About the Joomla SQLi
If you are using the version 3.7 of popular CMS Joomla! an update awaits your approval. The version 3.7 suffers from a severe SQLi (SQL Injection) vulnerability with a dread score of 8.6/10 and easy exploitation. An update for the same was released in next patch. All details for the same have been mentioned below.
Identifying the risk
A new component is added in the CMS, com_fields. This parameter is publicly accessible and vulnerable to SQLi.
Public accessibility increases the attack surface exponentially making application exploitable by anyone who uses it.
Technical Details
As explained by sucuri.net. com_fields component borrows some views from the administrative side component of the same name. It allows code reuse.
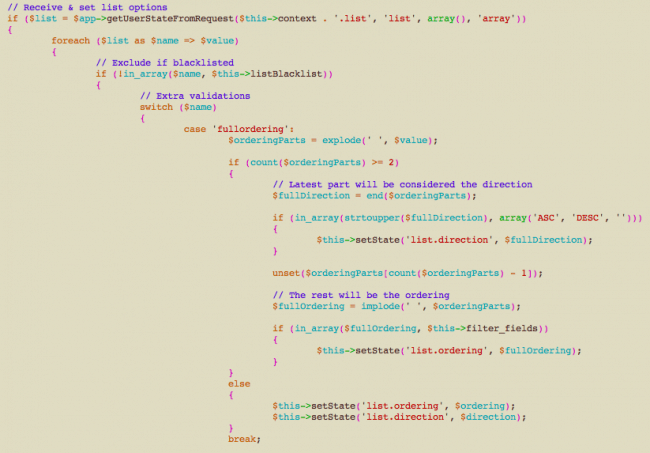
A $query->order() is a SQL query in Joomla. It is handled by concatenating the input with the SQL’s ORDER BY clause. Unfortunately, non-sanitised input was fed into the application.
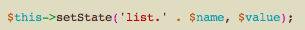
Sucuri quotes, “After the switch statement, this instruction sets the state we were looking for with a value that we can control, regardless of whether it generated a valid list.direction or list.ordering state.”
Consequences of the Vulnerability
Exploitation of the vulnerability is easy and can be done remotely. Understanding the capabilities of injection attacks, this SQLi enables the attacker to be able to hack into all databases. The attacker has to simply add the proper parameters to the URL in order to inject into the nested SQL queries to be able to run their exploit.
Fixing Joomla SQLi
Joomla released the patch to the vulnerability in May 2017 in the version 3.7.1. It is advised to update the Joomla version if you still are using the older version. At the time of writing the article latest version offered by Joomla is 3.7.3.
If you feel you have been hacked, contact Astra for professional assistance.
















[…] Vulnerabilities: CMS’s like WordPress, OpenCart, Magento, Drupal, Joomla etc. all have had critical vulnerabilities discovered in them. These vulnerabilities leave millions […]