Cross-Site Scripting (XSS) attacks are stated as one of the most rampant occurring yet easily fixable injection attack faced by e-commerce businesses and a variety of other web applications. From targeting applications built on archaic web technologies to newer ones using rich, client-side UIs, XSS has plagued them all. However, it is imperative to realize that vulnerabilities posing as a potential cause for a XSS attack can be easily detected and fixed timely.
How does a Cross-site scripting attack occur?
A cross site scripting (XSS) attack occurs when
- A web application requests for input data through an unreliable source
- The dynamic content inputted via the web request is used without being corroborated for lack of malicious content.
A simple example of such input data is when we submit our name, e-mail ID, username-password or any input in a form. Each of the above entered inputs can be manipulated if the underlying code doesn’t properly validate the inputs. An attacker makes use of this inability to inject malicious content, usually in the form of a Javascript code, HTML or any form of code executable by the browser. The end user has no way of suspecting the unreliable script and will end up executing it. Once injected, the script gains access to any cookies, session tokens or sensitive info used by this site.
An XSS attack is of 3 types:
- DOM Based Attack: Caused by malicious injection of code from client side. The injected code can be Javascript, Flash, Visual Basic etc.
- Persistent XSS Attack: Caused when payload is stored on server side and gets retrieved when there is a user request to a page
- Non-Persistent XSS Attack: Caused when payload is reflected back to the user by opening a link to a vulnerable website with a crafted input.
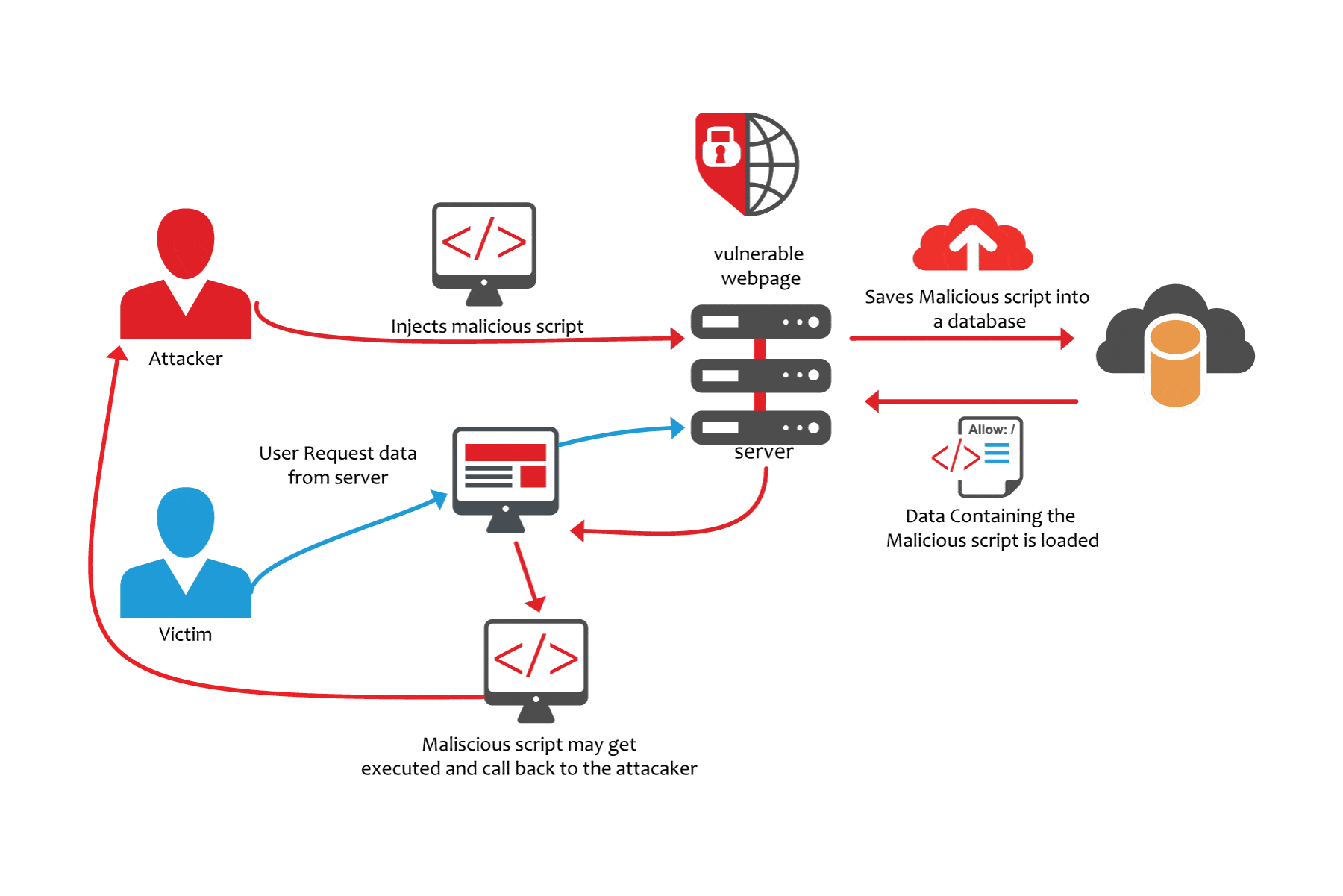
Anatomy of a Cross-site scripting (XSS) attack
How Attackers Exploit XSS?
- The attacker posts the following payload in the comment section.
- As soon as any legitimate users opens the comment box to see the following comment, HTML parses this script.
Notorious Cases of Cross-Site Scripting Attacks
XSS attacks mostly occur for financial gains, a notable one is the past attack against e-commerce giant eBay. The hackers injected a malicious Javascript code into several listings for cheap iphones, which in turn redirected users to a fake login page created to compromise user credentials.
Apart from e-commerce sites, several social media sites have been subject to such infamous attacks. Twitter was targeted with one such XSS worm that led to malicious links getting lodged on a website named StalkDaily. Another well- known XSS attack was the MySpace attack by the Samy worm – a benign virus which altered the profile page of MySpace users and sent random friend requests.
Precautions to Mitigate XSS Attacks
-
Input Validation
To prevent XSS, white-list most input to alphanumeric or in some cases, special characters. This will reduce surface attack and minimize the potential for bugs.
-
Use of secure DOM elements
Often, unsafe handling of DOM elements (document object model) lead to XSS attacks in even rich client UIs. For example, using the innerHTML attribute renders the user input as XSS with Javascript events. In this case, the safe alternative would be to use contentText or innerText.
-
JavaScript Escaping
Escaping single quotes can prevent injection within Javascript. HTML encoding that uses single quotes with ‘ should be used to prevent the injection issue
-
Output Encoding
Output encoding works wonders when it comes to neutralizing maximum XSS payloads. This method works to mitigate server side injection attacks. While HTML encoding is a rather common method, URL encoding can help obliterate any injections of markup in links and redirects.

















[…] cross site scripting (XSS) vulnerability came to light in the Magento Affiliate Plus extension rendering more than 7000+ stores vulnerable […]
[…] Cross-site Scripting (XSS) is a popular code injection vulnerability that allows a hacker to execute malicious JavaScript code into another user’s web browser. It’s risky because malicious JavaScript code can have drastic consequences like credit card hijacking, user information theft etc. […]
[…] Not Trust Those Inputs: Vulnerabilities like SQL Injection and Cross Site Scripting are one of the most exploited on web apps. Be it WordPress, Magento or OpenCart all have had cases […]
[…] add evil code. This is an easy way to get entry inside the website without doing much. Attacks like XSS and SQL injection are direct consequences of the lack of input sanitization. Recently, Joomla […]
[…] with its sites till now. The vulnerability of its sites getting infected lies mainly with the cross-site inscription(XSS). Still, it must not be forgotten that no site is completely hacked proof. Thus, this article […]