Often stated as one of the most overlooked of all web vulnerabilities, clickjacking aka UI redress attack refers to a type of attack that tricks users into unwarily clicking on nefarious links set up by the attacker. On clicking these links, the attacker is able to gather confidential information, compromise the user’s privacy, or make a user perform actions online that they normally wouldn’t do.
Why this form of attack is even more difficult to prevent is because this kind of attack employs a widely used functionality that is implemented by web nowadays – frames. While frames are widely used for login pages, Javascript interactions, content management in CMSes, it has been carefully exploited to perform UI redress attack as well.
Example of Clickjacking in Action
Suppose an online video library is vulnerable to clickjacking attacks. It may be compromised by clickjacking in the following fashion.
An attacker has a website which advertises of giving free movies or videos for it. The website has a ‘Grab your free copy here’ button on the page, but behind this button an invisible delete button from an actual video library web application is lined up. As soon as the victim presses the button, all the movies in their account will be deleted.
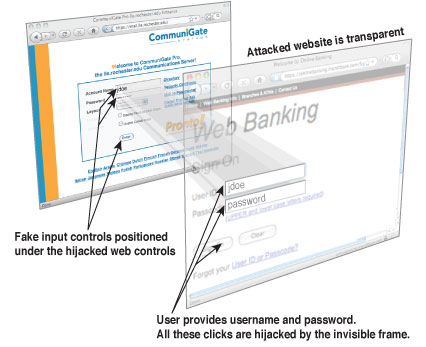
Furthermore, there are various attacks possible with clickjacking such as download of malwares in the system, actions such as unintended buys. In case an application supports a money transfer feature, transfers can be made without knowledge of the victim. In this manner, a logged in user is administrator of the application, all sorts of administrative actions can be executed without the knowledge of the user.
Clickjacking Protection Tips
Here are some protection tips one can take to prevent businesses and websites from becoming victims of clickjacking scams.
-
Including X-Frame options
Running web pages inclusive of HTTP header with X-Frame-options will prevent your site from being placed within a frame. X-Frame is supported by widely used browsers like Chrome, Internet Explorer and Apple Safari.
-
Protect the browser
Start by protecting your browser first. One way to reduce clickjacking risk during normal web activities is to install browser plugins like NoScript and NotScript. These prompt users to allow javascript actions on sites they visit, as well as specify domains which can be trusted. Also known as frame-busting, Javascript detects if your site has been placed in a frame and reload it in main browser window. For example, the javascript snippet may look like this:
try{if(top.location.hostname != self.location.hostname)throw1;}catch(e) {top.location.href = self.location.href;}3. Move elements on your pages
Moving elements on your web page from time to time can be a good idea to save yourself from being a clickjacking scam victim. Usually an attacker is unaware of current locations of elements from user’s side, and ends up placing infected elements on the basis of default settings. Eg: If there is a facebook like button on your webpage, moving its elements to another location can enable you detect if a clickjacking attempt was made
4. Invest in web application firewalls
Data reveals that almost 70 percent of SMBs get hacked each year due to absence of a web application firewall. The importance of splurging on a Web Application Firewalls (WAFs) is often underestimated by small and medium businesses, largely due to expense and their management. But having a firewall is well worth the time and money, mostly because it can prevent an attacker from interjecting your site and inputting code.
5. One time URLs
One time URLs for important pages can actually make it much harder for an attacker to fabricate a clickjacking attack. A clickjacking attack is similar to CSRF, and pretty much needs only 2 things to form an attack plan: your target URL and click area. Including a one time code to your URLs not only defends you against clikcjacking scams but also protects you from CSRF attacks.
6. E-mail evaluation
Spam e-mails appearing well crafted and authentic often share malicious links which are in turn used to trigger clickjacking attacks. Therefore, it is essential to implement a strong e-mail spam filter to block spurious emails which can ultimately lead to a potential clickjacking or other form of online attacks.

















Here is a beautiful tool that will help you with clickjacking: https://clickjacker.io/
Thanks for sharing the tool with our audience 🙂