Financial information of users are prime target for malicious actors looking for a weak link in your digital infrastructure. This is where Payment Card Industry Data Security Standard (PCI DSS) compliance becomes important. It is a well regarded compilation of security protocols aiming to secure all enterprises that engage in activities like the acceptance, processing, storing, or transmitting of cardholder information.
Adopting PCI DSS is important in shielding cardholder data from potential breaches and cyber attacks. It is a holistic standard covering various aspects of an organization’s IT spectrum, from its network architecture to policy development. Companies must check off 12 points in the PCI DSS compliance checklist.
The PCI compliance checklist 2023 will delve deeper into the PCI DSS checklist and provide it to you in a simplified manner helping you ensure compliance.
PCI DSS Compliance Checklist: Deciphering the 12 Crucial Steps

1. Establishing and Sustaining a Secure Firewall
The first step in the PCI checklist is to have a sturdy firewall configuration. A firewall serves as a shield between a trusted internal network and untrusted external networks, like the Internet. Its role is to prevent unauthorized access to or from a private network by scrutinizing and managing inbound and outbound network traffic based on pre-set security norms.
But simply installing a firewall won’t cut it. It’s paramount to effectively uphold and manage this firewall. This includes routinely updating firewall rules and regulations, inspecting them for potential security loopholes, and promptly rectifying any identified vulnerabilities. The objective is to ascertain that the firewall stays robust against mutating threats and continues to protect your payment card data ecosystem.
2. Discarding Vendor Default Settings for Enhanced Security
Default configurations supplied by vendors for systems and apps are often lacking in security, making them a popular target for attackers. To abide by PCI DSS, businesses must not use vendor-provided defaults for system passwords and other security parameters.
This step in the PCI DSS checklist necessitates altering default credentials, configurations, and settings for all devices, hardware, and software applications utilized within your organization. In addition, organizations need to uphold documentation delineating their security configuration practices. This not only guarantees a superior degree of security but also facilitates smoother auditing and verification of compliance.
3. Safe Storage of Cardholder Data
At the heart of PCI DSS compliance checklist is protecting cardholder information. Businesses need to implement strict measures to protect this sensitive information. Determining the movement of cardholder data within your network and ensuring its secure storage is critical. Recognized encryption algorithms and security keys should be used to preserve the secrecy of stored data.
4. Safe Transmission of Cardholder Data
This step in the PCI DSS requirements checklist centers on securing cardholder data while it’s transmitted across open, public networks. Data exchanged between systems, such as between a retailer and a payment processor, can become a prime target for cybercriminals. Therefore, businesses must ensure that cardholder data is appropriately encrypted prior to transmission.
Identifying where cardholder data is sent to and received from is fundamental to preserving its security during transmission. Businesses should utilize secure protocols to reduce the risk of data breaches.
5. Maintaining Regular Antivirus Updates
Merely installing antivirus software does not fulfill this step of the PCI compliance checklist . Regular updates and patches for antivirus software applications are essential to protect against malware and other potential threats that could compromise system and cardholder data integrity. This step in the PCI checklist ensures that your defensive mechanisms are current and prepared to combat emerging cybersecurity threats.
The antivirus software should operate across the entire IT infrastructure, including servers, workstations, and employee devices. It should always be active, utilizing the latest virus definitions, and it must generate logs for auditing and potential incident responses.
6. Secure Systems and Applications Deployment
This step in the PCI compliance checklist involves the identification and categorization of risks prior to deploying any technology involved in processing or handling sensitive payment card information. Businesses must conduct a comprehensive risk assessment to understand their current systems’ and applications’ threat landscape and vulnerabilities.
Once risks have been evaluated, businesses can then introduce necessary equipment and software in compliance with PCI standards. Timely patching is also a critical component of this step, ensuring databases, point-of-sale terminals, and operating systems are up-to-date, thereby minimizing the risk of breaches due to known vulnerabilities.
7. Necessary Restriction of Cardholder Data
This step in the PCI DSS checklist stipulates that access to such sensitive data should be granted strictly on a need-to-know basis, thereby avoiding unnecessary exposure of data. This means that access to cardholder data should only be granted to individuals who need it to perform their job functions.
Organizations must maintain a detailed access control policy, outlining who has access to cardholder data, to what extent, and for what reason. This includes documenting the access levels each user has and ensuring it stays updated. By limiting access to cardholder data, businesses can effectively reduce their risk exposure.
8. Unique User Access Identification
This step in the PCI compliance checklist stipulates that each user in a system must have a unique identifier. Shared or group usernames or passwords should never be used, as they complicate tracking user activities and heighten security risks. Each user’s unique access credentials should be complex enough to discourage unauthorized access.
Unique access identifiers serve two purposes. They not only deter unauthorized access but also enable traceability in the event of a data breach. User activities can be traced back to specific users, aiding incident response and future preventive measures. For enhanced security, PCI DSS requirements checklist also advocate the use of multi-factor authentication.
9. Physical Access Restrictions to Data
PCI compliance isn’t only about digital security; it also demands organizations to consider physical access to data. Businesses need to secure access to servers, paper files, and workstations that deal with cardholder data, ensuring effective physical security measures.
10. Continuous Monitoring of Network Access
Given the ongoing threat landscape, businesses must continuously monitor their network access points. This includes both physical and wireless networks, all of which need consistent protection and surveillance. To fulfil this step in the PCI DSS requirements checklist, businesses should maintain a comprehensive record of network activity, providing a foundation for security audits and investigations.
Businesses can utilize Security Information and Event Management (SIEM) tools to help log system activity and alert any potential security anomalies. According to PCI compliance checklist, these audit trail records must be maintained and synchronized for at least one year.
11. Regular Testing of Systems and Processes
In the face of constant attempts by cybercriminals to find vulnerabilities in systems, continuous testing is more than a good practice; it’s a requirement to be fulfilled in the PCI DSS compliance checklist. Regular testing activities like vulnerability scans and penetration tests can assist businesses in identifying potential weak spots and addressing them proactively.
Businesses should perform wireless analyzer scans quarterly to detect any unauthorized access points. It’s also crucial for external IPs and domains to be scanned by a PCI Approved Scanning Vendor (ASV). Likewise, internal vulnerability scans should be conducted at least every quarter. A thorough application and network penetration test should be done annually to fully evaluate a company’s security posture.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

12. Establishment of an Information Security Policy
The step in the PCI compliance checklist is about building, putting into action, and consistently updating a broad information security policy. This master plan should encompass everyone – from your team on the ground, the management hierarchy, to any relevant third parties. It spells out the ground rules for treating cardholder data and for keeping your IT environment secure.
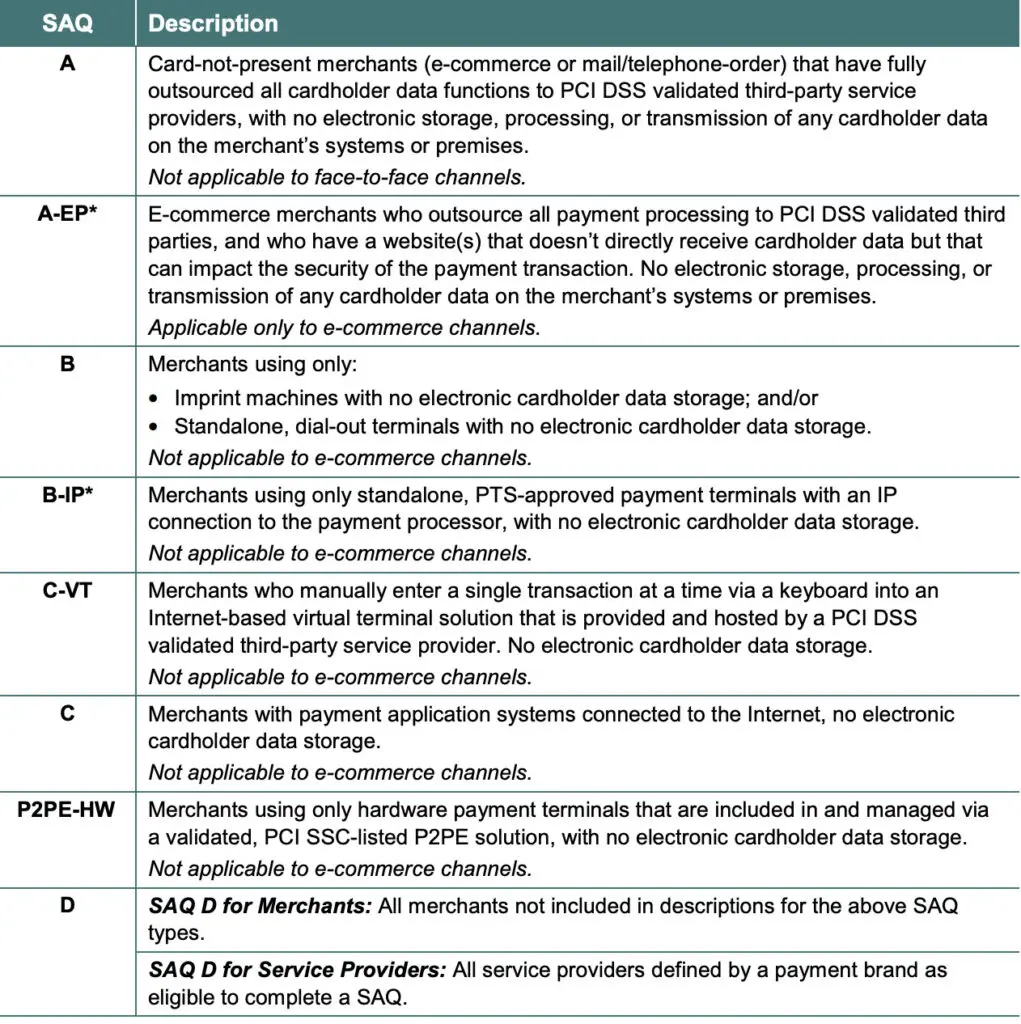
Diving Deep into Self-Assessment Questionnaires (SAQs)
Self-Assessment Questionnaires (SAQs) are cornerstones of the PCI compliance checklist. They are instruments supplied by the PCI Security Standards Council, which aid merchants in evaluating and reporting the efficacy of their payment card data security. Depending on the specificities of your business and how you process payment card data, you might need to tackle several types of SAQs.
Each SAQ comprises a sequence of yes-or-no queries concerning the security controls installed throughout your cardholder data environment. These queries map directly to the PCI DSS requisites, simplifying the process for businesses to exhibit their compliance status. Filling out an SAQ isn’t a one-off task but a continuous process, with businesses required to reassess their compliance on an annual basis or whenever considerable modifications occur in their payment card processing environment.
The Need for External Assessments and Routine Audits in the PCI Compliance Checklist
Despite possessing a firm grasp of PCI DSS requisites and diligently fulfilling Self-Assessment Questionnaires (SAQs), external evaluations and regular audits remain indispensable facets of PCI compliance. The necessity for these stems from the perpetually evolving threats, the intricate nature of payment systems, and the vital role independent scrutiny plays in maintaining the integrity of compliance.
External evaluations, carried out by a Qualified Security Assessor (QSA), offer an unbiased perspective on an organization’s compliance stance. QSAs are autonomous security entities accredited by the PCI Security Standards Council to execute PCI DSS assessments. Their mission is to ensure that the mandatory controls are not merely present but effectively operational, delivering an exhaustive and objective assessment of the organization’s compliance status.
Regular audits, conversely, serve as a steady surveillance mechanism. These audits, whether performed internally or externally, ensure persistent adherence to PCI DSS requirements. They empower organizations to identify potential non-compliance matters early and initiate remedial measures, thereby nurturing continuous enhancement in their security posture.
Consequently, a sturdy PCI DSS compliance program interweaves both self-evaluations (SAQs) and external assessments, bolstered by periodic audits. This multifaceted strategy ensures that an organization’s compliance is never stagnant but perpetually adapts to shifting threats and business landscapes.
Conclusion
Payment card transactions are an integral part of daily commerce, PCI DSS compliance is an essential security responsibility. The 12-point PCI compliance checklist effectively and efficiently manage cardholder data.
Choosing the right PCI QSA company is paramount in safeguarding the security and compliance of your organization’s web resources. It is highly recommended that you forge a partnership with industry-leading PCI QSA companies, such as Astra or the others mentioned in this article. You can tap into their expertise and gain invaluable insights into your current security posture.
To discover the full range of benefits of partnering with PCI QSA companies and to explore how they can tailor their solutions to your specific needs, we invite you to schedule a free consultation with the team of experts at Astra. Don’t leave your security to chance – consult with us today!
Frequently Asked Questions
What are the changes in PCI 2023?
Improved account security regarding passwords and user authentication. Requiring stronger and more robust discovery and monitoring of sensitive data. Expanding the scope of entities to whom PCI DSS applies.
What is the latest version of PCI compliance?
The PCI SSC released version 4.0 at the end of March 2022, although PCI DSS v3. 2.1 will remain active for two years through March 2024. PCI 4.0 will go live in March 2025.
What are the PCI 4 levels?
Level 1: Merchants that process over 6 million card transactions annually.
Level 2: Merchants that process 1 to 6 million transactions annually.
Level 3: Merchants that process 20,000 to 1 million transactions annually.
Level 4: Merchants that process fewer than 20,000 transactions annually.
















