Abandoned Cart Plugin in WooCommerce Abused – Update Immediately
WordPress-based sites are under attack from hackers exploiting an XSS vulnerability in the woocommerce-abandoned-cart plugin to plant backdoors and take over vulnerable sites.
The woocommerce-abandoned-cart plugin, allows the owners of WooCommerce sites to track abandoned shopping carts in order to recover those sales.
A lack of sanitation on guest user input and output allows attackers to inject malicious JavaScript into many data fields, which will execute when a logged-in user with administrator privileges views the list of abandoned carts.
Currently, WordPress sites using woocommerce-abandoned-cart or woocommerce-abandoned-cart-pro, are advised to update to the latest available version immediately. WordPress sites using Astra WAF, are protected from this attack due to the firewall’s built-in XSS protection.
Affected users without Astra installed are advised to consider a Site Security Audit to confirm the integrity of their WordPress sites.
Details of XSS Vulnerability in Abandoned Cart Plugin WordPress
When an unauthenticated user adds products to their shopping cart and heads to checkout, woocommerce-abandoned-cart‘s guest input comes into play.
The save_dataAJAX action sends the data entered by the guest back to the plugin. The intent is if the checkout process is not completed due to any reason, the shop’s owners will be alerted within their dashboard by the plugin.
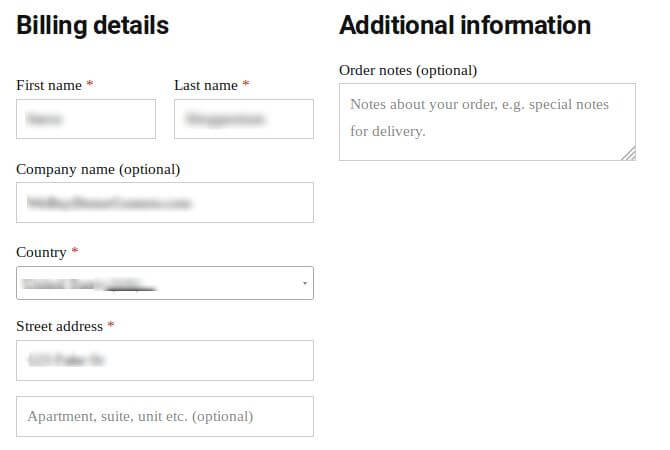
Input sanitization of these AJAX requests ($_POST fields) is not performed by the function which handles them. billing_first_name, billing_last_nameand billing_company are some of the shopper data fields which are directly stored as received from the user. Data from this request is then stored in the database and is accessible to an administrator from their WordPress dashboard. Customer information, individual carts, order totals, and such information are visible to the administrator from the dashboard.
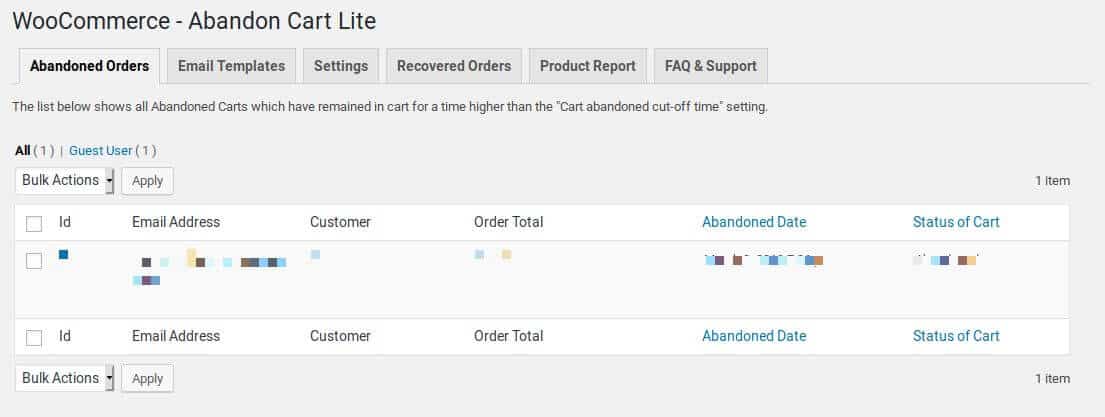
There is no output sanitization performed during the rendering of this data in the administrator’s browser. As the “Customer” field is a single field resulted from the stringing together of the billing_first_name and billing_last_name fields in the output table, it is the target for hackers exploiting this flow.
WordPress Admin panel Compromised because of Abandoned Cart Plugin? Drop us a message on the chat widget and we’d be happy to help you fix it. Fix my WordPress website now.
How Hackers are exploiting this Vulnerability in Abandoned Cart Plugin
Hackers are attacking stores that are based on WordPress WooCommerce in order to create shopping carts crowded with products having malformed names.
Leaving the site after inserting exploit code in any of the cart’s fields results in the store’s database storing the inserted exploit code.
This exploit code inserted by the hacker gets executed as soon as the respective backend page is loaded when accessed by an administrator to view the abandoned cart list.
In the attacks spotted by Wordfence, a bit.ly link was used to load a JavaScript file by the exploit code. On the sites on which the vulnerable plugin was active, the code tried to create two distinct backdoors.
While the first backdoor is a new administrator account created by the hackers, with the username “woouser” and an email address hosted at Mailinator, the second backdoor in a rather clever technique. It lists all the plugins installed on the website and searches for the first disabled plugin. Instead of re-enabling the plugin, the contents of its main file gets replaced with a script which will provide the Hackers with further access in the future.
Malicious commands can be sent to this backdoor by the attackers, even if the “woouser” account is removed, as long as the deactivated plugin’s files remain on the disk and are accessible by web requests.
Impact:
The impact of this flaw ranges from using the sites for SEO Spams to the hackers planting card skimmers.
Fixing Abandoned Cart Plugin Exploit
Version 5.2.0 of the Abandoned Cart Lite for WooCommerce which was released on February 18, 2019, saw a fix that dealt with the XSS attack vector used by hackers in this exploit.
It is highly recommended that all the store owners using this WordPress plugin on their sites must check for any suspicious entries in the list of admin accounts on their control panel, as well as keep their sites updated. It is entirely possible that the hackers could have changed the name from “woouser” to something else.
It is to be noted that this patch is not the complete solution to this flaw as it does not deal with the second backdoor or with pre-existing scripts that were injected. Hence, the recommendation for owners of stores using either woocommerce-abandoned-cart or woocommerce-abandoned-cart-prois to check for any script injections in their database. While the name of the table to review may be different, table namedac_guest_abandoned_cart_historyis where the guest shopper data can be located. Additionally, all unauthorized admin accounts must be removed as part of the cleanup.
WordPress Admin panel Compromised because of Abandoned Cart Plugin? Drop us a message on the chat widget and we’d be happy to help you fix it. Fix my WordPress website now.
















