The term ransomware word perfectly captures the idea behind it, i.e. holding a computer system or software captive until a ransom is paid. Traditionally, attackers use ransomware to target individuals but things are different now.
Ransomware demands saw a 144% increase in 2021, with the ransomware payouts averaging more than $6 million for victims in the U.S. Businesses, government bodies, individuals, and virtually anyone with a vulnerable system can take a ransomware hit.
In this post, we’ll walk you through some of the most ambitious and biggest ransomware attacks over three decades. We’ll discuss their origins, targets, and impact. In the end, we’ll share with you some practices you can implement to stay safe from ransomware attacks.
10 of the Biggest Ransomware Attacks
- WannaCry (Net loss: $4 billion)
- TeslaCrypt ( Net loss: Unknown)
- NotPetya (Net loss: $10 billion)
- Sodinokibi (Net loss: $200 million)
- SamSam (Net loss: $6 million up till 2018)
- COLONIAL PIPELINE RANSOMWARE ATTACK (Net loss: $4.4 million)
- Kronos (Net loss: Unknown)
- Impressa (Net loss: 50 Terabytes of data)
- Costa Rica Government (Net loss: $30 million/day)
- Swissport (Net loss: Unknown)
As you can tell from the list above, this is not a post about the ransomware that bagged the most amount of money. We’ve picked attacks across industries, based on the impact that transcends just monetary loss. This is to show you how both the individual and the collective have suffered from ransomware attacks and how variegated the attack approaches can be.
More about the Biggest Ransomware Attacks
In this section, we’ll look deeper into the attacks that we’ve listed earlier. Let’s dive in.
1. WannaCry
- Type: Crypto Ransomware
- Year of release: 2017
- Perpetrators: Shadow Brokers
- Entities affected: Microsoft Windows users
- Approximate losses: $4 billion
- Current status: Still active, but the decryption key is available
WannaCry spread like a digital epidemic in May 2017 and held hostage the files of 250,000 users of Microsoft Windows users across 150 countries. A hacker group called Shadow Brokers used a hack allegedly developed by the US National Security Agency called the EternalBlue to exploit a vulnerability in Microsoft Windows PCs.

The hackers encrypted files on the computer and demanded a ransom worth $300 – $600 to be paid in the cryptocurrency, Bitcoin. British Security researcher Marcus Hutchins halted WannaCry by registering the web domain in the malware’s code.
2. TeslaCrypt
- Type: Trojan Horse – Crypto Ransomware
- Year of release: 2015
- Perpetrators: Unknown
- Entities affected: Individuals using Windows XP, Vista, 7, and 8
- Approximate losses: $500/individual
- Current status: Inactive since 2016
TeslaCrypt was a Trojan Horse Cryptovirus that targeted 185 game files of 40 popular games like the Call of Duty series, World of Warcraft, Minecraft, World of Tanks, etc. The ransomware targets save data, player profiles, custom maps, and game modifications stored on the target’s hard drive. The later versions of TeslaCrypt also encrypted Word, PDF, JPEG, and other file types. It prompted the victims to pay a $500 ransom to get the decryption key.
The TeslaCrypt ransomware got better and better over 4 versions and the last version could encrypt files up to 4GB in size. The authors of the ransomware shut it down in May 2016.
3. NotPetya
- Type: Locker ransomware
- Year of release: 2017
- Perpetrators: Sandworm
- Entities affected: Businesses and Public Offices in Ukraine, Germany, and France
- Approximate losses: $10 billion
- Current status: Decryption available
Petya was a ransomware virus that surfaced in March 2016. It infected the master boot record of Windows computers to take the system hostage. NotPetya was a variant of the Petya released in June 2017. It was different from the Petya in two accounts. One, it used the EternalBlue hack to infect systems, and two, it was modified in a way that its effect could not be reverted.
It was named NotPetya and the allegation was that this attack was politically motivated and targeted against Ukraine by the Russian Military Agency. 80% of the affected companies were Ukrainian. In fact, the radiation monitoring system at Ukraine’s Chornobyl Nuclear Power Plant was shut down temporarily.
It was found that a backdoor created during an update of the Ukrainian company M.E. Doc was used to spread this malware. NotPetya is the most impactful ransomware attack to date having brought about financial losses worth $10 billion.
4. Sodinokibi
- Type: Crypto ransomware
- Year of release: 2019
- Perpetrators: REvil
- Entities affected: JBS and Kaseya were the main victim organizations
- Approximate losses: $200 million
- Current status: Decryption available
Sodinokibi is the name of a range of organized ransomware attacks that primarily victimized the transportation industry and the financial sectors. The malware encrypts files that have the following extensions .jpg, .jpeg, .raw, .tif, .png, .bmp, .3dm, .max, .accdb, .db, .mdb, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .aaf, .aep, .aepx, .plb, .prel, .aet, .ppj, .gif, and .psd. It encrypts files on a system and shows a ransom note on the screen.
The ransomware had a whitelist exempting countries that maintain a tight relationship with Russia. It probably used keyboard layouts to identify the exempted systems. For instance, it would not infect systems that use Ukrainian, Romanian, Georgian, Turkmen, Syriac, and Arabic. In 2021 Sodinokibi focused on US companies.
Its attacks on JBS and Kaseya have triggered the cybersecurity crackdown and the ransomware is most likely inactive.
5. SamSam
- Type: Locker
- Year of release: 2018
- Perpetrators: SamSam
- Entities affected: US industries using Windows servers
- Approximate losses: $6 million
- Current status: Active
The attackers behind the SamSam ransomware attack exploited vulnerabilities in Windows servers to establish persistent access to network assets. They infect the entire network and encrypt all hosts connected to it instead of attacking individual systems. The primary focus of the attacks has been on US companies. The FBI, NCCIC, and CISA put out a joint declaration about this ransomware in 2018.
6. Colonial Pipeline Attack
- Type: Locker
- Year of release: 2021
- Perpetrators: DarkSide
- Entities affected: Colonial Pipeline
- Approximate losses: $4.4 million
- Current status: Mitigated by paying the ransom
The Colonial Pipeline Company is responsible for carrying gasoline and Jetfuel to SouthEastern USA. It carries gasoline from Texas to as far as New York.
On May 7, 2021, a ransomware attack forced the company to shut down operations and on 9th May an emergency was declared in 17 states. A ransom amount of 75 Bitcoin which was worth $4.4 million at that point was paid to DarkSide under the supervision of the FBI. There was no other way to decrypt the infected files. Around $2.3 million from the ransom amount was recovered later by the Department of Justice.
7. Attack on Kronos
- Type: Crypto
- Year of release: 2021
- Perpetrators: Unknown
- Entities affected: Ultimate Kronos Group
- Approximate losses: Unknown
- Current status: Unknown
Kronos is a very popular workforce management solution that has more than 40 million users across 100 countries. Companies like Tesla, and PepsiCo use the Kronos platform to track employee data – attendance, payments, overtime, and whatnot.
In 2021, Kronos was victimized by a ransomware attack that infected the Kronos Private Cloud. The attack affected only the clients who used the Kronos Private Cloud to host their data. A lot of companies lost crucial employment data. Even though UKG has paid the ransom, they are yet to recover from the situation and are currently riddled by lawsuits that their clients and employees have filed.
8. Attack on Impressa
- Type: Locker
- Year of release: 2022
- Perpetrators: Lapsus$
- Entities affected: Portuguese Media Company Impressa, it’s TVstation SIC and Expresso newspaper
- Approximate losses: Unknown
- Current status: Mitigated
Impressa is a Portuguese media conglomerate with the nation’s largest TV station SIC TV, and a newspaper called Expresso. The company was attacked by a hacker organization by the name of Lapsus$. The attackers took over server infrastructure critical to Impressa’s operations on the new year’s weekend. The TV station and the newspaper remained closed on the Tuesday following the first weekend of 2022.
Even though Impressa regained control of their systems quite quickly after the attack, the hackers still retained access to their official social media accounts and pressurized to pay. Further details about the incident are blurry.
9. Attack on the Costa Rican Government
- Type: Locker
- Year of release: 2022
- Perpetrators: Conti Group
- Entities affected: 30 Costarican Government Offices
- Approximate losses: $30 million per day of the attack
- Current status: Active
The ransomware attack on the Costa Rican government has been identified as an act of war by the pro-Russiaan Conti group. The attack was mounted against 30 Costarican public offices including the Ministry of Finance, the Ministry of Science, Innovation, Technology, and Telecommunication, and the state internet provider RACSA.
The losses incurred by the hack amounted to $30 million every day the government had to close operations due to the hack. The nation is still dealing with the hack situation.
10. Attack on Swissport
- Type: Crypto
- Year of release: 2022
- Perpetrators: BlackCat
- Entities affected: Swissport
- Approximate losses: Unknown
- Current status: Ransomware removed. 1.6 TB data stolen.
“The €3 billion revenue firm, Swissport, has a presence across 310 airports in 50 countries and provides cargo handling, maintenance, cleaning, and lounge hospitality services.” The ransomware attack on Swissport did not cause a lot of immediate damage other than a few flight delays. However, the perpetrator, BlackCat has disclosed a sample of personally identified data that they had stolen during the attack. The attackers claim to have 1.6TB of sensitive data and they are ready to sell it to the highest bidder.
The Very First Ransomware Attack
The history of ransomware goes back three and half decades to the late eighties. The first ever ransomware that was recorded was the AIDS Trojan (PC Cyborg). The ransomware virus was released via floppy disc. It prompted the users to send $189 to a certain post-box to regain access to their systems.
Since then, ransomware technology has evolved continuously to the present day where asymmetric cryptography and intelligent payloads make it more and more difficult to untangle them.
Ransomware Attacks in 2022
On the 15th of February, 2023, the City of Oakland, California declared a local state of emergency as it had to shut its IT systems owing to a ransomware attack.
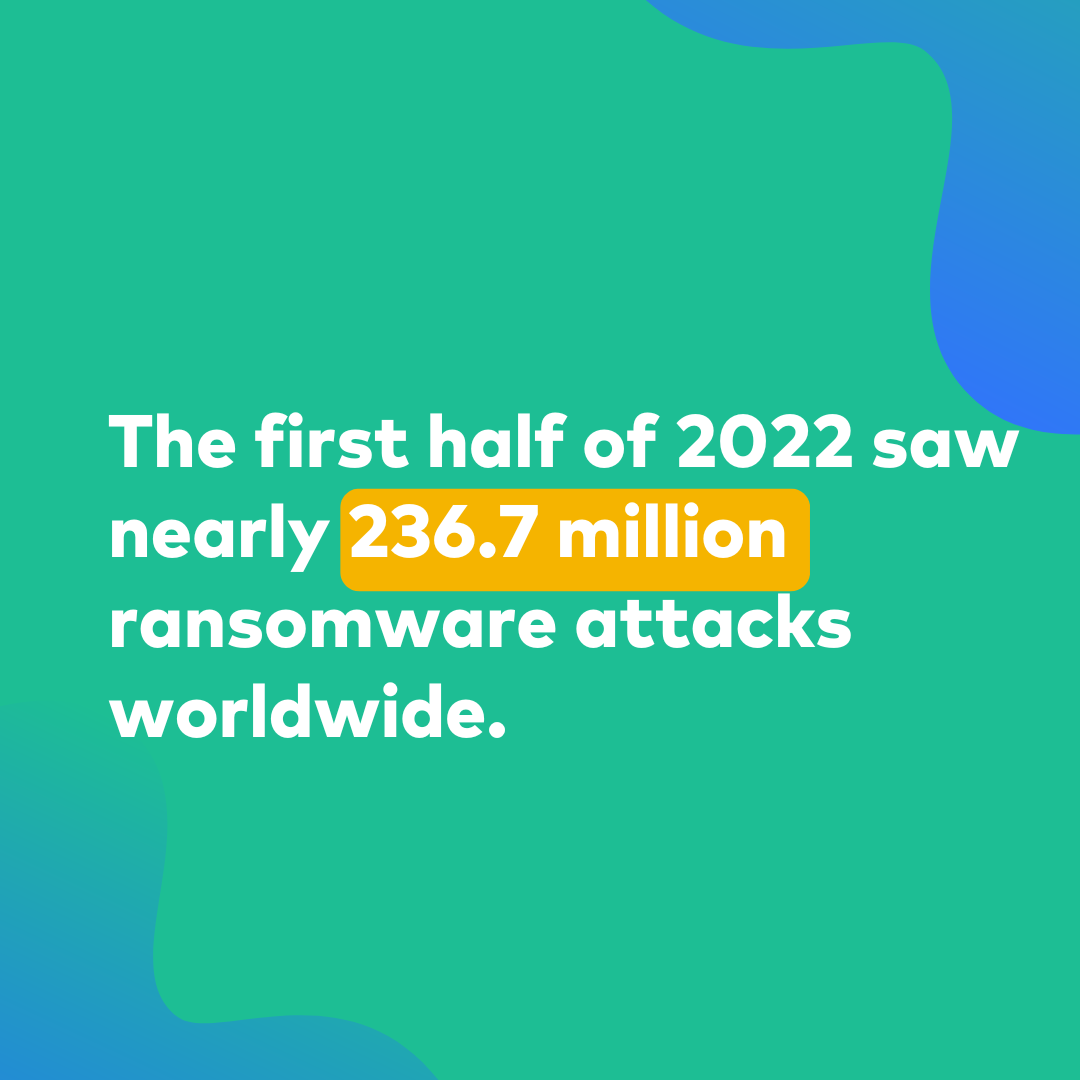
2021 and 2022 were some of history’s most active years in terms of ransomware attacks. The first half of 2022 saw nearly 236.7 million ransomware attacks worldwide. We have already talked about the attacks on Impressa, the Costarican government, and Swissport. A lot more happened in 2022.
Attacks were mounted on companies like Toyota, NVidia, and Optus, as well as the Bernalillo County of New Mexico. Overall 2022 was a frightening year for businesses to say the least.
Ransomware Types
Ransomware can be classified into two different types – crypto-ransomware and locker ransomware. In the former attackers get access to your files, encrypt them, and withhold the key. They give you the key to decrypt your files after you’ve paid the ransom demanded by them. The locker ransomware is used to lock you out of your computer.
What can You Do to Avoid Ransomware Attacks?
Here are some quick tips that will help you avoid ransomware attacks and alleviate the impact in the event of an attack.
- Back up your data. In case of a ransomware attack, you can ideally wipe your infected computer clean and restore the backed-up data.
- Do not run outdated systems or applications. Nothing hurts more than getting hacked by missing an update.
- Having a solid website protection system is a must – it should include a firewall, an antivirus, and a malware detection and cleanup mechanism.
- Be attentive while opening emails or clicking on attachments.
- Whitelist the applications that can be installed on your network to avoid infection by human error.
- Practice the least privilege approach when it comes to access to data and system assets.
- Prioritize endpoint security.
- Integrate regular security testing with your business functionality.
Conclusion
A large chunk of ransomware attacks are mounted by exploiting outdated software, erring employees, and inattentive managers. It is important to make security a habit if you are to survive the era of hyper-digitization and deep fakes. Social engineering is at its absolute peak at this point. Your organization’s security consciousness could be tested at any point. So it’s better to be prepared.
FAQs
1. Are ransomware and malware the same?
Malware is a specific type of software that is designed with malicious intent. Ransomware is a type of malware that is designed to encrypt data and take systems, hostage. So, every ransomware is malware, but not every malware is ransomware.
2. Is it possible to remove ransomware without paying?
If a decryption tool for the type of ransomware your systems are infected with is available, you can use it to decrypt the files and regain access. You will need a tool to remove the malware from the system.
If the decryption tool is unavailable, paying up might be your only way to regain access. If you have your data backed up, you can wipe your computer clean and restore the backed-up data.
3. What is responsible for the most successful ransomware attacks?
Phishing, exploitation of Remote Desk Protocol (RDP), and other software vulnerabilities.
















