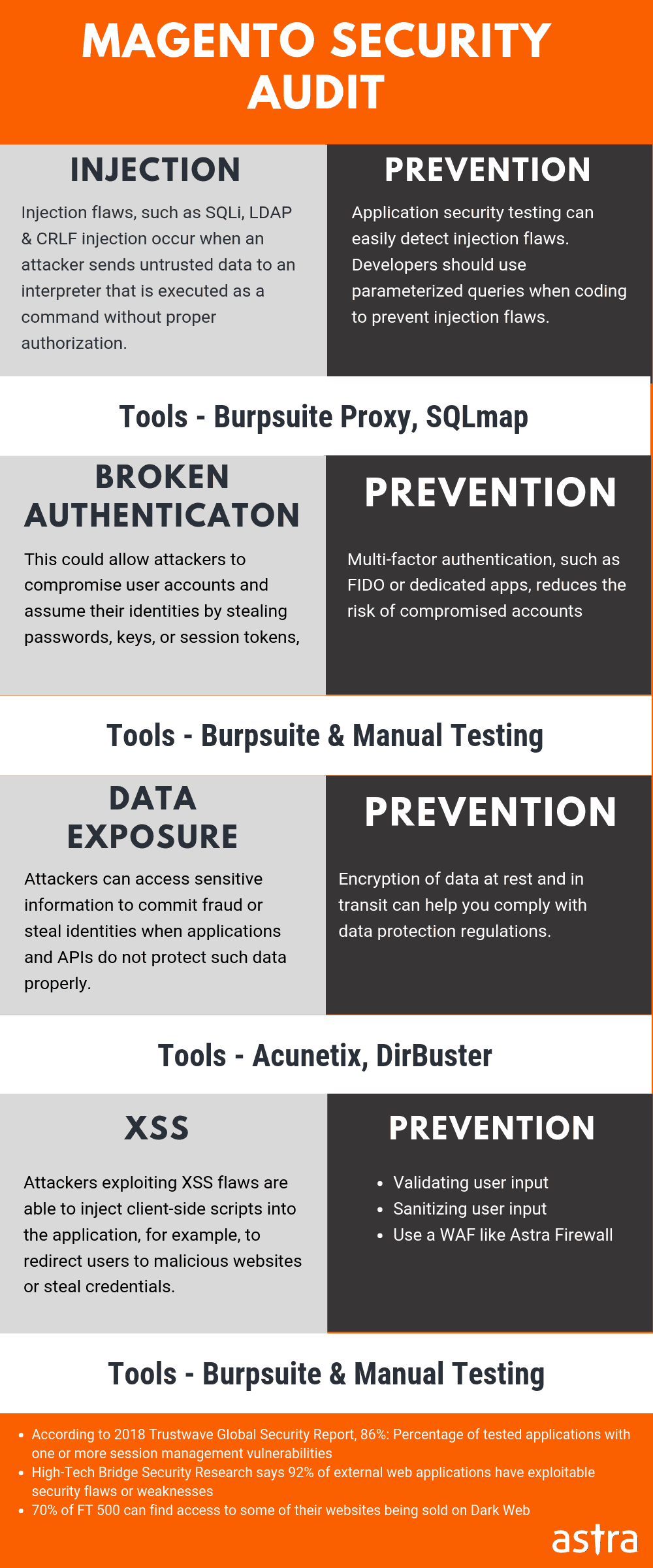
Magento 2, one of the largest open-source e-commerce platforms in the world, has often been an eye candy for people with malicious intent. No matter the amount of work gone into securing this platform, hackers tend to come up with new ways to circumvent security measures. As its reputation grows, so does the notoriety surrounding the diverse forms of malpractices possible with it. This article enlists ways in which store owners, marketing managers, e-commerce managers etc can implement essential Magento 2 security measures.
Related Guide – Complete Step by Step Guide to Magento Security (Videos, Extensions, Code & Infographs) (Reduce the risk of getting hacked by 90%)
1. Choosing the right hosting infrastructure
When choosing a hosting provider and a solution integrator, evaluate for reliability by asking about their approach to security. Verify that they work in accordance with industry standards like the OWASP security best practices and have a secure software development lifecycle.
In case you are building a new website, consider launching the site over HTTPS. This will securely encrypt your site as well as make it eligible for higher Google rankings. On the other hand for an existing website, upgrade the site to run on HTTPS.
2. Secure Environment
Ensuring that the Magento 2 security measures are in place goes a long way in disarming attackers with the means to compromise the e-commerce store. Best practices include keeping all software up to date and applying recommended security patches.
- To ensure a secure server operating system, make sure there is no unnecessary software running on the server.
- Disable FTP and make use of only secure communications protocol (SSH/SFTP/HTTPS) to manage files.
- In case you are using a server different than Apache web server, ensure that all system files and directories are protected. For example, in case of Nginx, see magento-nginx.conf on GitHub.
- Ensure that only Whitelisted IP addresses are allowed to access the admin panel. To learn how to restrict access to the Magento Admin area.
- Implement two-factor authentication for Admin logins. This provides additional security by requiring an additional passcode that is generated on your phone. Moreover, strictly restrain from using simple text passwords which can be easily guessed by a hacker.
- Secure the computer you use to access the Magento Admin Dashboard. Regularly update your antivirus software and use a malware scanner.
3. Secure Magento
-
Make sure you’re using the latest version of Magento. This entitles your installation to the most recent security enhancements. If not, make sure to install all security patches as recommended by Magento.
- Use a custom Admin URL which is unique and cannot be easily guessed. This could reduce exposure to scripts that might try to break in through your Admin URL.
- Use a strong password for the Magento Administrator account. This will make password guessing attacks difficult.
- Make use of IP whitelisting and .htaccess password protection to block access to any development, staging, or testing systems. Such systems are vulnerable to data leaks on compromise.
- Adhere to Magento’s security-related configuration settings for Admin Security, Password Options, and CAPTCHA.
4. Monitor for Signs of Attack
- Periodically review server logs for any suspicious activity. If need be, implement an Intrusion Detection System (IDS) on your network.
- Check if any unauthorized admin users have been created. You can monitor any suspicious activity, in the Admin Actions Log.
- Check the data integrity of files on the server. This can unearth any potential malware installation.
- Monitor all system logins (FTP, SFTP, SSH) for unexpected activity, uploads, or commands
5. Create a Disaster Recovery Plan
- Develop a disaster recovery/business continuity plan. Even a basic plan may help you stand on your feet in the time of need.
- Ensure there are backups of database and server files at an external location. Periodically ensure that backups are taken correctly and can be restored.
- Deploy a professional database backup solution rather than simple text file dumps of the database.
- Keep an eye for unauthorized transactions performed using cards of your customers. Alert your customers if any such incident is reported.
- In case of an attack, no matter how small, reset all credentials including those of the database, file access, payment gateway encryption keys, web services and Magento admin login, FTP, SSH etc.
Related Guide – Complete Step by Step Guide to Magento Security (Videos, Extensions, Code & Infographs) (Reduce the risk of getting hacked by 90%)
Worried about the safety of your Magento 2 store? Contact Astra’s web security suite for a comprehensive Magento Security solution.

















Nice blog. For any ecommerce site security is the most important thing. This blog contains all the detailed information about the security of magento store. So it is very useful for all the developers to protect magento store form being hacked. It is very useful blog so keep sharing such useful blogs.
Good Post, I agree that Two – Step Verification works as an additional security layer which makes difficult for attacker to hack, I learned about it on Magenticians, so do check out their Magento security Tips blog, they have listed some of the basic but best ways to secure a Magento store.