Joomla, one of the world’s most popular CMS powering over 3.3% of world’s websites, recently patched a critical vulnerability which has persisted in its content management system for 8 years. Leveraging this vulnerability could allow an attacker to steal administrator login credentials, paving way for further key information theft. This appalling revelation reveals the vulnerable state of CMSs which often go undetected and can pose a huge threat to users.
The German security firm RIPS Tech discovered the vulnerability: CVE-2017-14596, which was ultimately patched up in the recent version Joomla 3.8. The fix targets improper input sanitization in the LDAP authentication plugin, which affects Joomla versions 1.5.0 through 3.7.5. Below is a PoC video made by Ripstech security researchers and originally published on their blog.
LDAP Injection Vulnerability
Termed by researchers as the LDAP injection vulnerability, this allows an attacker to use the login controller to his advantage through the Joomla login page. Once the attacker gains control of the admin control panel, he can potentially take over the Joomla running site and the web server by enforcing remote code execution.
Following code snippets reveal the code lines spanning the vulnerability:
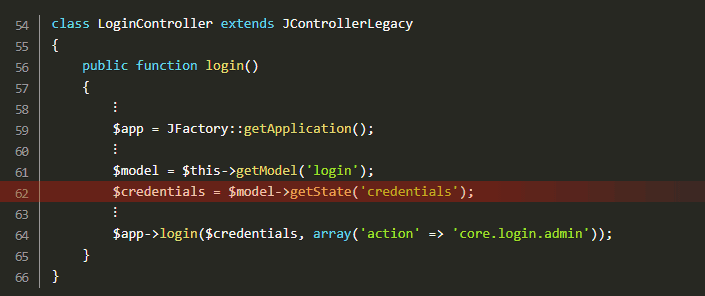
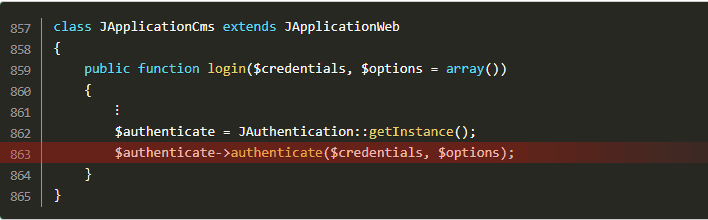
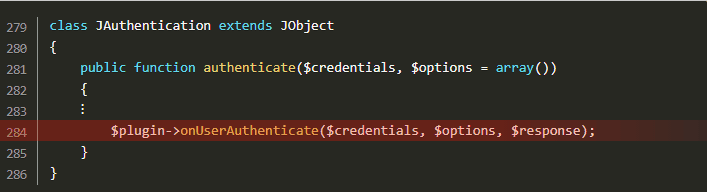
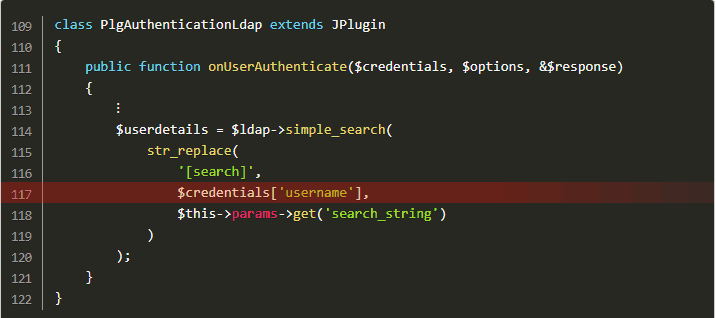
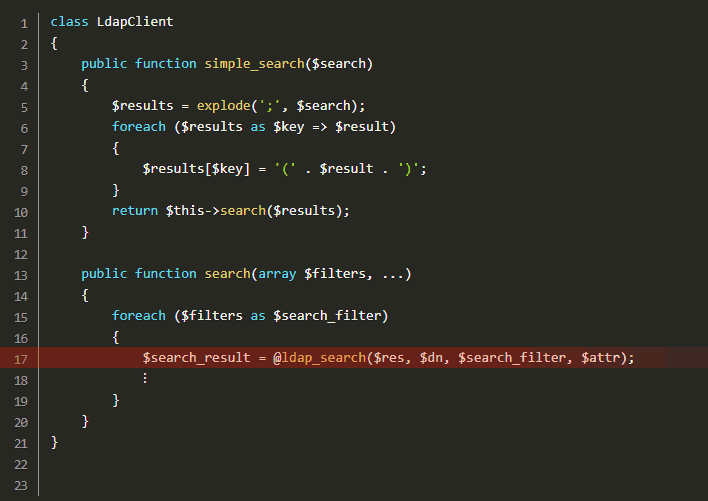
All the attacker needs to do is inject LDAP query syntax into the credentials, thus modifying the LDAP query. By using wildcard characters (.MP4) and noting authentication error messages, the attacker can modify requests and guess credentials.
The LDAP server is similar to the SQL database. While it is not widely used as the default authentication, some large organization do connect their sites to the LDAP server. This serves as an attractive target for malicious users looking to steal user credentials.
The Fix
The LDAP Injection Vulnerability is now addressed in Joomla 3.8 and is applicable to those accounts configured to use this plugin. Lack of input sanitization is one of the most common vulnerabilities faced by most CMS. It is advised to follow OWASP security guide for Testing Input Validation to secure your site against code execution attacks. Furthermore, Astra firewall can be a great value add to your Joomla website, contact us to secure your website against such attacks.
















