Over 700 WordPress and Joomla Websites have been infected with the ionCube malware that disguises as legitimate ionCube-encoded files.
IonCube is an old and powerful PHP Encoder which is used for to encrypt and protect files with PHP encoding, encryption, obfuscation and licensing capabilities. Owing to licensing costs, ionCube isn’t generally a contender for malicious uses.
However, attackers found a way to masquerade their malware resembling that of ionCube-encoded files to compromise various websites. Among the affected ones were sites based on WordPress, Joomla, and CodeIgniter. The malware allows hackers to create a backdoor on vulnerable websites, therefore resulting in data theft from vulnerable site users.
Signs of ionCube Malware Infection
Researchers discovered over 7000 fake ionCube files with innocuous names running on PHP servers. According to researchers, while few lines exist in the legitimate ionCube file, such was not the case for the fake ones. Moreover, every legitimate Ioncube file references to the ioncube.com domain. Such was not the case in the fake files
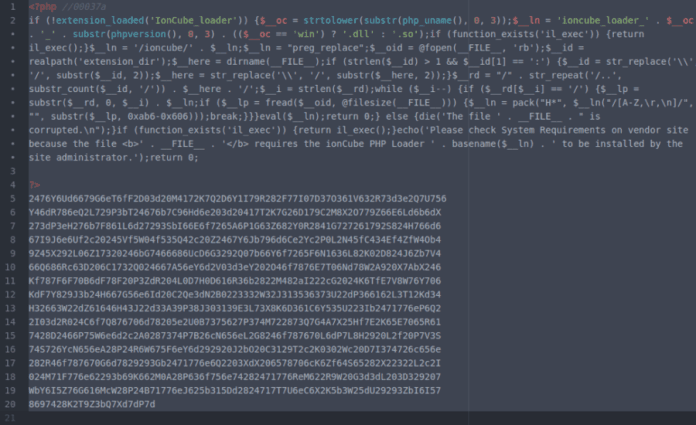
This is how a fake ionCube file looked like.
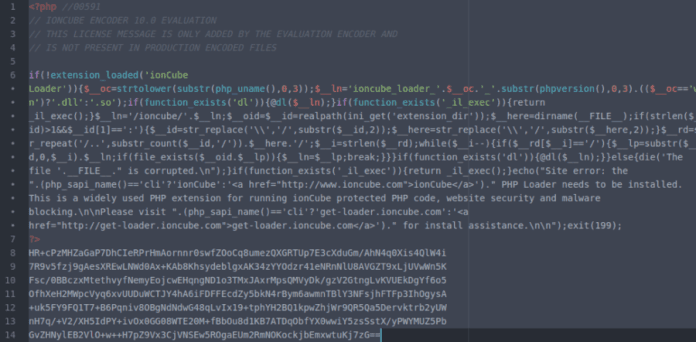
Whereas a legitimate ionCube file looks like this:
Additionally, researchers discovered code blocks after the PHP closing tags consisting of only alphanumeric characters and newlines, unlike the real file. According to researchers:
“While there’s still some degree of obfuscation, the presence of the $_POST and $_COOKIE superglobals and the eval request at the end of the file reveal its true purpose: to accept and execute remotely supplied code. It looks like the remote code supplied to this file is further obfuscated and there may be some sort of access control implemented, judging by the GUID-formatted string present.”
An investigation revealed the discovery of 700 infected sites, totaling over 7,000 infected files. PHP files such as “diff98.php” and “wrgcduzk.php” which were basically suspicious obfuscated files, appeared almost identical to the legitimate ionCube-encoded files.
On decoding, the fake ionCube file comprises of the ionCube malware. Theoretically, the injected malicious code can infect any website based on a web server running PHP.
How to Mitigate?
It can be difficult to differentiate between the fake and legitimate ionCube files, given a large number of malware variations out there. Moreover, if the developer hasn’t specifically installed ionCube-encoded files but finds such files on their servers are likely infected. It is common to see up to 100 slightly different variants of the malware on a single site. Moreover, cross-compatibility with different versions of PHP is minimal, reducing the viability of use as malware.
The ionCube Malware can be mitigated. Researchers recommend administrators to check the presence of ionCube-encoded files as an indicator of compromise. On positive detection, in order to completely eliminate the threat, a site-wide scanning is mandatory along with adoption of a web application firewall (WAF).
Download our free Secure Coding Practices Checklist for Developers to ensure that your site abides by all aspects of coding security.
To further mitigate your website against such online threats, install Astra’s Web Security Firewall.