scanner
Employ a trusted third-party scanning provider with PCI expertise and tools to conduct thorough external scans that comply with PCI DSS requirements.
3. Internal Scanning
Conduct quarterly internal scans from within the network to find potential vulnerabilities and misconfigurations.
4. Timely Remediation
Promptly fix critical and high-risk vulnerabilities found during scans, typically within 30 days. Also, document all remediation efforts for compliance.
5. Detailed Reports
Provide thorough PCI scan vulnerability reports detailing discovered vulnerabilities, their severity, and remediation steps. Maintain these records for at least one year for compliance purposes.
Conducting a PCI DSS Vulnerability Scan
Preparing for a PCI Vulnerability Scan
Preparation for PCI vulnerability scans must be carefully carried out for it to run smoothly, starting with compiling a comprehensive inventory of systems and components involved with processing, storage, or transmission of cardholder data as well as making sure these are updated or patched as soon as they become known vulnerabilities.
Establishing clear communication plans between organizations and their chosen Approved Scanning Vendors (ASVs) allows for smooth execution and timely responses to any identified problems that emerge during scanning sessions.
Steps Involved in a PCI Vulnerability Scan
Once the groundwork has been laid, it’s time to get down to business with scanning. A PCI vulnerability scan follows a structured path, starting with ASV conducting an external network scan in order to identify vulnerabilities from outside.
Once identified vulnerabilities have been assessed and classified based on severity level for easier prioritization of remediation efforts, when remediated, they are submitted as scan reports for compliance verification with PCI DSS requirements.
Choosing a PCI-Approved Scanning Vendor (ASV)
Selecting an Approved Scanning Vendor (ASV) is an integral step in the PCI vulnerability scanning journey. The PCI Security Standards Council recognizes an ASV to conduct vulnerability scans according to PCI DSS requirements.
When selecting one, organizations must carefully consider experience, expertise, services offered, and communication lines with your ASV vendor and establish clear lines with them so they understand any specific network environments of interest to your organization.
By choosing a reliable and competent ASV, organizations can foster lasting partnerships that ensure compliance in business environments with security and compliance.
After the Scan: Reporting and Remediation
Understanding the Scan Report
Once they complete a PCI vulnerability scan, organizations receive a comprehensive scan report outlining their network security state and any vulnerabilities identified during it, often categorized according to potential risk and severity.
Care should be taken when reviewing this document to both understand current vulnerabilities as well as develop an action plan to address them strategically, gain deeper insight into security posture, and make informed decisions during future remediation steps.
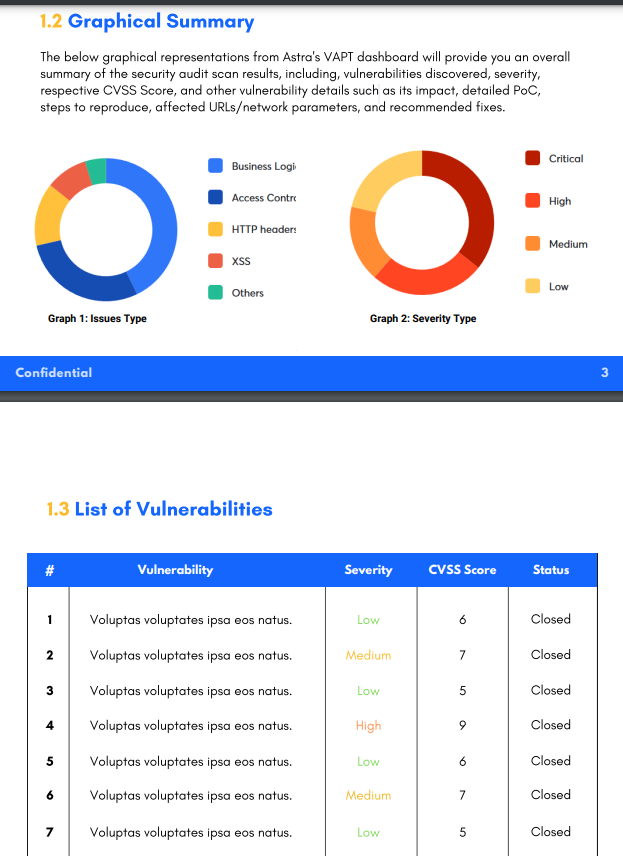
Remediation Steps after a PCI Vulnerability Scan
Once scanning is completed, remediation steps become an essential part of security operations. Remedying identified vulnerabilities requires taking an aggressive stance; organizations should prioritize vulnerabilities based on severity and impact to prioritize addressing each one accordingly.
Remediation may include closing identified loopholes, strengthening security protocols, or overhauling certain system components altogether; each remediation action taken must be recorded carefully so as to demonstrate compliance when reporting.
Reporting to Acquiring Banks and Card Brands
As soon as the remediation phase ends, organizations must notify all relevant parties – such as acquiring banks and card brands – of their compliance status. This phase includes providing an Attestation of Compliance (AOC) and validated scan reports as evidence that your organization abides by PCI DSS requirements.
Open communication between banks also plays an essential part here, ensuring all stakeholders remain abreast of your organization’s security posture – ultimately building trust between businesses and financial entities for secure card transactions.
How Can Astra Help?
As a trusted PCI Penetration Testing Provider, Astra’s dedicated team strives to continuously eliminate vulnerabilities. Our track record is a testament to our exceptional penetration testing services.
Astra’s approach to security testing and vulnerability assessment is built on three core principles: performance, precision, and reliability. Our highly skilled and experienced security experts excel at uncovering potential vulnerabilities that might otherwise go unnoticed.
Conclusion
Securing sensitive data in today’s digital landscape is both necessary and required of businesses handling cardholder information. PCI vulnerability scans offer organizations an effective method of identifying potential security gaps that needs mitigating through systematic scanning, reporting, and remediation process – essential elements in building consumer confidence while upholding the reputational protection of businesses.
As this guide draws to a close, it becomes evident that PCI compliance is both necessary and rewarding for any organization. Leaning into its structure strengthens defenses while encouraging an environment of proactive security management practices throughout daily operations – giving businesses greater confidence when traversing digital waters with increased ease and protection against threats or vulnerabilities. Staying one step ahead can protect organizations against risks while remaining compliant may even offer some tax breaks in regard to income taxes.
FAQs
Can I Conduct a PCI Vulnerability Scan Myself?
Organizations may perform internal vulnerability scans as an ongoing assessment of security posture; however, in order to meet PCI DSS compliance, scans must be performed by an approved scanning vendor (ASV), per the PCI Security Standards Council requirements. This ensures the scans adhere to an acceptable quality standard while upholding the integrity of the compliance process and process rigor.
What are the Common Vulnerabilities Detected?
Common vulnerabilities include outdated software, misconfigured network settings, or weak encryption protocols; often, vulnerabilities like SQL injection, cross-site scripting, and buffer overflows occur during scans as well. Organizations must remain mindful of these common flaws to reduce the risks of exploiting them while regularly applying updates or patches to system components.
How to Maintain PCI Compliance Post Scan?
Following their initial scan, organizations should look to integrate PCI DSS requirements into daily operations by regularly patching systems, conducting security assessments, and training staff in accordance with security best practices. Furthermore, periodic vulnerability scans beyond mandatory quarterly checks should also be established as this helps foster a vigilant environment.
















