About Amasty RMA Extension Vulnerabilities
During a security audit engagement with a client using Magento, our engineers discovered a few critical vulnerabilities in Amasty RMA extension. The first vulnerability allows a hacker to upload malicious files on the server. Since php files can also be uploaded, a hacker can easily upload malicious shells like c99, r57, anishell etc to the server.
If additional checks are not in-place, a hacker would get hold of entire server by exploiting this. Another vulnerability, which was not found only in a few websites using RMA allows a hacker to download any directory from the server.
With some information available about the web app, a hacker can download critical files from the server.
Details of the Vulnerability
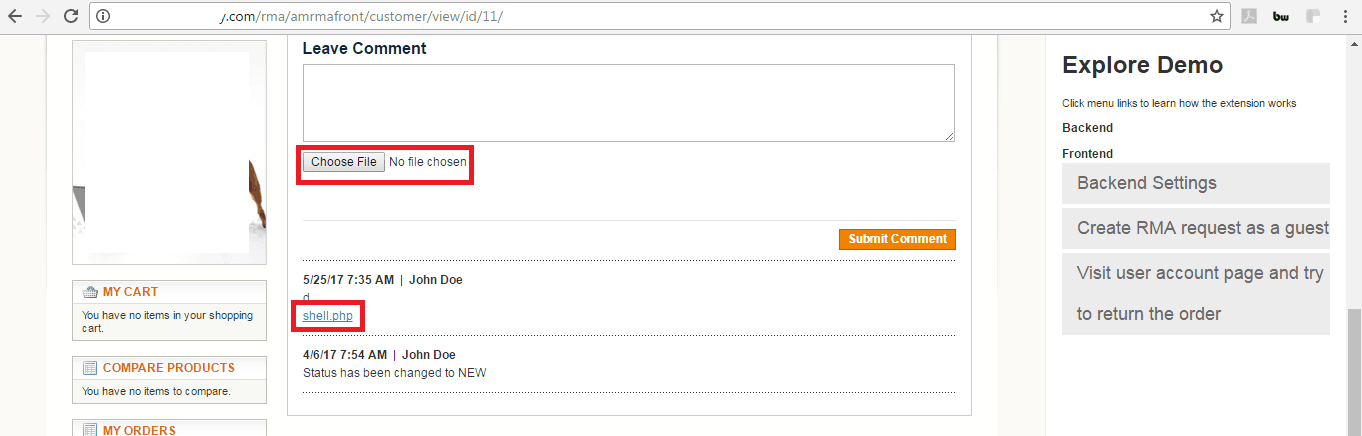
- Malicious File Upload: The upload area can be exploited by hackers to upload malicious files. Like while trying we were able to upload a php shell. That’s why its very important to secure Magento file upload. See the picture below:
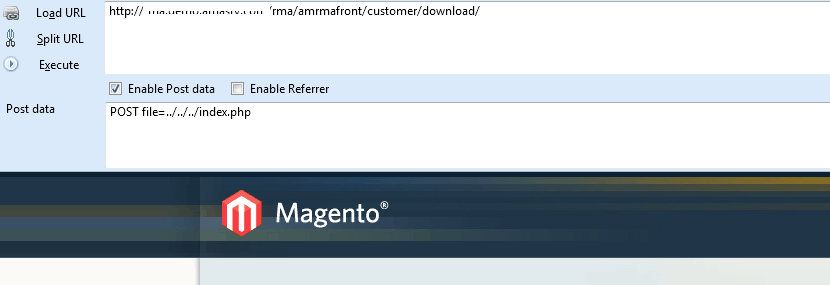
- Directory Traversal/file download: If the following request(see picture below) is made, an file on the server can be downloaded. For common files like .htaccess etc. which are present on almost every servers hackers can easily guess and download them. However, our client who was on magento 1.9 was vulnerable to this but reproducing on other versions wasn’t possible.
Consequences of Magento RMA Vulnerabilities
- Possible compromise of the complete server
- Server file download by hackers
- Targeted attack on end users/admins possible
Timeline
Amasty team was very quick in fixing the vulnerability. We received a quick reply from Kirill, product manager of RMA plug-in. Following which the patch was released within a few days.
Magento secure file upload
It’s very important to secure Magento file uploads, because the upload area can be exploited by hackers to upload malicious files. Like while trying we were able to upload a php shell.