AWS maintains high-quality security mechanisms; however, the increasing complexity of cyberattacks today means that any data stored within AWS needs external evaluation to strengthen security measures against vulnerabilities.
AWS penetration testing involves carefully assessing the cloud infrastructure to find hidden vulnerabilities. It is conducted by skilled penetration testers. This procedure replicates real-world attack situations specific to AWS and finds weaknesses that could cause data breaches.
The testing process thoroughly evaluates setups, access restrictions, and network topologies. Its objective is to provide practical suggestions for strengthening AWS environments’ security posture and guaranteeing the protection of your assets in the cloud.
What Makes Astra the Best VAPT Solution?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- The Astra Vulnerability Scanner Runs 8000+ tests to uncover every single vulnerability
- Vetted scans to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities
- Astra pentest detects business logic errors and payment gateway hacks
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Like many cloud platforms, AWS uses a Shared Responsibility Model. This model splits cloud security: AWS secures the infrastructure, and you secure your data.
As such, we can categorize the security testing of an AWS platform into two parts:
1. Security of the Cloud
Amazon (AWS) is responsible for securing the cloud against possible vulnerabilities and cyber attacks to protect companies using AWS services. The security of the cloud includes all zero-days and logic flaws that can be exploited at any step to disrupt the performance of an AWS server.
2. Security in the Cloud
Security in the cloud refers to the responsibility of the user/company to make sure their
deployed applications/assets on AWS infrastructure are secured against any cyberattacks. A user/company can enhance the security of their applications on the AWS cloud by implementing necessary security practices.
Importance Of AWS Pentesting
- Maintaining Client Responsibility
Following the Shared Responsibility Model, you need to uphold the security of your assets within the AWS cloud infrastructure. By conducting AWS pentesting, users can secure data and workloads, prevent unauthorized access, and maintain the overall security posture to reduce the risk of data breaches.
- Meeting Compliance Requirements
Several industry regulations and standards, such as HIPAA, ISO 27001, and SOC2, regard the safety of the data on your AWS cloud as critical, and it’s vital to meet these legal requirements. It’s also beneficial to establish data security as a top priority in the eyes of your customers. AWS pentesting helps you resolve vulnerabilities to comply with these regulatory requirements.
- Complete Cloud Security Assurance
AWS constantly updates its systems, so a penetration test that specifically looks for vulnerabilities like insecure APIs or configurations, weak authentication, and data exposure is vital. All areas of cloud security, including newly discovered threats and vulnerabilities, need to be carefully examined and addressed.
AWS Penetration Testing Checklist
Penetration testing within the AWS environment comes with its own set of intricacies, demanding a systematic and methodical approach to ensure thorough security evaluation of all three components covered, namely – Considerations, Preparations, and Steps. Here’s a detailed AWS Penetration Testing Checklist to help you get started:
Off-Limit AWS Sections for Pentesting
While penetration testing is a valuable security practice, certain activities are off-limits within AWS, as they can disrupt services or violate AWS terms of service:
- Servers belonging to AWS
- Physical hardware, facility, or underlying infrastructure that belongs to AWS
- EC2 belonging to other vendors
- Amazon’s small Relational Database Service (RDS)
- Security appliances managed by other vendors
Types of AWS Pentesting
- Configuration Review
A configuration review involves scanning the AWS environment setup, access controls, network configurations, and regulatory compliance. It aims to identify weak access policies, misconfigurations, and regulatory compliance.
- Internal Audit
An internal audit assesses the security of AWS resources from within the organization’s network by simulating attacks and mimicking the actions of insider threats. It analyses the data encryption and data storage policies of the client’s AWS environment.
- External Audit
External audits involve simulated attacks from outside the organization’s network perimeter, mimicking cyberattacks. It tests the perimeter defenses and external-facing applications like web apps, API endpoints, and content delivery networks.
How to Perform Penetration Testing on AWS?
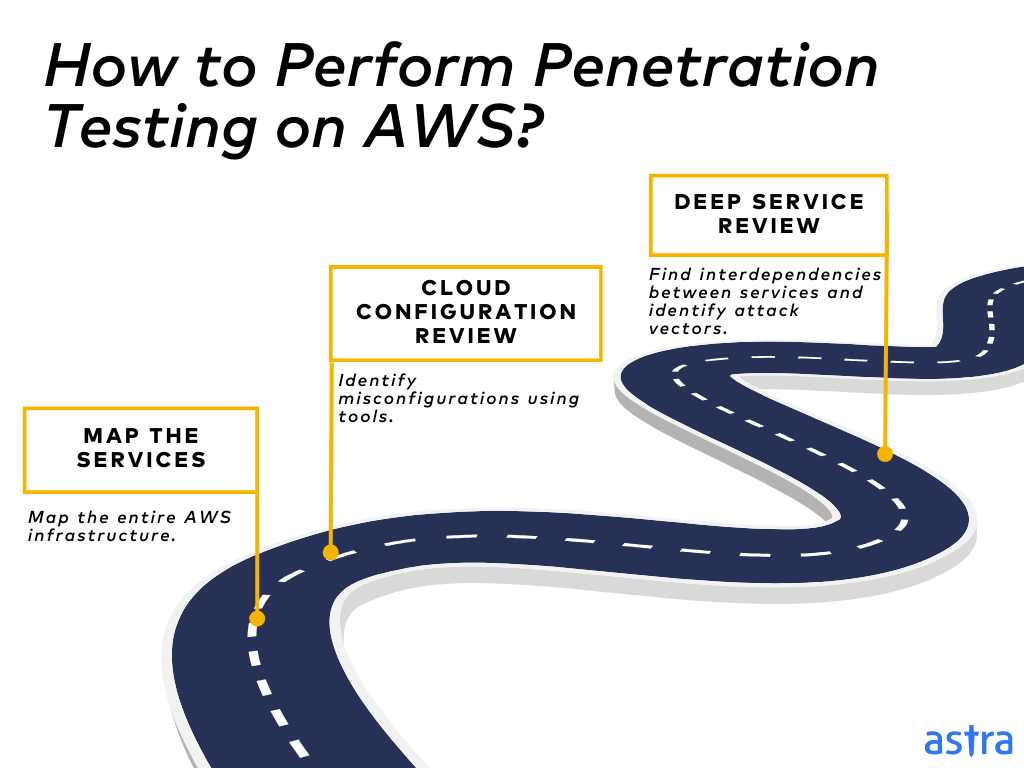
- Map the Services
The AWS penetration testing process starts by thoroughly mapping the entire AWS infrastructure to gauge the environment’s complexity and identify potential entry points for attackers.
The AWS environment’s components are mapped out by identifying EC2 instances, S3 buckets, IAM roles, RDS databases, Lambda functions, and VPC configurations. The relationships between these services are then analyzed to observe how data flows through the system.
- Cloud Configuration Review
The next step is to use tools like Scoutsuite or Prowler to conduct an automated review of all the AWS services to identify misconfigurations, open ports, or a lack of encryption.
As part of this process, security experts review parameters such as security groups, access control policies, and network configurations. Once these misconfigurations have been identified, you can formulate a remediation plan and implement AWS-recommended security controls to improve your data security.
- Deep Service Review
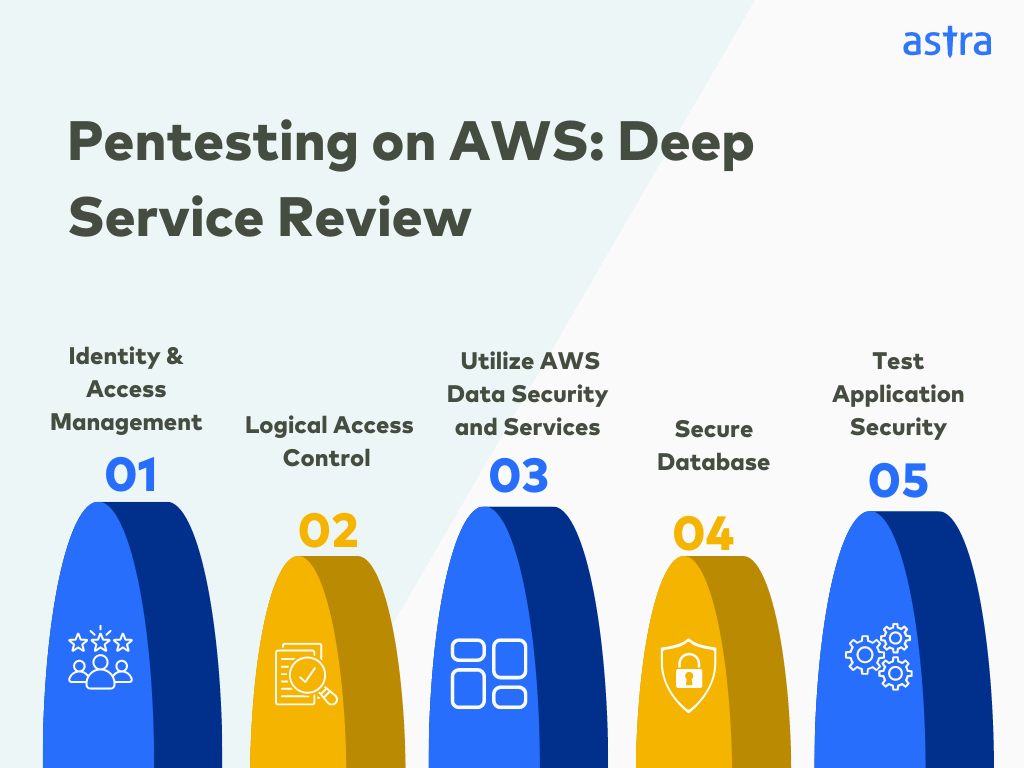
The third step would be to review each AWS service both individually and holistically within the entire infrastructure to find the interdependencies between services and identify potential attack vectors that may not be apparent in isolation. The steps involved in a deep service review are:
- Identity and Access Management (IAM)
A deep service review begins by identifying the assets of data stores and applications. In this step, the security expert implements two-factor authentication, removes keys from the root account, restricts permissions to service accounts, and deletes inactive accounts.
- Logical Access Control
Once you’ve identified assets, the next step is to manage access control on the cloud. Logical Access Control involves controlling access to resources, processes, and AWS users. You should also ensure that the credentials related to the AWS accounts are safe and secure.
- Utilize AWS Data Security and Services
AWS offers a range of services to manage and protect your data. You can employ these services to protect your data further:
- Amazon S3 – Simple Storage Service
S3 is a cloud folder generally known as a “bucket,” which is a storage server that delivers region exceptions, access logging, versioning, encryption, etc.
S3 provides SSE to encrypt data using AES-256 encryption and has access control lists that enable detailed control over who can access, modify, or delete data.
- Amazon EC2 – Elastic Compute Cloud
Users can launch and manage virtual servers to run applications using EC2’s resizeable compute capacity. EC2 instances also support secure communication protocols such as SSH (Secure Shell) and RDP.
The EC2 instances are logically isolated from each other within a virtual private cloud, which prevents unauthorized access and data leaks.
- Amazon EBS – Elastic Block Store
EBS provides block-level storage volumes for use with EC2 instances and supports encryption using a key management service to protect data.
IAM Policies and resource-based policies allow granular control over who can create, modify, and delete EBS volumes.
- Secure Database
The database is an important part of most web services. While performing the data audit, you should make sure to use the Multi-AZ deployment method and also limit access to specified IP addresses.
- Test Application Security
The hosted applications need to be thoroughly tested to identify and remediate vulnerabilities.
Security configurations, such as authentication, authorization, and data protection, should be applied to AWS Amplify services.
You can configure and manage AWS WAF rules to protect web applications from common exploits and attacks, such as SQL injection and cross-site scripting (XSS).
Understanding AWS Controls
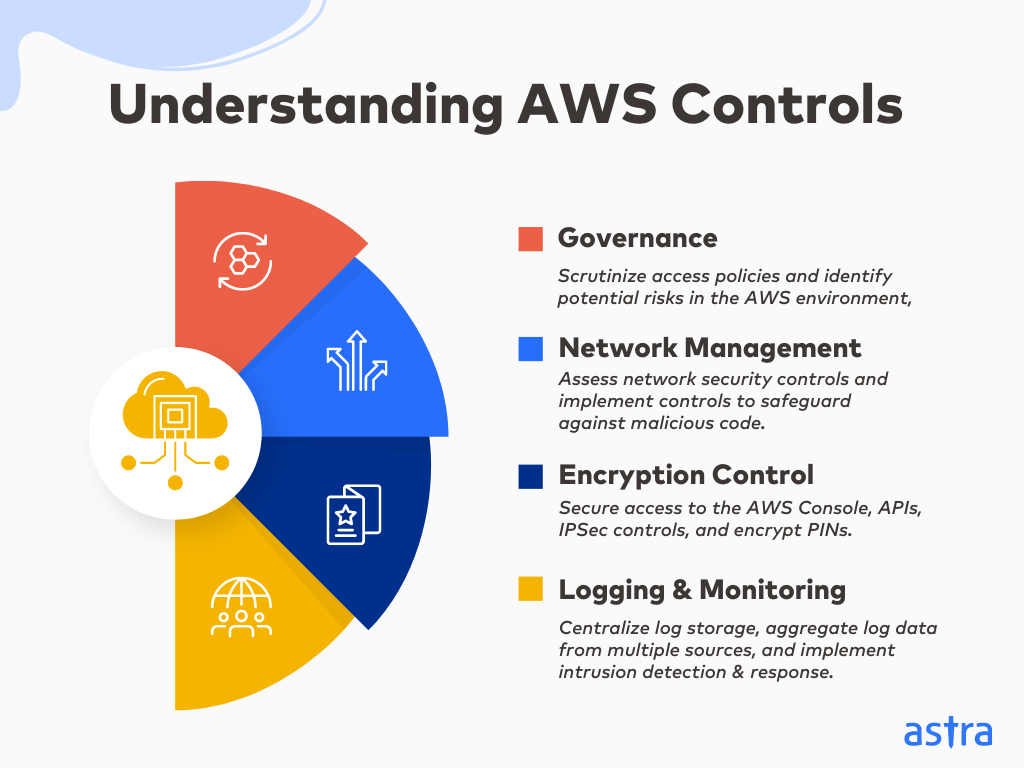
The AWS Pentesting process thoroughly tests the controls and configurations in the cloud. These controls include (but are not limited to):
a. Governance:
- Identify Assets & Define AWS Boundaries: Begin by clearly defining the scope of AWS assets and delineating boundaries for the assessment.
- Access Policies: Scrutinize access policies to ensure they align with security best practices and grant the appropriate permission levels.
- Risk Evaluation: Identify, review, and evaluate potential risks within the AWS environment, incorporating AWS into broader risk assessment frameworks.
- IT Security & Program Policy: Adhere to organizational guidelines and ensure that AWS usage aligns with IT security and program policies.
b. Network Management
- Network Security Controls: Assess network security controls to identify and rectify vulnerabilities or misconfigurations.
- Physical Links: Examine physical links to maintain the integrity of the network infrastructure.
- Granting & Revoking Access: Review processes for granting and revoking access rights to ensure timely and appropriate access management.
- Environment Isolation: Verify isolation of environments to prevent unauthorized access and lateral movement.
- DDoS Layered Defense: Evaluate DDoS mitigation strategies to protect against distributed denial-of-service attacks.
- Malicious Code Controls: Implement controls to safeguard against malicious code, including malware and exploits.
c. Encryption Control
- AWS Console Access: Secure AWS console access by implementing strong authentication and authorization mechanisms.
- AWS API Access: Ensure secure access to AWS APIs, safeguarding against unauthorized usage.
- IPSec Tunnels: Assess the security of IPSec tunnels, ensuring encrypted communication channels.
- SSL Key Management: Maintain robust SSL key management practices for secure data transmission.
- Protect PINs at Rest: Encrypt and protect Personal Identification Numbers (PINs) when at rest to prevent unauthorized access.
d. Logging and Monitoring
- Centralized Log Storage: Establish centralized log storage for comprehensive visibility into AWS activities.
- Review Policies for ‘Adequacy’: Regularly review logging policies to ensure they meet the adequacy requirements for security and compliance.
- IAM Credentials Report: Scrutinize Identity and Access Management (IAM) credentials reports to identify and rectify any suspicious or inappropriate access.
- Aggregate from Multiple Sources: Aggregate log data from multiple sources within the AWS environment for a holistic view of activities.
- Intrusion Detection & Response: Implement intrusion detection and response mechanisms to address security incidents and anomalies promptly.
AWS Penetration Testing Policy
Organizations need to have a well-defined AWS penetration testing policy in place. This policy should outline the rules, procedures, and expectations regarding penetration testing activities on AWS. Key elements of an AWS penetration testing policy include:
- Authorization Process: Clearly define the process for obtaining authorization from AWS or the AWS customer before conducting penetration testing.
- Scope and Objectives: Specify what is in scope and out of scope for testing, as well as the testing objectives.
- Testing Methods: Describe the testing methods and techniques that can be used, as well as any prohibited activities.
- Documentation Requirements: Outline the documentation and reporting requirements, including how findings should be documented and communicated.
- Compliance with Laws and Regulations: Emphasize the importance of compliance with relevant laws and regulations, including data protection and privacy laws.
- Incident Response: Include guidance on how to handle incidents or unintended disruptions that may occur during testing
- Retesting Procedures: Explain the process for retesting after vulnerabilities have been remediated.
AWS Penetration Testing Certification
AWS offers a penetration testing certification called the “AWS Certified Security-Specialty” certification. This certification covers various aspects of AWS security and can be quite lucrative for professionals in the field.
To achieve this certification, candidates are required to demonstrate their knowledge and skills in areas such as:
- Incident response
- Logging and monitoring
- Identity and access management
- Infrastructure security
- Encryption
- Penetration testing and vulnerability assessment
Tools Used in AWS Penetration Testing
Different sets of tools are available to pentest your AWS integrated services with different tests. Here are some of them:
1. Astra Security
Key Features:
- Platform: SaaS
- Pentest Capabilities: Continuous automated scans with manual tests
- Accuracy: Zero false positives
- Compliance Scanning: PCI-DSS, HIPAA, ISO27001, and SOC2
- Expert Remediation Assistance: Yes
- Workflow Integration: Slack, JIRA, GitHub, GitLab, Jenkins, and more
- Price: Starting at $1999/yr
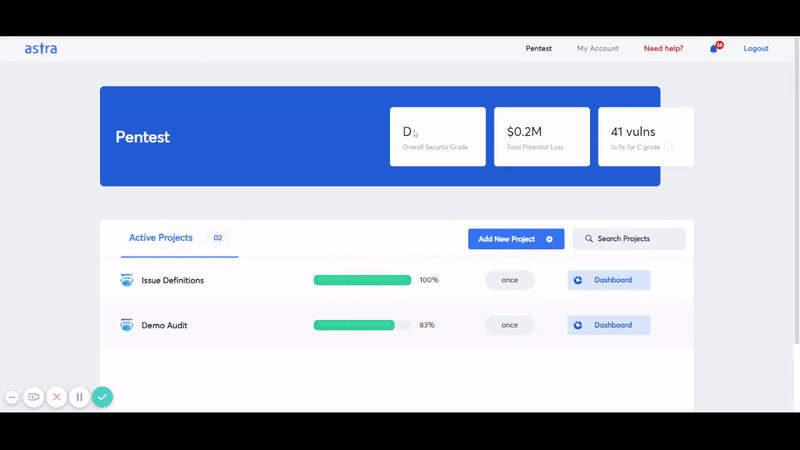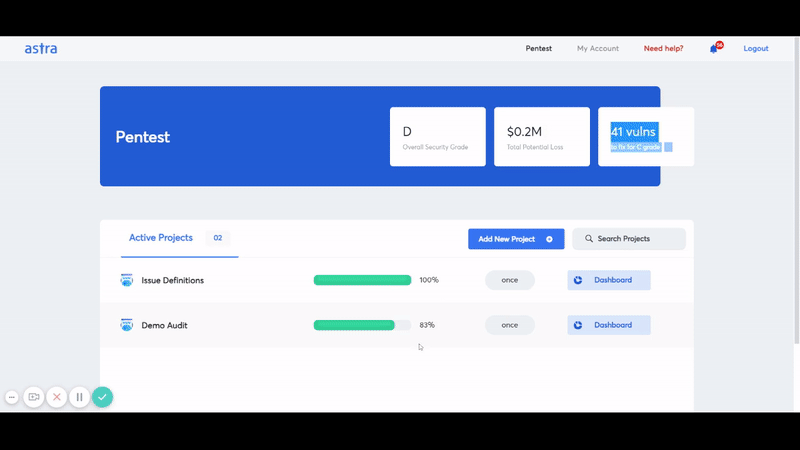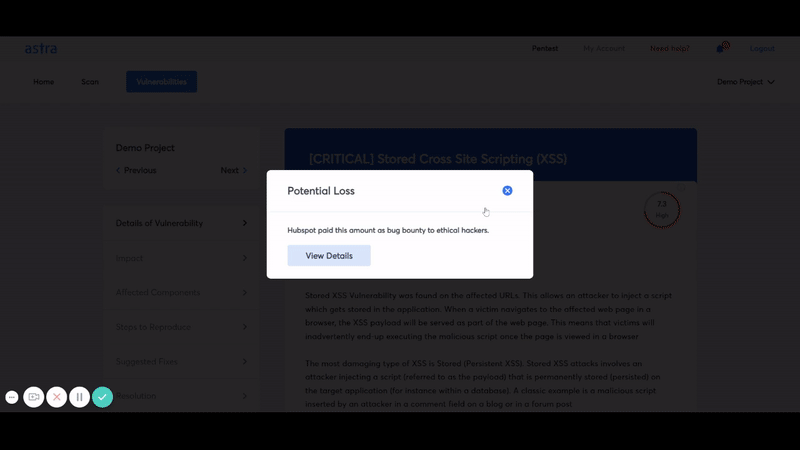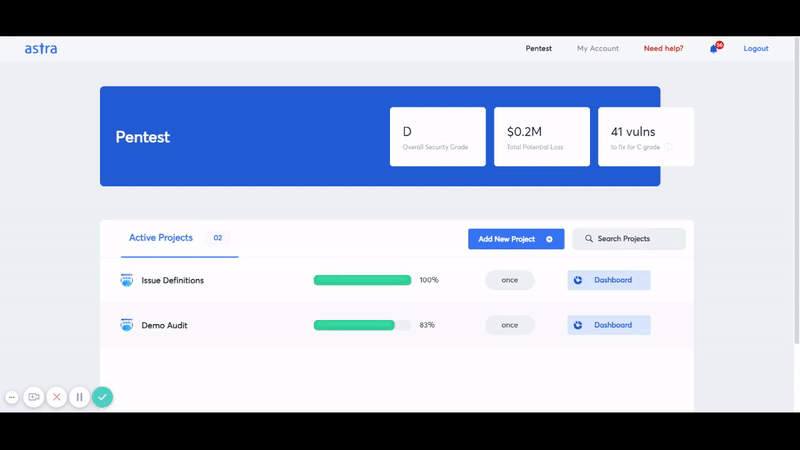
Astra Security is an AWS cloud penetration testing provider that allows you to pentest your AWS services and look for potential vulnerabilities. We offer an interactive dashboard where you can monitor the audit trail and see the detailed analysis for each discovered vulnerability and the recommended steps to fix those vulnerabilities.
Astra also offers multiple integrations with your pentest project’s existing tech stack, including GitHub, GitLab, Slack, Jira, and more.
2. AWS Inspector
Key Features:
- Platform: SaaS
- Pentest Capabilities: Automated security assessment service for EC2 instances
- Accuracy: Detection of vulnerabilities and security deviations
- Compliance Scanning: SOC, PCI, FedRAMP, HIPAA, and others
- Expert Remediation Assistance: No
- Workflow Integration: Integrates with other AWS services and tools
- Price: Pricing varies based on assessment type and frequency
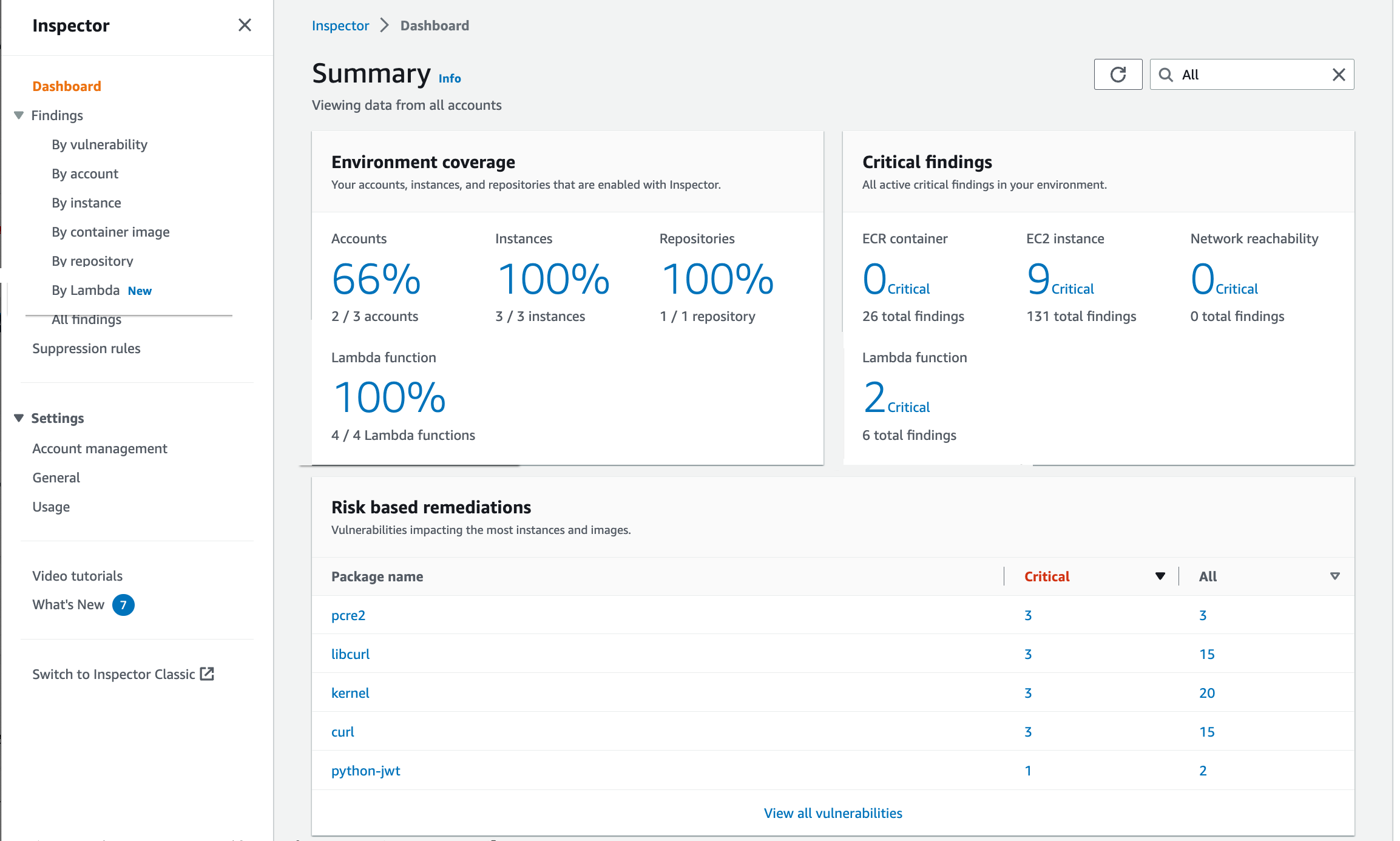
Amazon Inspector is an automated security assessment tool used by AWS to check EC2 instances’ network accessibility. Applications operating on the AWS platform are more secure because they find flaws and deviate from accepted practices.
AWS Inspector takes advantage of AWS’s security expertise by regularly adding the most recent security best practices and vulnerability descriptions to its knowledge base. The pricing for this service is based on assessment type and frequency.
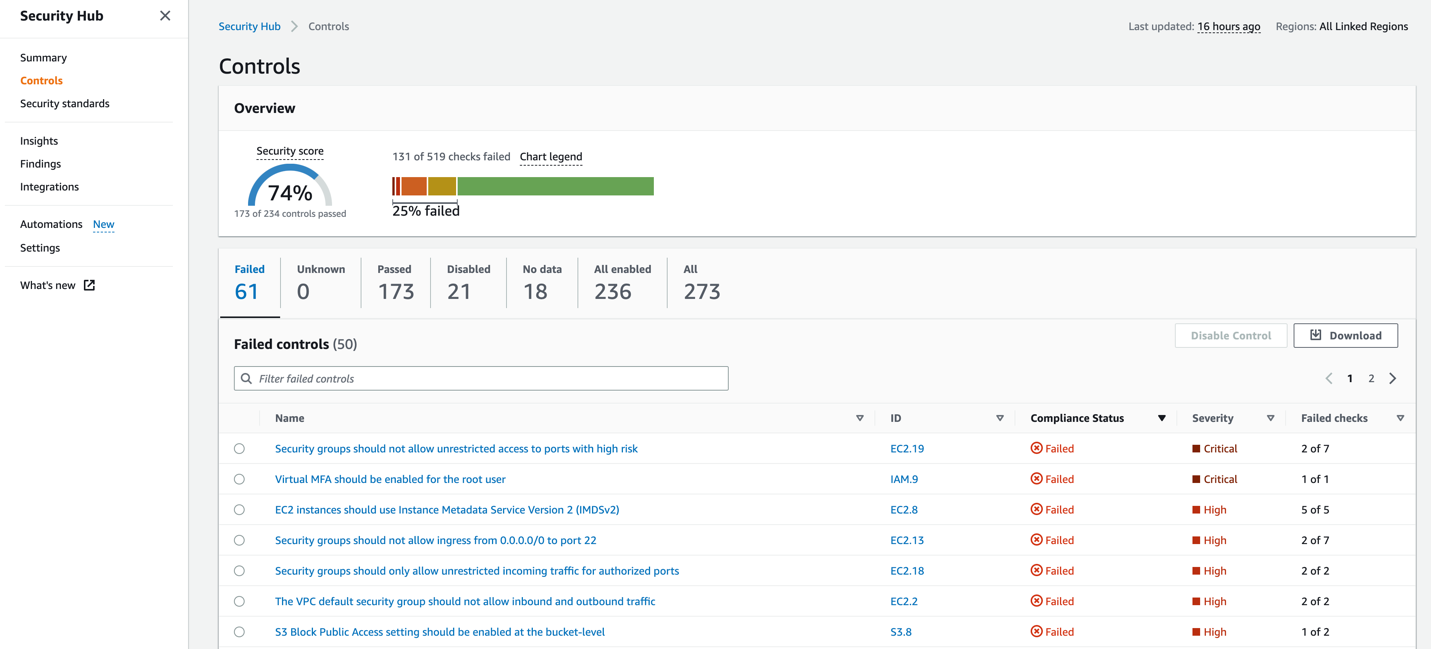
3. AWS Security Hub
Key Features:
- Platform: SaaS
- Pentest Capabilities: Automated assessment
- Accuracy: Does not ensure zero false positives
- Compliance Scanning: PCI DSS, NIST, and more
- Expert Remediation Assistance: No
- Workflow Integration: AWS Management Console, Security Hub API, AWS CLI, AWS SDKs Price: Usage-based pricing for security checks
AWS Security Hub is a cloud security posture management (CSPM) service that provides automatic, ongoing security reviews for all your AWS resources. Spotting misconfigurations and compiling security alarms in a standardized manner simplifies security operations and makes it easier to analyze, enhance, and resolve them.
It allows you to compare your AWS environment to industry standards and best practices, Security Hub effortlessly connects with AWS services and third-party solutions that are supported. The pricing for this service is based on usage.
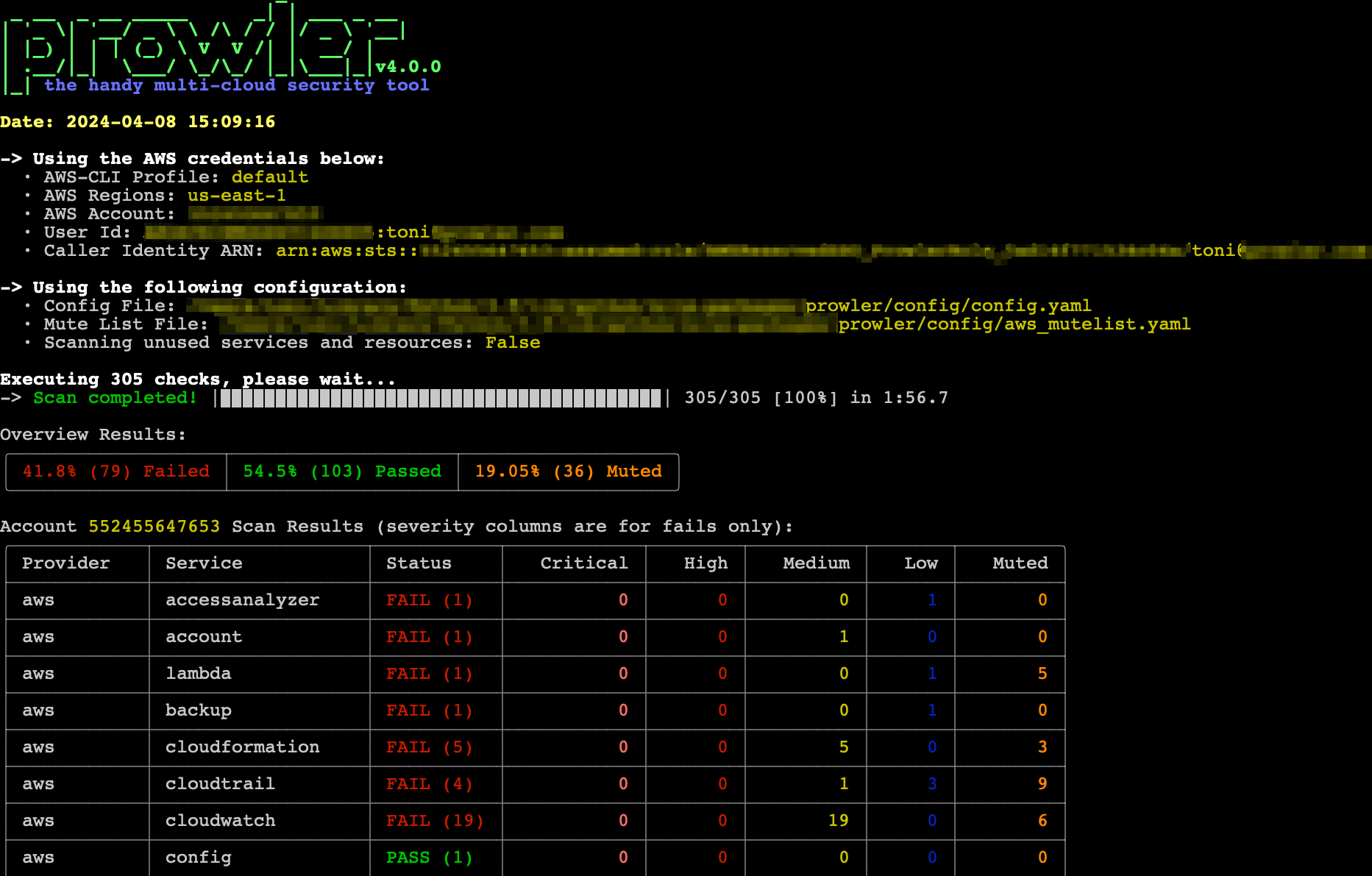
4. Prowler
Key Features:
- Platform: Open-Source
- Pentest Capabilities: Automated assessment
- Accuracy: Does not ensure zero false positives
- Compliance Scanning: PCI DSS, SOC2, HIPAA, NIST, and more
- Expert Remediation Assistance: No
- Workflow Integration: Github, Slack, JIRA
- Price: Free for the first few checks
Prowler provides a smooth integration and configurable dashboards that enable teams to create reliable apps and proactively safeguard cloud environments. This service is free for the first few checks.
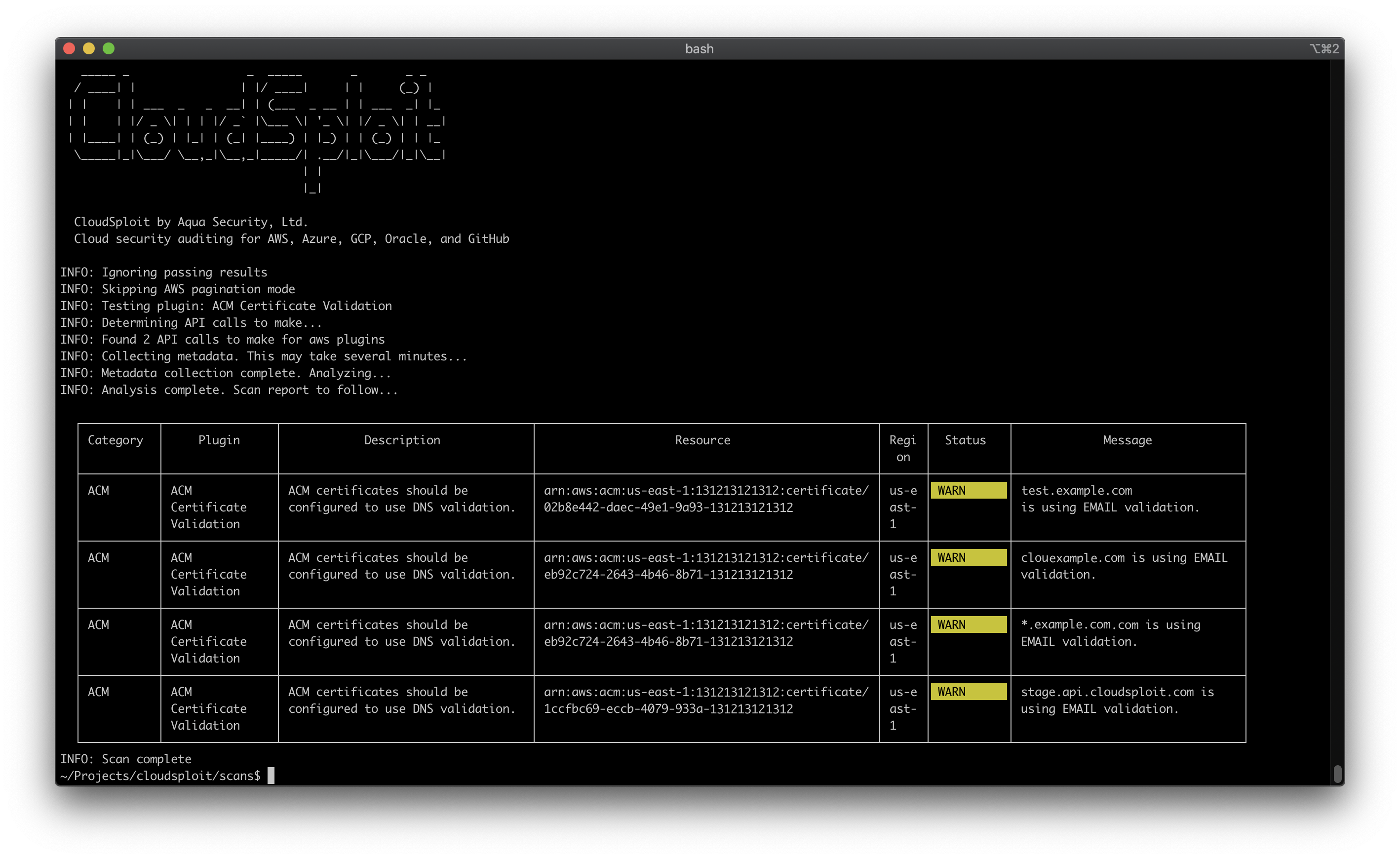
5. CloudSploit
Key Features:
- Platform: Open-Source
- Pentest Capabilities: Automated assessment
- Accuracy: Does not ensure zero false positives
- Compliance Scanning: None
- Expert Remediation Assistance: No
- Workflow Integration: JIRA, Opsgenie
- Price: Free for the first few checks
CloudSploit is a cloud security tool created exclusively for Amazon Web Services (AWS) customers to simplify the difficult process of safeguarding cloud infrastructure.
CloudSploit continuously scans several resources, settings, and activity logs for possible vulnerabilities and recommends fixes. CloudSploit is free for the first few checks.
AWS Penetration Testing Provider – Astra Security
As you would have gathered by now, AWS penetration testing is a serious undertaking involving complex processes that require expertise. Performing a complete security audit for the first time can be daunting, but with the right AWS pentesting provider, the process is made much simpler.
Astra Security is a penetration testing company that performs a complete security audit of your application. Our team of security experts can conduct an in-depth pentest of your AWS system and create a detailed remediation plan.
Astra Security also provides to its customers with an AWS pentesting checklist and a publicly verifiable AWS penetration testing certification.
Final Thoughts
Amazon Web Services (AWS) offers various integration opportunities for your application, including some built-in security features for the security of the cloud.
Given the increasing complexity of cyber attacks, AWS penetration testing is essential to ensure strong cloud security. As a user, you are responsible for protecting the cloud and your data within it, as per AWS’s Shared Responsibility Model.
AWS users can proactively detect vulnerabilities and improve their security posture using technologies such as Astra Security’s extensive penetration testing procedures. With the help of Astra’s experience and adaptable solutions, you can confidently manage the intricacies of AWS security, guaranteeing the safety of crucial assets in the cloud environment.

FAQs
Is penetration testing allowed on AWS?
Yes, penetration testing is allowed on AWS, but it requires prior authorization. AWS offers guidelines and processes for conducting penetration testing to help ensure security without disrupting services or violating terms of service. However, tests involving Command and Control (C2) necessitate prior approval.
What is the difference between cloud security and penetration testing?
Cloud security encompasses infrastructure and service protection, while cloud penetration testing assesses cloud-based app and infrastructure security. It identifies vulnerabilities and risks and offers a remediation plan. Cloud providers secure infrastructure, and customers secure accounts, apps, and data.
Is an AWS Pentest expensive?
While initial costs may vary, conducting regular AWS Pentests can actually save money by identifying and mitigating vulnerabilities before they lead to costly security breaches or compliance violations.
















