The leading web application language PHP is found to have several critical vulnerabilities in versions 7.1, 7.2 & 7.3. The most dreading of it all is the arbitrary code execution vulnerability in PHP. Many popular CMS like, WordPress, Magento, Drupal, Joomla, etc. use PHP as their tech stack.
Although there have not been any wild attacks yet. Still, the severity of the vulnerability could be guessed by the vast number of websites it puts to risk.
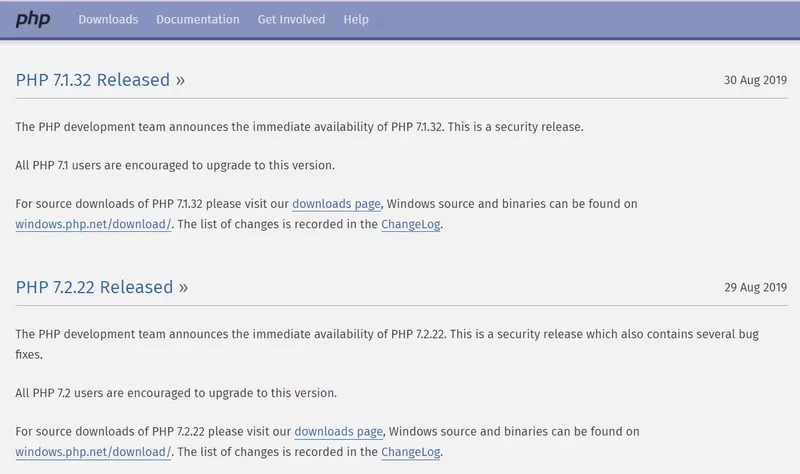
PHP released an update on 29th Aug about the bug fixes and release of new versions. However, web owners are yet to update their website’s PHP versions.
The updated versions are:
- PHP version 7.1.32 for 7.1
- PHP version 7.2.22 for 7.2
- PHP version 7.3.9 for 7.3
Download the updated versions from here.
Technical Details
The vulnerabilities found and patched by PHP could allow arbitrary code execution in websites, if not updated. Apart from code execution, it could also allow attackers to install malicious programs; see, modify, and delete data; create fake user accounts. Also, a failed exploitation could render DoS (denial-of-service) for your website.
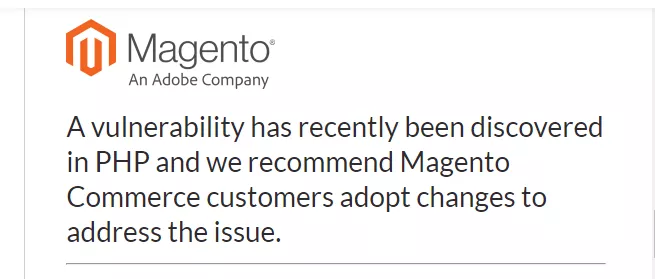
Most CMS developers are taking it upon themselves to spread the word to their customers. For instance, Magento sent a mail to its customers citing the critical vulnerability. It also put a deadline of 30th September for its customers to update their PHP versions.
Bug Fixes in Version 7.1.32
- Fixed bug #78256 (heap-buffer-overflow on exif_process_user_comment). (CVE-2019-11042)
- Fixed bug #78222 (heap-buffer-overflow on exif_scan_thumbnail). (CVE-2019-11041)
- Fixed bug #77919 (Potential UAF in Phar RSHUTDOWN).
Bug Fixes in Version 7.2.22
- Fixed bug #78363 (Buffer overflow in zendparse).
- Fixed bug #78379 (Cast to object confuses GC, causes crash).
- Fixed bug #77946 (Bad cURL resources returned by curl_multi_info_read()).
- Fixed bug #78333 (Exif crash (bus error) due to wrong alignment and invalid cast).
- Fixed bug #78342 (Bus error in configure test for iconv //IGNORE).
- Updated to LiteSpeed SAPI V7.5 (Fixed clean shutdown).
- Fixed bug #78179 (MariaDB server version incorrectly detected).
- Fixed bug #77191 (Assertion failure in dce_live_ranges() when silencing is used).
- Fixed bug #69100 (Bus error from stream_copy_to_stream (file -> SSL stream) with invalid length).
- Fixed bug #78282 (atime and mtime mismatch).
- Fixed bug #78326 (improper memory deallocation on stream_get_contents() with fixed length buffer).
Bug Fixes in Version 7.3.9
- Fixed bug #78363 (Buffer overflow in zendparse).
- Fixed bug #78379 (Cast to object confuses GC, causes crash).
- Fixed bug #78412 (Generator incorrectly reports non-releasable $this as GC child).
- Fixed bug #77946 (Bad cURL resources returned by curl_multi_info_read()).
- Fixed bug #78333 (Exif crash (bus error) due to wrong alignment and invalid cast).
- Fixed bug #77185 (Use-after-free in FPM master event handling).
- Fixed bug #78342 (Bus error in configure test for iconv //IGNORE).
- Fixed bug #78380 (Oniguruma 6.9.3 fixes CVEs). (CVE-2019-13224)
- Fixed bug #78179 (MariaDB server version incorrectly detected).
- Fixed bug #78213 (Empty row pocket).
- Fixed bug #77191 (Assertion failure in dce_live_ranges() when silencing is used).
- Fixed bug #69100 (Bus error from stream_copy_to_stream (file -> SSL stream) with invalid length).
- Fixed bug #78282 (atime and mtime mismatch).
- Fixed bug #78326 (improper memory deallocation on stream_get_contents() with fixed length buffer).
- Fixed bug #78346 (strip_tags no longer handling nested php tags).
Conclusion
We cannot stress this enough, update as soon as possible. Downloading these security patches will mitigate the risks to a bare minimum. And, install a web application firewall to check any attempted attack. The Astra firewall provides continuous protection to your website against RCE, SQLi, XSS, CSRF, OWASP Top 10 and 100+ other cyber attacks.















