The current electronic payment techniques have completely transformed the transaction processes. Both businesses and customers benefit from smooth financial transactions because of the ease of credit and debit cards. However, as technology progresses, so do cyber risks, making cardholder data protection a major issue for organizations. This is where the PCI risk assessment comes in.
PCI DSS is a comprehensive structure designed to protect sensitive information during payment card transactions. A key aspect of complying with PCI is completing a thorough PCI risk assessment, which serves as the foundation for detecting vulnerabilities and implementing effective risk mitigation techniques. In this article, we will delve deep into what PCI DSS is, the significance of PCI compliance risk assessment, and the best practices to follow for implementing PCI DSS.
What is a PCI-DSS Risk Assessment?
PCI-DSS risk assessment is a process that helps organizations identify, analyze, and prioritize any risks that might compromise the resources, operations, or PCI compliance goals of an organization. It is the cornerstone of a strong information security program and facilitates efficient risk management. Organizations may proactively identify potential threats, and adopt effective mitigation techniques.
PCI compliance risk assessment or even a regular risk assessment is an integral part of strategic decision-making, guiding the ways companies navigate their operational landscape. This systematic approach allows organizations to estimate the likelihood and potential impact of identified risks, prioritizing them according to their overall effect on organizational objectives.
Importance of PCI Risk Assessment
PCI compliance risk assessment plays a crucial role in ensuring the security and compliance of organizations, and here are some compelling reasons why it is of utmost importance:
- PCI DSS Compliance: Simply put, PCI risk assessment is a non-negotiable part of PCI assessment process. If you choose to skip this step, you’re asking for trouble. Non-compliance comes with some heavy penalties, like fines and legal liabilities. But the real kicker? A damaged reputation. Once you lose the trust of your customers, partners, and stakeholders, it’s an uphill battle to win it back.
- Data Breach Prevention: Here’s the harsh truth: cardholder data is a gold mine for cybercriminals. But with a comprehensive PCI risk assessment, you can be one step ahead. By pinpointing vulnerabilities and setting up the right controls, you reduce the risk of data breaches.
- Cost Savings: Sure, a PCI risk assessment may seem like an upfront cost. But in reality, it’s a long-term investment in the financial health of your organization. Being proactive about potential security risks can save you from the financial nightmare of a data breach – including the costs of forensic investigations, legal actions, and lost business.
- Business Continuity: A good PCI risk assessment is like a shield for your business. It makes sure your critical systems and processes are protected, keeping disruptions to a minimum. And even when a security incident does sneak through, your robust risk management strategy ensures you can bounce back quickly.
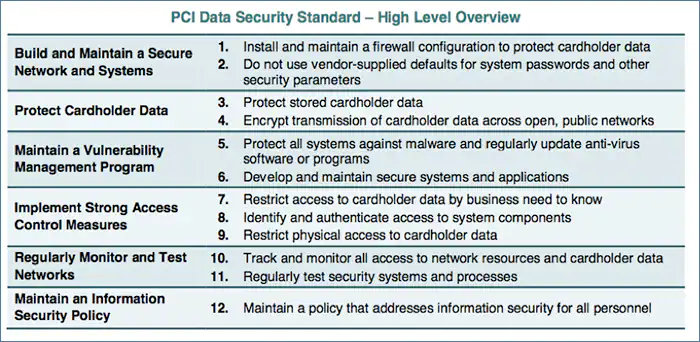
PCI-DSS Fundamental Requirements
Organizations are required to comply with 12 PCI DSS requirements that have been carefully created to provide a solid safety record within organizations that handle credit, debit, and cash card payments.
Following is a summary of PCI DSS’s 12 fundamental requirements:
- Build and Maintain a Secure Network: To safeguard cardholder data, it is essential to build and maintain secure network infrastructure. It includes procedures like implementing firewalls, adopting secure protocols, and preventing unauthorized access.
- Protect Cardholder Data: The goal of this parameter is to encrypt cardholder data during transmission and storage so that it is unreadable and insignificant to potential attackers.
- Maintain a Vulnerability Management Program: To mitigate known vulnerabilities that cybercriminals might exploit; organizations must consistently upgrade and patch systems, applications, and software.
- Implement Strong Access Controls: To stop unauthorized data breaches, it is important to restrict access to cardholder data to authorized personnel only. This requirement involves the use of distinct user IDs, multiple-factor authentication, and access restrictions based on job roles.
- Regularly Monitor and Test Networks: Continuous monitoring and periodic security testing help identify potential threats and vulnerabilities promptly. This requirement comes with the PCI-DSS risk assessment guidelines which involve activities such as network monitoring, penetration testing, and security assessments.
- Maintain an Information Security Policy: By establishing a thorough and clear information security policy, you can make sure that every employee and stakeholder is aware of their responsibilities and obligations concerning the protection of cardholder data.
PCI DSS Risk Assessment Steps
PCI DSS risk assessment is a specialized form of risk assessment tailored to meet the specific requirements of PCI DSS compliance. Its primary objective is to comprehensively evaluate an organization’s cardholder data environment, identifying and assessing potential risks related to the confidentiality, integrity, and availability of cardholder data.
The PCI risk assessment process typically encompasses the following key steps:
1. Scope Identification
A clear definition of the cardholder data environment’s scope within the organization’s infrastructure is essential. This involves identifying all systems, networks, and processes that handle cardholder data. This establishes your PCI scope. Proper PCI-DSS scoping ensures that critical components are not overlooked during PCI assessments.
Details to mention during the scoping include:
- How is the data used?
- How is the cardholder information processed and transmitted?
- Who has access to the credit card data stored by your company?
- Any potential personnel or systems that can affect the cardholder data.
Understanding the flow of cardholder data through various systems and processes is crucial to pinpoint potential vulnerabilities and areas of risk. This PCI assessment process helps identify weaknesses in the data flow, allowing the implementation of targeted security controls.
2. Threat Identification
The PCI risk assessment involves identifying both internal and external threats that could compromise cardholder data. These threats may include cyberattacks, social engineering, insider threats, malware, and physical security breaches. Understanding potential threats helps develop focused risk mitigation strategies.
When vulnerabilities are tested, systems that are scanned include:
- Digital assets (weak passwords, improper authorization measures)
- Physical assets (documents with cardholder information)
- Internal assets (company personnel and their access)
Mainly threats arise from vulnerabilities and other risks. Vulnerabilities are essentially flaws in the components, procedures, or internal controls. Whereas risks refer to the odds with which a threat is likely to be exploited and the impact it would have on the cardholder data stored by your organization.
3. Vulnerability Assessment
Vulnerability PCI assessments are conducted on identified systems and processes to determine weaknesses that could be exploited by potential threats. Vulnerability scanning, penetration testing, and security audits are some of the techniques used to identify and address security gaps.
Vulnerability assessments should be able to identify a wide range of vulnerabilities that cover top vulnerabilities such as CVEs, OWASP Top 10 vulnerabilities, SANS Top 25, and other vulnerabilities deemed a threat to cardholder data by PCI-DSS.
Once the vulnerability assessment is carried out for the identification of vulnerabilities and the impact of their exploitation, the next step is to sort them out based on the risk they present to your cardholder data storage. This is known as risk rating.
4. Risk Rating
Each identified risk is evaluated based on its potential impact and likelihood. Assigning a risk rating helps prioritize mitigation efforts, allowing organizations to focus on addressing the most critical risks first.
The two ways risks are classified into include:
- Likelihood of risk: This refers to the chances in which a detected vulnerability could be exploited. For example, if you suffered a breach last year, it is likely to happen again unless additional security measures have been implemented.
- Potential of risk: This refers to what the potential impact of vulnerable exploitation would be for your organization.
The next part of risk rating involves developing and implementing risk mitigation strategies and controls. Organizations must select appropriate security measures to reduce the likelihood and impact of identified risks. These controls may include encryption, access controls, network segmentation, regular security testing, and employee training.
5. Ongoing Monitoring
PCI risk assessment is an iterative process that requires regular reviews and updates. This ensures that the organization remains vigilant and adaptive to evolving threats and changes in the business environment.
Once your risk assessment and subsequent mitigation are complete, it is important to document the whole process and make a risk management strategy for your organization’s systems. When crafting it you need to understand and specify your goals related to the evaluation, prioritization, and mitigation of the risks, threats, or vulnerabilities. You must also carry out pentests, and or vulnerability assessments between regular intervals or after any system update.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Best Practices for Conducting PCI Risk Assessment
To ensure the effectiveness of PCI risk assessment, organizations should adopt the following best practices:
Establish a Cross-functional Team
Involve stakeholders from IT, security, compliance, legal, finance, and various business units to ensure a holistic approach to risk assessment. Each team member brings unique perspectives and insights that contribute to a more comprehensive assessment.
Define the Scope Clearly
Clearly defining the boundaries of the cardholder data environment is critical. This ensures that all relevant systems, processes, and third-party entities are included in the assessment.
Data Mapping and Flow Analysis
Thoroughly understanding how cardholder data moves through the organization helps in identifying potential weak points. Data mapping and flow analysis facilitate the identification of areas where data is most vulnerable to compromise.
Adopt Industry Standards
While PCI DSS provides essential guidelines, organizations can benefit from adopting other established frameworks and best practices, such as the NIST Cybersecurity Framework or ISO 27001. These frameworks complement PCI DSS and provide additional insights into managing risks effectively.
Use Qualified Assessors
Engage qualified and experienced assessors to conduct the risk assessment. These individuals possess the necessary expertise and knowledge to conduct a thorough evaluation and provide valuable recommendations.
Regularly Review and Update
Risk assessment is not a one-and-done exercise. Regularly reviewing and updating the assessment ensures that the organization remains prepared to address new threats, changes in the business environment, and updates to PCI DSS.
Document Everything
Maintain comprehensive documentation of the risk assessment process, findings, and mitigation strategies. Proper documentation ensures that the organization can demonstrate its commitment to security during audits and assessments.
Integrating Risk Mitigation Strategies
Once risks are identified and assessed, organizations must implement suitable risk mitigation strategies. Some effective strategies include:
Strong Access Controls: Implementing robust access controls is a paramount task for organizations. These controls restrict access to cardholder data, allowing only authorized personnel to interact with sensitive information. These include measures such as multi-factor authentication, which can add an additional layer of security, least privilege access, ensuring each user has the minimum levels of access they need to perform their work, and regular access reviews to update and maintain these controls in line with changes in personnel and roles.
Data Encryption: Data encryption transforms readable data into a coded version that is unreadable to unauthorized individuals. It plays a pivotal role in maintaining data security. By encrypting cardholder data during transmission and storage, organizations ensure it’s protected from unauthorized access. This encrypted data, even if intercepted, remains useless to the attacker without the appropriate decryption keys.
Network Segmentation: Network segmentation involves splitting a computer network into smaller parts. Segmenting the network helps isolate cardholder data from other systems, effectively reducing the potential attack surface. This can act as a buffer, ensuring even if one part of the system is compromised, the attacker does not have free access to all areas, thereby limiting potential damage.
Regular Security Testing: Regular security testing such as penetration testing and vulnerability assessments is a proactive measure to identify and fix security gaps. Through these assessments, potential vulnerabilities can be spotted and addressed before they can be exploited by malicious entities. These tests should be conducted at a frequency that matches the organization’s risk environment and whenever significant changes occur in the system.
Employee Training and Awareness: Human error or ignorance can often be a weak point in the security chain. Therefore, regularly educating employees about the importance of security, best practices, and how to recognize and report potential security threats is essential. An aware and educated employee can act as an additional line of defense against cyber threats.
Incident Response Plan: It’s crucial for an organization to be prepared for potential security incidents. A comprehensive incident response plan should be developed, outlining procedures to identify, contain, eradicate, and recover from security incidents. Such a plan helps to minimize the impact of potential security incidents and ensures the organization can respond effectively, thereby safeguarding business continuity and reputation.
Conclusion
PCI risk assessment is a fundamental process in achieving and maintaining PCI DSS compliance. By thoroughly understanding the cardholder data environment, identifying potential risks, and implementing effective risk mitigation strategies, organizations can significantly enhance their security posture and protect sensitive data from cyber threats.
A proactive and vigilant approach to risk assessment not only secures the organization’s reputation and customer trust but also helps foster a culture of security and compliance across the organization.
Choosing the right PCI QSA company is paramount in safeguarding the security and compliance of your organization’s web resources. It is highly recommended that you forge a partnership with industry-leading PCI QSA companies, such as Astra or the others mentioned in this article. You can tap into their expertise and gain invaluable insights into your current security posture.
To discover the full range of benefits of partnering with PCI QSA companies and to explore how they can tailor their solutions to your specific needs, we invite you to schedule a free consultation with the team of experts at Astra. Don’t leave your security to chance – consult with us today!
FAQs
What is the role of PCI QSA companies in PCI-DSS audits?
PCI QSA companies are authorized firms that assess organizations for compliance with the Payment Card Industry Data Security Standard (PCI-DSS). They conduct comprehensive audits, evaluate security controls, and recommend improved data protection practices.
How do PCI QSA companies help organizations achieve PCI-DSS compliance?
PCI QSA companies assist organizations in achieving PCI-DSS compliance by conducting thorough assessments of security controls, identifying gaps, and providing guidance on remediation. They also offer services such as vulnerability scanning, penetration testing, and security policy development.
What are the key services offered by PCI QSA companies?
PCI QSA companies offer various services, including PCI-DSS compliance assessments, vulnerability scanning and penetration testing, security policy development, remediation support, and more. These services help organizations strengthen their security posture and meet the requirements of PCI-DSS.
What sets Astra Security apart from other PCI QSA companies?
Astra Security stands out for its expertise in cybersecurity, going beyond compliance. They combine advanced technologies with industry best practices, providing a holistic approach to security and actionable insights for effectively protecting web resources.
















