Did your website get hacked?
Attackers are increasingly using sophisticated tools and methods to break into websites and accounts. From bots to SQL injections, anything can be used to launch an attack. After an attack the looming question of “How to fix my website?” is easily answerable if you know the right steps to take. If you ever get hacked, recovering the data is the top priority. After you fix the website, you need to find out the source and plug it. The source of the attack can be anything, from weak passwords to vulnerable plugins. Thus, it is necessary that you secure all potential access points for attackers. Following this after hack checklist will help you guard against a large number of attacks and keep your website safe in general.
After hack checklist for protecting your website
1) Scan all local computers which may access this account for the presence of malware, such as Trojans, keyloggers, viruses, etc : Malware can enter websites and steal credentials through the computers that developers use to access the website’s backend. Keyloggers are special programs that capture the keystrokes on a keyboard and send the data to a hacker waiting behind the scene. When you type your password and other credentials, they get logged into the program which is analyzed by the hacker. After hacking your keyboard or the input device, on proper analysis, hackers can easily extract passwords and other credentials from this data. This is a very common way to attack and you can prevent this by using onscreen keyboards. Avoid using wireless keyboards since the Bluetooth, or the Wi-Fi signal are hackable, and an attacker can access all the keystrokes.
Viruses and malware easily spread through online programs or infected removable devices. Avoid inserting any unknown or untrusted removable devices on your computers. The viruses and malware are not visible on the surface, and thus users are unaware of their presence. Once they activate within the computer, they can spread through the computer to the website. To avoid any infections, try using antivirus software from a reputed company. This is apparently the first step in the list of after hack steps. If there is more than one developer for a single website then buying a group subscription for all the computers is the best step. This will protect the accounts and prevent any spread of malware through the computers.
Facing security issues with your website? Drop us a message on the chat widget and we’d be happy to help you. Fix my website results now.
2) Update all logins associated with your account, using strong passwords, including FTP, database, and applications etc: This is one of the most important steps in this after hack list. We use passwords to secure everything from our social media accounts to our bank accounts. Most of us believe that having a password containing special characters and alphanumeric characters can protect the password from attackers, which is a common misconception. The secret to an effective password is the length. Edward Snowden, a world-renowned whistle-blower suggest using an uncommon phrase which is long, as a password. The longer the passwords, the more computational strength it will require to crack. Attackers often go after hackable passwords or pins.
Check some of our blogs on outdated plugin and theme hacks.
Moreover, we ignore certain areas which we feel do not require passwords such as databases and applications. Try adding passwords to all necessary places which earlier did not have one. This will make it tough for hackers to enter the account and they will have to spend considerable time and energy to tackle the security checkpoints on each level. Two-step verification is also another great way to enforce security of your accounts and applications.
3) Update and maintain all hosted applications and their add-ons (plugins, themes, widgets, modules, etc.) with the most current, secure, versions: Staying updated can be helpful in a number of areas such as making the system faster and increasing functionality. Updates also ensure that the security protocols are updated and are able to protect the accounts against the latest threats. A number of plugins and add-ons provides security patches. Such as Magento patches are necessary if you use Magento for your website. Using old plugins or not updating them will make them vulnerable to newer threats and attacks such as SQL injection. Such attacks are constantly updating and changing themselves. Moreover, an attacker can take control of your website after hacking these plugins. Thus, updating the plugins or opting for newer plugins is probably a good option if you are serious about the security of your account.
4) Review all hosted content for malicious and unrecognized files, and clean/remove/replace content as necessary: Uploading infected files can spread malware throughout the account quickly and will compromise the security. That may also be the source of the attack on your website. Thus, it is necessary to scan all uploading files and content to avoid any damage to the account. By using security services such as Astra, you can easily monitor all content for any viruses or signatures of corrupted scripts. So, scan all existing files and contents on your website. Moreover, use an online web security service to scan all incoming files and new content on the site before publishing.
5) Add a Captcha, or human verification method, to all submission style forms or comment sections that you have on any sites in the hosting. This includes any login pages for CMS application or anything that has fields to enter content with a submission button of some type: This is one of the steps in this after hack checklist that a number of users ignore. Captcha is a very innovative way to identify if the user is a bot or a human. We often see Captchas when we visit login pages or in comment sections. Identifying the user will help us prevent any incidents of hacking on the website.
In the history of hacking, bots have successfully launched and carried out attacks on websites and companies. Bots also scrape data from websites and may compromise the information of clients and users stored on the website. Bots also can log in to the website by conducting brute force attacks on the login credentials. Eliminating the bots from accessing the website and certain sections can stop attacks and data thefts. You can also take help from this checklist to secure your website.
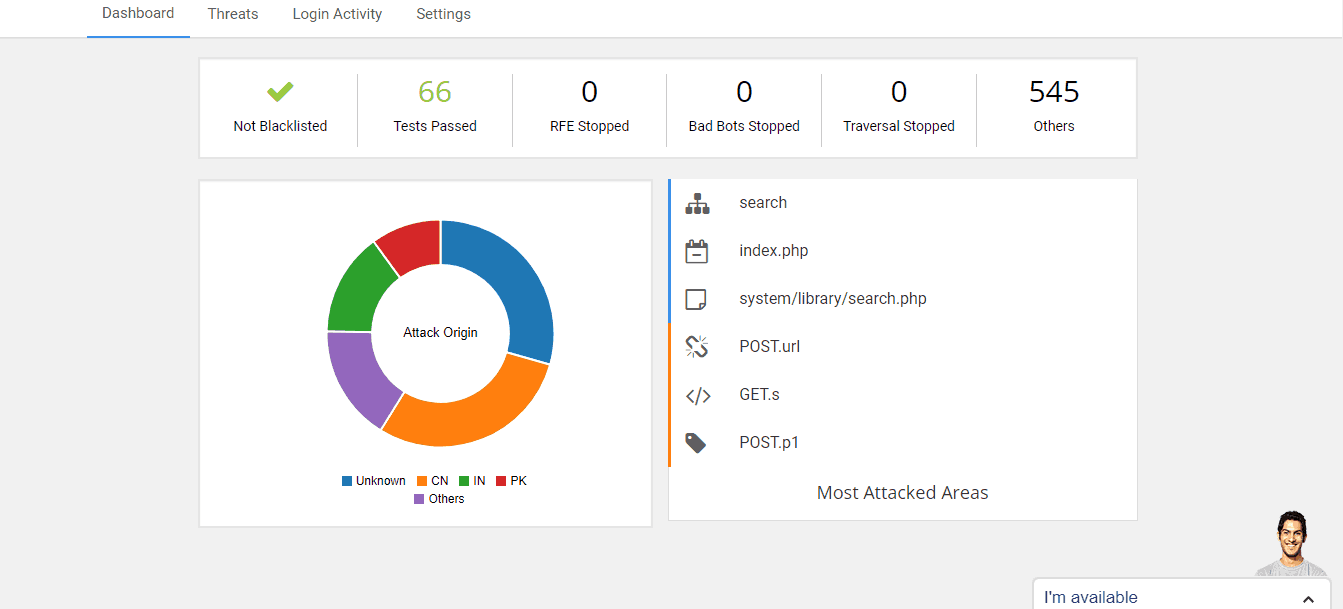
These after hack steps will surely help you keep your website safe since any downtime is harmful to the reputation of your website. However, for complete security of your website, you will require dedicated services that employ security tools and software. This is where services like Astra can help us. They provide the complete palette of website security. With their help, you can rest assured that all areas of your website are secured and safe from attackers. With the help of their rock-solid web security features and plans, they can clean your hacked website and prevent repeated attacks.
















