The introduction of SQL servers was a big thing in the database industry. Before the introduction of SQL servers, database systems were proprietary and expensive. And SQL Server was the first database system compatible with the open-source database systems that were already in use.
The open-source database systems, however, were not as powerful as SQL servers. With power comes responsibility! As the SQL servers are very popular among organizations; these are one of the favourite targets of hackers and cybercriminals. SQL server audits are the perfect way to keep SQL servers secure from all kinds of attacks and intrusions. In this article, we’re discussing how to strengthen the security of SQL servers with a proper security audit.
So, let’s dig in!
What is SQL Server?
SQL Server is widely used for storing and managing data. It can handle large amounts of data, and it is easy to use. It has several components, including the relational database management system (RDBMS), the SQL Server Management Studio, and the SQL Server Agent.
SQL Server is a relational database management system (RDBMS) developed by Microsoft. It is primarily designed and developed to compete with MySQL and Oracle databases.
5 Main Components of SQL Server
The main components of SQL Server are:
1. Database Engine: The Database Engine manages and controls access to the data and makes sure there is no interference between the application and the data.
2. Reporting Services: Reporting Services is a component of SQL Server that provides a platform to deliver reports and create custom reports.
3. Analysis Services: Analysis Services is a component of SQL that provides business intelligence and data warehousing capabilities.
4. Integration Services: Integration Services is an ETL (Extract, Transform and Load) tool that makes it easy to extract data from different sources, transform it and load it into the destination database.
5. Master Data Services: Master Data Services helps enterprises centralize their data to a single database.
Why is securing SQL Servers important?
For most web users, the idea of data security is often limited to the protection of sensitive financial information, like credit card numbers. It’s easy to see why when data breaches are often in the news. But the truth is that SQL Server security is vulnerable at many levels, and the problem goes beyond sensitive customer information of customers such as credit card data, etc.
For instance, there are two main types of SQL Server security problems: Internal and External.
Internal security problems result from poor management, like poor data backups, while external security problems occur when outside parties hack into your database. Regardless of the type, SQL security problems can have a significant impact on your business.
SQL servers hold the bulk of the world’s data, and they’re instrumental in the success of any business. With the right security practices and regular SQL servers, SQL security audit can prevent SQL server hacking attempts. You can ensure that your company isn’t vulnerable to data loss, downtime, or other issues that could negatively impact your business’s success.
What is SQL Server Security Audit?
When it comes to SQL Server security, you need to know what SQL Server Audit is and how does it help you with securing your databases.
SQL Server Audit is a process that enables you to track and log events on the Database Engine and keep the SQL secure. The events can be tracked and logged at the instance level or on a per-database basis.
SQL Server Audit provides a number of features that one can use to track and log specific events. Auditing in SQL Server is a feature that records information about database systems and user actions for later review.
One can create a history of database activities, including database object creations, modifications, and deletions.
The SQL Server Audit enables you to audit the following:
1. Object access attempts, such as connection attempts and logins and database management activities.
2. Data modification attempts.
3. Administrators and users who connect to the Database Engine.
4. Database object access attempts.
5. User-initiated activities such as creating logins and databases.
5 Best Practices for SQL Server Security
They say that prevention is better than cure, so how can you protect your SQL Server from attacks? What are the best practices for SQL Server audit activities?
We all know that SQL Server is vulnerable to malicious attacks. Hackers are always looking for holes in SQL database server to get to the data stored inside. That’s why it’s important to have a strong SQL security audit trail that will help you track who changed what, when, and why.
1. Allow Specific Traffic Only
SQL Server should only be accessible to authorized traffic. SQL Server is installed with Windows Firewall enabled by default, but the default configuration allows all inbound and outbound connections.
This means that anyone can connect to your SQL Server and access it with a valid login. This is a great security feature, but an attacker only needs one hole to access your server. To protect your server from unauthorized access, limit the network traffic you allow to your server.
2. Keep the SQL Server-Updated
If you’re a DBA, you know that SQL Server is a powerful server capable of a lot. One of the things that makes SQL Server a powerhouse is that it’s constantly updated with the latest security patches.
If you want your servers to be up to date, you need to make sure your tools and applications are regularly updated as well. That way, you can ensure your server is secure and running smoothly. If you don’t, your SQL servers could be vulnerable to attacks, resulting in serious security breaches.
3. Secure Backups
Backups are something that most of us take for granted. You make backups to protect yourself from data loss. A backup is the only way to go if your web server fails. And it’s the only way to go if your web server is hacked.
All of your backups need to be in a secured location on the web. They need to be in a secured physical location. They need to be compressed and encrypted. A backup of the complete SQL Server is not a backup; It’s just an archive that contains all the sensitive details like emails, passwords, credit card details, etc.
4. Proper Password Policy for Admins
Strong passwords are a must for all database administrator accounts to make them resistant to brute-force attacks. As a database administrator, you usually have more than one database account. To prevent unauthorized users from accessing your database, you need to use strong passwords. The use of strong passwords protects your database from brute-force attacks.
A brute-force attack is a simple method of breaking an encrypted password. The attacker tries to guess the right password, using every possible combination until success.
5. Audit Regularly
SQL Server audit should be a normal part of your database maintenance schedule and include both the server and the databases. You should be checking for SQL Server Agent jobs, connections, and server settings for the server.
The list of jobs should include all SQL Agent jobs, including those created by other applications. Auditors should check the connections to verify that no unauthorized connections have been made to the instance. Finally, it would help if you verify that all server settings are as they should be.

What is SQLi, and How do you fix that?
A SQL injection is an attack on a back-end database that allows an attacker to interfere with the queries the application is making. This is performed by inserting specially-crafted input into an entry field on the website that connects to the database. If the application is not configured to verify that the input is valid, the attacker can execute code on the database server.
SQL injection must exploit a security vulnerability in an application’s software, for example, when user input is incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed.
Hackers can exploit the vulnerability in applications written in any programming language where the language engine processes untrusted data without adequate validation.
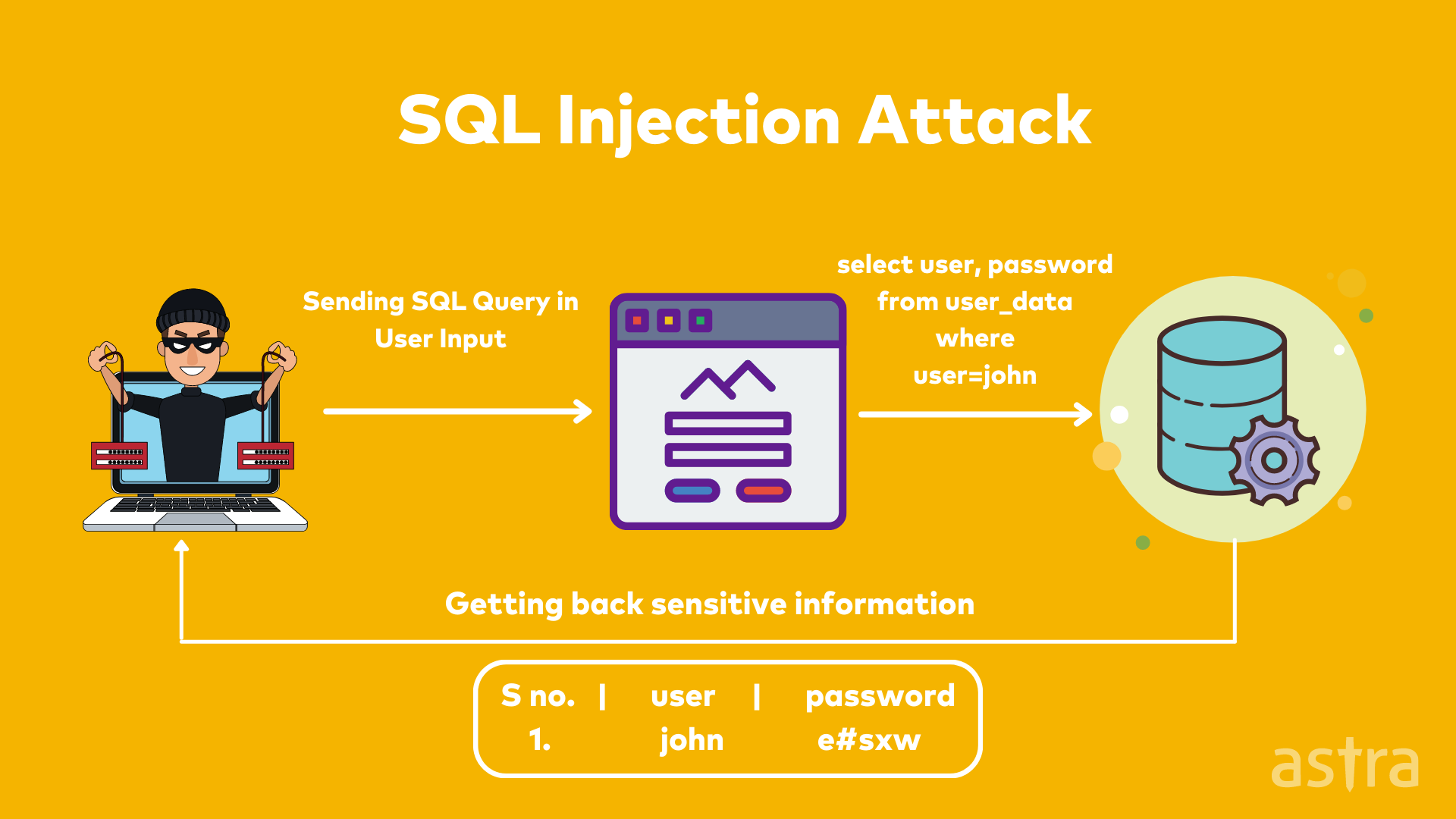
Impact of an SQL Injection Attack
A successful SQL injection attack can result in unauthorized access to sensitive data, such as passwords, credit card details, or personal user information. In a worst-case scenario, a successful SQL injection attack can completely compromise your system.
Hackers can perform a SQL injection attack by using your website search box, login form, or directly entering SQL commands into your website SQL commands.
For example, if you have a web page that has a login box such as the following:
<form action="login.php">
<input type = "email" name = "email">
<input type = "password" name = "password">
<input type ="submit">
</form>
Attackers can use SQL injection to bypass this login page and retrieve sensitive data from the database.
SQL injection prevention techniques
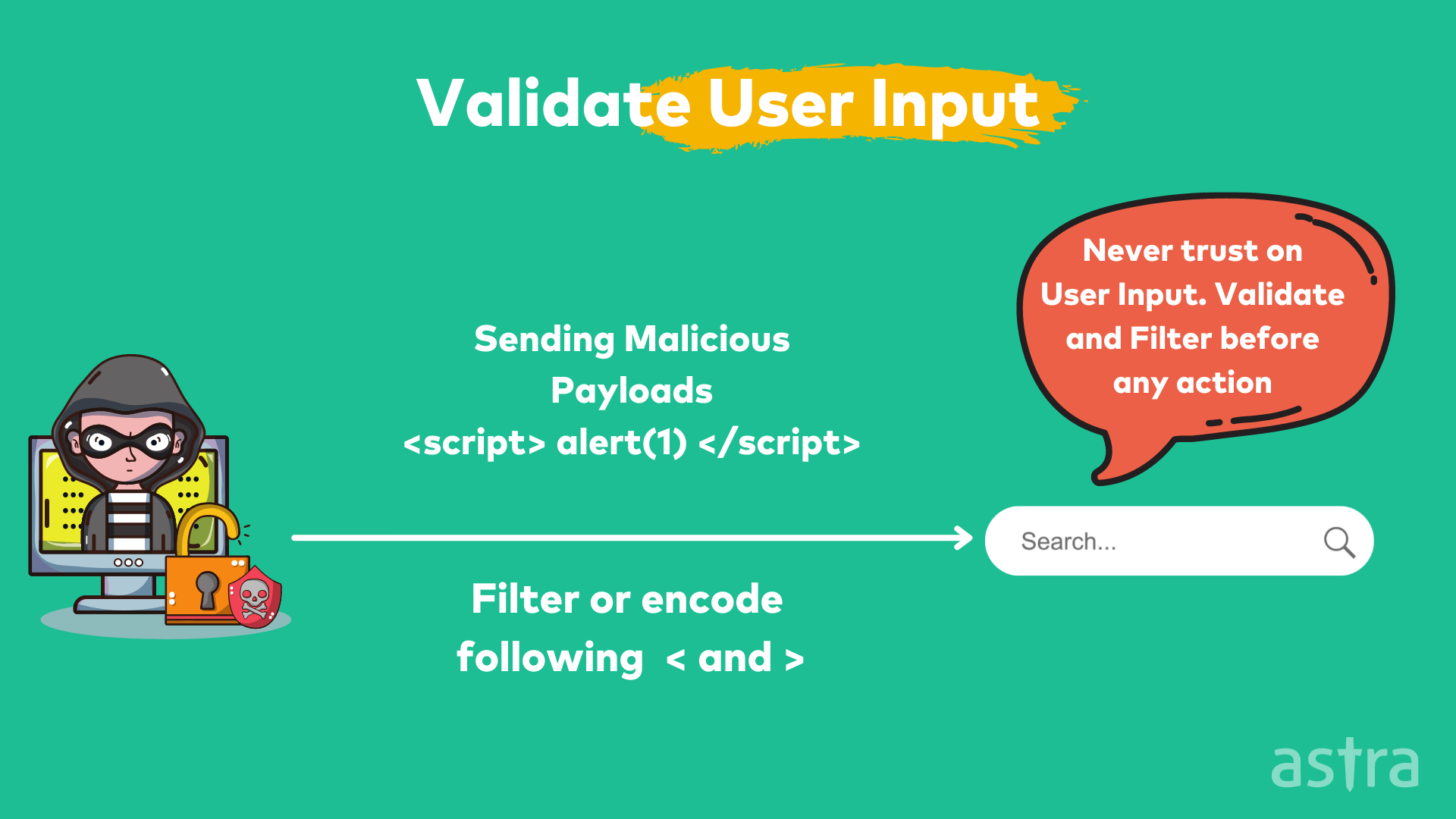
1. Input Validation
Input validation is a security technique used to filter out any malicious code entered into a form field. Input validation is an important aspect of security and helps protect your data from being tainted or stolen.
Input validation is a catch-all term for many of the different security techniques that websites use to prevent malicious code from being entered into your website. Input validation is used in several different places on a website, including Forms, Cookie values, Request headers, URL query strings.
Input validation is often confused with input sanitization, but they are two different things. Validation is a process that ensures that a field contains a certain type of data, while sanitization is a process that ensures that a field contains a safe version of a certain type of data.
2. Parameterized Queries
Parameterized queries are a means of pre-compiling an SQL statement to supply the parameters for the statement to be executed. This is particularly useful in situations where you have a query that is being executed multiple times but with different values in the various places in the SQL statement where a parameter is needed.
The most obvious example of this is when you have a query being executed many times in a loop, while some of the values in the query change each time through the loop. Parameterized queries are a bit of a dark art in SQL Server. They require a bit of finesse and a certain amount of knowledge about how SQL Server processes queries to do them effectively.
Learn More About SQL Injection Attacks
Why choose Astra for SQL Server Audit?
Today, most businesses require cyber security solutions like SQL server audit to protect their confidential data. The cyber security market is growing in terms of both opportunities and challenges. This is why Astra, a leading cyber security solutions company, offers comprehensive cyber security services.
At Astra, we provide cutting-edge cybersecurity services to our clients, which aim to provide solutions to their most pressing issues.
The Astra’s Rock-Solid Firewall is an application that actively blocks malicious files, spyware, adware, and other attacks. The program monitors your computer for any signs of intrusion, and it notifies you if it finds something suspicious. It also blocks communication with known malicious websites to prevent infections.

Conclusion
You might think that having a secure, locked-down SQL Server is enough to keep it safe from hackers. Well, you’d be wrong. Most SQL Server security failures come from within the company that owns the server, not from outside hackers. This is why it’s a great idea to regularly perform a SQL security audit on your SQL Server database servers to keep it secure.
















