The rapid evolution of technology has led businesses and individuals alike to embrace the cloud for its convenience, scalability, and cost-efficiency. However, as the cloud soars higher, so do the security challenges that come with it. In this article, we will explore the latest cloud security trends and innovations that are shaping the future of data protection in the digital era. Buckle up as we unveil the key strategies and cloud security trends that will help you safeguard your data vaults amidst the clouds!
Key Takeaways
- Opt for the zero-trust model of cloud security where everyone has to be continuously authenticated and authorized on different parameters to gain access.
- Use AI-driven threat detection to analyze massive amounts of data to detect anomalies, vulnerabilities, & suspicious activities.
- Enable MFA (multifactor authentication) for added security to reduce the risk of unauthorized access.
- Encrypt data that is being processed by memory, not just those in transit.
- Implement user and behavior analytics to conduct real-time monitoring for the detection of suspicious user behavior to enhance your IAM’s capacity.
- Integrate security and security testing into your SDLC pipeline rather than implementing it later.
6 Trends in Cloud Security
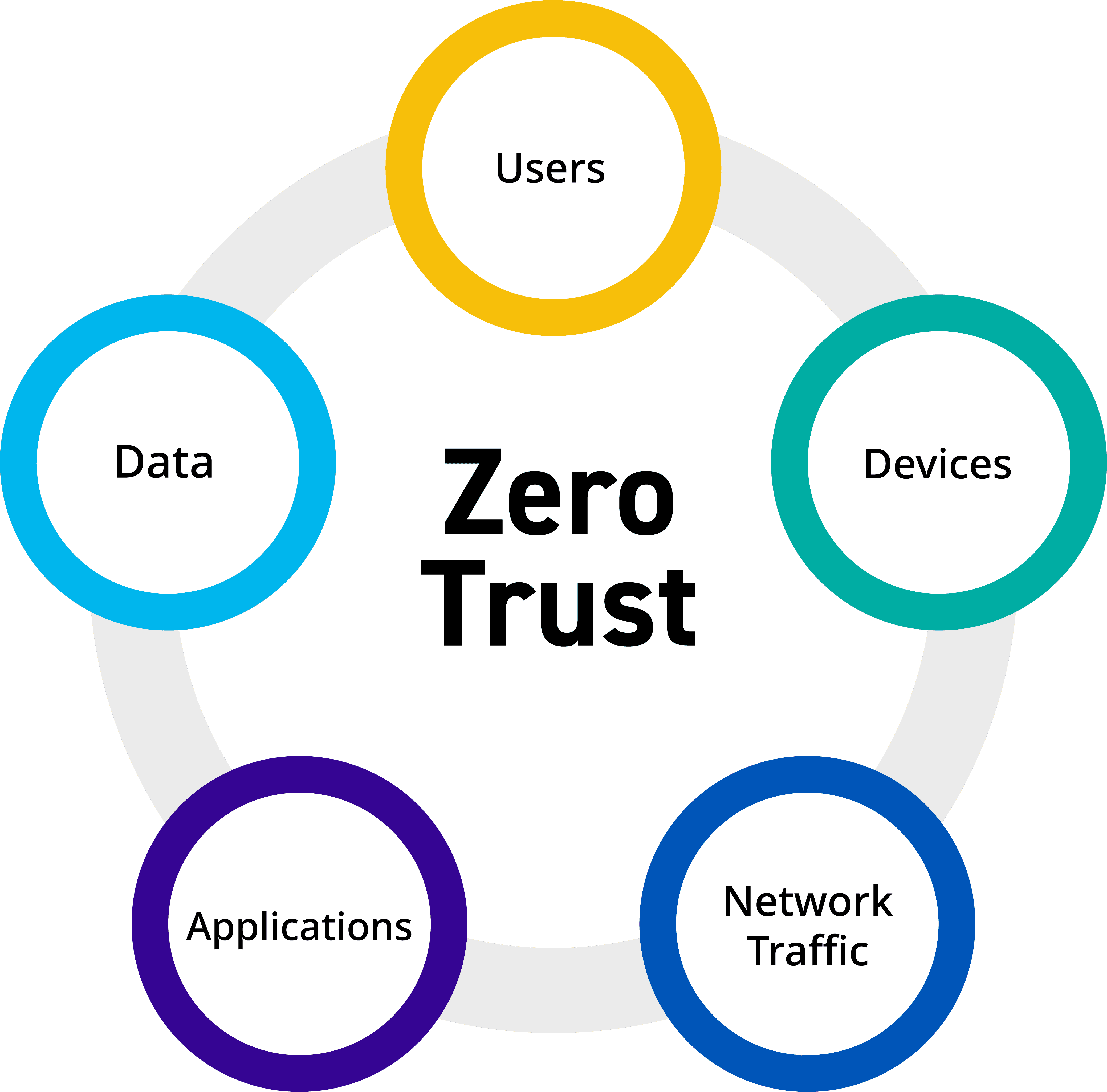
1. Zero Trust: Trust No One, Verify Everything
Gone are the days when the perimeter-based security model was sufficient to protect data. With the rise of cloud adoption and the proliferation of remote work, the Zero Trust model has gained prominence in the context of trends for security in cloud apps. It operates on the principle of “trust no one, verify everything.” In this context, users are continuously authenticated and authorized based on various factors like device health, location, and user behavior. This ensures that only legitimate users gain access to sensitive data, even if they are working outside the corporate network.
2. AI-Driven Threat Detection: The Watchful Eye in the Sky
As cyber threats become more sophisticated, traditional security measures may not suffice. Enter Artificial Intelligence (AI)-driven threat detection, which serves as the watchful eye in the sky. AI algorithms continuously analyze massive amounts of data to identify anomalies, potential breaches, and suspicious activities. This proactive approach helps businesses detect and mitigate threats before they can wreak havoc on the cloud infrastructure. AI-driven threat detection remains one of the major cloud security trends.
3. Multi-Factor Authentication (MFA): The Golden Lock for Cloud Entry
Passwords alone are no longer enough to ensure secure access to cloud services. Multi-Factor Authentication (MFA) adds an extra layer of protection by requiring users to provide multiple forms of identification before gaining entry. This may include something they know (password), something they have (smartphone), and something they are (biometric data). MFA significantly reduces the risk of unauthorized access, ensuring the cloud remains a fortress of data security.
4. Confidential Computing: Encrypting Data in Use
Cloud security trends are not just about securing data at rest or in transit; it also extends to protecting data while it’s being processed in memory. Confidential Computing addresses this concern by encrypting data while it is in use. This allows cloud providers to perform computations on encrypted data without ever exposing the actual information. As a result, sensitive data remains shielded even from potential insider threats or malicious actors targeting the cloud infrastructure.
5. Identity and Access Management (IAM) Enhancements
IAM remains a critical aspect of cloud security, and continuous enhancements in this area are inevitable. New trends in cloud security management are emerging, such as adaptive access controls, which dynamically adjust access privileges based on user behavior, context, and risk assessment. User and entity behavior analytics (UEBA) is another area gaining traction, providing real-time monitoring and detection of anomalous user behavior, helping prevent unauthorized access or insider threats. These IAM enhancements add an extra layer of protection and contribute to a more comprehensive security framework.
6. DevSecOps: Integrating Security into the Cloud Pipeline
In the past, security was often an afterthought in the development and deployment of cloud applications. However, rising cloud security trends of DevSecOps has changed the game. DevSecOps integrates security practices into the entire cloud development pipeline, ensuring that security measures are not compromised in the quest for faster deployments. This seamless collaboration between developers, IT operations, and security teams enhances the overall security posture of cloud-based applications.
Evolution of Cloud Security
Cloud security’s evolution in the years since the COVID-19 pandemic has been drastic. Around 55% of organizations mentioned that employees would continue working remotely at least once a week post-pandemic. Keeping this major variable in mind, companies competitively upped the measures of cloud security offered.
The 2020 period proved to be an unprecedented challenge for all IT leaders, in terms of shifting key working infrastructure without increasing costs or cutting short on security. With cloud technologies and the dependency on them from companies increasing rapidly, it is clear that the future of cloud security highly hinges on constant improvement in the current trends and the development of newer security measures. This will ensure the protection of the cloud and its assets from any emerging threats.
Current State of Cloud Security
Cloud security is at a pivotal point in its evolution. While concerns over misconfigurations, data leaks, and theft still are a looming possibility within the cloud, the security landscape has improved dramatically over the past years.
The use of various cloud security trends such as shifting to a Zero Trust Security Model, relying on AI-enhanced threat detection for more accurate identification of threats, implementing IAM enhancements, and using MFA are certainly playing a part in keeping your assets safe and secure in the cloud.
Navigating cloud security’s ever-changing landscape can be challenging. However, with the remote work environment amplifying, focusing on fortifying one’s cloud security will pan out well in the future.
Darkside of Cloud Security Trends
Despite the most recent advancements in the field of cloud security, concerns remain in the form of emerging threats. With more and more businesses shifting their operations to the cloud, newer exploitable vulnerabilities and risks emerge.
Other persistent issues within the current state of cloud security include misconfigurations, and a lack of vulnerability assessments or penetration tests to detect any emerging vulnerabilities. The rapid adoption of cloud technologies often poses a challenge to the security measures maintained to protect them. These initial lapses in security implementation can easily be taken advantage of by malicious attackers.
Lastly, a major area of challenge in effective cloud security is the user’s awareness of it. The shared responsibility model reasons that both users and providers are responsible for different aspects of cloud security. If the user does not have adequate awareness of their cloud security responsibilities, that itself is cause for concern and must be addressed immediately.
Leverage Astra Security to keep up with Cloud Security Trends
In the ever-evolving landscape of cloud security trends, Astra Security stands out as a leading player in the field of security audits. As companies increasingly rely on the cloud for their data storage and operations, the need for thorough security assessments becomes paramount to keep up with the changing cloud security trends. Astra Security’s comprehensive approach to security audits aligns perfectly with the emerging security trends in cloud computing.
In the context of cloud security trends, Astra Security’s unique blend of automated and manual pentesting offers a cutting-edge solution to identify and mitigate vulnerabilities in cloud infrastructures. This approach ensures that cloud environments are thoroughly tested, reducing the risk of false positives and providing accurate assessments.
Astra Security checks for compliance with various international security regulations and standards, such as ISO 27001, SOC2, HIPAA, GDPR, and PCI-DSS to keep with cloud security trends. Astra Security facilitates seamless collaboration by integrating with CI/CD pipelines. This integration allows organizations to assess their security posture throughout the cloud development and deployment stages, supporting the shift towards DevSecOps practices.
Cloud security is not a one-time event; it requires continuous monitoring and support. Astra Security’s 24×7 team of expert auditors ensures that organizations have round-the-clock support to address any security concerns promptly, aligning with the trend of proactive security measures in the cloud.
We offer a range of testing services that are customizable and tailor-made to suit your needs and to keep up with the emerging security trends in cloud computing.
These include:
1. Vulnerability Assessments and Penetration Testing
Astra Security provides both manual and automated vulnerability assessments & penetration testing for assets. Our intelligent vulnerability scanner is capable of testing for 8000+ vulnerabilities and is deployed to detect and identify vulnerabilities.
Additionally, for penetration testing, these vulnerabilities are exploited manually by Astra’s experienced pentesters or through automated pentesting. Brute forcing, fuzzing, and injections are some of the tests carried out on the vulnerability to try further access.
2. Vulnerability Scanning
Astra provides manual and automated vulnerability scans. Manual scans are carried out by expert cybersecurity testing professionals at Astra. These scans are comprehensive and personalized per customer requirements.
Automated vulnerability scans by Astra Vulnerability Scanner are further available in three different categories.
– Lightening: Super quick scan for vulnerabilities that takes around 9-10 minutes.
– Emerging: Targeted scans that check for the emerging or latest vulnerabilities mentioned in the world of cyber security.
– Full Scans: Complete in-depth automated scans that scan for well-known vulnerabilities, CVEs, OWASP Top 10, SANS Top 25, and newer ones from bug bounty reports
3. Free Website Scanner
Astra provides a free website scanner that checks for basic vulnerabilities, blacklisting, and SEO spam.
Future Of Cloud Security Trends
The future of cloud security will see advancements in trends that are focused on improving digital fortifications. AI-driven threat detection zero-trust platforms, and other automated security measures have immense potential in helping mitigate emerging threats.
With remote working environments on the rise, the focus is likely to shift towards securing endpoints while also increasing data encryption measures. Moreover, continuous monitoring, holistic user training, and proactive threat intelligence will become integral in maintaining robust cloud security.
As the digital landscape continues to evolve, a collective effort involving industry collaboration, the latest solutions, and adaptive strategies will become more important in ensuring a resilient, well-protected cloud security system.
Conclusion
As the cloud landscape continues to expand, so do the challenges surrounding data security. Embracing these cutting-edge cloud security trends is imperative for businesses and individuals alike to protect their sensitive information from cyber threats. Zero Trust, AI-driven threat detection, MFA, Confidential Computing, and DevSecOps are all indispensable tools in the cloud security arsenal. By staying ahead of the curve and implementing these strategies, you can safeguard your digital assets amidst the vast expanse of the cloud, ensuring a secure and uninterrupted flight to success.