Penetration testing is a process where an expert pentester makes use of tools to carry out manual exploits to identify vulnerabilities within your security infrastructure. Red teaming refers to the process of exploiting a target system like a hacker without time limitations while assessing the security measures and responses deployed against the vulnerabilities found.
Today, we will discuss what Red Teaming means in the cybersecurity context., how it is performed, how different is it from penetration testing, and which one to choose for your organization.
What is a Penetration Test?
Penetration Testing is a type of security testing that imitates cyber-attacks to identify the vulnerabilities of a system or a network before they can be taken advantage of by adversaries in the real world.
It does this by exploiting found vulnerabilities within the asset to see the extent of severity they pose to the security.
Penetration Test Purpose
Carrying out hacker-style penetration tests improves and aids in the maintenance of cybersecurity and compliance. Pentests can detect unpatched vulnerabilities within your assets like web and mobile applications, and networks.
Security regulations like PCI-DSS, HIPAA, and ISO 27001 mandate or require risk assessments to be carried out on a yearly basis to assess the fulfillment of cybersecurity best measures.
What is Red Teaming?
Red teaming is the process of assessing and exploiting a target system like a hacker. It is a way of testing how well an organization can defend itself against cyberattacks by simulating the actions of a real hackers.
It helps identify and fix security gaps, improve the performance of security teams, and increase the overall resilience of the organization. It can can involve various techniques, such as social engineering, network exploitation, physical intrusion, and web application attacks.
Red teaming appears to have similar principles and objectives as penetration testing, though I assure you they are not the same.
Red Team Assessment Purpose
‘Red Teaming’ was originally a military concept. It was first used to challenge biases and prejudices inherent in formulating defense security processes. Military services started hiring independent personnel skilled in critical thinking to call out the blatant flaws in these processes that otherwise appeared natural to the internal staff. This model was then replicated in government and political houses to highlight flaws in supposedly fine processes.
Soon, red teaming found its way into various other domains like – IT & computing, cybersecurity, control systems, physical security, counter-intelligence, and so on. Stakeholders were keen to test their system with red team assessment service from an outsider’s standpoint. And in other cases, they were required to do so due to various compliance mandates.
Red Teaming vs Pentesting
Although similar in theory, compared to pentesting, red teaming is a complex testing solution that takes more time and resources to give a thorough picture of not only the vulnerabilities in a security system but also the security measures and responses deployed against them.
The primary goal of red teaming is to test an organization’s assets for vulnerabilities & loopholes. It also tests the prevention measures and incident response mechanism, and inbuilt security biases & group-think in security processes.
A red team typically works (in stealth) against the blue team – responsible for upholding the security of an organization. If you’d please, you can think of it as a cop & thief situation. Where the red team plays the thief, and the blue team plays the cop. No need to tell, the red team wants to steal without getting noticed by the cop, here, the blue team. The job of the blue team is to save the organization from any act of security trespassing by detecting and thwarting it in time.
Difference Between Red Teaming & Penetration Testing
As we said Red Teaming and Penetration Testing are not equal. There are some fundamental differences in these processes which give them two different names. Let us look at some of the important differences between them:
| Red Teaming | Penetration Testing |
|---|---|
| Red teaming is an adversary-based assessment of the defense capabilities. | Penetration testing is a methodology-based assessment of the system & network. |
| Red teaming involves critical thinking and challenges security biases. | Penetration testing highlights hidden vulnerabilities in the system. It doesn’t deal with the biases with which they were constructed. |
| Red teaming is a secret process done to identify weak points in assets, people, and protocols. | Almost all concerned members (including the blue team) are informed about penetration testing beforehand. |
| A red team test is unique to the organization. One model doesn’t fit all in red teaming. | The penetration testing methodology can be replicated for more than one application or network. |
| Red teaming usually involves going against the norm in testing a system. The scope in a red teaming is very holistic covering - process, people, protocols, and system. | Penetration testing does not look beyond the scope of assessing a system. |
| Red teaming explores alternatives in plans, operations, concepts, organizations and capabilities. | Penetration testing does not offer an alternative perspective to constructing the security framework. It is limited to providing fixes for vulnerabilities. |
| Red teaming costs more. | Penetration testing is cost-effective. |
Related Article: Penetration Testing Quote | 10 Best Cyber Security Audit Companies [Features and Services Explained]
Red Teaming or Penetration Test: What Should You Conduct?
We have understood the differences between Red teaming & penetration testing. Now, what should you choose?
In our experience, we have seen mostly bigger & complex organizations undergo the red team test. Most smaller and medium-sized organizations go with penetration testing.
Here’s how to decide if you need to conduct red teaming or not?
- Check if you have complicated systems & processes in your organization
- Check if the security impact on your organization would be massive & impactful
- Check if you have a well-defined environment for all operations
If you answered in YES to all these queries, you should definitely go for red teaming.
Red Team Penetration Testing Methodology & Tools
Although a red team testing is tailored to each organization, the methodology generally includes:
- System modeling
- Attack tree development
- Planned deception
- Propaganda
- Authorized espionage
- Vulnerability assessments
10 common tools used during Red teaming are:
- Nmap
- SQLmap
- Nikto
- Openvas
- OSINT framework
- Shodan
- Metasploit
- FOCA
- Veil
- Phishery, and other tools as mentioned here.
Red Teaming & Penetration Testing with Astra Security
Astra Security offers comprehensive penetration testing with Astra’s industry-first Pentest Suite. With Astra, you get:
- A completely managed vulnerability dashboard
- An automated scanner (detects over 2500 vulnerabilities; scans remotely as well as behind logins)
- Steps-to-reproduce the vulnerability (including PoCs, selenium scripts, etc)
- Detailed steps-to-fix, and expert assistance
- Monetary loss value associated with a vulnerability
- Intelligently calculated risk score for each vulnerability
- A grading system to rank the security of your assests
- Publicly verifiable certificate
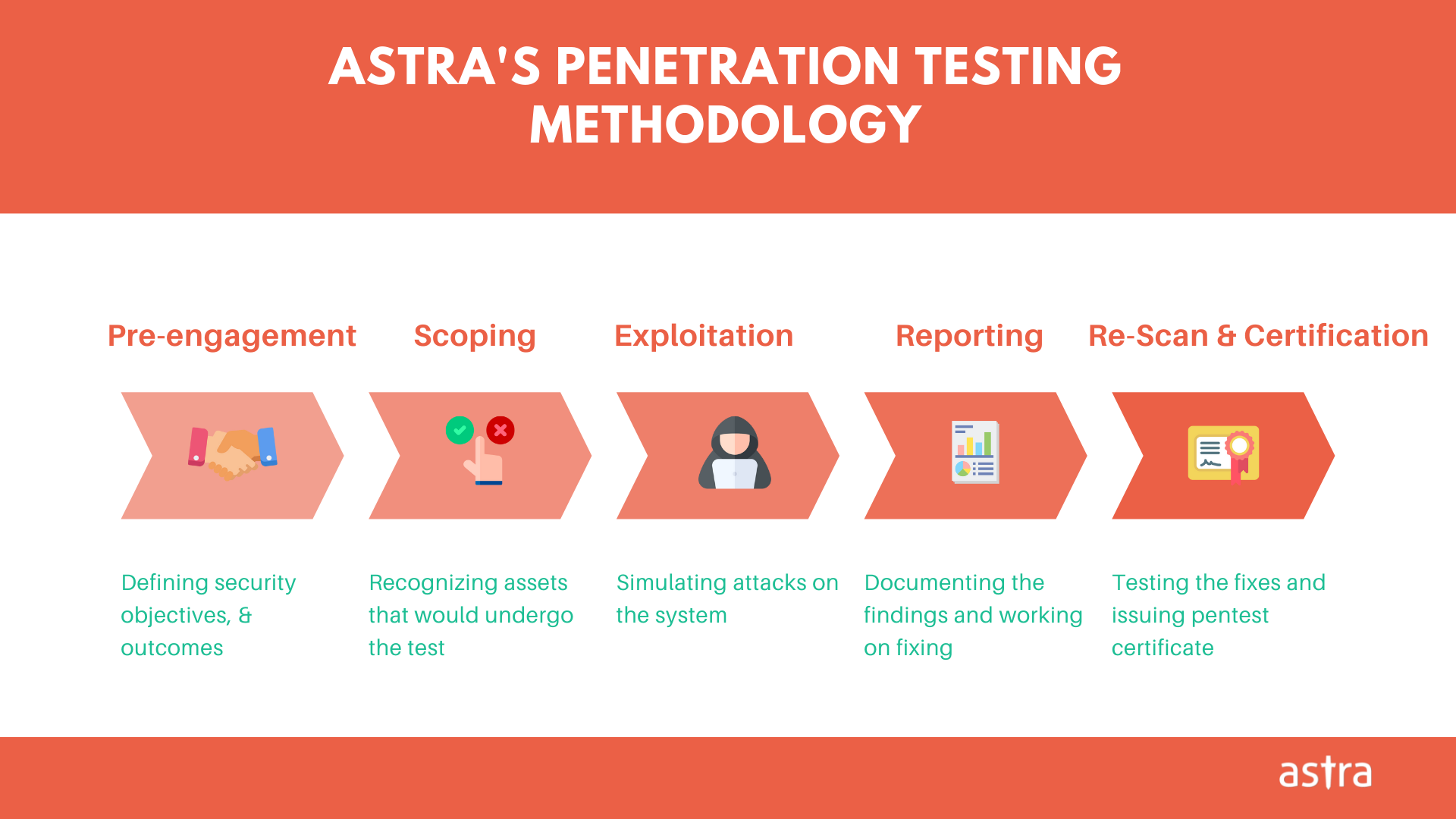
We also help you with Red teaming engagements via our vetted security partners.
Conclusion
Hidden biases & group-thinking can sabotage the defense mechanism in giant organizations. It is extremely important to pinpoint those biases and the vulnerabilities they cause. Red teaming critically analyzes the security of an organization to suggest alternative ways to build security frameworks. While red teaming and penetration testing appears similar in concept, they are poles apart in practice. Your organization will need red teaming if it has more complex and well-defined processes. If not, penetration testing is an equally good option for you.
If you’re looking for red teaming services or penetration testing services, we can surely help you 🙂
FAQs
1. Is red teaming the same as penetration testing?
No, red teaming and penetration testing are different procedures with some overlapping features.
2. What is red teaming and penetration testing?
Penetration testing refers to the process of evaluating a system’s security posture by finding and exploiting vulnerabilities present in the said system. In red teaming, a group of security experts tries to break into a system by using hacker-style methodologies.
Who is a red team penetration tester?
A red team penetration tester is a cybersecurity professional who acts as a hacker to identify and resolve vulnerabilities in a network. They launch their attacks without prior notice to their team to identify any loopholes in their network. They are ethical hackers who are on the offense, staging strategic attacks.
















