Being a successful e-commerce platform, PrestaShop, no doubt, is a lucrative target for hackers. Hackers are continuously on the hunt for an overlooked vulnerability in popular CMS(s). They are always on the lookout for new methods to deliver their payload like injecting malware in the traffic of open Wi-Fi via ARP poisoning. Further, PrestaShop Malware is any kind of malicious code deployed by the hackers via a vulnerability in order to exploit a Prestashop store.
According to the book Learning Malware
Analysis,
The growing threat of cyber attacks on critical infrastructure, data centers, and private/public, defense, energy, government, and financial sectors poses a unique challenge for everyone from an individual to large corporations. These cyber attacks make use of malicious software (also known as Malware ) for financial theft, espionage, sabotage, intellectual property theft, and political motives.
If you have been wondering about the various types of Prestashop malwares and how to protect yourself from them, then look no further. This article is the remedy you need.
Related article:
PrestaShop Malware Injection: Modes of Delivery
PrestaShop malware injection can be executed by the following:
Code Vulnerabilities
Prestashop malware infection most likely occurs due to buggy code. This is applicable for both core files and plugins. Let us take a look at some common vulnerabilities and how they can be used to inject PrestaShop malware.
Get the ultimate Prestashop security checklist with 300+ test parameters
SQL Injection in PrestaShop
An SQL vulnerability can be used to inject malicious code in the tables of PrestaShop store. In some cases, the SQLi vulnerability can be used to upload files to the server. Therefore, in such cases, the attackers can upload malicious script on the PrestaShop store web server. PrestaShop was vulnerable to an SQLi flaw, which was dubbed as CVE-2018-8824.
Related article- Consequences of SQL Injection in PHP website and CMS
Cross-Site Scripting (XSS) in PrestaShop
If the PrestaShop store is vulnerable to an XSS vulnerability, the attackers can directly inject malware in case it is a stored XSS vulnerability. If the vulnerability is a reflected XSS, the attackers can send a specifically crafted URL to the admin of the Prestashop store. This can then load a malicious script from the attacker-controlled server thereby injecting PrestaShop malware. PrestaShop 1.7.2.4 was found vulnerable to XSS which was dubbed as CVE-2018-5681.
Remote Code Execution in PrestaShop
Remote code execution vulnerability can allow the attackers to interact with the server of PrestaShop store directly. Therefore, if the PrestaShop store is vulnerable to an RCE, the attackers can directly inject malware into the legitimate pages of the website. This type of malware can be hard to detect if the code is obfuscated. PrestaShop (1.5 through 1.7) was recently found vulnerable to an RCE, which was dubbed as CVE-2018-19355.
Social Engineering and Drive-By Downloads
Social engineering attacks are relevant even to this day to deliver malware payload. At times the attackers can inject malware into the Prestashop store on the pretext of offering ‘Customer Support’. Often, the email of the Prestashop store’s web admin is targeted by attackers to conduct drive-by downloads. Which means the web admin is tricked into clicking a URL and therefore malware is silently installed on the Prestashop store. Prestashop versions up to 1.7.2.5 were found vulnerable to an UI-Redressing/ Clickjacking security issue. This allowed the attackers to hide malware behind legitimate buttons or links. Social engineering can also be combined with reflected XSS as mentioned above to deliver Prestashop malware.
Zero-day and Trojans in PrestaShop
At times, the attackers can get to lay their hands upon some uncovered vulnerabilities in the Prestashop. These are then used by attackers to conduct large scale malware attacks on multiple Prestashop installations on the web. Also, there have been instances when hackers have targeted the software from its core repository server and injected it with malware. For instance, the PHP Pear package manager was injected with malware from its official site. Such type of Prestashop malware which looks like a legitimate software is known as a Trojan.
Malicious Adverts in PrestaShop
As mentioned before, hackers evolve new ways to inject Prestashop malware every day and using adverts to deliver malware is another example. In case you have rented some of your web space for advertisement, it can be purchased by attackers to deliver malware to your customers. Detection of such malware can be difficult as everything may seem to be clean from your side but the Prestashop malware infection is being caused due to malicious advertisements.
Types of PrestaShop Malware:
PrestaShop Malware: Cryptocurrency Miner
This variant of Prestashop malware intends to use the processing power of your server and users visiting your Prestashop store to mine cryptocurrency. A simple crypto miner malware contains code that looks something like this:
<script src=”https://authedmine.com/lib/simple-ui.min.js” async></script>
Coin hive is a legitimate service which is frequently abused by hackers due to its ease of implementation. This is just a simple variant of the malware. More complex crypto mining malware obfuscate their code and therefore are not easy to detect. One variant uses non-dotted decimal notation for the hostname. Moreover, to hide this Coin hive library, the malware uses a fake jQuery script. It also uses miner variable names similar to Google Analytics parameters to evade detection.
PrestaShop Malware: Ransomware
PrestaShop ransomware is the malware which encrypts the system files and renders the system unusable. Thereafter, only one file, typically index.php is visible which contains a message asking for bitcoin payment to a particular address. What is more malicious here is that even after the payment of ransom, there is no assurance that the files will be decrypted. Removal of such malware is not difficult but recovery of the server data becomes a challenging task. Some ransomware attacks like wanna cry have crippled critical systems all over the world therefore, in this scenario prevention seems to be the best cure.
PrestaShop Malware: Credit Card Skimmer
Some types of PrestaShop malware are customized to steal the transaction info from your PrestaShop store. The code snippet from one such malware is given in the image below.

As evident from the code, this malware firstly establishes a database connection. Thereafter, the malware steals the following info from the ps_payment_cc table:
- Payment ID of the transaction.
- Credit Card Number.
- Brand name of the credit card.
- Credit Card Expiry Date.
After, getting these details, the malware siphons off these details to attacker-controlled servers.
Related Article – Fixing Card Hack in PrestaShop
PrestaShop Malware: Viruses
PrestaShop viruses can perform a variety of malicious operations on your store. These can range from a harmless prank to deleting the entire file system! However, to maintain persistence, PrestaShop viruses need to obfuscate their code. Since PrestaShop is built using PHP, a typical virus signature could be something like the ‘php.malware.fopo‘ virus as shown in the image below.

As seen in the image, the FOPO has made the code unreadable to humans thereby evading detection. In order to read the code for malware removal, a FOPO deobfuscator is required. Some plugin developers of PrestaShop use FOPO tool to protect their code. So, detection of this malware becomes complex and should never be done by untrained professionals. Moreover, this is a reference of a generic PrestaShop virus and there are multiple such complex viruses so covering each and everyone is beyond the scope of this article.
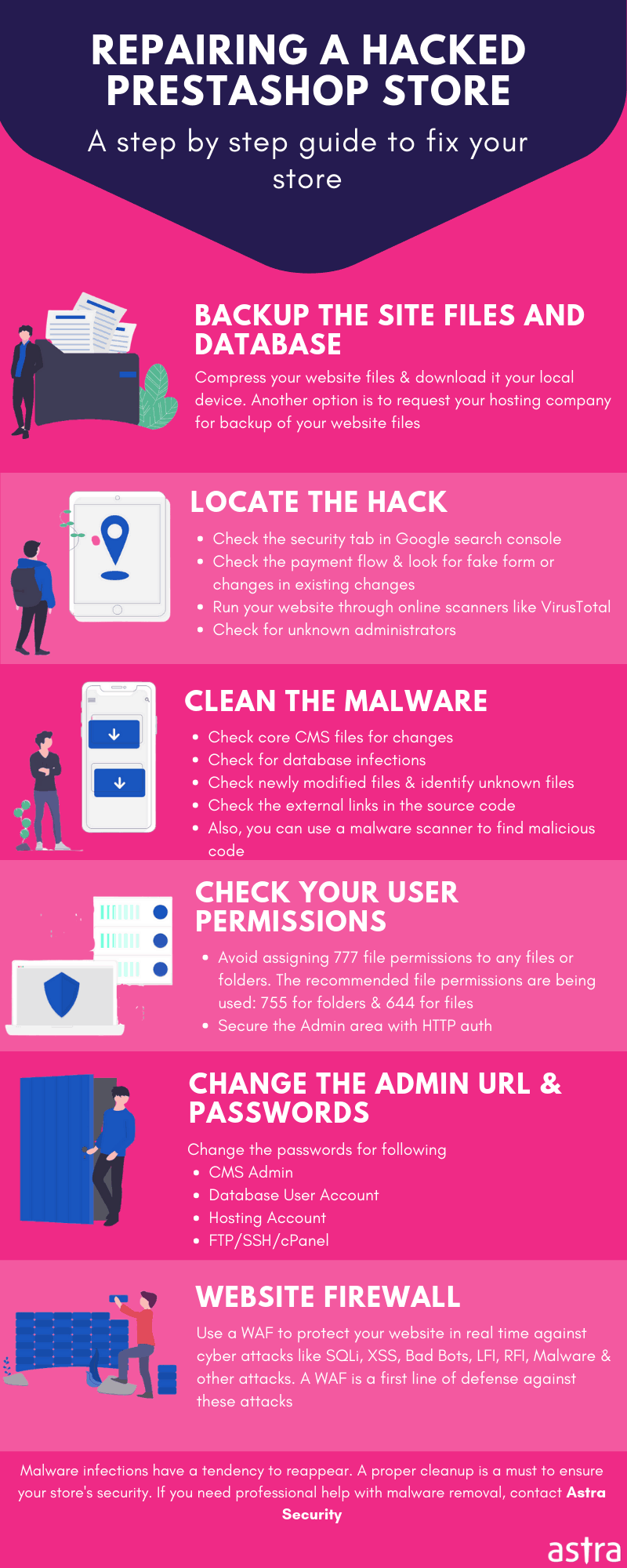
PrestaShop Malware Removal
In case your store is infected with PrestaShop malware, it is advised to begin by taking a look at the filesystem. Since PrestaShop uses PHP, hackers modify PHP configuration files like php.ini , user.ini, etc. These files are also responsible for permission setting of the system and therefore can provide greater resources to the attackers. Another such crucial file is the .htaccess file. This file is modified by the PrestaShop malware to redirect a site’s traffic to a spam site. However, since these files are sensitive do not delete the code you find suspicious. Instead, comment it out and contact security experts. To find the PrestaShop malware hidden in base 64 format, use this command via SSH:
find . -name “*.php” -exec grep “base64″‘{}’; -print &> code.txt
This command will search all the code hidden in PrestaShop files in the form of base64 encoding and save it to the code.txt file which can be decoded later. Apart from base64 encoding, FOPO is also used to hide code. FOPO code can be obfuscated using the tools available online. Now to clean the database, use the PHPMyAdmin tool. This tool can be used to search for malicious entries in the database. Some malicious keywords to look out for are:
$_POST, $_GET , eval, exec ,system, passthru, gzdecode, gzuncompress, base64_decode, file_get_contents, file_put_contents, strtoupper.
Each of these terms can be individually entered into the phpMyAdmin and searched for within the files or tables. Look at the example shown in the image below.

Ultimate PrestaShop Malware Protection
All this manual process seems to be tiresome and there is still no guarantee that the PrestaShop malware infection will go away. To avoid this hassle, use a security solution as the one Astra provides. Astra firewall blocks all the malicious attempts made by attackers to infect your PrestaShop store. While the Astra security solution scans your file system for infection. Astra automatically cleans and updates your PrestaShop files. Just install Astra and let it take care of everything.