Dwarfing Japan’s GDP twice, cybercrime is estimated to reach 9.2 trillion in 2024. So, how can enterprises and security analysts mitigate such threats?
While hundreds of penetration testing tools promise robust cybersecurity for enterprises and analysts, finding your perfect match is like looking for a needle in a haystack.
Thus, our security experts have handpicked the 17 best penetration testing tools that focus on your non-negotiables, including but not limited to cost, timeline, functionality, technical knowledge, deployment, and pentest capabilities.
17 Most Popular Penetration Testing Tools of All Time
- Astra Pentest
- Burp Suite Professional
- Cobalt Strike
- Rapid7
- Acunetix
- Nessus Professional
- IndusfaceWAS
- Kali Linux
- NMap
- Wireshark
- Nikto
- W3af
- Aircrack-ng
- BeEF
- Ettercap
- Vega
- ZAP
Choosing a Pentest Tool: Enterprise vs. Security Analyst
Although both companies and analysts utilize pentesting tools, needs and considerations naturally differ.
Companies and enterprises often look for a complete suite of tools that caters to multi-asset infrastructures and appeals to all the stakeholders using the tool. They prioritize tools that offer end-to-end pentesting, vulnerability management, and support, generate comprehensive reports, and integrate seamlessly with existing workflows.
Conversely, security analysts are concerned with individual tool capabilities such as effectiveness, flexibility, ease of use, and specific asset specialization. Security analysts might also prioritize Vulnerability Assessment tools over Penetration Testing tools that aren’t deployed on the company-wide network, and analysts are usually the sole users.
This table highlights the key differences between choosing a Pentest Tool as an Enterprise vs choosing a Pentest Tool as a Security Analyst:
| Features | Pentest Tool for Enterprises | Pentest Tool for Security Analysts |
|---|---|---|
| Managing End-to-End Pentests | Essential for scheduling, assigning, and tracking tests | Not applicable, pentester focuses on hacking the given scope |
| Generate Custom Reports | It is crucial for presenting findings to stakeholders and regulators | Might not be necessary, depending on individual reporting requirements |
| Deployment Capabilities | On-premise or cloud deployment based on the company’s policies | Portable and usable on personal computers |
| Acceptance of Reports | Requires reports accepted by industry standards and customers | Value detailed findings over report formatting |
| Collaboration | Enables team collaboration and knowledge sharing | Primarily for individual use |
| Workflow Integrations | Integrates with existing security platforms, ticketing systems & CI/CD | Not essential, they value tool functionality over integration |
On the other hand, some common traits resonate with both enterprises and security analysts:
1. Effectiveness:
Both enterprises and analysts look for tools that effectively uncover vulnerabilities in the given scope. The ideal pentesting tool takes an offensive approach to uncover vulnerabilities.
SQLMap is an excellent example of how it probes the application for SQL injection, and once there’s a sign of the vulnerability, it exploits it. Ultimately, a pentest tool is judged by its effectiveness, among others.
2. Cost:
Enterprises seek cost-effective penetration testing solutions that deliver results without compromising quality. On the other hand, security experts prioritize open-source or flexible pricing tools.
3. Asset Specialization:
Enterprises look for pentesting platforms that target their unique infrastructure and applications, while security analysts seek tools tailored to specific assets like web applications, mobile devices, or cloud environments.
4. Accuracy:
Enterprises rely on the accuracy of vulnerability and attack vector identification to prioritize remediation efforts. Conversely, security professionals rely on accurate findings to build trust and deliver credible reports.
Why Astra is the best in pentesting?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- Our automated scanner scans for 9300+ vulnerabilities
- Vetted scans ensure zero false positives
- Our intelligent vulnerability scanner emulates hacker behavior & evolves with every pentest
- Astra’s scanner helps you shift left by integrating with your CI/CD
- Our platform helps you uncover, manage & fix vulnerabilities in one place
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Types of Penetration Testing Tools
1. Open-Source Tools
Freely available and community-driven, open-source pentesting tools are often the starting point for budget-conscious security analysts and bootstrapping startups. Some prime examples include – OWASP ZAP for web app exploration and SQLmap for uncovering SQLi vulnerabilities.
Open source is the backbone of the cyber security industry! However, the learning curve for using open-source tools is often steep, false positives are possible, and ongoing maintenance is typically required.
2. Web App Pentest
Dynamic Application Security Testing (DAST) tools like Astra or Burp Suite automate vulnerability scans, while Static Application Security Testing (SAST) tools like Checkmarx scrutinize source code for hidden faults.
While web app penetration testing tools are efficient for common vulnerabilities, they necessitate manual help to identify complex flaws like payment gateway hacks.
3. Network Pentest
Automated network penetration tools such as NMap and Nessus leverage vast databases to identify open ports, outdated software, and misconfigurations.
However, with manual vetting and technical monitoring, they can easily navigate intricate network topologies and often generate many false positives.
4. Mobile Pentest
Unlike the above, mobile application penetration testing necessitates a different playbook. A popular tool like MobSF can assist with static analysis.
However, manual pentest is the only option for a security analyst to scan the app’s source code, analyze its network traffic, and exploit device and platform-specific vulnerabilities.
5. Cloud Pentest
While cloud providers offer shared responsibility models, securing your configurations remains crucial. Some of the best penetration testing tools, like CloudSploit and Prisma Cloud, assess cloud infrastructure for misconfigurations and insecure settings.
Nonetheless, a probe for complex issues, such as insecure API integrations and inadequate data encryption practices, calls for a deeper approach.
6. Automated Pentest
Automated penetration testing tools, integrated into the Software Development Lifecycle (SDLC, provide unique continuous vulnerability detection. Tools like Nexpose and Qualys automate vulnerability detection and reporting, enabling rapid remediation.
However, automation has limitations in uncovering complex vulnerabilities and requires human expertise for scoping and prioritization.
7. Penetration Testing as a Service Platform
PTaaS Platforms leverage human intelligence, automated tools & agile delivery methodologies to find vulnerabilities in a given scope continuously. Providers such as Astra and Rapid7 conduct comprehensive assessments to deliver tailored reports and actionable insights.
They are ideal for enterprises looking for end-to-end, flexible, and cost-effective penetration testing solutions.
Key Features to Look for While Choosing a Pentest Tool
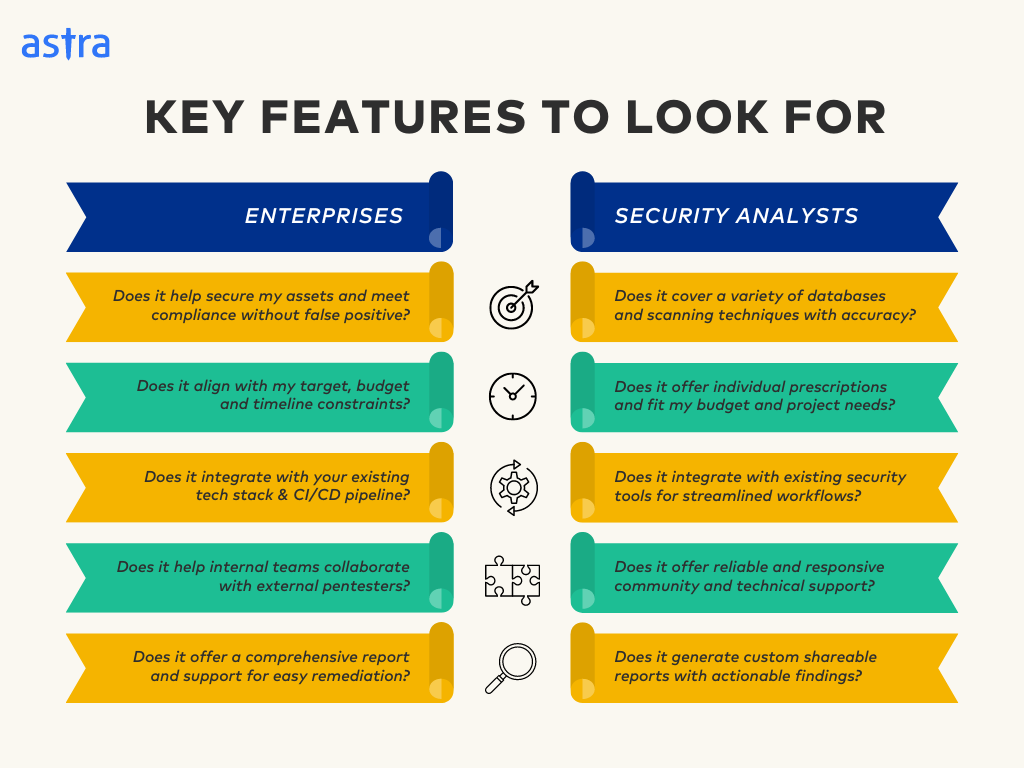
Use Our Pentest Tools Chooser
Confused about which pentesting tool is best for you? Our chooser helps you make the perfect decision based on your specific needs.
17 Best Penetration Testing Tools for Companies & Pentesters in 2024
The Complete Pentest Platform: Astra Pentest
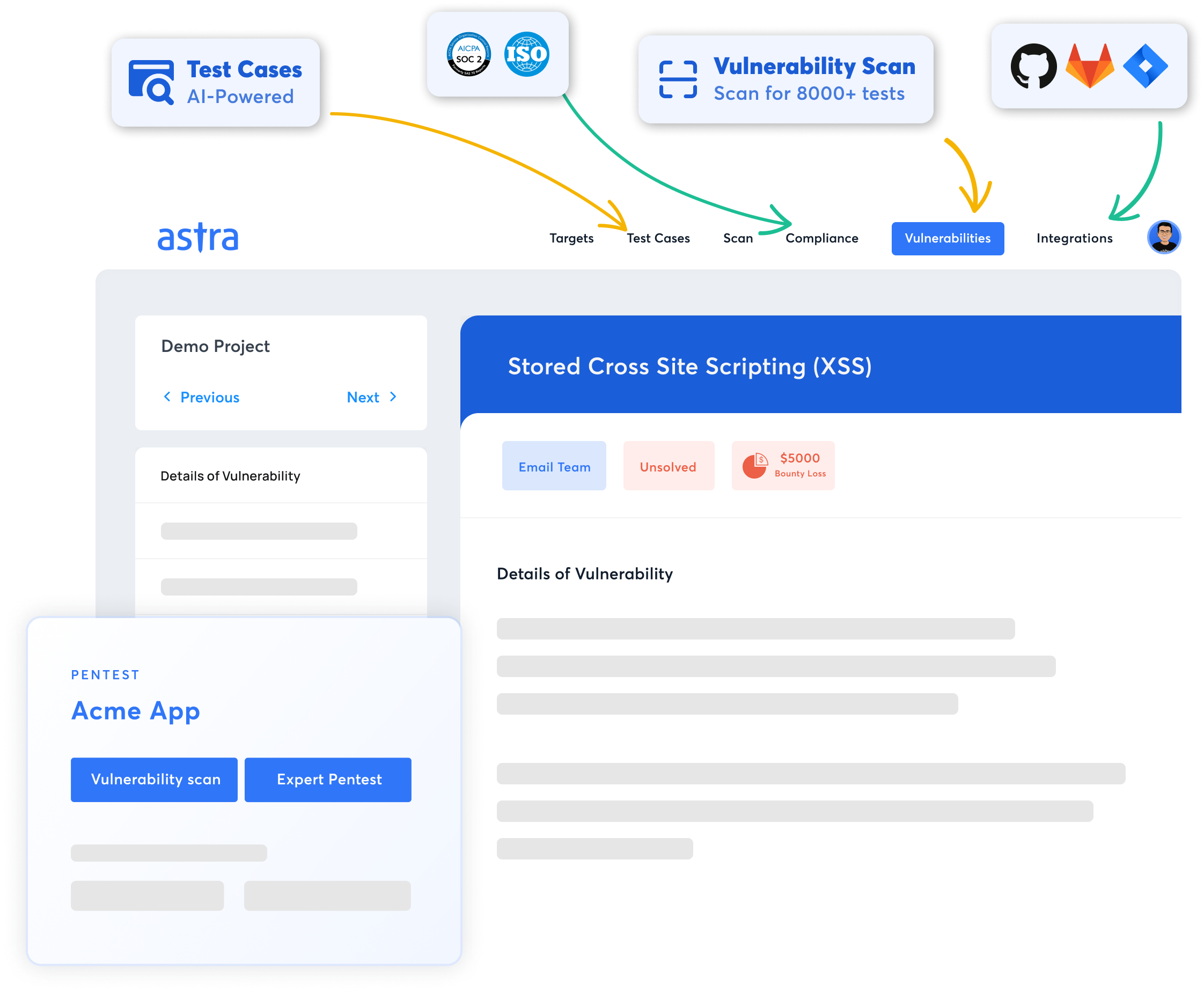
Key Features:
- Platform: Online
- Pentest Capability: Continuous automated scans with manual tests
- Accuracy: Zero false positives
- Compliance: PCI-DSS, HIPAA, ISO27001, and SOC2
- Expert Remediation: Yes
- Integration: Slack, Jira, GitHub, GitLab, Jenkins, and more
- Price: Starting at $1999/yr
The Astra Pentest Platform is a comprehensive penetration testing suite that combines our automated vulnerability scanner with AI and manual pentesting capabilities in compliance with various industry standards, including OWASP TOP 10 and SANS 25.
While expert-vetted scans ensure zero false positives, the in-depth hacker-style manual penetration tests reveal critical vulnerabilities like payment gateway hacks and business logic errors.
The plug-n-play SaaS tool includes a convenient Chrome extension for login recording, enabling authenticated scans behind login pages without redundant reauthentication.
All in all, with over 50 years of combined experience of security engineers and a portfolio of 9,300+ automated test cases and compliance checks, Astra empowers enterprises and security analysts to achieve their security goals.
Pros:
- Seamlessly integrate with your CI/CD pipeline
- Continuously scan for vulnerabilities with regularly updated scanner rules
- Collaborate with security experts with OSCP, CEH & CVEs under their name
- Rapidly prioritize and remediate vulnerabilities
- Generate custom executive and developer-friendly reports
Limitations:
- Only a 1-week free trial is available
Penetration Testing Platforms for Enterprises:
| Features | Astra Pentest | Burp Suite | Cobalt Strike |
|---|---|---|---|
| Pentest Capabilities | Continuous automated scans with manual tests for multiple assets | Automated and manual scans for web apps | Automated adversary emulation and manual penetration testing for networks |
| Accuracy | Zero false positives | False positives possible | False positives possible |
| Compliance | PCI-DSS, HIPAA, GDPR, ISO, PCI-DSS & SOC2 | PCI-DSS, OWASP Top 10, HIPAA, and GDPR | - |
| Expert Remediation | Yes | No | No |
| Workflow Integrations | Slack, Jira, GitHub, GitLab, Jenkins, and more | Slack, Jira, Jenkins, GitLab, and more | Outflank Security Tooling and Core Impact |
| Pricing | Starting at $1999/yr | $449/yr/user | Available on quote |
1. Burp Suite Professional
Key Features:
- Platform: Windows, macOS, Linux
- Pentest Capability: Automated and manual scans for web apps
- Accuracy: False positives possible
- Compliance: PCI-DSS, OWASP Top 10, HIPAA, and GDPR
- Expert Remediation: No
- Integration: Slack, Jira, Jenkins, GitLab, and more
- Price: $449/yr/user
Burp Suite Professional is one of the best penetration testing tools for web apps that offers a variety of features for manual and automated testing. It pinpoints vulnerabilities by intercepting and manipulating web traffic, automating repetitive tasks, fuzzing, and brute-forcing logins.
It detects common vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure direct object references (IDORs). Burp Suite also offers easy integration with external tools for a smooth user experience.
Pros:
- Offers a variety of extensions to enhance performance
- Automates routine testing processes
Limitations:
- Crashes and socket connection errors have been reported
- Does not highlight information leakage, such as personal and financial data
2. Cobalt Strike
Key Features:
- Platform: Networks and systems
- Pentest Capability: Automated adversary emulation and manual penetration testing.
- Accuracy: False positives possible
- Compliance: None
- Expert Remediation: No
- Integration: Outflank Security Tooling and Core Impact
- Price: Available on quote
As a well-known commercial platform for advanced adversary emulation and network penetration testing, Cobalt Strike by Fortra is the ideal match for an enterprise with a more hands-on approach. It allows you to tailor payloads, evasion techniques, and attack methodologies.
The tools offer a vibrant community and resource repository, offering tutorials, plugins, and knowledge-sharing resources for CXOs and CTOs.
Pros:
- Variety of built-in modules for crafting targeted attacks
- Features an exclusive and extensive exploit database
Limitations:
- Downloads can take hours, even for a few megabytes
- Can be expensive for SMEs
3. Rapid7
Key Features:
- Platform: Cloud and Web Applications
- Pentest Capability: Continuous automated scanning and manual pentests
- Accuracy: False positives possible
- Compliance: CIS, ISO 27001, and PCI DSS
- Expert Remediation: No
- Integration: ServiceNow Security Operations, LogRhythm NDR, and ManageEngine
- Price: Available on quote
Rapid7 offers a unified penetration testing platform that empowers enterprises to achieve sustainable security across the entire attack surface. It understands the challenges of managing complex security landscapes and offers end-to-end vulnerability management.
With vulnerability scanning, external penetration testing, security orchestration, and automation response (SOAR) in its portfolio, Rapid7 helps generate third-party pentest reports to facilitate compliance audits.
Pros:
- Provides in-depth visibility into vulnerabilities and threats
- User-friendly interface
Limitations:
- Relatively high priced for SMEs and startups
- Turnaround on technical support can be slow
4. Acunetix
Key Features:
- Platform: Windows, macOS
- Pentest Capability: Continuous automated scanning for web applications
- Accuracy: False positives possible
- Compliance: OWASP, SOC2, NIST, HIPAA, and ISO 27001
- Expert Remediation: No
- Integration: GitHub, Jira, and Atlassian
- Price: $1958/yr (Vulnerability Scanning only. Pentest pricing available on demand)
As a dedicated pentest scanner with advanced features, Acunetix automates the process as much as possible. It scans your applications for over 4,500 vulnerabilities, including common threats like SQL and XSS injections.
Acunetix offers simple workflow integrations and detailed reports with proof-of-concept examples to help improve the efficiency of remediation efforts for an enterprise.
Pros:
- Intelligent automated scanning tool
- Easy to navigate and learn
Limitations:
- Limitations in vulnerability detection as specific bugs need manual insight
- Can generate false positives
5. Nessus Professional
Key Features:
- Platform: Windows, macOS
- Pentest Capability: Automated vulnerability scans for web apps, mobile & cloud
- Accuracy: False positives possible
- Compliance: HIPAA, ISO, NIST, and PCI-DSS
- Expert Remediation: Available at extra cost
- Integration: IBM Security, Splunk, GitHub, and GitLab
- Price: Starting at $4,236/yr
Nessus is a comprehensive tool under the Tenable umbrella that can identify and assess vulnerabilities in a wide range of IT systems. Its extensive vulnerability coverage and automation capabilities genuinely set it apart.
The compliance support by the commercial pentest tool across various standards and industries like PCI DSS, HIPAA, and ISO helps maintain year-round compliance.
Pros:
- Easy to navigate and use UI
- Scanning and reporting tasks can be automated
Limitations:
- Scanning timelines can be inconsistent
- Custom asset tags require separate automation
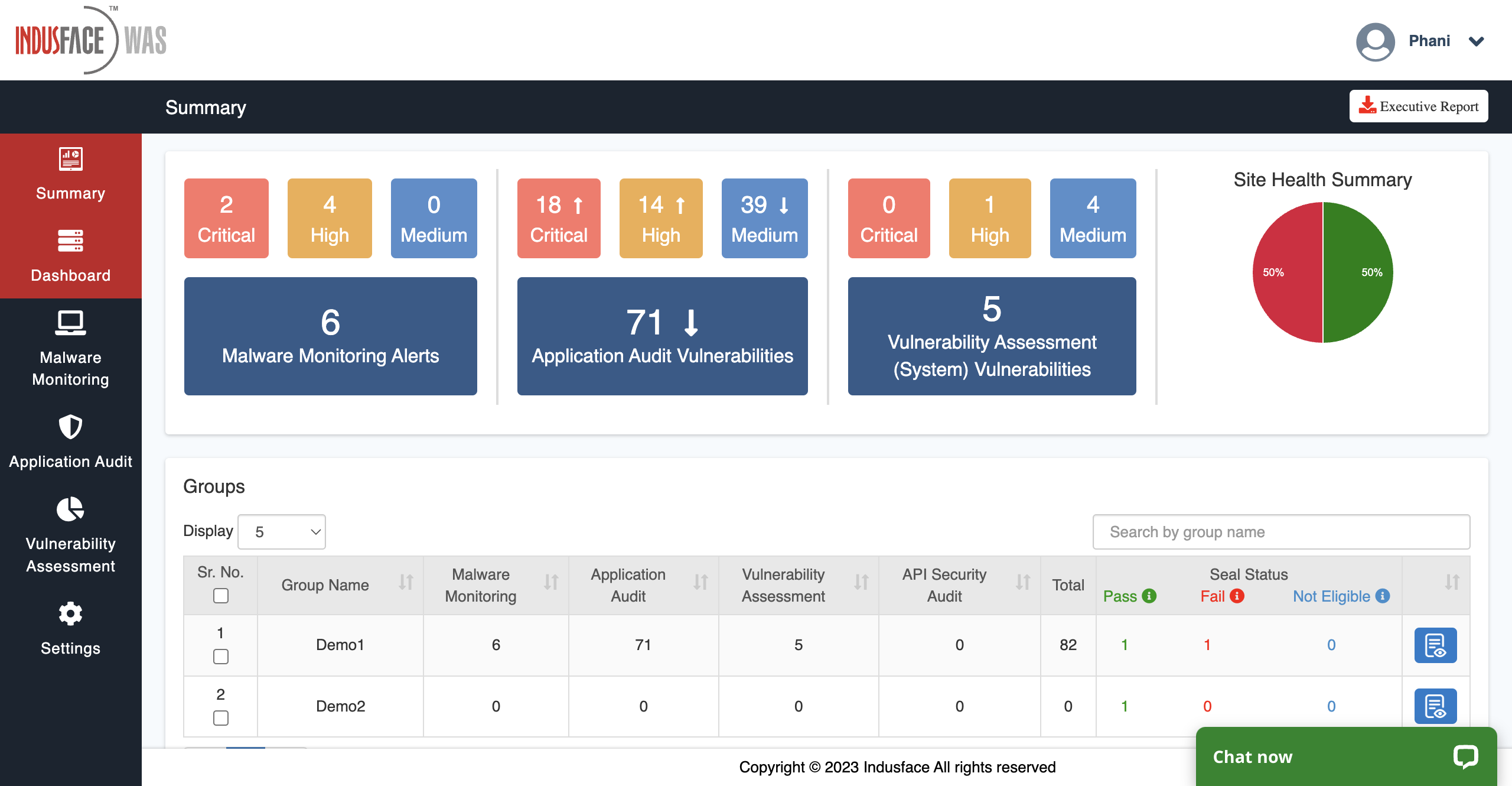
6. IndusfaceWAS
Key Features:
- Platform: Web applications
- Pentest Capability: Continuous automated vulnerability scans and manual pentests
- Accuracy: False positives possible
- Compliance: SOC2, ISO and OWASP
- Expert Remediation: Available at extra cost
- Integration: Jira, GitHub, Slack, and Microsoft Teams
- Price: Starting at $199/app/month
IndusFaceWAS is a managed dynamic application security testing (DAST) tool that provides enterprises real-time monitoring, automated assessment, and manual penetration testing solutions.
The platform generates detailed reports, including proof of concept documentation, and facilitates compliance testing across various industry standards.
Pros:
- Quick support and timely responsiveness
- OWASP top 10 and SANS 25 detection
Limitations:
- GUI is not very intuitive
- Frequent scan update emails can be overwhelming
Penetration Testing Platforms for Security Analysts:
| Features | Astra Pentest | Kali Linux | Nmap |
|---|---|---|---|
| Pentest Capabilities | Unlimited and continuous automated scans with manual tests | Unlimited Scans for vulnerability scanning, exploitation, privilege escalation, and post-exploitation | Unlimited scans for network discovery, vulnerability scanning, service identification, and OS fingerprinting |
| Target | Web apps, API, mobile, cloud, & networks | Online and physical systems, applications, &networks | Network infrastructure, IoT devices, limited cloud instances |
| Deployment | SaaS/Cloud | Installer packages for live boot and disk installation | Flexible deployment through the command line, scripting, and graphical interface (Zenmap) |
| Accuracy | Zero false positives | False positives possible | False positives possible |
| Pricing | Starting at $199/month | Open-source | Open-source |
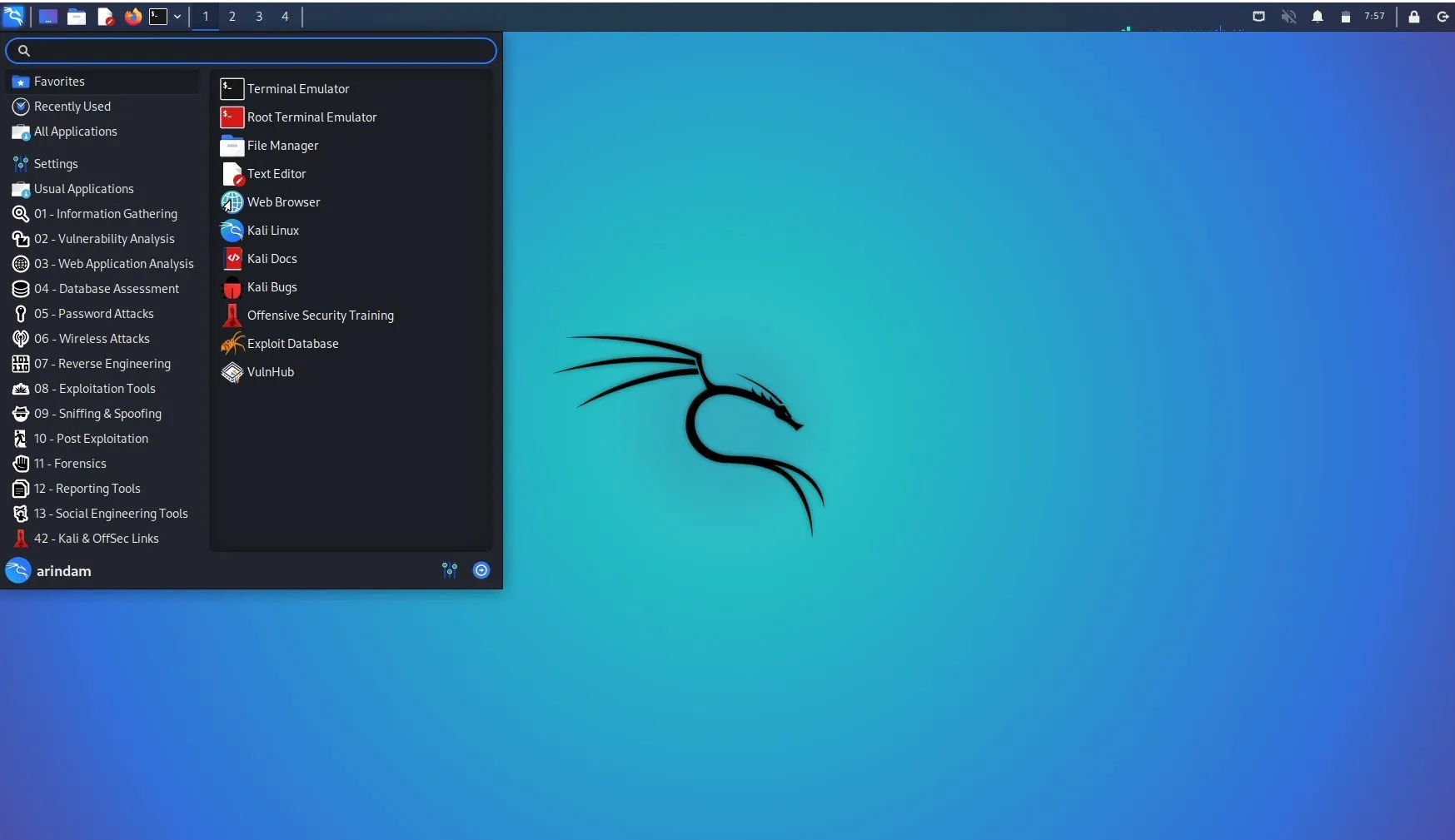
1. Kali Linux
Key Features:
- Target: Online and physical systems, applications, and networks
- Pentest Capabilities: Unlimited Scans for vulnerability scanning, exploitation, privilege escalation, and post-exploitation
- Deployment Capabilities: Installer packages for live boot and disk installation
- Accuracy: False positives are possible
- Price: Open-source OS
With 600+ pre-installed security tools, Kali Linux is a holistic software penetration testing OS that enables security to cover a wide breadth and depth of VAPT tasks ranging from initial assessment to post-exploitation analysis.
With extensive customization options, the OS provides extensive documentation, tutorials, and support to aid learning and troubleshooting.
Pros:
- Comprehensive community support
- Regular updates and patches
- High-speed execution of tasks
Limitations:
- Need to be fluent in Linux commands
- Learning curve is steep for beginners
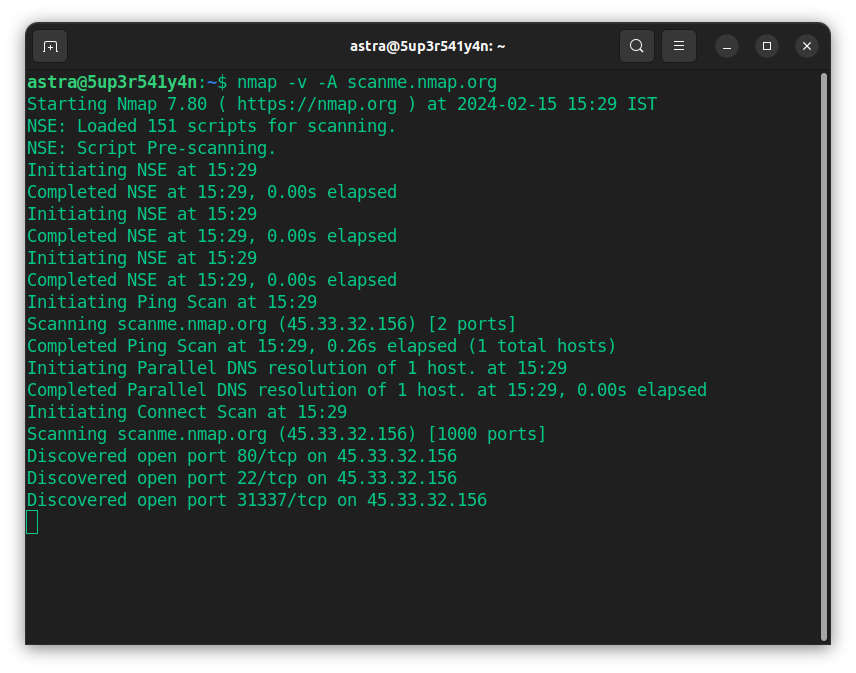
2. Nmap
Key Features:
- Target: Network infrastructure, IoT devices, limited cloud instances
- Pentest Capabilities: Unlimited scans for network discovery, vulnerability scanning, service identification, and OS fingerprinting
- Deployment Capabilities: Flexible deployment through the command line, scripting, and graphical interfaces
- Accuracy: False positives are possible
- Price: Open-source tool
Nmap is an open-source command line and network scanning tool that analyzes your network’s structure to find possible entry points and reveal running services on target systems. The operating system detection feature adds another layer of intelligence to its arsenal.
Nmap’s version detection capabilities and scriptable interaction through the NSE help security professionals automate tasks, improve scan capabilities, and create custom scripts for specific situations.
Pros:
- Active Community to build and grow the tool
- Versatile pentesting tool suitable for a wide range of applications
- Powerful scripting capabilities for automation
Limitations:
- A learning curve for beginners
- Aggressive scanning techniques can be very intrusive at times
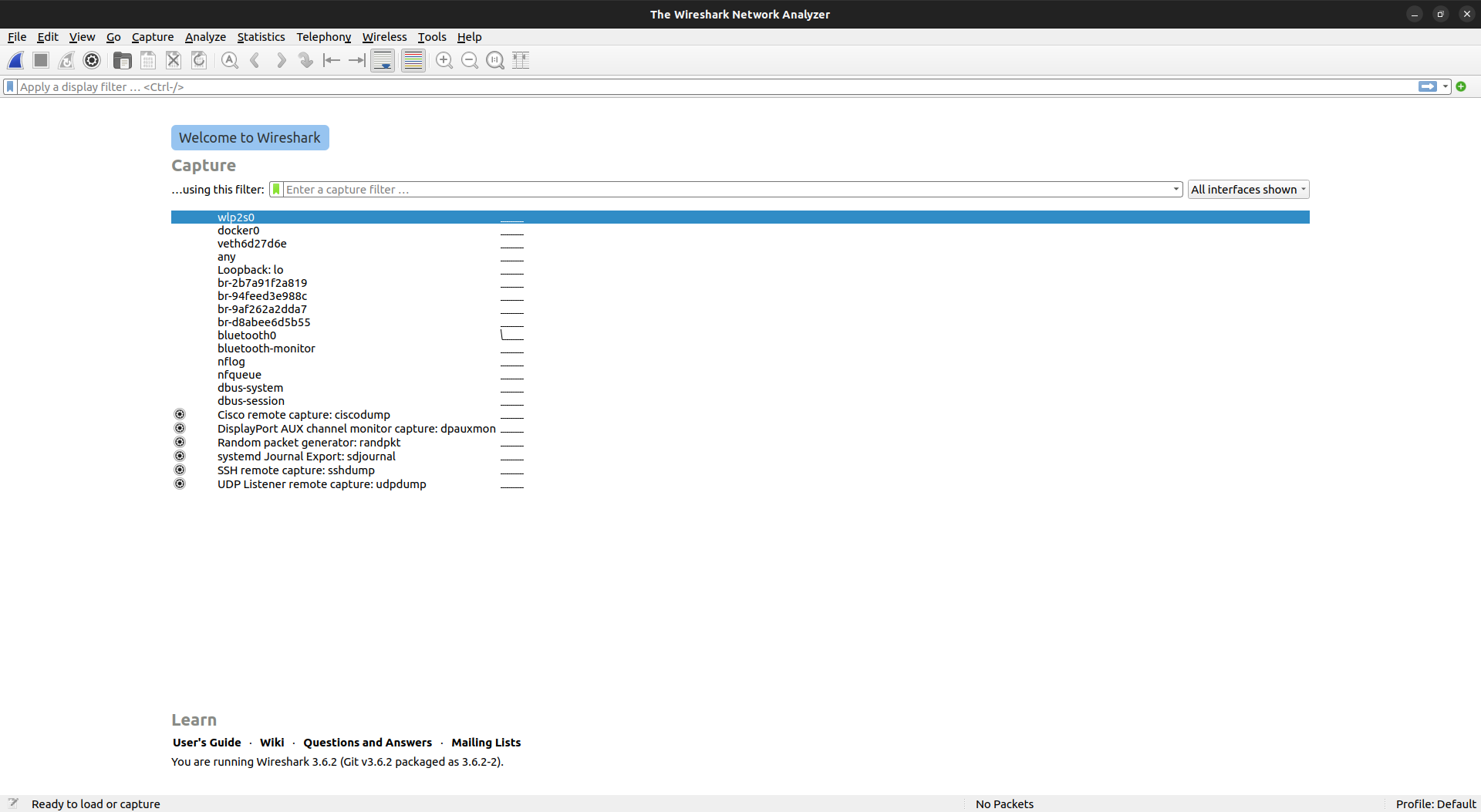
3. Wireshark
Key Features:
- Target: Network
- Pentest Capabilities: Vulnerability detection, deep packet inspection, and traffic analysis
- Deployment Capabilities: Installer packages for traditional and portable versions
- Accuracy: False positives are possible
- Price: Open-source tool
As a prominent network packet analyzer, Wireshark is a versatile internal penetration testing tool that empowers security analysts to identify vulnerabilities in protocols, configurations, and applications.
It can analyze real-time and historical network traffic to reconstruct attack timelines, identify attack vectors, and understand attacker behavior.
Pros:
- Powerful tool for troubleshooting network issues and security threats
- In-built filters facilitate analysis
Limitations:
- Performance issues with large packets of data
- Difficult for beginners to navigate
4. Nikto
Key Features:
- Target: Web applications and servers
- Pentest Capabilities: Vulnerability and misconfiguration identification
- Deployment Capabilities: Manual installation from source code
- Accuracy: False positives are possible
- Price: Open-source tool
As one of the best open-source penetration testing tools designed specifically for web apps and servers, Nikto has access to a wide variety of bug databases. It scans for 6700+ vulnerabilities, including outdated software, misconfigurations, and common exploits.
It helps security analysts identify open directories, insecure file permissions, and weak HTTP headers. Nikto also offers customization plugin support.
Pros:
- Scans for over 6700+ vulnerabilities
- Fosters a learning environment
Limitations:
- May generate false positives that require manual vetting
- Does not provide an in-depth analysis of vulnerability exploit and impact
5. W3af
Key Features:
- Target: Web applications
- Pentest Capabilities: Vulnerability scanning, threat exploitation, and attack simulation
- Deployment Capabilities: Manual installation from source code and pre-built packages
- Accuracy: False positives are possible
- Price: Open-source tool
Web Application Attack and Audit Framework, better known as W3af, is a web application pentest scanning tool that offers manual pentesting capabilities. Unlike most open-source tools, it goes beyond identification to assess their impact and severity.
W3af also helps security analysts automate repetitive tasks like scanning and reporting to save time and effort, especially in the case of comprehensive security audits.
Pros:
- Integrates well with DevSecOps practices
- Supports multiple operating systems and manual exploit customizations
Limitations:
- False positives are possible
- GUI can be complex to navigate
6. Aircrack-ng
Key Features:
- Target: Wireless networks
- Pentest Capabilities: Password cracking, vulnerability assessment, traffic analysis, and wireless card testing
- Deployment Capabilities: Can be installed from sources and specific pre-combined binaries
- Accuracy: False positives are possible
- Price: Open-source tool
As a pentest tool that exclusively focuses on wireless networks, Aircrack-ng helps automate various tasks for vulnerability assessment and pentesting the above. It gives security analysts a more holistic understanding of the network’s security posture.
Moreover, Aircrack-ng’s command-line interface facilitates customization, including attacks such as replay attacks, de-authentication, and fake access points.
Pros:
- Tackles multiple stages of wireless network pentesting
- Offers granular control through command-line options
Limitations:
- Wireless compatibility can be an issue; isn’t effective in all cases
7. BeEF
Key Features:
- Target: Web browsers
- Pentest Capabilities: Social engineering for in-depth vulnerability assessments
- Deployment Capabilities: Can be installed from sources, pre-built packages, and via Docker
- Accuracy: False positives are possible
- Price: Open-source tool
As the name suggests, the Browser Exploitation Framework, or BeEF, is an open-source pentest tool designed to evaluate the security of web browsers. It helps analysts simulate malicious attacks to identify vulnerabilities and assess the security posture.
Once the security analyst has gained control of a browser, BeEF helps analyze post-exploitation impacts such as redirecting traffic, keystroke logging, and theft of sensitive data.
Pros:
- Easy to install and configure
- Hassle-free tool for beginners
Limitations:
- User interface is comparatively tricky to navigate
- Database configuration can be a little difficult
8. Ettercap
Key Features:
- Target: Network infrastructure and web applications
- Pentest Capabilities: Passive network sniffing, active attacks, and network analysis
- Deployment Capabilities: Manual installation from source code and pre-built packages
- Accuracy: False positives are possible
- Price: Open-source tool
Ettercap is an open-source penetration testing tool that allows security analysts to analyze network traffic and simulate session hijacks, Man-in-the-Middle(MitM), and DOS attacks.
The tool also supports scripting languages and plugins to allow analysts to automate repetitive tasks and customize functionalities to their specific needs.
Pros:
- Offers extensive scripting support
- Community-developed plugins help enhance functionality
Limitations:
- Cannot run on Windows 10
- The interface is a little dated
9. Vega
Key Features:
- Target: Web applications
- Pentest Capabilities: Website crawling and automated scanning
- Deployment Capabilities: Manual installation from source code and pre-built packages with JRE
- Accuracy: False positives are possible
- Price: Open-source tool
As an open-source web security scanner and penetration testing platform, Vega allows analysts to intercept and analyze web traffic, crawl web applications, and pinpoint vulnerabilities, including SSL/TLS misconfigurations.
The tool also facilitates JavaScript extensions to help tailor the pentest to a professional’s specific needs and gain a better understanding of complex application behavior.
Pros:
- Offers extensive scripting support
- Community-developed plugins help enhance functionality
Limitations:
- Cannot run on Windows 10
- The interface is a little dated
10. Zed Attack Proxy
Key Features:
- Target: Web applications
- Pentest Capabilities: Automated and manual pentests, including
- Deployment Capabilities: Manual installation from source code pre-built packages and Docker
- Accuracy: False positives are possible
- Price: Open-source tool
Zed Attack Proxy, or ZAP, is a web application security testing (WAST) tool primarily used for penetration testing. It acts as a MitM proxy, allowing security analysts to intercept, analyze, and modify web traffic between a browser and a web application.
In addition to pre-built scanners and manual pentest tools, it allows security analysts to manipulate sessions, fuzz, and launch brute-force attacks.
Pros:
- User-friendly interface, especially for beginners
- Community-developed plugins help enhance functionality
Limitations:
- Can generate false positives necessitating manual vetting
Final Thoughts
The above list highlights some of the best penetration testing tools addressing the diverse needs of both enterprises and security analysts.
Astra & Rapid7 offer end-to-end pentesting, reporting, and workflow integration for enterprises seeking comprehensive suites.
Security analysts seeking deep, flexible, and user-friendly penetration testing tools for specific assets can leverage Kali Linux, ZAP, and Burp Suite. The importance of specialized tools like Wireshark, Aircrack-ng, and BeEF, of course, cannot be ignored.
With that said, platforms like Astra Pentest combine these benefits, offering a comprehensive PtaaS pentest tool solution ideal for both parties.
Ultimately, the quality of your penetration testing tool plays a crucial role in determining your cybersecurity culture’s growth rate and stability.
FAQs
What is Penetration Testing?
Penetration testing is a security exercise where security experts search your systems for vulnerabilities using the processes a hacker would. And then attempt to exploit some of those vulnerabilities in order to find out their severity, and the risk they pose to the organization.
How are penetration testing and vulnerability assessments different?
Vulnerability assessments passively scan for known weaknesses, while penetration tests actively exploit vulnerabilities like an attacker. Pen tests offer in-depth analysis of exploitability and impact, while VA scans provide broad visibility with prioritization.
This post is part of a series on penetration testing, you can also check out other articles below.
Chapter 1. What is Penetration Testing
Chapter 2. Different Types of Penetration Testing?
Chapter 3. Top 5 Penetration Testing Methodology to Follow in 2024
Chapter 4. Ten Best Penetration Testing Companies and Providers
Chapter 5. Best Penetration Testing Tools Pros Use – Top List
Chapter 6. A Super Easy Guide on Penetration Testing Compliance
Chapter 7. Average Penetration Testing Cost in 2024
Chapter 8. Penetration Testing Services – Top Rated
Chapter 9. Penetration Testing Report

















I think this is a excelent article, what is the source?