Azure security refers to the safeguards implemented by Microsoft Azure to protect the information and services hosted on its cloud platform. Azure security offers a safe environment for using cloud services, storing data, and executing applications, assisting enterprises in meeting regulatory requirements. Azure security assessment tools test your cloud architecture to find data and identify hazards, their potential effects, and their likelihood of occurring.
Assessments check compliance, identity, and access management, network security, storage and access controls, and incident response plans.
These assessments aim to identify any security gaps, non-compliant configurations, and weak controls to reduce the risk of a security breach in your Azure environment.
What is the Azure security assessment?
The Azure security assessment is a process that helps organizations identify and address potential security gaps in their Azure deployments. The key benefit is that it gives organizations confidence that their Azure deployments follow security best practices and minimize exposure to threats and data breaches.
Microsoft Azure Responsibility
Microsoft is responsible for securing the cloud infrastructure that runs Azure services. This includes the physical security of the data centers, networking infrastructure, and virtualization layer.
The Azure Security Framework takes responsibility for security settings for Azure’s managed services, including Azure Kubernetes Service (AKS), Container Instances, Cosmos DB, SQL, Data Lake Storage, Blob Storage, and others.
Customer Responsibility
Customers of Azure are in charge of the security in their cloud, or, to put it another way, everything that they instantiate, create, and use.
The customer is responsible for securing account credentials, applications running on Azure, virtual machines, application code, and data within their Azure subscription.
Top 7 Azure security assessment tools
- Astra Security
- Qualys Cloud Platform
- Nessus
- OpenVAS
- Rapid7 InsightVM
- Trustwave AppDetectivePRO
- Alert Logic
1. Astra Security
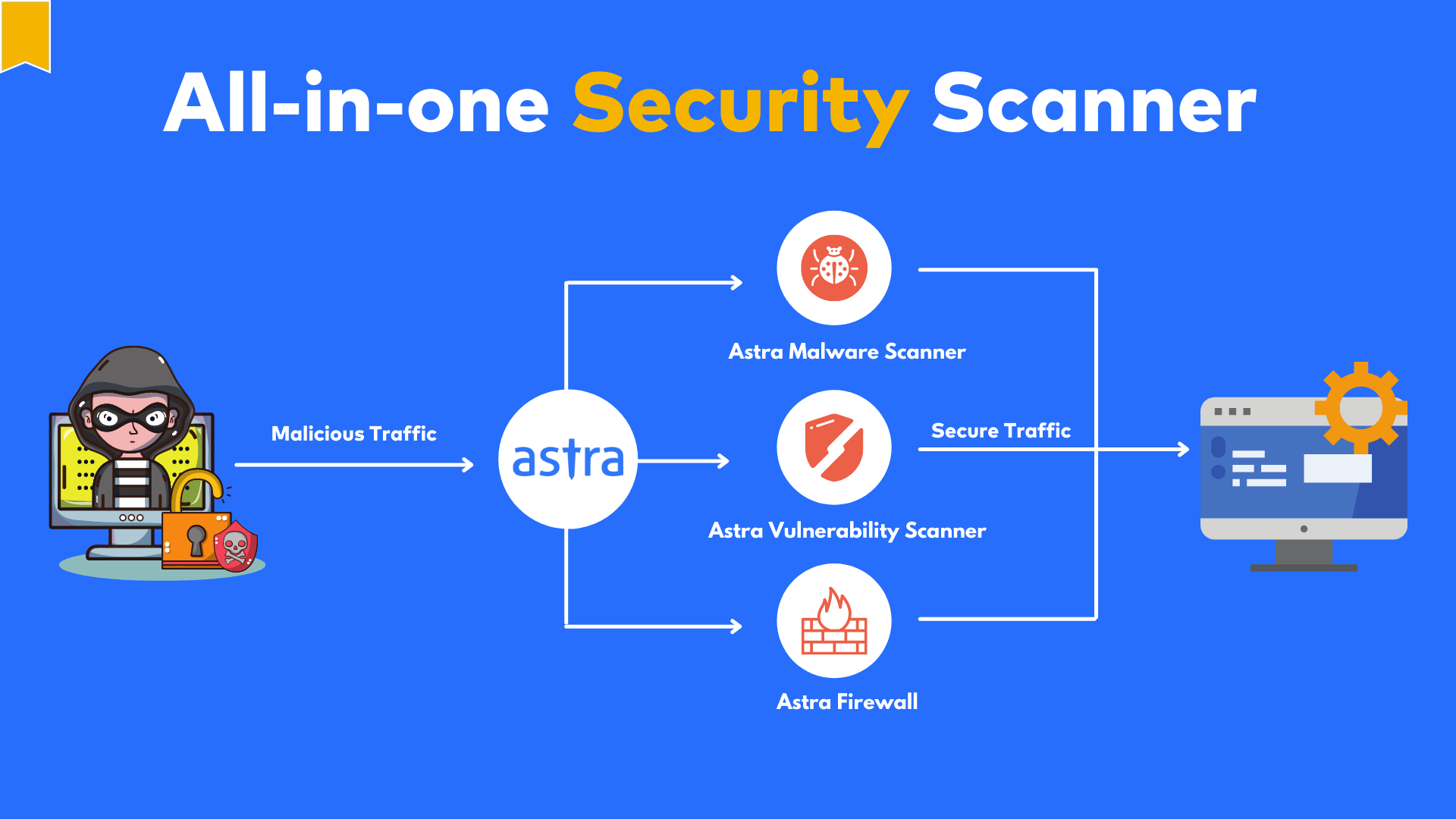
Astra Security is one of the major Azure security assessment tools that provides automated Azure security assessment and remediation of Azure infrastructure.
Astra continuously scans for vulnerabilities, malware, and misconfigurations across Azure resources like VMs, storage, web apps, and networks.
Astra Security provides actionable reports with risk scores based on CVSS and contextual data that are simple to understand.
Astra uses a sizable, dynamic database of known CVEs, intelligence-based vulnerabilities, the OWASP Top 10, and SANS 25 in its Azure cloud security assessment.
Features
- Integrations: Azure, Jenkins, GitHub, GitLab, JIRA, etc.
- Compliance scans: PCI-DSS, GDPR, HIPAA, SOC2, and ISO 27001
- Pentest types: Manual and automated
What is good?
- 24×7 customer support
- Zero false positive assurance.
- Actionable VAPT reports
Disadvantages
- No free trial
- It could have more integrations.
2. Qualys Cloud Platform
Qualys Cloud Platform is one of the Azure security assessment tools delivers comprehensive analytics and continuous monitoring for the Azure cloud.
Qualys automates vulnerability management, compliance monitoring, and security configuration assessments for workloads across on-premises and Azure cloud infrastructures.
Azure Connector by Qualys uses its continuous synchronization mechanism to carry out asset discovery for your cloud.
Qualys obtains all resource groups for a subscription using Azure APIs and lists all virtual machines for the chosen resource group.
Features
- Sensors: remotely deployable, centrally managed, and self-updating
- Reporting: Download vulnerability and compliance reports
- Scanning methods: Agentless, no-touch, API- and snapshot-based scanning
What is good?
- Scheduled scans
- Automated reporting
- Cloud asset management
Disadvantages
- Customer support can be improved.
- Specific tasks need to be automated.
- Navigation is complex.
3. Nessus

Nessus is a proprietary vulnerability scanner that can conduct Azure security assessments.
Nessus audits for vulnerabilities, configuration issues, and malware across the virtual machines, networks, and storage in Azure deployments.
The Microsoft Azure Cloud environment can be audited using Nessus to find misconfigurations in the cloud environment and account settings.
It provides remediation guidance and options to schedule automated scans.
Features
- Essential and password-based authentication methods
- Pre-built templates and policies
- Offline vulnerability assessment using live results
What is good?
- Wide coverage of vulnerabilities
- Low false positives.
- A holistic view of the complete environment.
Disadvantages
- Reporting could be improved.
- Access for multiple users can be improved.
- The potential for automation exists.
4. OpenVAS
The OpenVAS Azure Assessment tool is designed to help identify security vulnerabilities in the Azure environment and provide a comprehensive report of potential issues.
The OpenVAS Microsoft Azure security Assessment tool scans the Azure environment for known vulnerabilities using an extensive database of tests.
It checks for vulnerabilities in operating systems, web applications, databases, and other components of the Azure infrastructure.
The tool also checks for compliance with industry standards such as PCI-DSS, HIPAA, and ISO 27001.
Features
- Compliance with industry standards like PCI-DSS, HIPAA, and ISO 27001
- Customizable scan scheduling
- Integration with other vulnerability scanners
What is good?
- Free and open-source
- Scan for a wide range of vulnerabilities.
- Generate detailed reports.
Disadvantages
- Scan time can be reduced.
- Potential for false positives
- Support options can be increased.
5. Rapid7 InsightVM
Rapid7 InsightVM Platform provides data collection, visibility, analytics, and automation to establish a shared point of view between security, IT operations, and DevOps teams.
InsightVm is one of the major Azure security assessment tools that automates penetration testing to identify vulnerabilities and configuration risks in Azure deployments.
The Security Console is used to create sites, run scans, and generate reports, and is accessible via a web interface using any browser.
InsightVM provides analytics, scanning, and remediation capabilities for VMs, networks, containers, and web apps across on-premises and Azure.
Features
- Scan engines: Local, distributed, AWS, and Azure
- Automated containment: Reduce exposure to vulnerabilities
- Goals and SLAs: Allow tracking of service level agreements and plans.
What is good?
- Asset organization in groups.
- Pre-defined scan templates
- Highly customizable
Disadvantages
- More API calls need to be made.
- Customer support could be improved.
- Reporting has scope for enhancement.
6. Trustwave AppDetectivePRO

Trustwave AppDetectivePRO audits web applications and APIs in Azure App Service environments.
It is one of the Azure security assessment tools that performs static and dynamic scanning to detect vulnerabilities like XSS, SQLi, CSRF, and logic flaws in web apps.
Trustwave’s Azure testing tool is specifically designed to scan Azure SQL databases and identify security vulnerabilities, misconfigurations, and compliance issues.
It can comprehensively assess the Azure SQL environment and provide organizations with a detailed report of potential security risks and how to address them.
Features
- Adaptable DAM policies to keep an eye on the essential things
- Compliance checks for PCI DSS, HIPAA, and GDPR
- Access visibility and rights control
What is good?
- Prevents data exfiltration
- Automation of audits
- Continuous monitoring
Disadvantages
- UI can be more intuitive.
- Support needs to be enhanced.
- The testing scope is limited.
7. Alert Logic
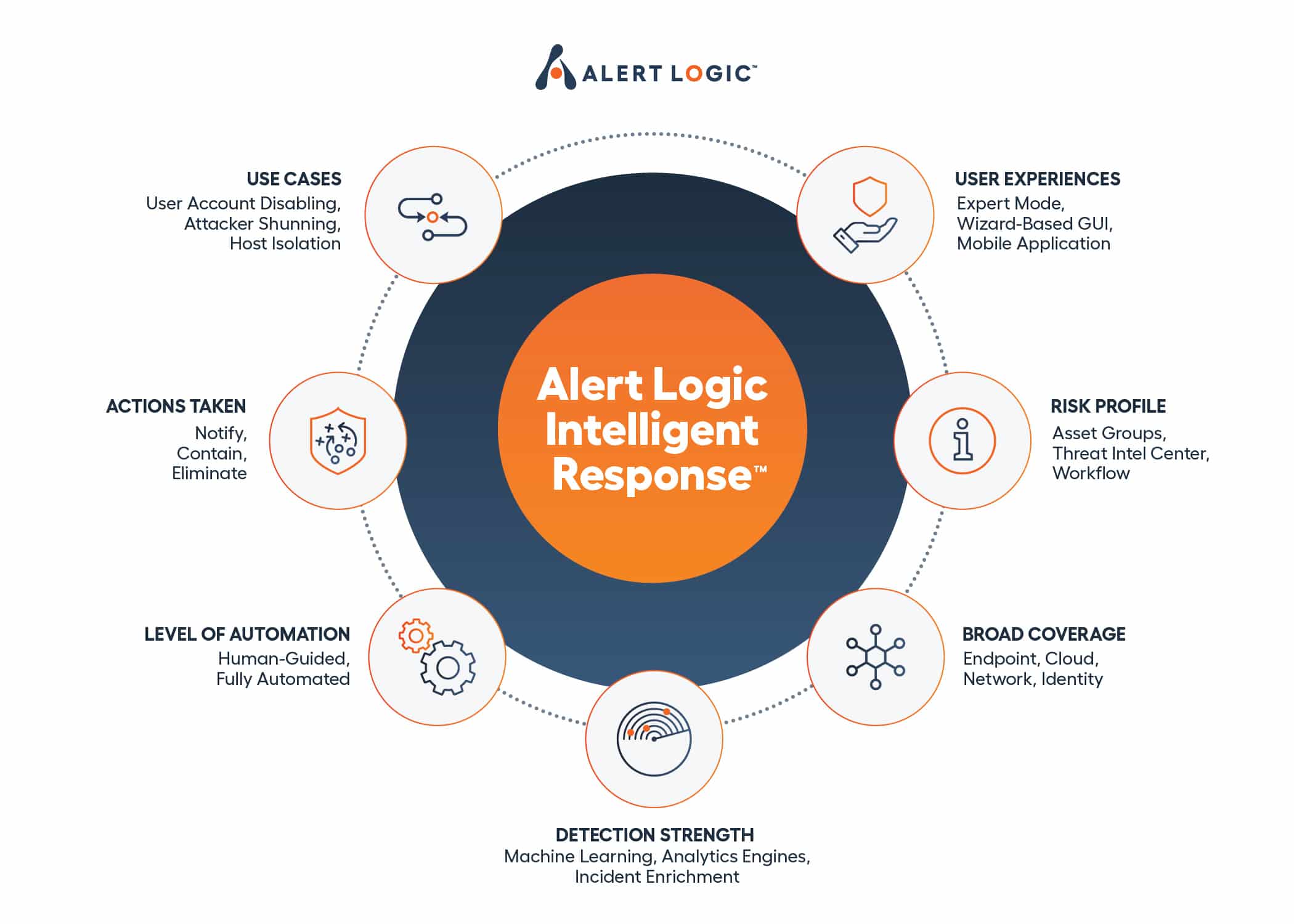
Alert Logic provides Azure security assessment services to assist businesses in strengthening their security posture.
Alert Logic finds flaws, spots security occurrences, examines log data, and ensures compliance with industry standards through vulnerability assessments, threat detection, log management, and compliance monitoring.
These services offer controlled detection and response capabilities, incident response support, and recommendations that may be implemented.
Alert Logic assists businesses in proactively identifying and addressing security issues in their Azure environments. This ensures the protection of crucial assets and the capability to manage possible threats efficiently.
Features
- Security consulting: To help businesses with their security strategy, architecture design, and Azure deployments, Alert Logic offers security consulting services.
- Reporting: Organizations can view incident patterns, compliance status, and valuable insights for improvement according to Alert Logic’s extensive reporting and analytics.
- Visibility: Unified visibility in a single-pane view
What is good?
- Comprehensive Protection
- Compliance Assurance
- Continuous Monitoring
Disadvantages
- Limited Customization
- Dependency on Third Party
- Integrating its services takes more time
How To Choose The Best Azure Security Assessment Tools
Reputation and experience
The Azure security assessment tools must have a good reputation in the industry.
A good Azure security assessment solution can be selected by checking reviews and ratings from other users to understand the tool’s reliability and effectiveness.
Also, you can look for a tool that has been around for a while and has a proven track record of delivering security assessments.
Features
A comprehensive set of security assessment features makes Azure security assessment tools attractive.
The tool should include vulnerability scanning, penetration testing, compliance checking, and risk assessment.
The best Azure security tools should cover all areas relevant to your organization’s security needs.
Customer support
When choosing Azure security assessment tools, look for a vendor with a dedicated support team available 24/7 to help with any issues you may encounter.
Additionally, check whether the vendor offers employee training and proper documentation to help you get the most out of the tool.
Detailed reports
Reports are essential to gain a deep understanding of the vulnerabilities present in the environment and accordingly prioritize remediation efforts.
Choosing a tool that provides actionable insights that can remediate vulnerabilities to help you improve your security posture is essential.
User Interface
Good Azure security assessment tools should be easy to use and navigate, even for non-technical users.
The best Azure security assessment tools have an intuitive user interface, and it should be easy to find the features and functions you need. The navigation should be consistent throughout the agency.
Intuitive Dashboard
An intuitive dashboard can make it easier to access the tool’s features and get a quick overview of its security posture.
Perfect Azure cloud security assessment tools provide a customizable dashboard that allows you to focus on the most critical areas of your organization.
Features of Azure security assessment tools
1. Vulnerability Scanning
Azure security assessment tools use automated scanning techniques to identify vulnerabilities in an organization’s IT environment.
The Azure security assessment checklist checks operating systems, applications, and other software vulnerabilities.
The scanning process is designed to be non-intrusive and can be performed regularly to ensure that new vulnerabilities are identified as they are discovered.
2. Threat Detection and Monitoring
Threat detection and monitoring are critical for organizations that want to proactively identify security threats and respond quickly to mitigate their impact.
Azure security assessment tools use a combination of techniques to detect and monitor potential threats in an organization’s IT environment.
The Azure security assessment tools can also use machine learning and artificial intelligence algorithms to identify patterns of behavior that may indicate a security breach.
3. Reporting
Organizations receive thorough reports describing vulnerabilities and configuration errors discovered in the Azure environment through reporting and suggestions in the Azure security assessment tools.
To address identified risks and enhance security, these reports evaluate concerns according to their importance and include actionable recommendations, best practices, and compliance requirements.
They allow businesses to prioritize remediation activities, evaluate their security posture in Azure continuously, and make educated decisions.
4. Compliance Assessment and Documentation
Azure security assessment tools can generate reports and documentation that help organizations demonstrate compliance with industry standards and regulations.
Compliance documentation includes the status of an organization’s compliance with GDPR, HIPAA, PCI DSS, and other industry regulations and standards.
A compliance assessment is critical for organizations to stay current with the most recent security best practices and uphold regulatory compliance.
It assists organizations in evaluating their security posture, identifying vulnerabilities, implementing necessary controls, and demonstrating compliance with industry regulations and standards with the help of Azure security assessment tools.
5. Remediation Recommendations
Enterprises must appropriately prioritize their efforts and allocate resources to address the most urgent security threats.
Remediation recommendations involve advice on installing security measures, changing configuration settings, and applying software patches.
The advice is based on best practices in the industry, and it can be altered to fit an organization’s particular requirements.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Importance of Azure Security Assessment Tools
- Vulnerability detection: Azure security assessment tools are critical for identifying vulnerabilities and security risks in an organization’s Azure environment. Organizations can proactively mitigate risks and protect their data and applications from cyber threats by identifying these vulnerabilities.
- Risk Assessment: Azure security assessment tools can assess the risk associated with different components of an organization’s Azure environment. These Azure security assessment tools can provide a risk score for each component based on factors such as the sensitivity of the data stored on the element, the level of access control in place, and the number of recent security incidents associated with the component.
- Compliance and Regulatory Requirements: Organizations ensure compliance with industry regulations and standards such as HIPAA, PCI-DSS, and GDPR with the help of Azure security assessment tools. The tools can scan an organization’s Azure environment and identify areas where they may fall short of compliance requirements.
- Security Automation and Integration: Azure security assessment tools automate the security assessment process, saving organizations time and money compared to manual methods. Automating and integrating security operations enables organizations to detect and respond to security incidents more quickly, minimizing the impact of any potential breaches.
- Cost-saving and time-efficient: By automating the security assessment process, Azure security assessment tools can save businesses time and money. In contrast to manual procedures, these security tools can assist organizations in identifying security threats more quickly and effectively, freeing up resources for remediation actions.
Cloud Security Assessment Considerations for Azure
Here are some common considerations for Azure when conducting assessments:
- Identity and Access Assessment: To ensure that only authorized users can access resources, this assessment looks at the efficiency of authentication mechanisms and multifactor authentication settings.
- Network Security Assessment: In network configurations, firewalls, and virtual network settings, the assessment checks for vulnerabilities.
- Data Security Assessment: To ensure that sensitive data is adequately protected, this assessment includes an analysis of the encryption practices, classification, and access controls.
- Compliance and Governance Assessment: This assessment ensures compliance with the regulatory requirements and data protection and safety, ensuring appropriate controls and procedures are in place.
Conclusion
A critical step towards protecting your Azure environment is to undertake a security assessment. You can reinforce your security posture and protect against possible threats by knowing how the process operates, what types of evaluations are carried out, and practical issues.
What are the most common issues in Azure Security?
1. Misconfigured Security Settings: Vulnerabilities can be caused by incorrectly developed security controls such as improperly configured firewall rules, access control lists, and network security groups (NSGs), which could allow unauthorized access or expose critical resources.
2. Insufficient Data Encryption: Default encryption of VM drives is not available on Azure, which may pose a security risk. Users of Azure should enable and activate the disk’s encryption.
3. Lack of Logging and Monitoring: Inadequate logging and monitoring practices can make it difficult to detect and respond to security incidents on time, thereby allowing threats to be noticed.
4. Insecure Application Development: Attacks such as SQL Injection or Cross-Site Scripting can occur due to weaknesses in applications run by Azure, like insecure practices or a lack of input validation.
What are cloud security assessment considerations for Azure?
1. Identity and Access Assessment: To ensure that only authorized users can access resources, this assessment looks at the efficiency of authentication mechanisms and multifactor authentication settings.
2. Network Security Assessment: In network configurations, firewalls, and virtual network settings, the assessment checks for vulnerabilities.
3. Data Security Assessment: To ensure that sensitive data is adequately protected, this assessment includes an analysis of the encryption practices, classification, and access controls.
4. Compliance and Governance Assessment: This assessment ensures compliance with the regulatory requirements and data protection and safety, ensuring appropriate controls and procedures are in place.
What is the process of Azure security assessment using Azure security assessment tools?
1. Identify the Azure resources and data that require security evaluation.
2. Analyze storage security configurations, data classification and protection methods, Azure Key Vault usage, and data encryption.
3. Set up Log Analytics and Azure Monitor to gather and examine security logs for identifying and looking into security incidents.
4. As new threats and vulnerabilities appear, constantly check for updates to security controls, configurations, and policies.
5. To identify and mitigate threats quickly, evaluate the configurations of the Azure Security Center, the threat detection policies, and the incident response capabilities.
6. To improve security posture and decrease vulnerabilities, comply with Azure security best practices, standards, and recommendations.