Network penetration testing services refer to the services offered by a penetration testing company. This refers to gap analysis, vulnerability scans, compliance-specific scans, and penetration tests all of which help boost network security.
This article will discuss the top 5 network penetration testing services, the various types of network penetration testing, and discuss the features of the best network penetration testing services provider i.e. Astra Security.
Some of the features to look for when choosing the right provider for network penetration testing services are:
- Pricing: Are the pricing and quotes offered affordably?
- Scalability: Can the services offered be scaled up when required?
- Robust Vulnerability Scanning: Is the vulnerability scanner comprehensive and capable of detecting all flaws?
- Regular Pentests: Do they provide periodic quarterly or half yearly or annual pentesting options?
- Zero False Positives: Do they give a report with a zero false positive assurance?
Network Penetration Testing Service by Astra
Astra Security comes to the rescue with all the above-mentioned features. It is capable of carrying out more than 3000 tests and comprehensive vulnerability scans to find any hidden vulnerabilities within your networks. The tool’s well-detailed reports with zero false positives and POC videos assist one’s team in fixing any flaws with ease.
Top 5 Network Penetration Testing Services
1. Gap Analysis
Gap Analysis is a service offered by pentesting and security companies to analyze one’s security system thoroughly to discover any gaps in the security system. Such an analysis provides you with input on the security practices you can update or change in order to maximize your network security.
It also provides suggestions for the next steps to be taken to achieve your ideal security goals. This allows you to compare the existing security measures and the suggested ones thus gaining an understanding of how the previous security measures affect your business.
2. Vulnerability Assessment
This refers to the identification of risks and vulnerabilities that exist within the network-implemented security measures. They are scanned against known databases of vulnerabilities based on various frameworks like NIST, OWASP Top 10, and SANS 25.
Along with this vulnerabilities are also identified based on intel received. Once the identification is complete a report is generated listing the vulnerabilities, their severity scores, and possible measures for remediation.
3. Compliance-Specific Scans
Compliance-specific scans are those that are conducted specifically based on the compliance that needs to be achieved and maintained by your organization for its data security. They can be ISO 27001, SOC 2, HIPAA, PCI-DSS, and or GDPR.
You need to make sure that the network penetration testing services provider opted by you can scan for these regulatory standards. Once the scans are complete any areas of non-compliance identified can be resolved quickly to avoid penalties.
4. Penetration Tests
Penetration tests refer to the exploitation of the vulnerabilities found while scanning the networks for flaws. These vulnerabilities are then exploited using hacker-style methods to achieve the truest simulation of a real attack.
The results from such an authorized simulation are then generated as a report containing the scoping of the test, details of exploits, and the list of vulnerabilities found. One of the major advantages of a penetration test is that it provides deep insight into the damages that can be caused by an actual breach.
The reports are then made use of by the organizations for remediation and documentation purposes.
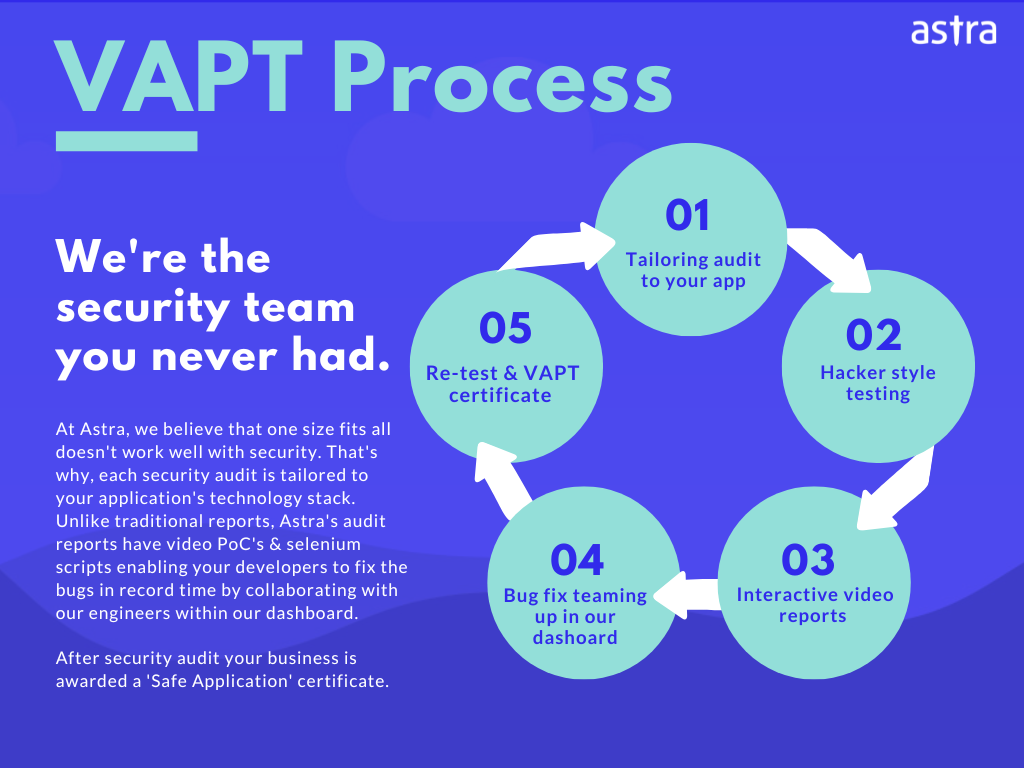
5. Boost Security
Making use of network penetration testing services boosts one’s organization’s data safety since data is transmitted 24*7 through networks and must always be protected.
Since data that is transmitted is usually protected through encryption the next vital step is to ensure the safety of the network as a whole. Thus making use of network penetration testing services boosts security and reduces the chances of security breaches.
Features of Good Network Penetration Testing Services
1. Scalability
A good network penetration testing company should provide services that are scalable i.e. can be increased or decreased based on the needs of the customer company. The company should have the resources and manpower to extend and scale up its services if the need arises.
2. Pricing
Figure out whether the network penetration testing services provider you’re going with provides customizable packages and quotes that can be arranged within your company budget.
3. Periodic Pentests
The pentest provider should also have a periodic pentest option in order to ensure that your organization’s safety measures are up to date and free of any vulnerabilities. These tests should provide detailed information regarding the current status of the security system so that your organization can take the necessary steps to ensure maximum safety.
Also Read: Third-Party Penetration Testing And Why You Should Consider It
4. Robust Vulnerability Scanning
The tool must also provide a robust vulnerability scanner capable of detecting major and minor vulnerabilities, and even business logic errors that may be plaguing your business revenue. It should also provide scans-behind-logins to ensure that the authorization measures in place only provide access to those who have the permissions.
5. Zero False Positive Assurance
Another feature of note with a good network penetration testing company is their assurance of zero false positives. Check if they provide thorough expert vetting of automated pentest results to avoid any false positives in the report.
Types Of Network Penetration Testing Services
Network penetration testing services are popularly divided into two major categories:
- External Network Penetration Testing Services
External network penetration testing services refer to carrying out vulnerability assessments and penetration tests on the network as remotely for the purposes of documenting and achieving a security audit.
The externally facing assets of an organization are exploited to gain access to its network and thus the data being transmitted. If successful, a report of the exploited vulnerabilities and remediation measures are generated to avoid an actual breach.
- Internal Network Penetration Testing Services
Internal network penetration testing services are done internally by the organization itself or by hiring third-party pentest providers. Such a penetration test looks for vulnerabilities from within the network itself.
Employing internal pentesting services can result in vulnerabilities being missed out or not getting identified as the testing company is already used to the system and may only focus on crucial areas leaving out equally vulnerable areas undetected.
Also Read: Internal Penetration Testing
Best Network Penetration Testing Service Provider- Astra Security
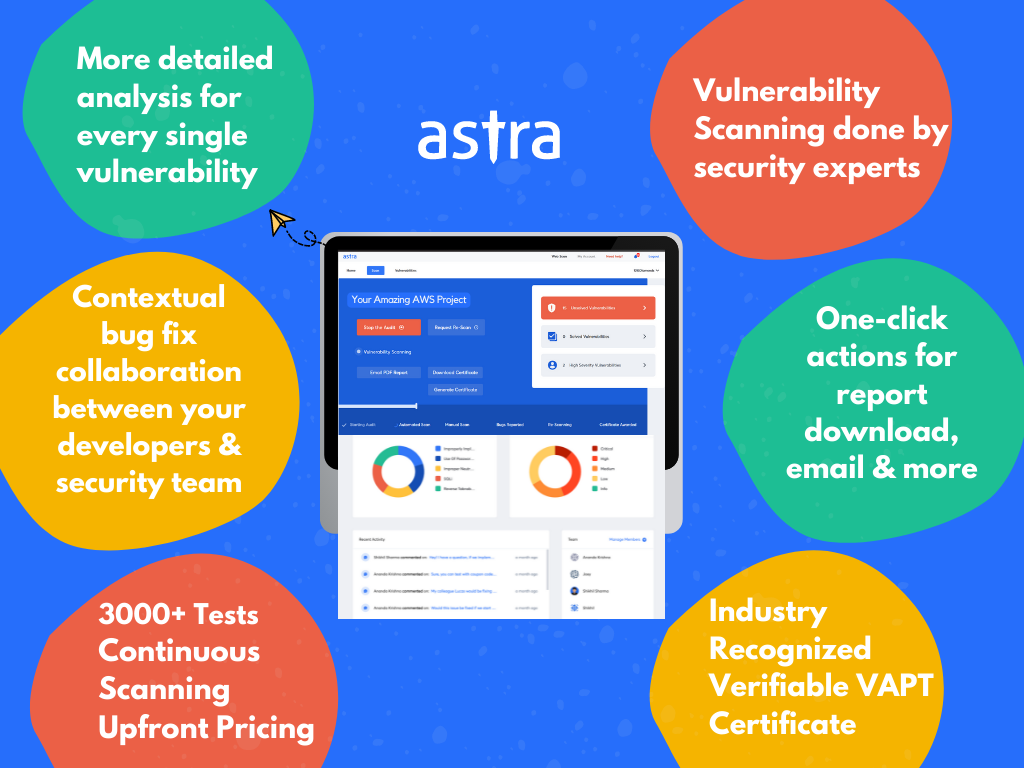
1. Regular Pentests
Astra provides continuous hacker-style penetration tests to identify and exploit vulnerabilities through vulnerability scans. This helps organizations gain an in-depth understanding of how an actual hack would affect their systems, network, and data.
2. Continuous Vulnerability Assessment
Astra provides a continuous comprehensive vulnerability assessment of your networks to ensure that there are no vulnerabilities. If scan the detect any vulnerabilities these are segregated based on their severity and explained in detail in the reports which can be used for remediation.
Also Read: Continuous Penetration Testing: The Best Tool You’ll Find
3. Comprehensive Vulnerability Scanner
Astra Pentest provides a world-class comprehensive vulnerability scanner that is capable of finding vulnerabilities using NIST and OWASP methodologies. These vulnerabilities are identified based on known CVEs, OWASP Top 10, SANs 25, and intel from various reliable sources.
With a total of ease of use and navigation, Astra’s dashboards win its customers over its great user experience. There are separate dashboards available for pentest and compliance making it easier for identifications and resolutions.
The dashboard displays the vulnerabilities found in real-time with the severity scores and provides an option of collaboration with the target’s development time for quicker smoother patching.
5. Maintain Compliance
Astra helps maintain compliance with its compliance-specific scans for regulatory standards like PCI-DSS, SOC2, GDPR, ISO 27001, and HIPAA. Astra’s scans find areas of non-compliance based on the compliance standards you choose to scan for. This is important as your organization can stay compliant and avoid any hefty fines.
6. Detailed Reports
Well-detailed reports are yet another alluring feature of Astra’s network penetration testing services. These reports have the scope of testing explained, vulnerabilities found on scanning, methods employed for exploitation of vulnerabilities, and the damages and information revealed from exploiting them as well.
Based on this, the report also mentions the CVSS scores for these vulnerabilities and well the detailed steps to take to patch them up. These reports are extremely useful for organizations when it comes to patching, or for documenting purposes for an audit.
7. Pentest Certificate
Astra pentest certificate is a must-have and is only provided to customers who patch all the vulnerabilities found in the network penetration test and obtain a rescan to ensure that there are no further vulnerabilities.
This certificate is publicly verifiable and can be displayed on customer websites to showcase its reliability and security-conscious nature. This brings about more customers who trust the services offered by your network.
8. 24*7 Customer Care
Astra provides 24*7 expert assistance to its customers through e-mails, phone calls, and even the dashboard. Customers can touch with any queries they have regarding any vulnerabilities within the reply box under every vulnerability detected.
9. Zero False Positive
Zero false positives are a sure thing with Astra’s thorough vetting which is done by expert network pentesters based on the automated pentest results obtained. This double checking, therefore, ensures that the customers don’t have to worry about any false positive vulnerability detection.
Conclusion
This article has successfully discussed and defined what network penetration testing services are and explained the best services to keep note of. Along with this the features to keep in mind while looking for a provider of such services have also been mentioned.
Astra Pentest with its impeccable network penetration testing services has been featured and explained in the article for your benefit. So head on over to Astra to make your networks as safe as possible!
FAQs
1. What are the three different penetration testing methodologies?
The three different network penetration testing methodologies are black-box, gray-box, and white-box penetration testing.
2. Why should network penetration testing be performed?
Network penetration testing is essential to ensure that network security is maintained to avoid any malicious attacks.
3. Why are regular network penetration tests required?
Regular network penetration tests are required to scan and test the networks to find any vulnerabilities that may have risen before they cause any damage.
















