Article Summary
A comprehensive guide on rock-solid Joomla security that will help you secure your website. The guide includes DIY steps, Joomla scanner & security extension.
Joomla CMS is widespread on the internet due to its ease of use. But, even though popular, Joomla suffers cyber-attacks quite frequently. Furthermore, poor Joomla security structure is the leading cause for the majority of attacks on these Joomla websites. This long-forgotten Joomla security asks for a fresh remembrance.
Hence, we compiled this comprehensive & step-wise guide on Joomla security for you. This guide intends to provide you easy-to-follow steps to enhance your website’s security. Moreover, it has been framed keeping in mind the average Joomla user with moderate tech acumen. So, if securing your Joomla website from all coming attacks is on your agenda, then give it a read.
Click below links if you are looking for
A Brief History of Joomla Security Vulnerabilities
Did you know? It took Joomla 8 years (2009-2017) to fix a critical vulnerability in the LDAP authentication plugin!
Several vulnerabilities compromised Joomla sites in the past. For instance, the CVE-2017-8917 was a popular SQL injection vulnerability in 2017. This was so easy to exploit that any users with little knowledge about SQL could exploit it. Another vulnerability termed as CVE-2018-15882 allowed uploading specially crafted .phar files to Joomla thereby bypassing the file upload filter and allowing unrestricted file upload of even reverse shells! Therefore, here we are highlighting the key components and implementation of Joomla security that shall help you in checking these attacks.
Joomla Hacking Statistics
Various studies have shown that Joomla accounts for almost 4.3 percent of all hacked websites. However, Joomla is more secure than other competing CMSes like WordPress because Joomla ensures that all extensions deploy safety standards. Further, the CVE details of Joomla show the following results.
Clearly, XSS (36.9%) remains the biggest attack vector on Joomla. After XSS, Joomla has been compromised with gaining information (20.5%). Code execution has a 13.9% share in infecting Joomla.
Joomla Security Tips for Rock Solid Security Against Hackers
1. Take Regular Backups
Preparing for the worst-case scenario can save you a lot of time if attacked. Therefore it is advised to create a complete working backup of your Joomla site. A functional backup can restore your website in minutes after a cyber attack.
Scan your website for 140+ security issues like header security, cookie security, CORS tests, HTTPS security etc.
The two main components of a backup are:
- Joomla Core Files and other important files
- The database
Further, the methods of backing up can be flexible too. You can take a backup either in the two ways – Manual and Automated. Here is how:
Manual Process
The manual backup of the Joomla site needs two components: files and the database. This can be done in the following steps.
For Joomla Files
To backup, your Joomla files and folder, use an FTP utility or the file manager in case you use a third-party hosting.
- Step 1: The first step would be to download an FTP client like FileZilla on your local machine where you need the backup.
- Step 2: Connect to your site using SFTP instead of FTP as the latter is more secure. In the host field, enter “sftp://”(or ftp:// in case SFTP is unavailable) followed by the name of your website. In the username, field enter your username and password in the password field of FileZilla and click on “Quick Connect”.
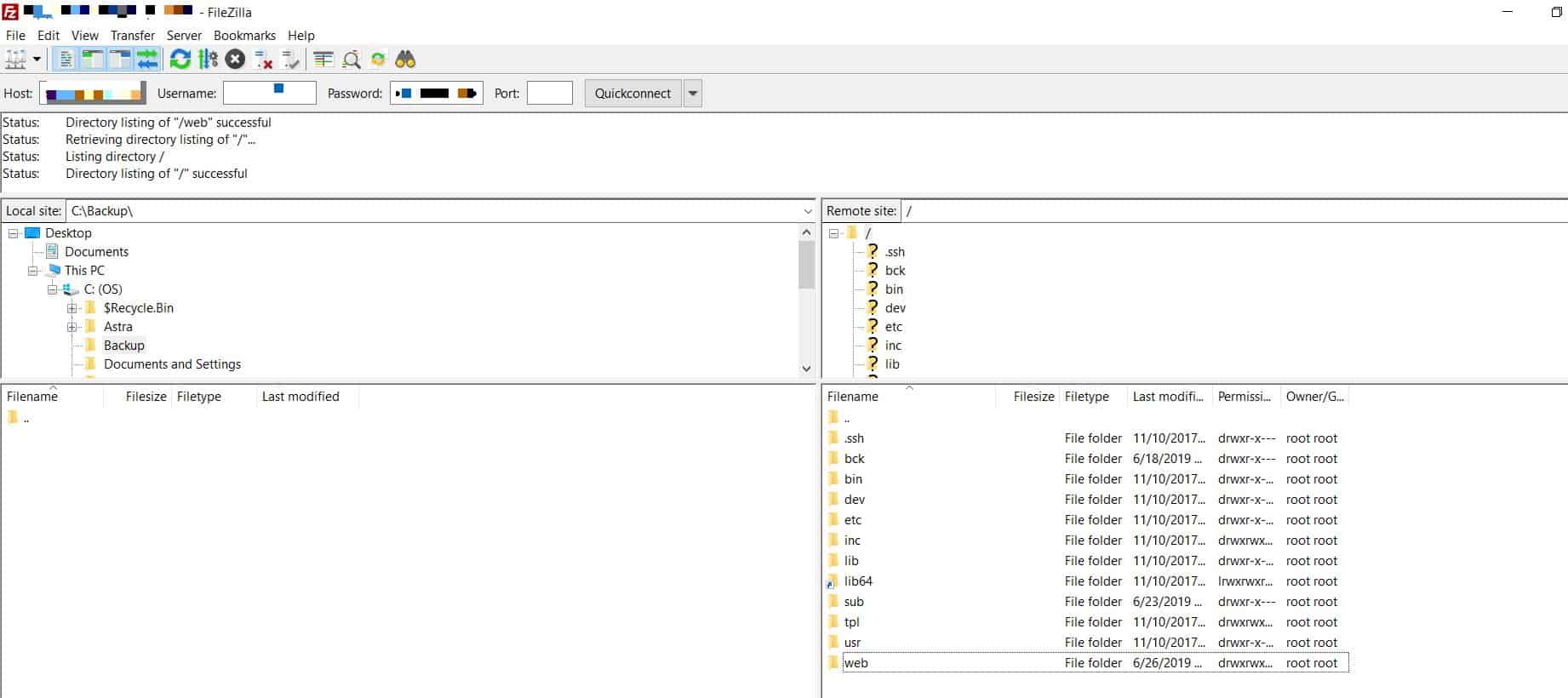
- Step 3: Now once connected, locate a folder on the local machine where you wish to save the backup of files. Enter the folder in the address bar of “local site” windowpane.
- Step 4: Finally, in the “remote site” windowpane, navigate to the root and copy the contents to “local site” windowpane. The bottom panel will show progress. Once it is complete, check your files on the local folder.
FTP clients can download all the files one by one to your local machine. However, this process may be slow. Once the files have been downloaded, compress the folder into a single zip file. Password protect it and save it to a secure location.
For Joomla Database
The database can be backed up using the command line. To accomplish this, follow these steps:
- Step 1: Firstly, identify the name of your Joomla site’s database. To do so, open the configuration.php file in Joomla root directory.
- Step 2: In this file, search for code which looks something like this:
public $user = 'user1';
public $password = 'abc';
public $db = 'user_db'; - Step 3: Remember this code as it contains your username, password, and database name.
- Step 4: Now log into your site via SSH and navigate to the folder where you want to save the copy of your database.
- Step 5: Finally, run the following command:
mysqldump -uuser1 -pabc user_db > db-backup.sql - Step 6: This command would take your user name through -u parameter and password through -p parameter. Finally, it would save the database user_db to a file called db-backup.sql.
- Step 7: Download this file locally and save it to a secure location. Afterward, delete this backup from your website. Alternatively, this can be done using phpMyAdmin but in some sites, this utility tool may not be installed so it is best to do this via SSH commands.
Automatic Process
For automatic backup, Joomla extension like Akeeba can help.
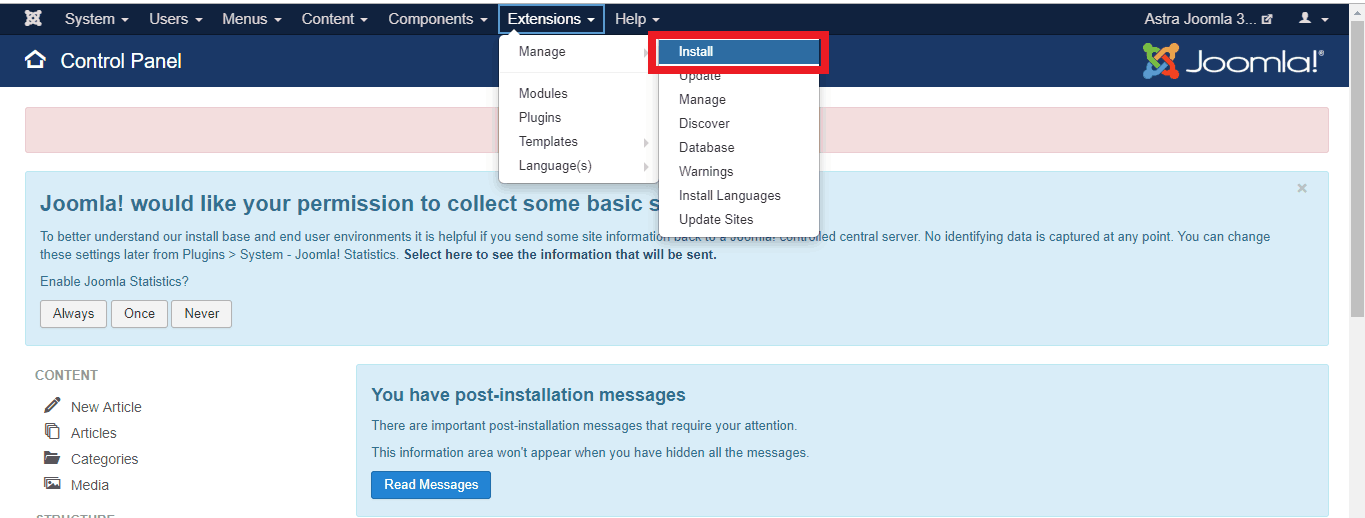
- Step 1: To install Akeeba on your Joomla site, download the file for Joomla using Akeeba’s official site.
- Step 2: Now, login to your admin area and navigate to Extensions>Manage>Install.
- Step 3: Next, click on the ‘Or Browse For File‘ button and select the .zip file. After the installation is complete, it will redirect to a page to confirm the same.
- Step 4: Now to backup your site, navigate to Components >Akeeba Backup. Once this component is accessed, there will be a ‘Backup Now’ button visible. Click it.
- Step 5: Another page will open which will allow you to add a short description to the backup and add a comment. Once you are done with both, click on the ‘Backup Now’ button and the process will be initiated. The progress can be monitored while it works.
- Step 6: When the backup is complete, you will be redirected to a page. Here, click on “Manage Backups”. This will open up a page containing all the backups. You can download the backup from here and save locally.
Dealing with a Joomla security issue? Drop us a message on the chat widget, and we’d be happy to help you. Fix my Joomla website now.
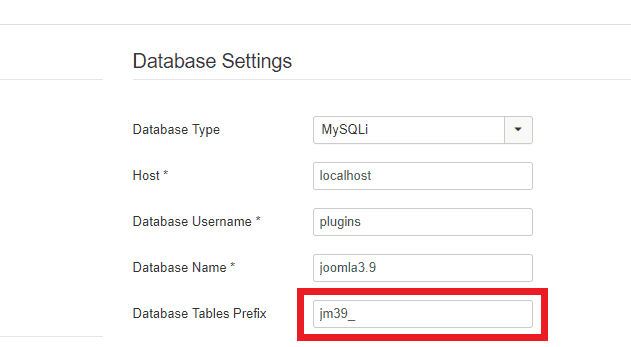
2. Joomla Database Tables Prefix
Joomla database holds sensitive information about your site including your user passwords, comments, site URLs, etc. Having the by default database prefix can invite serious SQL injection risks. Therefore, it would be a proactive step for Joomla security to add a unique prefix to your tables. This would randomize your table names. And it would make it difficult for attackers to retrieve data from the Joomla database.
To change database prefix follow these steps:
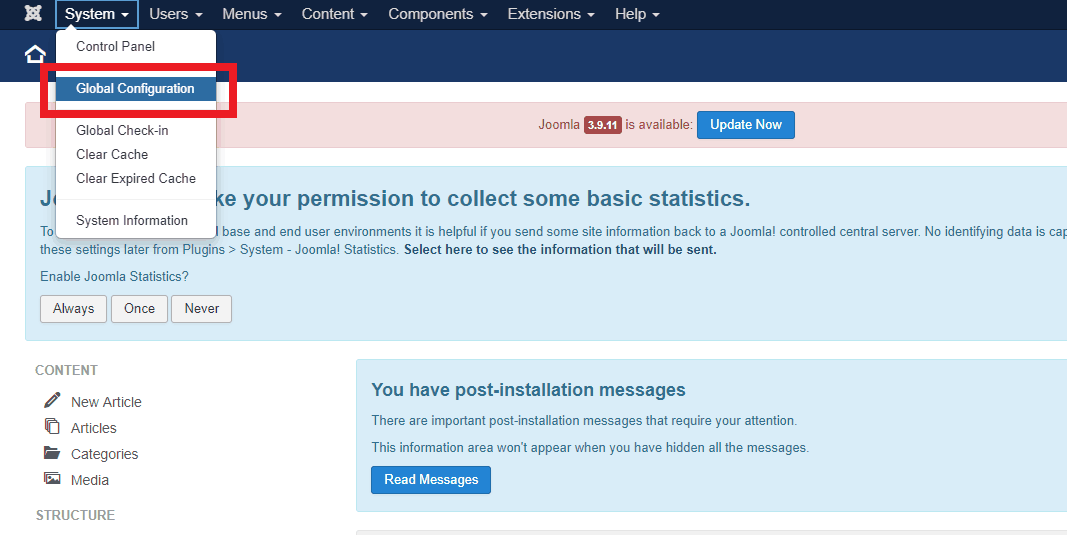
- Step 1: Firstly navigate to System>Global Configuration.
- Step 2: Now, click the Server Tab and open the ‘Database Settings‘.
- Step 3: Finally, in here edit the ‘Database Tables Prefix‘ value.
3. Keep Your Joomla Website Updated
Although, Joomla has a dedicated security team which is known for rolling out patches quickly. Yet, not patching your Joomla site from official updates can make it vulnerable to hacking and spam campaigns running on the web. For instance, the shade ransomware specifically targeted sites running on Joomla by exploiting buggy extensions. Apart from ransomware, once compromised, your Joomla site can also be used to churn out large quantities of spam.
Thus, updating Joomla can provide security and stability to the site. Further, not all updates are full site version updates. A few updates may be minor updates and bug fixes while some updates are version updates. To check your site for updates do the following:
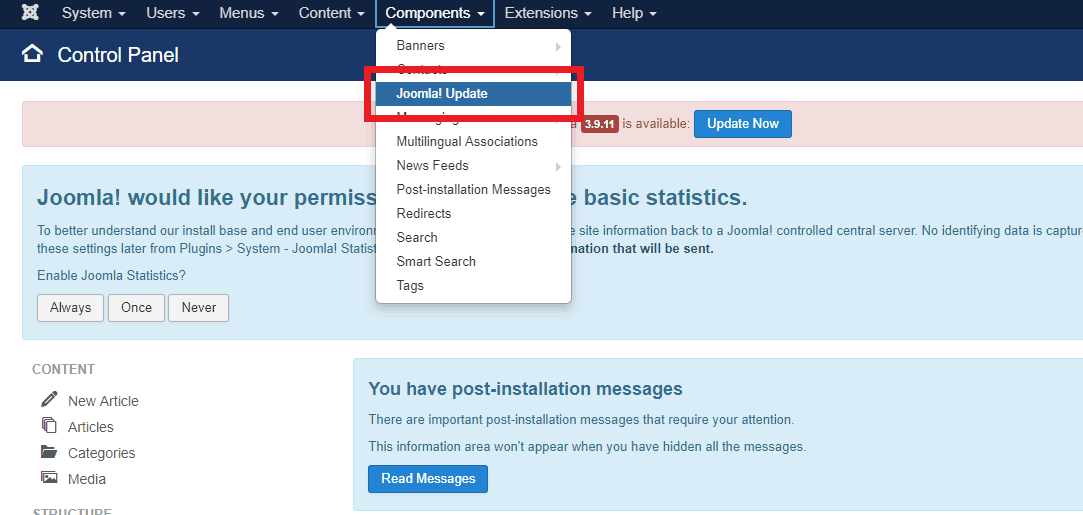
- Step 1: Login to your Joomla site as the administrator
- Step 2: Thereafter, navigate to Components>Joomla Update
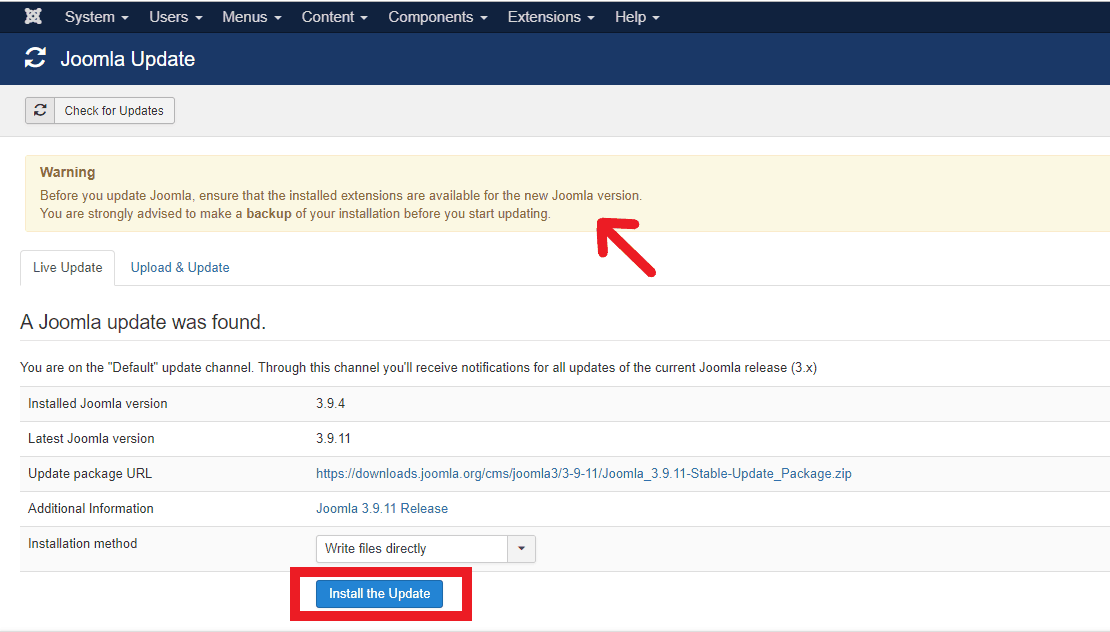
- Step 3: Now, Joomla will check if any new update is available. If it shows a new update, simply click on “Install the Update” option.
Joomla Version Update Process
Before updating to a newer version of Joomla certain things should be looked out. These are:
- Templates Update: Check if your Joomla templates are compatible with the newer version. If not, ask the template provider to update or use an alternative.
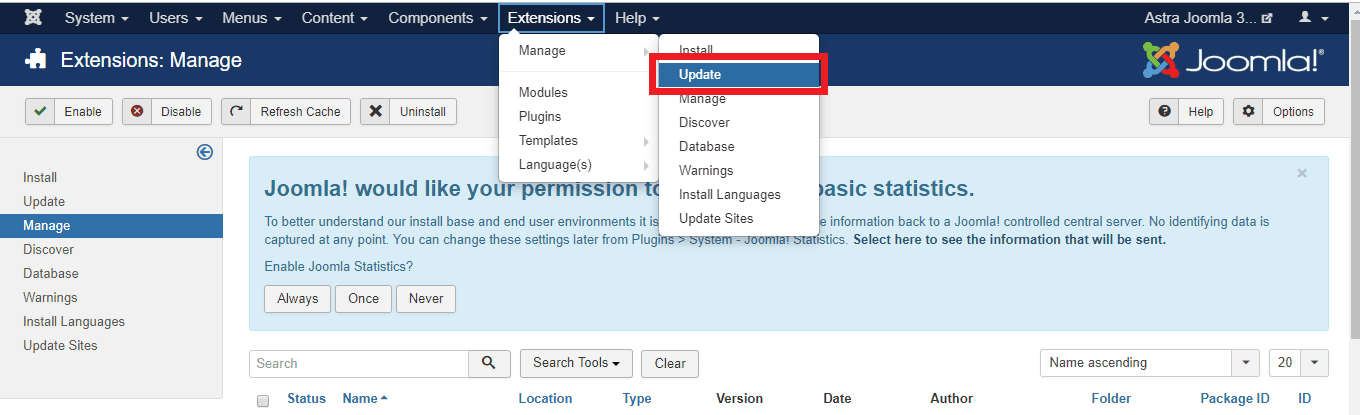
- Extensions Update: Inspect and make sure that all the Joomla extensions are compatible with the newer version. Remove all those which are not compatible. To update the extensions, navigate to Extensions>Manage and click on update.
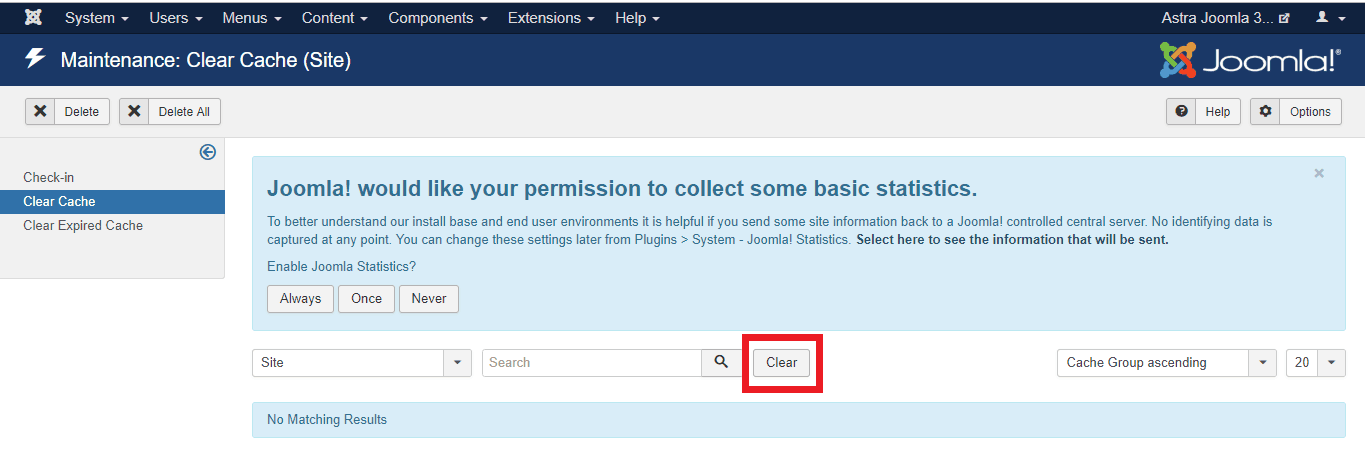
- Clear Cache: After updating to a newer version of Joomla, clear the cache from your Joomla site. This can be done using the inbuilt functionality of Joomla. Look at the image given below for reference.
Note: To stay updated with the latest developments in Joomla security, subscribe to official email notifications of Joomla.
4. Hide Your Joomla Version
Often, the attackers first fingerprint your website. Therefore sending out the Joomla version on each page can make it convenient for hackers to chose an exploit for your site for the specific version. Thus, for better security, always hide the Joomla version in the main template file.
Here is how you can do this:
- Step 1: Firstly, navigate to the following location: /yourwebsiteroot/templates/yourtempaltename/index.php
- Step 2: Open this file in a text editor and within it, look for the code:
<jdoc:include type="head" />. Use the search feature of text editor. - Step 3: Once this line is found, add the following code right before it:
$this->setGenerator(""); - Step 4: Now, your site will now hide your Joomla version. In case you update your site, make sure to repeat this process for Joomla security.
However, using Astra will automatically block any sensitive info leakage from your site. Still having trouble in updating your Joomla site, get help.
5. Use .htaccess to deploy basic configuration settings
A Joomla website comes with an already written .htaccess file. .htaccess files are exclusive to the apache server and you can use it to control a couple of security settings on your website.
You can use .htaccess to block users, to password-protect certain files & folders, to redirect users to other pages on your website.
.htaccess is a simple text file placed inside your website’s root folder. You can use the pre-configured .htaccess file defined by Joomla to better protect your website.
Here is the recommended .htaccess content by Joomla.
##
# @package Joomla
# @copyright Copyright (C) 2005 - 2018 Open Source Matters. All rights reserved.
# @license GNU General Public License version 2 or later; see LICENSE.txt
##
##
# READ THIS COMPLETELY IF YOU CHOOSE TO USE THIS FILE!
#
# The line 'Options +FollowSymLinks' may cause problems with some server configurations.
# It is required for the use of mod_rewrite, but it may have already been set by your
# server administrator in a way that disallows changing it in this .htaccess file.
# If using it causes your site to produce an error, comment it out (add # to the
# beginning of the line), reload your site in your browser and test your sef urls. If
# they work, then it has been set by your server administrator and you do not need to
# set it here.
##
## No directory listings
<IfModule autoindex>
IndexIgnore *
</IfModule>
## Can be commented out if causes errors, see notes above.
Options +FollowSymlinks
Options -Indexes
## Mod_rewrite in use.
RewriteEngine On
## Begin - Rewrite rules to block out some common exploits.
# If you experience problems on your site then comment out the operations listed
# below by adding a # to the beginning of the line.
# This attempts to block the most common type of exploit `attempts` on Joomla!
#
# Block any script trying to base64_encode data within the URL.
RewriteCond %{QUERY_STRING} base64_encode[^(]*\([^)]*\) [OR]
# Block any script that includes a <script> tag in URL.
RewriteCond %{QUERY_STRING} (<|%3C)([^s]*s)+cript.*(>|%3E) [NC,OR]
# Block any script trying to set a PHP GLOBALS variable via URL.
RewriteCond %{QUERY_STRING} GLOBALS(=|\[|\%[0-9A-Z]{0,2}) [OR]
# Block any script trying to modify a _REQUEST variable via URL.
RewriteCond %{QUERY_STRING} _REQUEST(=|\[|\%[0-9A-Z]{0,2})
# Return 403 Forbidden header and show the content of the root home page
RewriteRule .* index.php [F]
#
## End - Rewrite rules to block out some common exploits.
## Begin - Custom redirects
#
# If you need to redirect some pages, or set a canonical non-www to
# www redirect (or vice versa), place that code here. Ensure those
# redirects use the correct RewriteRule syntax and the [R=301,L] flags.
#
## End - Custom redirects
##
# Uncomment the following line if your webserver's URL
# is not directly related to physical file paths.
# Update Your Joomla! Directory (just / for root).
##
# RewriteBase /
## Begin - Joomla! core SEF Section.
#
RewriteRule .* - [E=HTTP_AUTHORIZATION:%{HTTP:Authorization}]
#
# If the requested path and file is not /index.php and the request
# has not already been internally rewritten to the index.php script
RewriteCond %{REQUEST_URI} !^/index\.php
# and the requested path and file doesn't directly match a physical file
RewriteCond %{REQUEST_FILENAME} !-f
# and the requested path and file doesn't directly match a physical folder
RewriteCond %{REQUEST_FILENAME} !-d
# internally rewrite the request to the index.php script
RewriteRule .* index.php [L]
#
## End - Joomla! core SEF Section.
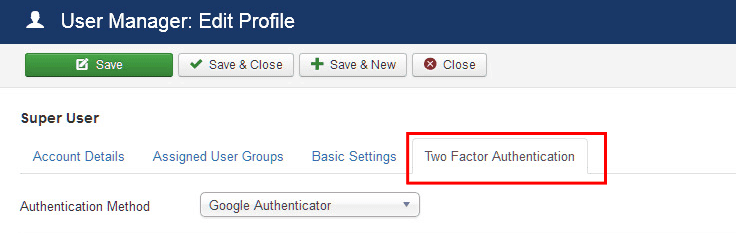
6. Use Joomla Two Factor Authentication
Two-factor authentication adds an extra layer to Joomla security. To enable two-factor authentication in Joomla:
- Log in and navigate to User Manager>Edit>Two-Factor Authentication Tab.
- If you are unable to find this plugin then go to the Plugin Manager. In there, navigate to Two Factor plugins and enable the one for Google Authenticator.
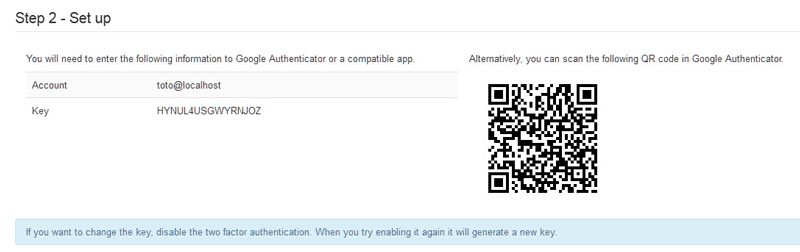
- Now to enable two-factor authentication from Google, download the Google Authenticator app on your mobile or computer.
- Now, a QR code will be visible to you in options in your Joomla site. Scan this code using the Google Authenticator app on mobile. Or add the key in Google Authenticator running on a computer.
- Now navigate to the Activate Two-Factor Authenticator field of your Joomla site. Here, enter the six-digit code generated on your Google Authenticator App. Finally, click on save and close.
- After you log out, now you will see that for login, Joomla will ask for a secret key along with the password. This secret key can be obtained from the Google Authenticator app on your mobile or computer.
7. Restrict Access to Joomla Admin Area
Since the Joomla admin area is a sensitive resource, it is wise to limit access by IP filtering. This can also be done for other sensitive folders of Joomla. To implement this,
- Step 1: Firstly create a .htaccess file if not already present in the directory you wish to protect.
- Step 2: Add the following code to the .htaccess file:
Order Deny, Allow
Deny from all
Allow from xx.xx.xx.xx - Step 3: Enter the IP you wish to allow access from in place of the xx.xx.xx.xx. However, if you have a dynamic IP, this doesn’t seem to be a good idea.
- Step 4: If this code doesn’t work for you, try appending this to the .htaccess file:
RewriteEngine on
RewriteCond %{REQUEST_URI} ^(.*)?administrator$
RewriteCond %{REMOTE_ADDR} !^xx\.xx\.xx\.xx$
RewriteRule ^(.*)$ – [R=403,L]
If you use Astra, it can block users on your Joomla site based on IP address or geolocation.
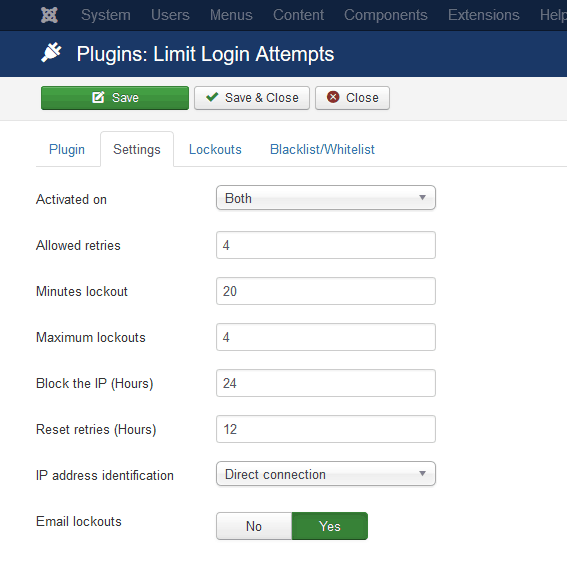
8. Limit Login Attempts in Joomla
It is necessary to limit the login attempts on admin panel to avoid brute force attacks on Joomla security. At present this can only be implemented by various Joomla extensions. One such freely available plugin is the “Limit Login Attempts” plugin. To install this plugin:
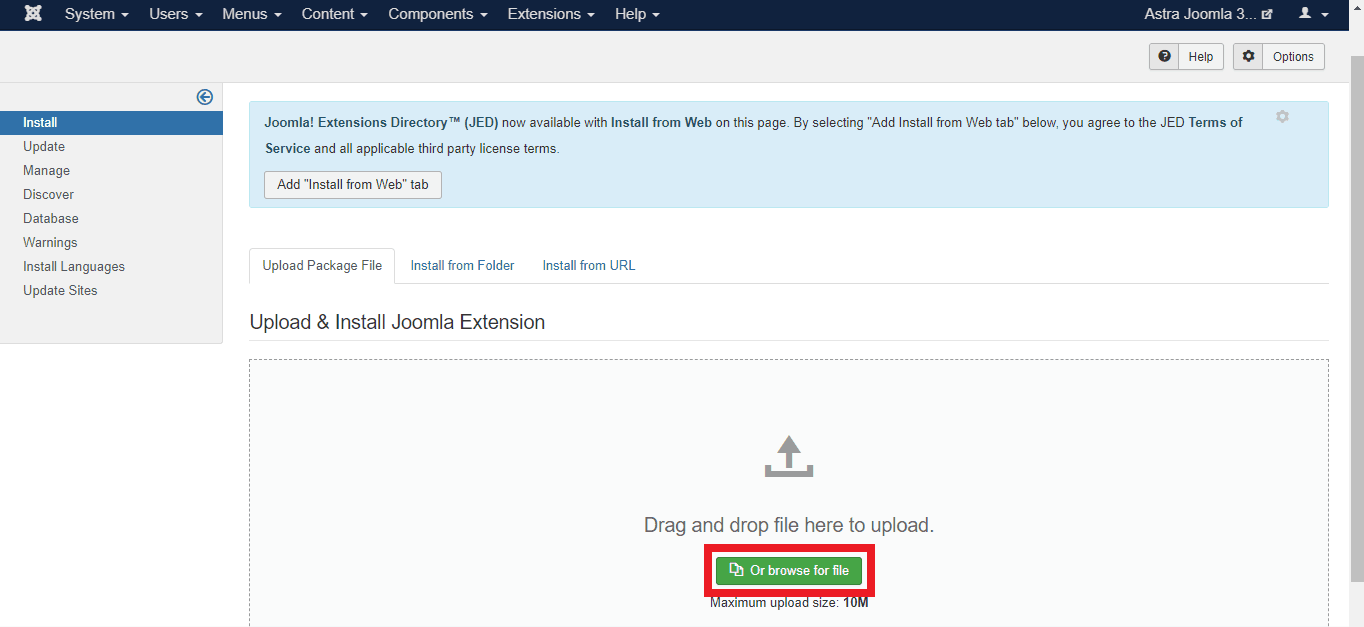
- Step 1: Download the .zip file from the official site. Now login to your admin area and navigate to Extensions>Manage>Install
- Step 2: To install the “Limit Login Attempts” plugin, now click on the ‘Or Browse For File‘ button and select the .zip file downloaded by you. After the installation is complete, it will redirect to a page to confirm the same.
- Step 3: Now navigate to Components >Limit Login Attempts. Once this plugin is accessed, there will be a “Settings” button visible. Click it.
- Step 4: Here, you can tweak various parameters like allowed tries, etc. After changing, click on the “Save & Close” button.
9. Use Strong Passwords
Using a secure password is necessary for healthy Joomla security. Make sure your login password is long enough (8-14 characters) and includes alphabets, numbers, and symbols. Since, passwords are case sensitive, using both uppercase and lowercase letters make it even stronger. Further, make it a habit to change passwords at least once a month.
On the other hand, a weak password is one which can be guessed easily. Passwords like your own name, your website’s name, 12345678, 9874561, etc. categorizes as weak passwords.
You can create passwords either on your own or use an online password generator for the purpose. However, if you are creating a password on your own, here is an example of how you can convert that to a strong password.
Replace letters with numbers & symbols
Example-“Spooky Halloween” becomes “sPo0kyH@ll0w3En”
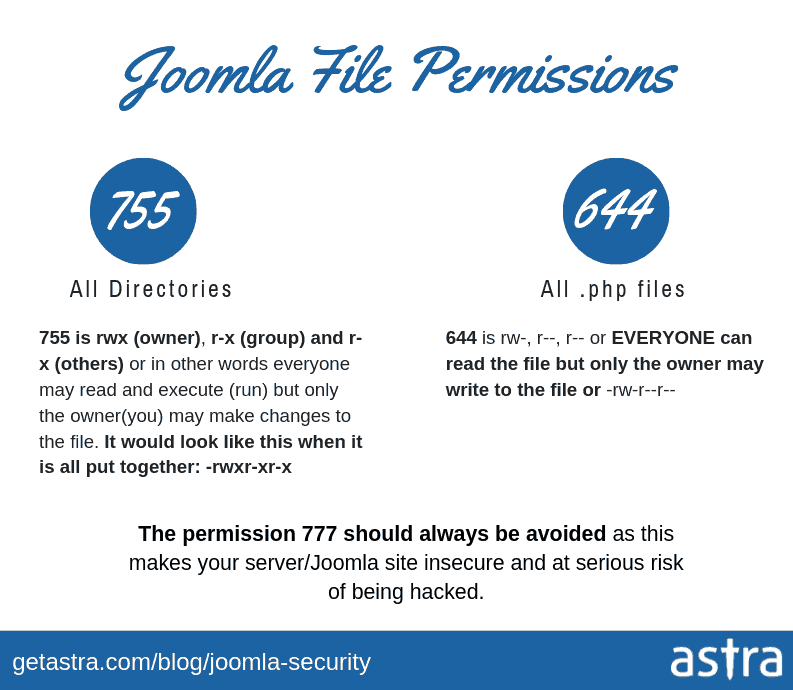
10. Set Recommended Joomla File Permissions
Joomla security can be further strengthened if file permissions are set correctly. The default suggestion by Joomla is 644 for files and 755 for directories.
- Open your FTP client like FileZilla and connect to your website.
- Select the file/folder whose permission you wish to change. Right-click and select the File Permissions option.
- For files, change the Numeric Value field to 644 for files and for directories, change it to 755. Finally, click on the “OK” button.
- Set Configuration.php file permissions to 444 & never use 777 permissions for files & folders
However, if some of your permissions are incorrect and attackers try to modify those files, Astra will automatically block the attempts and secure your site.
Dealing with a Joomla security issue? Drop us a message on the chat widget, and we’d be happy to help you. Secure my Joomla website now.
11. Update PHP version of your Joomla website
Using the latest version of PHP can protect you from a variety of Joomla hacking attacks and to strengthen your Joomla security. Make sure you are using the latest version of PHP. In case you use shared hosting, ask your service provider to update. They shall update it for you. However, you can also update it from your cPanel. To do so:
- Step 1: Login to your cPanel and search for “PHP Version Manager” or in some cases “PHP Configuration option”
- Step 2: Once found, click on it. This will open the option to select the PHP version.
- Step 3: Finally select the PHP version 5.6+ or 7 and click on “Save”.
12. Disable Dangerous PHP Functions
Some functions of PHP are often used by attackers to compromise your site. Therefore, these functions are a threat to Joomla security and it is better to disable them. To do so:
- Step 1: Login to your site and open the file manager.
- Step 2: Browse and open the php.ini file.
- Step 3: Add the following code to that file: disable_functions = “show_source, system, shell_exec, passthru, exec, popen, proc_open, allow_url_fopen, eval”
13. Disable Script Injections
To block any attempts by the hackers to inject malicious code into the PHP files of your Joomla site, use the .htaccess file. Simply append the following code to .htaccess file to disable script injection attacks:
Options +FollowSymLinks
RewriteEngine On
RewriteCond %{QUERY_STRING} (<|%3C).*script.*(>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} GLOBALS(=|[|%[0-9A-Z]{0,2}) [OR]
RewriteCond %{QUERY_STRING} _REQUEST(=|[|%[0-9A-Z]{0,2})
RewriteRule ^(.*)$ index.php [F,L]
14. Filter Spam Comments in Joomla
A large portion of internet traffic is from automated tools. These bots often crawl websites and try to inject spam links into the comment fields of various sites. These spam comments can be a threat to Joomla security while at the same time, they can make your site look unprofessional. Therefore, vet each comment before approving. You can also use Joomla extensions like Akismet to filter spam in your comments.
15. Use Secure Hosting
Make sure your hosting provider implements Joomla security safeguards. In case of a shared server ensure that subnetting is implemented. At times cheap hosting can prove to be costly therefore, choose the hosting plan with consideration for Joomla security. Therefore, before choosing a hosting plan, look for various parameters like customization, support, reviews, etc.
16. Use SSL to Boost Joomla Security
Using SSL(Secure Socket Layer) certificate can encrypt the communication between your Joomla site and its users. This is not also good from the Joomla security perspective but can also help your site with Google rankings. Get an SSL certificate from a verified certifying authority. Finally, make sure that all your HTTP traffic is redirected to HTTPS. To implement this, append the following code to your .htaccess file:
# Redirect HTTP to HTTPSRewriteEngine On RewriteCond %{HTTPS} offRewriteCond %{HTTP:X-Forwarded-Proto} !httpsRewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
17. Joomla Security Audit
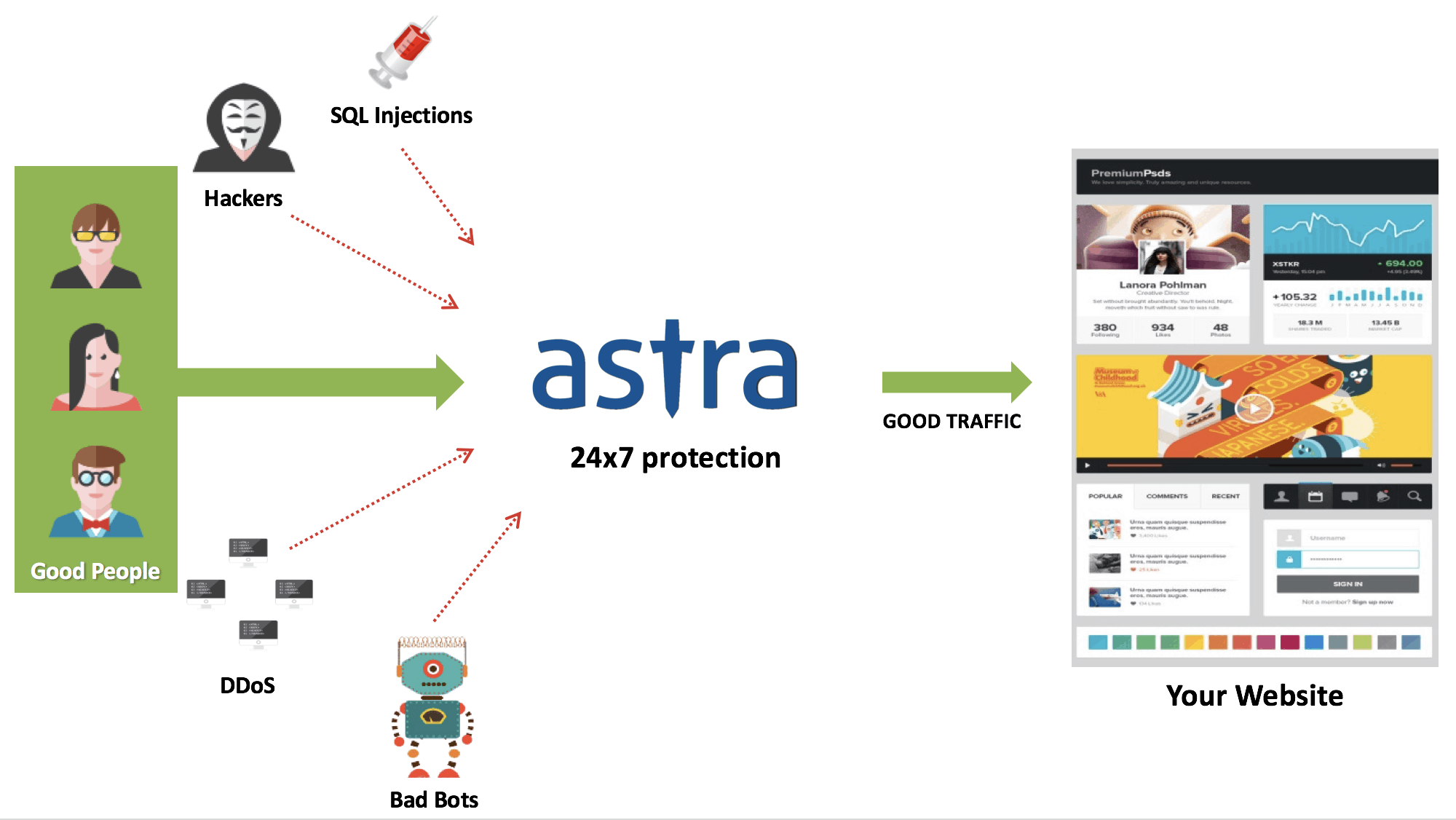
To keep your website safe & secure it is extremely important to uncover vulnerabilities before a hacker does. A security audit can help you here. You can opt for a professional security audit by Astra. Astra uses an optimized mix of manual and automated mechanism to discover vulnerabilities in your site. You will get a detailed report at the end of it. And, our security engineers will be there till the time your developers fix all the vulnerabilities.
Further, for a secured website, it is important to indulge in periodical security audits. Meticulous security audits are a great way to enhance your Joomla security.
18. Firewall to Enhance Joomla Security
A firewall can play an active role in blocking any coming attacks to your Joomla site. As the name suggests, a web security firewall acts as a barrier between your Joomla website and the internet. Every request made from the internet to your site passes through the firewall. Therefore, any hacking requests are blocked.
Astra provides a reliable and affordable firewall which can protect your Joomla site seamlessly. Moreover, such a comprehensive package comes at an affordable price and specially curated for Joomla security.
Conclusion
This guide tries to cover various practices to improve your Joomla security. Therefore, implementing each measured step by step can ensure a hassle-free working of your website in the domain of website security.
Update [December 2020]:
Recent Security Updates in Joomla Core
1. Write ACL violation in multiple core views [CVE-2020-35616]
A high impact ACL violation exploit is discovered in Joomla Core that results in lack of input validation in the process of handling ACL rulesets.
- Reported Date: November 4, 2020
- Fixed Date: November 24, 2020
- Affected versions: Joomla v1.7.0 – v3.9.22
- Issue fixed in the version: Joomla v3.9.23 (Update Immediately)
2. CSRF in com_privacy emailexport feature [CVE-2020-35615]
A low severity Cross-site Request Forgery (CSRF) vulnerability is discovered in the emailexport feature of com_privacy in Joomla.
- Reported Date: October 8, 2020
- Fixed Date: November 24, 2020
- Affected versions: Joomla v3.9.0 – v3.9.22
- Issue fixed in the version: Joomla v3.9.23 (Update Immediately)
3.User Enumeration in backend login [CVE-2020-35614]
A low impact and low severity improper handling vulnerability was discovered in Joomla Core that can lead a user enumeration attack from the backend login page.
- Reported Date: August 15, 2020
- Fixed Date: November 24, 2020
- Affected versions: Joomla v3.9.0 – v3.9.22
- Issue fixed in the version: Joomla v3.9.23 (Update Immediately)
4. SQL injection in com_users list view [CVE-2020-35613]
A high impact improper filter issue is discovered in com_users list that can result in SQL injection (SQLi) vulnerability in the backend list of Joomla core.
Reported Date: October 13, 2020
Fixed Date: November 24, 2020
Affected versions: Joomla v3.0.0 – v3.9.22
Issue fixed in the version: Joomla v3.9.23 (Update Immediately)
Got any suggestions ? Comment below!

















One of the best guide on Joomla security that I came across. Superb work 🙂
Thanks, Aditya
Your post on Joomla security is just awesome. I have read few other posts but you have gone extra mile by putting relevant screenshots. Can you please share your resources on Malware scan of Joomla site & your pricing for the same.
Thanks, Aston for your kind words. Here are the links that you have asked for
Joomla Hack Removal guide – https://www.getastra.com/blog/911/joomla-hacked-joomla-vulnerabilities-how-to-check-symptoms-fixes/
You can choose the relevant plan from here – getastra.com/pricing
Also, if you have any doubts, feel free to initiate a chat