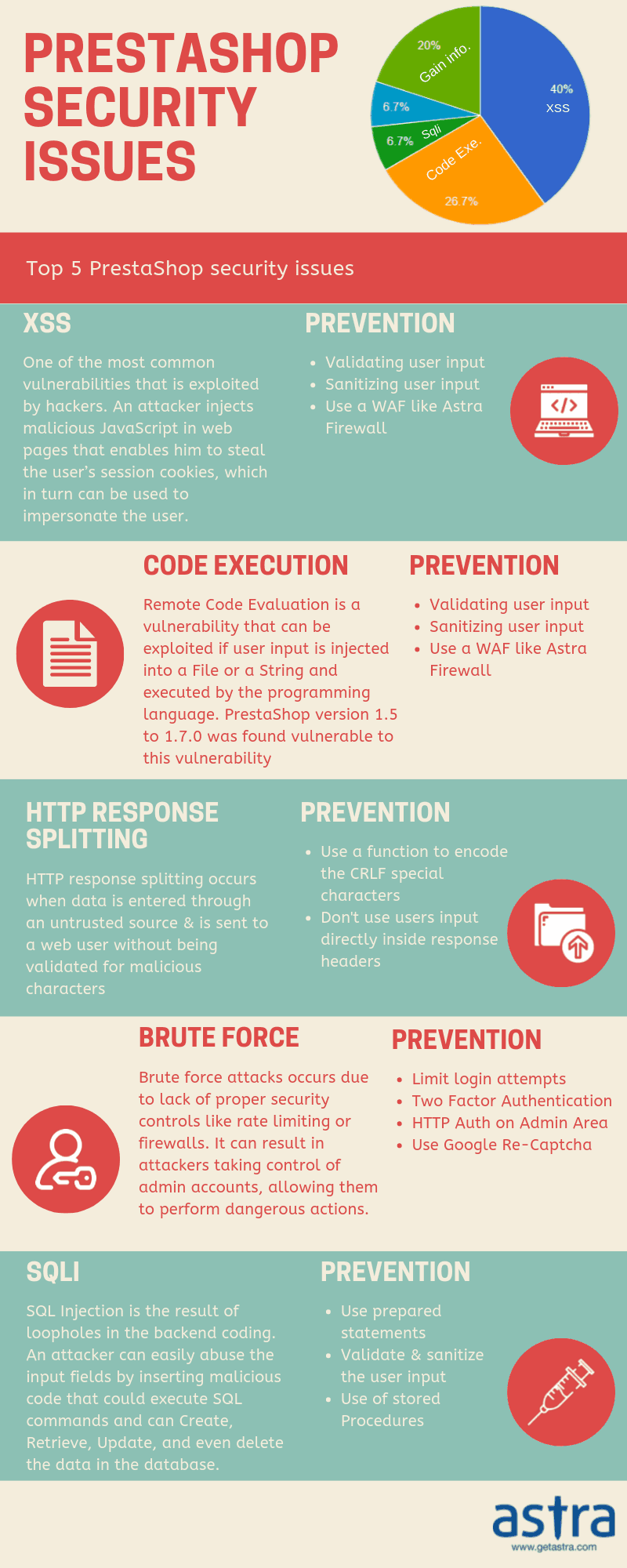
Prestashop Security Issues
In the ever-thriving business of online retail, Prestashop is a competitive contender in the global retail e-commerce Software Market. While this industry has been largely dominated by big players like Magento, Opencart, and Shopify. Prestashop is rising up the ranks and is being accepted as a reliable alternative for setting up online retail businesses. An immensely feature-rich, free, open-source e-commerce solution used to run stores in the cloud or via self-hosting, Prestashop is currently being used by around 250,000 shops worldwide and with popularity security issues become common.
However, e-commerce software is constantly under scrutiny for being targets to malicious attacks looking to steal credit card information, essential consumer data or gain admin privileges. A steep rise in the number of Prestashop security issues has been witnessed in the past few years.
In this blog, we elucidate some of the most commonly found vulnerabilities in Prestashop in the past:
1. XSS (Cross Site Scripting Vulnerability)
Cross-site scripting is one of the most commonly occurring vulnerabilities in CMSs and software solutions nowadays. In Prestashop’s case, it’s been no exception. Prestashop versions before 1.5 encountered multiple cross-site scripting (XSS) vulnerabilities which essentially allows remote attackers to inject arbitrary web script or HTML to cause modification of some system files or information.
XSS vulnerabilities are often exploited when the system fails to properly sanitize user-supplied input. The attacker leverages this loophole and executes an arbitrary script code in the browser of an unsuspecting user and attract him to follow a malicious URI. This way, the attacker can get access to cookie-based authentication credentials, paving the way to numerous other Prestashop attacks.
Facing security issues with Prestashop? Drop us a message on the chat widget and we’d be happy to help you. Fix my Prestashop website now..
2) UI-Redressing/Clickjacking vulnerability
The UI-Redressing/ Clickjacking security issue was unearthed in Prestashop versions up to 1.7.2.5. Leveraging this exploit, the attacker hides a snippet of malicious coding beneath apparently legitimate buttons or other clickable content on a website.
Clickjacking aka UI redress attack refers to a type of attack that tricks users into unwarily clicking on nefarious links set up by the attacker. On clicking these links, the attacker is able to gather confidential information, compromise the user’s privacy, or make a user perform actions online that they normally wouldn’t do. This essentially alters the site’s appearance and paves the way to initiate further Prestashop attacks and those against site visitors.
3. Remote File Inclusion
Prestashop 1.3.6 and prior versions were found to be prone to cms.php remote file-inclusion vulnerability. This occurs when it fails to sufficiently sanitize user-supplied input. Exploiting which, an attacker can fully compromise the application along with the underlying system, which may further lead to other attacks.
Remote file inclusion (RFI) is an attack targeting vulnerabilities in web applications that dynamically reference external scripts. The attacker exploits the referencing function to upload malware from a remote URL located within a different domain. An RFI attack results in information theft, compromised servers, and a complete site takeover.
4. Cross-Site Request Forgery Vulnerabilities
CSRF (Cross-site request forgery) is one of the most commonly occurring security issue among CMSs, with Prestashop being no exception. Exploiting this, a remote attacker can perform unauthorized actions on version 1.5.4 and others through the affected application. Moreover, he can also plan further attacks.
A CSRF attack involves a malicious website sending a request to a web application via another formerly authenticated website. This allows the attacker to dodge authentication procedures by impersonating the victim using his/her credentials and perform a malicious activity or financial transactions. Targets prone to such attacks are online banking services, social media applications and web interfaces for network devices.
Prestashop Hacked? Drop us a message on the chat widget and we’d be happy to help you. Fix my Prestashop website now.
5. Prestashop SQL injection
SQL injection one other common PrestaShop security issue. PrestaShop 1.6.0 and other versions were reported to be vulnerable from SQL injection. The problem lied in the parameter id_manufacturer
SQL Injection occurs due to improper sanitization of inputs. The DBMS executes the unsanitized input which ultimately leads to sensitive information disclosure and system takeover. Prestashop (1.5.5.0 – 1.7.2.5) suffers from this vulnerability and has been dubbed as CVE-2018-8824. Moreover, this is caused by the module named Responsive Mega Menu (Horizontal+Vertical+Dropdown)
6) Privilege Escalation
Termed as one of the serious vulnerabilities, Privilege Escalation occurs when a user with lower administrative privileges is granted higher privileges. Dubbed as CVE-2018-13784, versions below 1.6.1.19
Prestashop’s user cookie contains buggy encryption due to its use of Blowfish/ECD or AES encryption. Due to this, an attacker can alter the contents of a Prestashop cookie leading to privilege escalation. The attacker can then access user sessions, steal sensitive information like credit card details or gain admin access.
7) Remote Code Execution
A remote code execution vulnerability (CVE-2018-8823 )was discovered in Prestashop security this year itself, affecting PrestaShop versions 1.5.5.0 through 1.7.2.5. Remote Code Execution allows remote attackers to execute arbitrary PHP code via the code parameter. The vulnerability was found to be in the Responsive Mega Menu Pro module.
Remote Code Execution is a method through which an attacker is able to execute a malicious code and overtake control of the affected system with the privileges of the user running the application. This is often a result of buggy coding resulting in a complete compromise of the server.
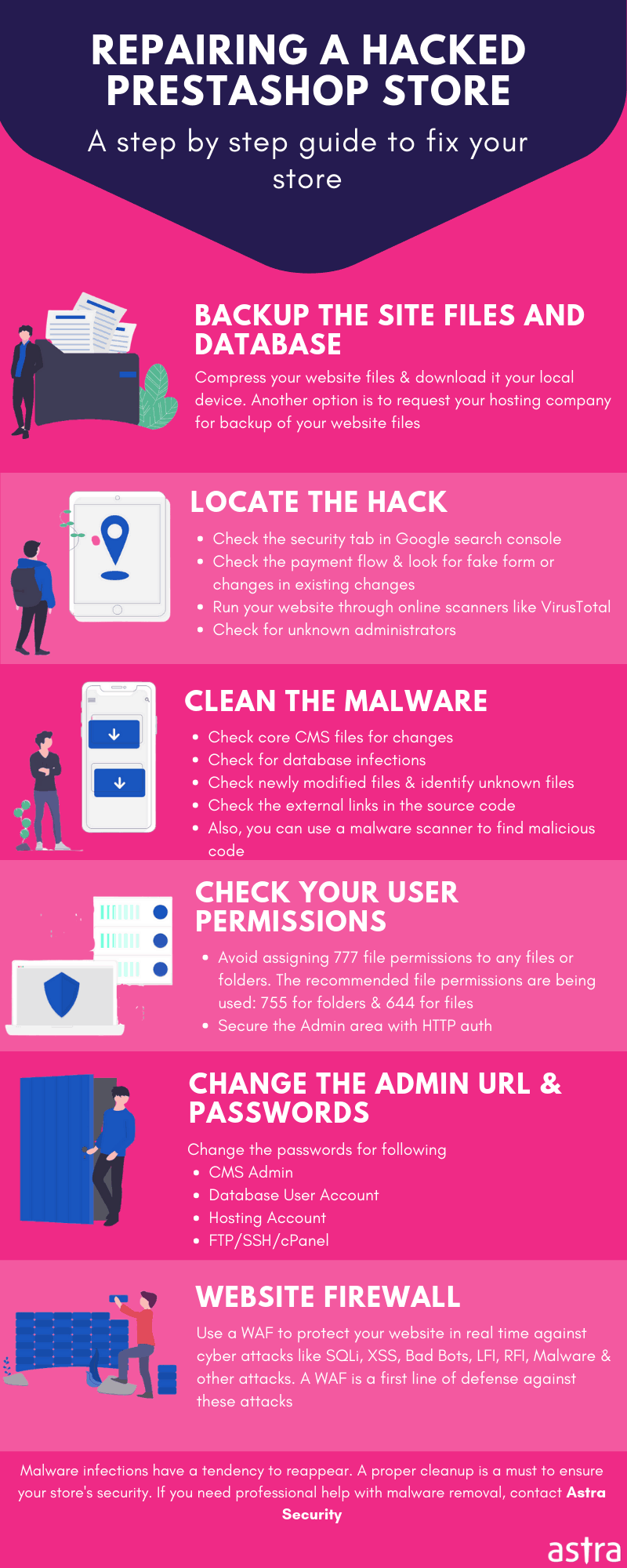
Looking for a reliable web application software to secure your site against Prestashop attacks? Get in touch with Astra’s Web Security team to avail complete web security against all possible online threats.

















Great Article, Awesome