From the inception of the Internet, data security has become a paramount concern.
In a world where smartphones are now indispensable, ensuring Android app security is no less important.
With over 3.6 billion active Android devices worldwide, taking steps to secure these apps is a crucial task.
As such, the following sections will discuss:
- The current state of mobile security
- Key aspects of Android app security
- Common issues with ensuring Android app security
- Android app security checklist
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

The Current State of Mobile Security
Mobile security today is a constant arms race.
While developers create increasingly sophisticated protections, criminals simultaneously devise new methods of breaching them.
For example, consider frequent news stories detailing large-scale data breaches or new malware infecting thousands of devices.
Despite this, developers often overlook mobile app security, focusing more on functionality, aesthetics, or speed.
However, as a large portion of data breaches originate from insecure mobile apps (like in the infamous Uber data breach), ignoring security allows countless opportunities for criminals. With billions of Android devices in service, ensuring Android app security is not just important—it’s imperative.
Understanding Android App Security
Android is equipped with multiple layers of security to protect users and their data. Google Play Protect checks installed apps for malicious software – such as malware signatures or strange permissions – from the app installation process.
For example, if you install a note-taking app with access to your call logs, Google Play Protect will issue a warning. Furthermore, Android provides sandboxing, which isolates each app in its own environment.
For instance, a photo editing app with no access to emails is confined to its sandbox.
To add an extra layer of security, Android devices are encrypted by default, making it hard to access data without authorization.
However, cyberattacks may still occur through zero-day exploits or social engineering. To prevent such attacks, keep devices updated with the latest security patches.
Signs of a Compromised App
When evaluating the safety of an app, there are some signs that it may have been compromised. Here are a few red flags to look out for:
1. Unexpected Data Usage
If an app is using more data than usual, this could be a sign of malicious activity. Hackers often use your data to send personal information to other servers.
2. Device Performance
An app that causes your device to slow down, crash, or drain your battery faster than usual could indicate a security issue.
Any suspicious activity on your device or linked accounts, like sent messages or calls that you did not make, could be a sign that an app has been compromised.
4. Unwanted Ads or Pop-Ups
Excessive ads or pop-ups, particularly from an app that isn’t ad-supported, could indicate that adware or malware has compromised it.
5. Unfamiliar Apps
If you notice unfamiliar apps installed on your device that you didn’t personally download—this could be a result of a compromised app.
6. Changes in App Behavior
Sudden changes in how an app functions or interacts may be an indicator of a compromise. For instance, if it seeks new permissions or starts asking for sensitive data it didn’t require before.
Key Aspects of Android App Security
1. Authentication and User Verification
Authentication and User Verification is one of the key aspects that ensures a robust Android app security system. Here’s how it works:
A. Passwords
These are commonly the first line of defense against unauthorized access. For example, secure Android apps require strong passwords that include a mix of numbers, symbols, and uppercase and lowercase letters.
B. Biometrics
It involves the use of physical characteristics, like fingerprints or facial recognition, to verify users. For instance, banking apps often use this as an additional layer of security.
C. Multi-factor Authentication (MFA)
It adds an extra layer of protection by requiring multiple methods of verification. For example, after entering your password, an app may send an OTP (One-time password) to your registered mobile number or email address for further verification.
D. Behavioral Biometrics
This method tracks and uses patterns of user behavior such as typing speed or screen interaction style to verify a user’s identity.
E. Security Questions
These are yet another form of user verification, where you have to answer questions only you should know the answer to.
F. Device Binding
Certain apps associate your user account with your specific device, adding a layer of security.
2. Application Sandboxing
Application Sandboxing is a vital aspect of Android app security that isolates applications from each other. This mechanism operates on the principle that every app should have its separate ‘sandbox’ or playing area.
For instance, imagine you’re at a playground where each kid has their individual sandbox to play in. They can build sandcastles, burrow holes, or scatter the sand all they want within their box but cannot interfere with others’ sandboxes.
Translating this to the world of apps, such sandboxing ensures that if an app, like a music player, somehow becomes malicious, it cannot interfere with another app, say, your banking app. It restricts applications from accessing data or code from other applications unless given explicit permission, thereby greatly reducing the risk of a potential breach.
3. Android Permissions
Android permissions act as gatekeepers to protect your personal information from being accessed by apps without your knowledge. Whenever you install a new app on your Android device, you’ll notice it asking for certain permissions, like access to your contacts, location, camera, etc.
For instance, a mapping app would need location access to guide you to your destination. However, a simple puzzle game asking to access your contacts might raise a flag. Then, the power lies in your hands to grant or deny such permissions.
It’s advisable to only allow necessary permissions, thereby ensuring that your sensitive information is not exposed to potentially malicious apps.
4. Encryption
Encryption is like a secret code that scrambles your data, making it unreadable to anyone who doesn’t have the key to decipher it. With Android, information like your photos or messages are locked away – just like having your personal files in a safe, but instead, it’s your smartphone.
Common Android App Security Issues
Despite Android’s robust security measures, some risks persist. These include:
1. Malware Infections
Malware, such as viruses, worms, or ransomware, can covertly infiltrate your phone, causing it to malfunction and compromise your data.
2. Phishing Attacks
Fraudulent emails or texts trick users into revealing sensitive information, like passwords or credit card details, to attackers. This is commonly experienced through malicious links in seemingly harmless app notifications or emails.
3. Unsecure Wi-Fi Networks
Using unencrypted public Wi-Fi networks can make your device vulnerable to attacks. It’s akin to willingly leaving your front door wide open, granting cybercriminals a chance to steal personal data.
4. App Impersonation
Bogus apps resembling genuine ones successfully trick users into installing them, leading to them divulging their login information or accessing malicious links.
5. Data Leakage
Often, apps require access to a user’s personal data to function, but some may mishandle this information, leading to unintentional data exposure.
6. Operating System Flaws
Every software has some vulnerabilities, and Android is no exception. These flaws can be exploited by hackers to gain unauthorized access to devices.
7. Lack of Updates
Outdated software or apps may lack the latest security updates, making them a soft target for attackers.
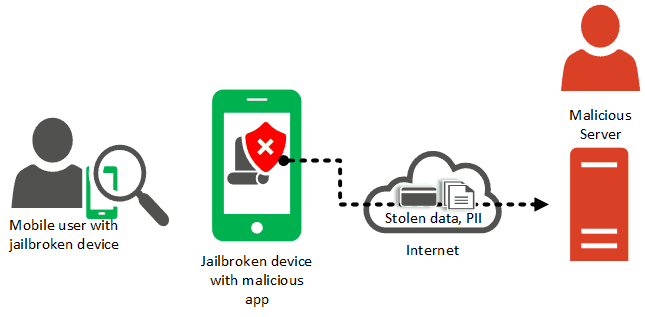
8. Jailbreaking
While it provides more control and customization, jailbreaking or rooting your Android device can leave it susceptible to security threats.
Android Security Best Practices
To ensure your Android device’s security, follow these best practices:
1. Download Responsibly
Only download apps from trusted sources like Google Play Store. Applications from unknown sources can contain malware.
2. Regularly Update Software and Apps
This keeps your device’s security features up-to-date, fixing any existing vulnerabilities.
3. Limit Permissions
Only grant necessary app permissions. Remove permissions that seem unnecessary for the app’s function.
4. Install Security Software
Use anti-virus or security apps from reliable providers to protect your device against malware.
5. Avoid Public Wi-Fi
Public networks can expose your device to cyber threats. Use a VPN if necessary.
6. Use Strong, Unique Passwords
This makes unauthorized access difficult.
7. Enable Two-Factor Authentication
This adds an extra security layer, requiring more than just your password for login.
8. Encrypt Your Device
Use Android’s built-in encryption to protect your personal data from unauthorized access.
9. Do Regular Backups
Back up your data regularly to prevent loss from potential security breaches.
10. Use Fingerprint or Face Recognition
These are hard to replicate, making them safer options than traditional passcodes.
11. Turn Off Auto-Fill
Although convenient, auto-fill functions make it easier for others to gain unauthorized access to your accounts.
Android App Security Checklist
Here’s a simple checklist to get you started:
- Code Review and Static Analysis:
- Conduct regular code reviews to identify vulnerabilities.
- Use static analysis tools to find and fix security issues in the codebase.
- Secure Coding Practices:
- Follow secure coding guidelines and best practices.
- Avoid hardcoding sensitive data like passwords and API keys.
- Authentication and Authorization:
- Implement strong authentication mechanisms.
- Enforce proper authorization to restrict access to sensitive features and data.
- Data Encryption:
- Encrypt sensitive data in transit using HTTPS.
- Encrypt data at rest using appropriate encryption algorithms.
- Secure Communication:
- Ensure that all network communications are secure.
- Validate SSL certificates and avoid trusting all certificates.
- Input Validation:
- Validate user input to prevent SQL injection, XSS, and other injection attacks.
- Use input validation libraries and frameworks.
- Secure Storage:
- Safely store sensitive data using Android’s Keystore.
- Avoid storing sensitive information in SharedPreferences.
- Access Controls:
- Enforce proper access controls to prevent unauthorized access to app components.
- Implement role-based access control if necessary.
- Code Obfuscation:
- Obfuscate your code to make reverse engineering difficult.
- Use tools like ProGuard or R8 for code obfuscation.
- Secure API Usage:
- Ensure that APIs used by your app are secure and properly configured.
- Use API keys and tokens securely.
- Secure File Handling:
- Safeguard against unauthorized access to files and directories.
- Use Android’s FileProvider for secure file sharing.
- Patch Management:
- Keep third-party libraries and SDKs up to date to patch known vulnerabilities.
- Stay informed about Android security updates.
- Logging and Error Handling:
- Implement proper logging practices.
- Avoid logging sensitive data, and ensure error messages are not exposed to users.
- Penetration Testing:
- Conduct regular penetration testing to identify vulnerabilities.
- Use tools and services to simulate attacks and assess app security.
- Secure Updates:
- Ensure that app updates are delivered securely.
- Verify the integrity of updates before installation.
- User Education:
- Educate users about app security best practices.
- Encourage strong password practices and caution with third-party app installations.
- Incident Response Plan:
- Develop a plan to respond to security incidents.
- Define procedures for reporting and mitigating security breaches.
- Compliance:
- Ensure compliance with relevant data protection regulations (e.g., GDPR, CCPA).
- Follow platform-specific security guidelines provided by Google.
- Threat Modeling:
- Conduct threat modeling exercises to identify potential security threats.
- Prioritize and address high-risk areas.
- Continuous Monitoring:
- Implement continuous security monitoring for your app.
- Use analytics and monitoring tools to detect and respond to anomalies.
Secure Your Digital Landscape with Astra
Astra is a leading SaaS company that specializes in providing innovative Android app security solutions. Our comprehensive suite of cybersecurity solutions blends automation and manual expertise to run 8000+ tests and compliance checks, ensuring complete safety, irrespective of the threat and attack location.
With zero false positives, seamless tech stack integrations, and real-time expert support, we strive to make cybersecurity simple, effective, and hassle-free for thousands of Android applications & businesses worldwide.
In conclusion, the current state of mobile security is a constant battle against evolving threats. Android offers robust security measures, including Google Play Protect and sandboxing, but signs of a compromised app must be recognized. Key aspects of Android security include authentication, application sandboxing, permissions, and encryption. However, adhering to best practices such as downloading responsibly, regular updates, limiting permissions, and enabling two-factor authentication is crucial for protecting your Android device and personal data. Stay vigilant to ensure a secure mobile experience.
FAQs
What is a sandbox in Android security?
In Android security, a sandbox is a restricted & isolated environment where each app runs independently. It limits an app’s access to system resources, ensuring it can’t interfere with other apps or the core operating system. This containment reduces the potential for security breaches and protects user data and device integrity.
Why shouldn’t I install apps from unknown sources?
Installing apps from unknown sources can expose your device to malware and security threats. Official app stores have strict security checks, ensuring apps are safe, functional, and free of malicious intent, providing a safer user experience.
What is two-factor authentication?
2FA, or Two-Factor Authentication, is a security process that requires users to provide two different authentication factors before gaining access to a system or account. These factors typically include something the user knows (like a password) and something they have (like a smartphone for receiving authentication codes), enhancing account security.
















