Article Summary
The website analytics plugin for WordPress Slimstat, has been found vulnerable to stored XSS (cross-site scripting) vulnerability in versions <=4.8. At moment of writing this blog, it is installed on 1,00,000+ websites. Slimstat is a known plugin for tracking website analytics in real time, it monitors and reports stats of access logs, returning customers and registered users, JavaScript events, etc.
The website analytics plugin for WordPress Slimstat has been found vulnerable to stored XSS (cross-site scripting) vulnerability in versions <=4.8. At the moment of writing this blog, it is installed on 1,00,000+ websites. Slimstat is a known plugin for tracking website analytics in real time, it monitors and reports stats of access logs, returning customers and registered users, JavaScript events, etc. Termed a popular plugin in WordPress of this niche, so the XSS vulnerability in Slimstat was sure to create eddies in the water.
Current Status of the Risk in Slimstat WordPress Plugin
About the vulnerability, it allows an unauthenticated user to insert JavaScript in access logs of version <= 4.8. The plugin developers, however, were quick to fix the issue and the updated version 4.8.1 made to the plugin directory soon afterward. Yet if you have not updated to the patched version the risk lingers for you.
Below are the technical details of the XSS found in Slimstat,
Slimstat WordPress Plugin Vulnerability Details
Due to this vulnerability, any unauthenticated visitor can inject arbitrary JavaScript code on the plugin access log functionality, for which Slimstat is mostly used. Further, this access log is accessible from the plugin access log page as well as the admin dashboard.
An access log allows a user to have details of access requests on his website, it generally includes specifics like IP address, server details, hosting details, etc.
In Slimstat, any malicious user could inject arbitrary code on the plugin access log. This will get executed once an admin logs in.
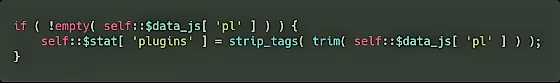
Most importantly, this plugin has only one sanitization method, i.e. strip_tags, which only removes tags from an inserted plugin value. This sanitization criterion can easily be fooled by using a single quote and then adding an event handler.
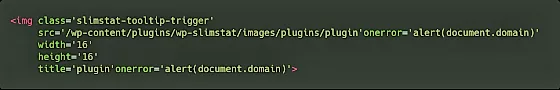
Here is how the image is generated for the plugins, where $a_plugin is the plugin:
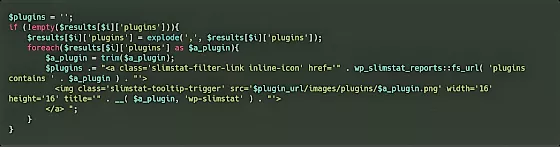
As a result of which, there occurs an error (shown in the picture) as plugin’onerror’. Since the request could not be executed, it gets stored in as a potential XSS vulnerability.
Update to Mitigate the Risk of Slimstat Exploit
In cases of vulnerable plugin situations, you can hardly do anything other than updating the version and having all preventive security measures handy. Other than updating, having a continuous and comprehensive Web Firewall that blocks XSS, SQLi, CSRF, and other common cyber attacks. Astra offers one such firewall, that will monitor, block and report any attempted attacks on your website. Click here to get an Astra demo now.
















