Powering nearly 75 million websites globally and deemed as the most favorable CMS platform of all, WordPress is widely used by most online retailers and entrepreneurs when it comes to conducting online business. The popularity splurges as the CMS adheres to a ready-to-use, SEO friendly and mobile compatible templates.
A plethora of WordPress plugins are available today, which carries out a lion’s share of the work on the website. Plugins provide the added functionality to websites, a major reason why WordPress is so popular.
This extent of popularity often places WordPress as one of the most targeted CMSs when it comes to cyber-crime. WordPress plugins are prone to vulnerabilities, often placing the plugin containing website at a great peril to leak of sensitive information and server control. Every plugin added to your site increases a security risk, and therefore, it becomes imperative to evaluate if each one of them is regularly updated. Listed below are some of the notoriously known vulnerabilities in WordPress plugins that rendered thousands of websites at risk in the past.
1. Revolution Slider Plugin Vulnerability
Unearthed in November 2016, the unpatched version of the Revolution Image Slider Plug-in is essentially the outdated version of Revslider and was extensively used by a large number of WordPress websites.
The notoriously known Panama Papers leak of April 2016 took place courtesy this plug-in, leading to a leak of massive amounts of personal data spanning to over 2.6 TB of data and 11.5+ million documents during that time.
This vulnerability allowed an attacker to download any file from the server, and also steal database credentials, thus allowing the attacker to compromise the website completely. Such kinds of vulnerability are designated as a Local File Inclusion (LFI) attack whereby an attacker is able to access, review, and download a local file on the server.
Also, check Major WordPress plugins exploited in 2018
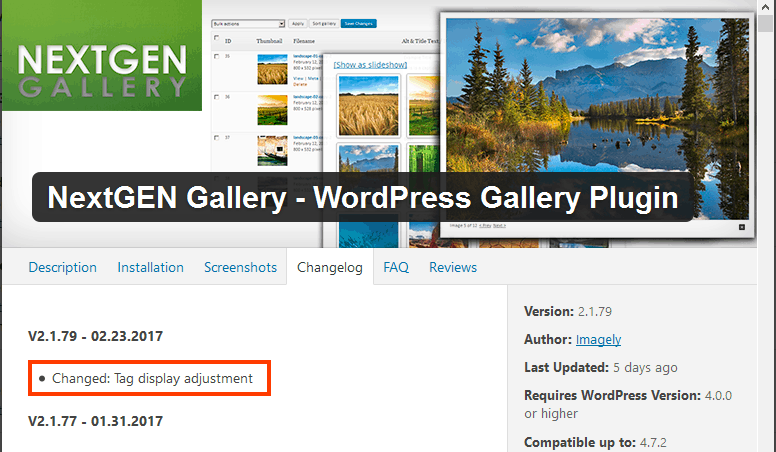
2. NextGEN Gallery Plugin Vulnerability
NextGen Gallery, one of the most popular Gallery plugins in WordPress CMS was deemed as vulnerable to hacks that allow visitors to steal password data and secret keys from databases. With over 1 million installations, the flaw is in the form of an SQL Injection bug allowing inputs of malicious nature to be injected into WordPress prepared SQL queries. Moreover, under certain conditions, the attacker could feed commands to a server’s backend database.
There were 2 attack scenarios with this vulnerability:
- A WordPress site owner activates the NextGEN Basic TagCloud Gallery option on his site: This feature allows site owners to display image galleries that users can navigate using tags, all the while altering the site’s URL as the user navigates through photos. Since there exists an improper input sanitization in URL parameters, the attacker can modify link parameters and insert SQL queries that will be executed by the plugin when the malformed URL is loaded.
- When website owners open their site for blog post submissions: In this case, the attacker can insert malicious NextGEN Gallery codes since they are able to create accounts on the site and submit a blog post/article for review. Depending on the attacker’s skill, the malicious code will allow him access to internal database and loss of personal information.
However, the vulnerability was fixed in NextGEN Gallery version 2.1.79. NextGEN Gallery changelog on the WordPress Plugins repository says “Changed: Tag display adjustment”.
3. Neosense version 1.7 flaw
In 2016, the Neosense business template v1.7 was discovered with a flaw exploiting which an attacker could upload malicious files to sites running on this theme. This way an attacker could gain control of the site without user authorization by simply uploading a file using Curl and run it immediately using that URL.
DynamicPress, the WordPress theme publisher ties this vulnerability to use the open source code “qquploader,” an Ajax-based file uploader that had been implemented without any security. Exploiting this, an attacker can upload a malicious PHP script with the extension .php or .phtml to the site’s download directory.and gain access to the upload directory.
The vulnerability was, however, rectified in the next version Neosense v 1.8
4. FancyBox
Fancybox, one of the most popular WordPress plugin used by thousands of websites for displaying images, HTML content and multimedia was deemed flawed after a critical zero-day vulnerability was discovered. The vulnerability allowed attackers to inject a malicious iframe (or any random script/content) into the vulnerable websites which redirected the users to a ‘203koko’ website.
The reach of this vulnerability can be judged by the fact that of the nearly 70 million websites running WordPress, nearly half use this plugin. However, two versions of the plugin were released soon after to fix this flaw.
5. TimThumb vulnerability
A WordPress image resizing library called TimThumb had left numerous WordPress plugins at risk to malicious attacks. Popular plugins vulnerable due to this issue include TimThumb, WordThumb, WordPress Gallery Plugin and IGIT Posts Slider amongst many others.
The vulnerability allowed an attacker to remotely execute an arbitrary PHP code on the affected website. Once complete, the attacker can compromise the website in any way he wants.
http://vulnerablesite.com/wp-content/plugins/pluginX/timthumb.php?webshot=1&src=http://vulnerablesite.com/$(rm$IFS/tmp/a.txt)
http://vulnerablesite.com/wp-content/plugins/pluginX/timthumb.php??webshot=1&src=http://vulnerablesite.com/$(touch$IFS/tmp/a.txt)
The vulnerability was later patched in an update.
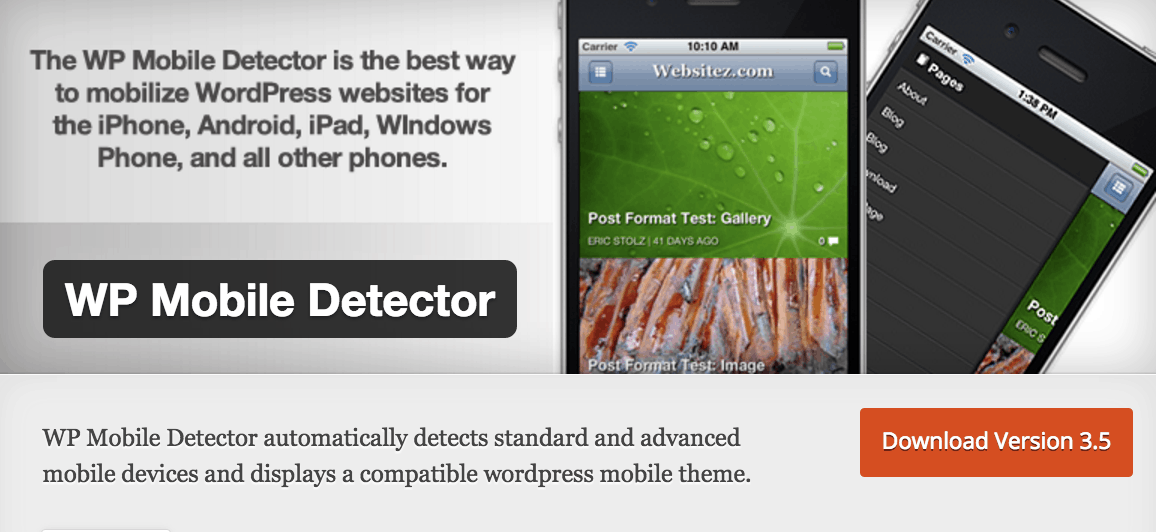
6. WP Mobile Detector
Over 10,000 websites use a WordPress plug-in named WP Mobile Detector which turned out to possess a flaw.
The vulnerability could be exploited using a script called resize.php script which enabled remote attackers to upload arbitrary files to the Web server. These files could act as backdoor scripts, also known as Web shells, thus providing a backdoor access to the server and the power to inject malicious pieces of code into legitimate pages.
To know more about how to secure your freshly installed WordPress site, visit our comprehensive guide to WordPress security.
Contact Astra to provide the ultimate protection to your wordpress website.
















Thanks for sharing the best information and suggestions they very nice and very useful to us. You made a good site it’s very interesting one.I am satisfied with your site and also your information.
[…] been incidents in the past where vulnerabilities in plug-ins of WordPress and Magento have lead to thousands of websites getting […]
[…] of the most popular content management systems in the world is rendered vulnerable to yet another vulnerability capable of bringing down an entire WordPress powered system. Statistically powering nearly 29% of […]
[…] too. But then there are thousands of plug-ins/extensions these CMSs use which prove to be an easy entry point for hackers. The controversial Panama Papers Leak of 2016 was because of a vulnerability in the famous […]
Thanks for sharing this content with us, I find this really helpful.