AWS penetration test involves testing your AWS infrastructure for vulnerabilities by a team of skilled penetration testers that hackers might exploit. Upon completion of the pentest, a detailed report constituting the areas of weaknesses and the course of action to fix them are also mentioned.
As the digital realm advances, cloud services are becoming a popular method of corporate storage, processing, and management of data. In fact, according to a recent report by Statista, Amazon Web Services (AWS) maintains its dominant position in the global cloud infrastructure market, with a 32% share in Q2 of 2023.
But, with such popularity comes the risk of fast-growing cybercrime. Whether it is corporate espionage or ransomware attacks, cloud providers including Amazon are daily subjected to increasingly sophisticated attacks. This is where AWS pentesting comes in.
In this article, we will take a deep dive into AWS pentests and cover the following:
- What is the shared responsibility model in AWS?
- What is the AWS penetration testing checklist?
- Which tools are used in AWS Testing?
Like most cloud storage platforms, AWS also follows a Shared Responsibility Model. To put it in everyday language, the Model essentially divides the security responsibilities in the cloud where AWS takes care of keeping the cloud and its infrastructure secure, while users, whether individuals or companies are in charge of safeguarding their own data and assets stored in the cloud.
As such, we can categorize the security testing of an AWS platform into two parts:
1. Security of the Cloud
The security of the Cloud is the security responsibility of Amazon (AWS) to make sure their cloud platform is secured against any possible vulnerabilities and cyber attacks for the companies that are using any AWS services. The security of the cloud includes all the zero days and logic flaws that can be exploited at any step to disrupt the performance of an AWS server/s.
2. Security in the Cloud
Security in the cloud is the responsibility of the user/company to make sure their deployed applications/assets on AWS infrastructure are secured against any kind of cyberattacks. A user/company can enhance the security of their applications on the AWS cloud by implementing necessary security practices.
Why Astra is the best in pentesting?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- Vetted scans ensure zero false positives
- Our intelligent vulnerability scanner emulates hacker behavior & evolves with every pentest
- Astra’s scanner helps you shift left by integrating with your CI/CD
- Our platform helps you uncover, manage & fix vulnerabilities in one place
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

AWS Penetration Testing Checklist
Penetration testing within the Amazon Web Services (AWS) environment comes with its own set of intricacies, demanding a systematic and methodical approach to ensure thorough security evaluation of all three components covered namely – Considerations, Preparations, and Steps. Here’s a detailed AWS Penetration Testing Checklist to help you get started:
Considerations of AWS controls: Inclusion and Limitations
Before diving into AWS penetration testing, it’s essential to understand the critical Amazon Web Services controls and configurations that need to be thoroughly tested for security. These controls include but are not limited to the following list:
a. Governance:
- Identify Assets & Define AWS Boundaries: Begin by clearly defining the scope of AWS assets, and delineating boundaries for the assessment.
- Access Policies: Scrutinize access policies to ensure they align with security best practices and grant the appropriate level of permissions.
- Risk Evaluation: Identify, review, and evaluate potential risks within the AWS environment, incorporating AWS into broader risk assessment frameworks.
- IT Security & Program Policy: Ensure that AWS usage aligns with IT security and program policies, adhering to organizational guidelines.
b. Network Management
- Network Security Controls: Assess network security controls to identify and rectify vulnerabilities or misconfigurations.
- Physical Links: Examine physical links to maintain the integrity of the network infrastructure.
- Granting & Revoking Access: Review processes for granting and revoking access rights, ensuring timely and appropriate access management.
- Environment Isolation: Verify the isolation of environments to prevent unauthorized access and lateral movement.
- DDoS Layered Defense: Evaluate DDoS mitigation strategies to protect against distributed denial-of-service attacks.
- Malicious Code Controls: Implement controls to safeguard against malicious code, including malware and exploits.
c. Encryption Control
- AWS Console Access: Secure AWS console access, implementing strong authentication and authorization mechanisms.
- AWS API Access: Ensure secure access to AWS APIs, safeguarding against unauthorized usage.
- IPSec Tunnels: Assess the security of IPSec tunnels, ensuring encrypted communication channels.
- SSL Key Management: Maintain robust SSL key management practices for secure data transmission.
- Protect PINs at Rest: Encrypt and protect Personal Identification Numbers (PINs) when at rest to prevent unauthorized access.
d. Logging and Monitoring
- Centralized Log Storage: Establish centralized log storage for comprehensive visibility into AWS activities.
- Review Policies for ‘Adequacy’: Regularly review logging policies to ensure they meet the adequacy requirements for security and compliance.
- IAM Credentials Report: Scrutinize Identity and Access Management (IAM) credentials reports to identify and rectify any suspicious or inappropriate access.
- Aggregate from Multiple Sources: Aggregate log data from multiple sources within the AWS environment for a holistic view of activities.
- Intrusion Detection & Response: Implement intrusion detection and response mechanisms to promptly address security incidents and anomalies.
Are there any sections off-limits for AWS penetration testing?
While penetration testing is a valuable security practice, there are certain activities that are off-limits within AWS, as they can disrupt services or violate AWS terms of service:
- Servers belonging to AWS
- Physical hardware, facility, or underlying infrastructure that belongs to AWS
- EC2 belonging to other vendors
- Amazon’s small Relational Database Service (RDS)
- Security appliances managed by other vendors
Steps to take before performing AWS Penetration Testing
Before initiating AWS penetration testing, several preparatory steps are crucial to ensure a smooth and successful assessment:
- Define the scope of the penetration test including the target systems.
- Run your own preliminary i.e. run vulnerability scanners like AWS Inspector or Astra’s vulnerability scanner to find basic vulnerabilities before the in-depth analysis.
- Define the type of security test you will conduct.
- Outline the expectations for both the stakeholders and the penetration testing company (if outsourced).
- Establish a timeline to manage the technical assessment.
- Define a set of protocols in case the test reveals that security has already been breached.
- Obtain the written approval of the related parties to perform a pen test.
How to perform Penetration Testing on AWS?
The following section will provide you with a detailed overview of the systematic steps required to initiate, execute, and conclude a successful AWS penetration testing engagement.
1. Identity and Access Management (IAM)
The first and most important step in the process of penetration testing is to identify the assets of data stores and applications. Some important points to keep in mind during asset identification are:
- Removal of keys from the root account
- Implement two-factor authentication
- Do not use the root account for daily tasks or automation
- Restrict the permission to service accounts
- Limit the use of one key per user
- Regularly change SSH and PGP keys
- Delete inactive security accounts
2. Logical Access Control
The next step to follow after the identification of assets is to manage the access control on the cloud. It is a process of assigning different actions to the resource. The main process of Logical Access Control involves controlling access to resources, processes, and users of AWS. Credentials related to the AWS accounts must be safe and secure.
3. S3 Buckets
S3 is a cloud folder generally known as a “Bucket”. It is a storage server that delivers region exceptions, access logging, versioning, encryption, access logging, etc. Here are two important things you must ensure to maintain the security of the S3 buckets:
- Permissions (such as GET, PUT, DELETE, LIST for HTTP methods) should be restricted to certain users
- The logging and versioning of the bucket should be enabled.
4. Database Service
The database is an important part of most web services. It is important to follow the necessary steps to secure the database of your application. The key points to keep in mind while performing a security audit are:
- Use the Multi-AZ deployment method.
- Limit access to specified IP addresses.
AWS Penetration Testing Policy
It’s essential for organizations to have a well-defined AWS penetration testing policy in place. This policy should outline the rules, procedures, and expectations regarding penetration testing activities on AWS. Key elements of an AWS penetration testing policy include:
- Authorization Process: Clearly define the process for obtaining authorization from AWS or the AWS customer before conducting penetration testing.
- Scope and Objectives: Specify what is in scope and out of scope for testing, as well as the testing objectives.
- Testing Methods: Describe the testing methods and techniques that can be used, as well as any prohibited activities.
- Documentation Requirements: Outline the documentation and reporting requirements, including how findings should be documented and communicated.
- Compliance with Laws and Regulations: Emphasize the importance of compliance with relevant laws and regulations, including data protection and privacy laws.
- Incident Response: Include guidance on how to handle incidents or unintended disruptions that may occur during testing
- Retesting Procedures: Explain the process for retesting after vulnerabilities have been remediated.
AWS Penetration Testing Certification
AWS offers a penetration testing certification known as the “AWS Certified Security – Specialty” certification, which covers various aspects of AWS security which can be quite lucrative for the professionals in the field. To achieve this certification, candidates are required to demonstrate their knowledge and skills in areas such as:
- Incident response
- Logging and monitoring
- Identity and access management
- Infrastructure security
- Encryption
- Penetration testing and vulnerability assessment
This certification is a valuable recognition of expertise in securing AWS environments and conducting penetration testing within the AWS ecosystem.
Tools Used in AWS Penetration Testing
There are several tools available in the market that you can use to pentest your AWS integrated services. Different sets of tools are available to carry out different types of tests. Here are some of them:
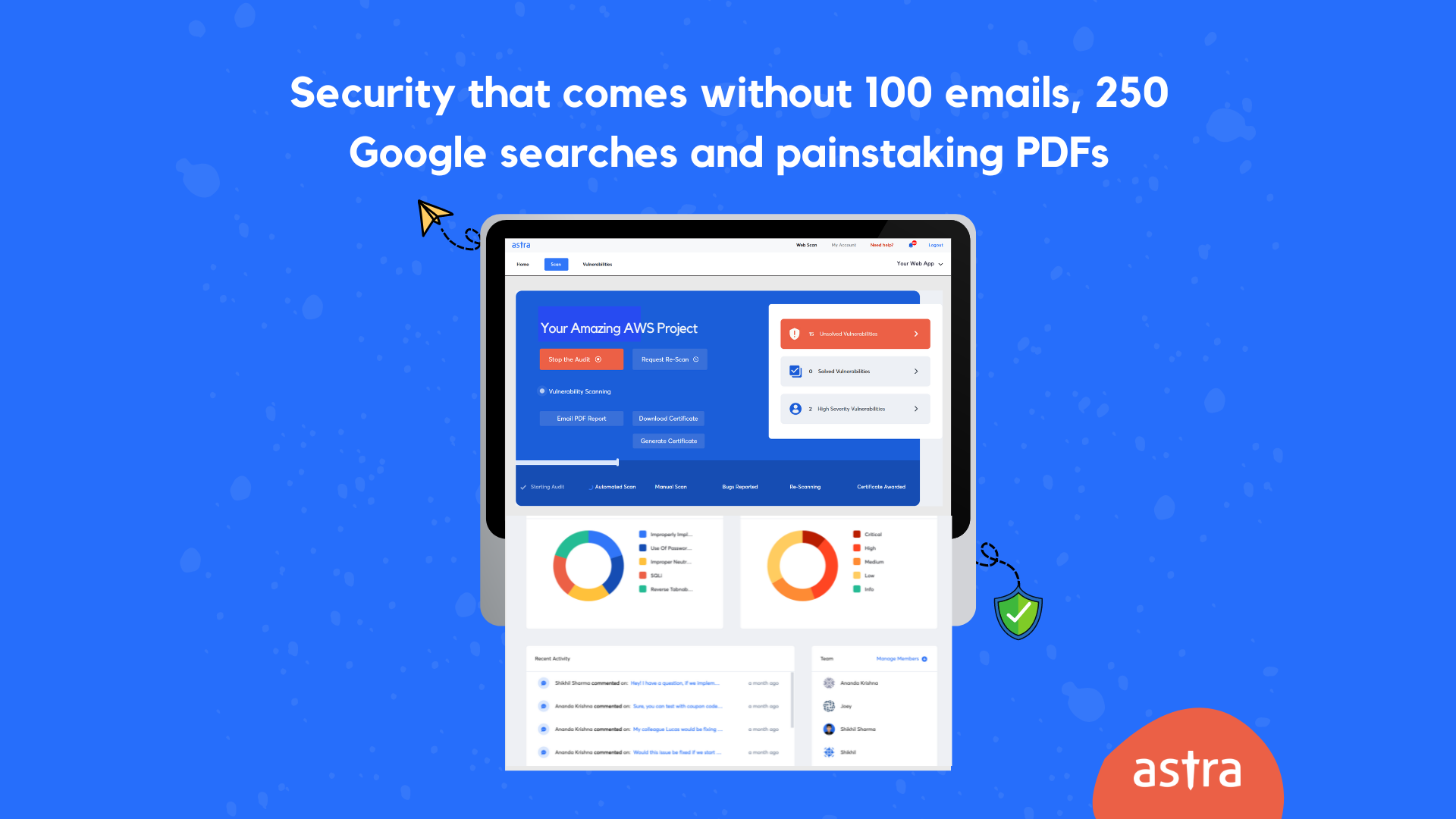
1. Astra Security Scan
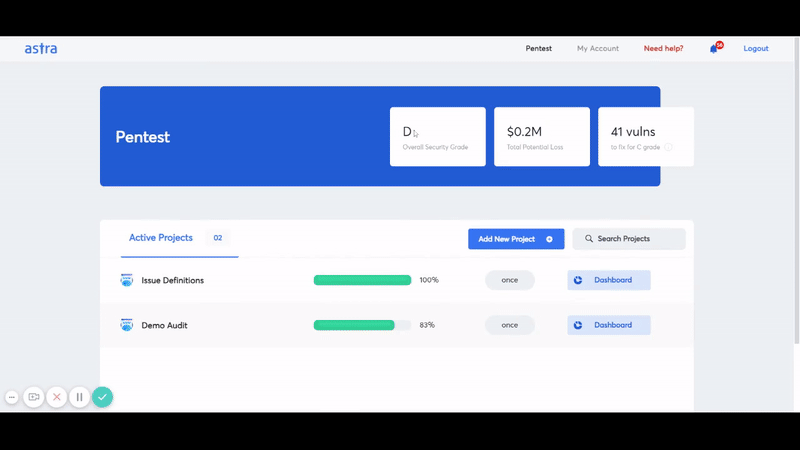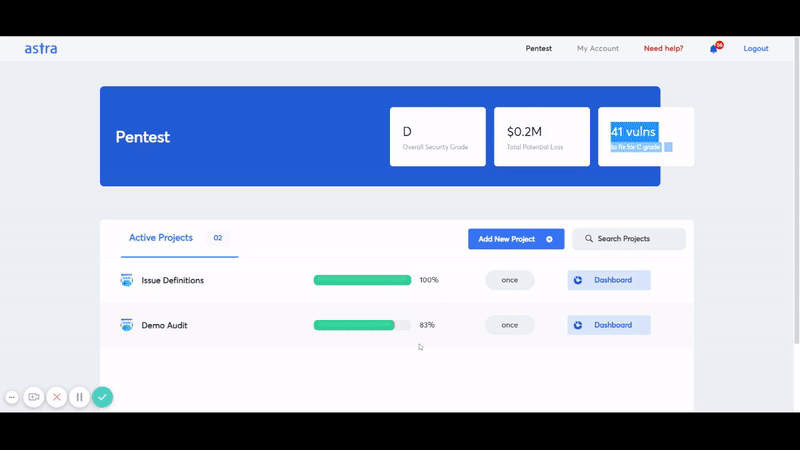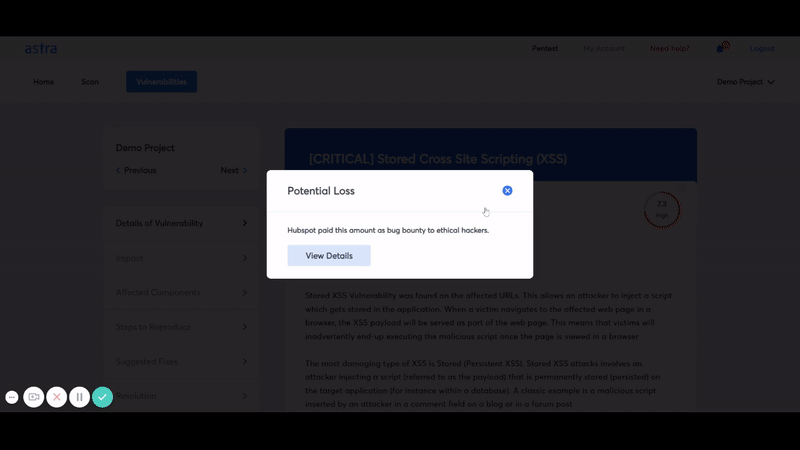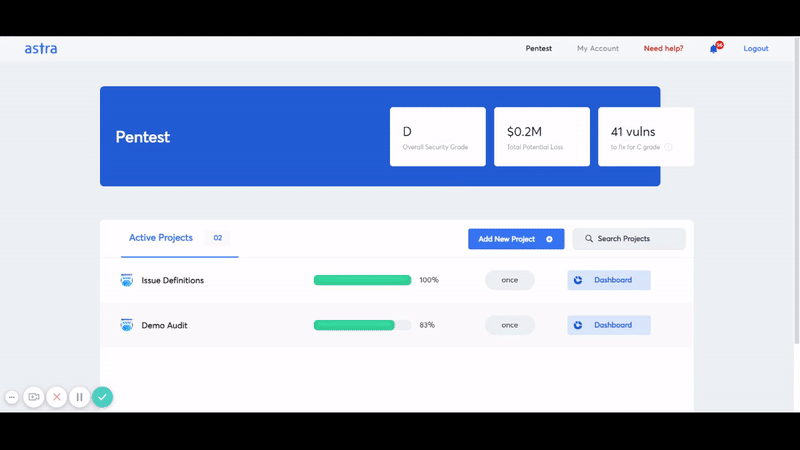
It is an AWS cloud penetration testing tool that allows you to pentest your AWS services and look for potential vulnerabilities. It offers an interactive dashboard where you can monitor the audit trail and see the detailed analysis for each discovered vulnerability along with the recommended steps to fix those vulnerabilities.
They also offer multiple integrations with the existing tech stack of your pentest project including GitHub, GitLab, Slack, Jira, and more. It also allows you to start automatic pentest with every feature update.
2. AWS Inspector
This service by AWS helps in the automation of vulnerability management through immediate scanning of AWS workloads to detect software vulnerabilities and exposure.
3. AWS Security Hub
This is a tool designed by AWS to automate security checks and centralize security alerts within the platform. It is concerned with security posture management across all accounts and regions.
4. Prowler
It is an open-source security testing tool that allows you to scan your AWS account for potential vulnerabilities, IAM permissions, and compliance based on a set of standard benchmarks such as the AWS Foundations Benchmark.
5. CloudSploit
It is an AWS pentesting tool that allows you to audit the configuration state of services in your AWS account. It checks for publicly exposed servers, unencrypted data storage, lack of least-privilege policies, misconfigured backup, restore settings and data exposure, and privilege escalation.
6. Cloudsplaining
It is an open-source tool for AWS IAM security assessment that allows you to identify violations of least privilege and generate a risk-prioritized report for evaluation.
AWS Penetration Testing Provider – Astra Security
As you would have gathered by now, AWS penetration testing is a serious undertaking involving complex processes and requiring specific knowledge. Performing a complete security audit by yourself for the first time can be difficult. But you don’t have to worry. Astra is here to help you out.
Astra Security is an AWS penetration testing company that performs a complete security audit of your application. We are a group of security experts who can provide an in-depth analysis of your AWS system. See our AWS Security Audit Program.
Astra Security provides its customers with an AWS pentesting checklist and a publicly verifiable AWS penetration testing certification.
Conclusion
Amazon Web Services (AWS) offers various integration opportunities to your application with some in-built security features for the security of the cloud. But the security in the cloud resides completely in your hands. Henceforth, performing penetration testing becomes more and more important every day for your business. You can go through the above guide to do it yourself. You can also get professional help from Astra Security.
If you have further queries on AWS penetration testing by Astra Security, chat with us with the chat widget. You can also contact us by dropping comments in the comment box and we will be happy to help you!

FAQs
Is penetration testing allowed on AWS?
Yes, penetration testing is allowed on AWS, but it requires prior authorization. AWS offers guidelines and processes for conducting penetration testing to help ensure security without disrupting services or violating terms of service. However, tests involving Command and Control (C2) necessitate prior approval.
What is the difference between cloud security and penetration testing?
Cloud security encompasses infrastructure and service protection, while cloud penetration testing assesses cloud-based app and infrastructure security. It identifies vulnerabilities, risks, and offers a remediation plan. Cloud providers secure infrastructure, customers secure accounts, apps, and data.
















