WordPress is loved by website owners as well as hackers. If you too have your website in WordPress, then this article is for you. Here, we have listed the most common WordPress security issues that are in craze with the hackers. Further, we have covered burning questions like “Who is attacking you”, “How they are attacking you” & “How can you be safe?”. And, in this article, you will find the most practical ways to protect yourself from the said threats.
WordPress’ vast usage (60 million+ websites) keeps it in demand with hackers. Even though WordPress developers leave no stone unturned in keeping the CMS secure, it is also true that the attacks on WordPress persist. Clearly, we seem to have missed a catch here. And that is, WordPress security depends more on the admin than it does on the CMS. So, if you diligently followed the security measures discussed in this article, I am sure most of your WordPress security issues will go away.
Go through the below URLs if you are looking for
- WordPress Security Guide (Reduce the chances of getting hacked by 90%)
- WordPress Hack Removal Guide
- WordPress Security Plugin
WordPress Security Issues: What are the threats to WordPress?
The threats include the following three things:
- Humans – Those are individuals hunting the web for vulnerabilities and exploit them.
- Bots – Bots are single programs developed by an attacker and used to creep into a website and attack it.
- Botnets- Botnets are a cluster of programs run on different machines, coordinated and controlled by a central server.
-
Human
Human attacks involve a live person manually searching & attacking your website’s vulnerabilities. These attacks are superior to bots and botnets for they are more nuanced and are harder to detect.
A human attacker targets websites one at a time. Thus, they skip making a noise in the cyberspace. They are very careful in their process and can remain hidden for the longest time. Most human attackers target only big and powerful sites which store huge amount of sensitive personal information. This information, if stolen, is easily monetizable. -
Bot
Bots are programs designed to automate the hacking of websites. Usually, bots are run on single machines and can target a fairly large chunk of websites. This is to say, most WordPress Site hacks have bots behind them.
Bots can check hundreds of websites at once for their versions, known vulnerabilities in it and attack if found. As a result, the bots are really fast and effective. In addition, they can exploit zero-day vulnerabilities ( vulnerabilities that are not yet known & patched by the developer) too. Unlike human attacks, bot attacks are more aggressive in these exploits and thus, easily detectable. -
Botnets
Made from the words Bot & Net, botnets represent a group of bots lurking in the cyberspace and watching sites. These are run using a web of machines, coordinated with each other to reach and exploit WordPress websites on a much larger scale. Botnet attacks are similar to bots however differ in the fact that botnets can harm much more websites paralelly than single bots.
Why are they attacking your WordPress website?
The motive behind these attacks varies incredibly. Ranging from a beginner’s curiosity at one end to executing illegal business at the other, WordPress attacks are truly scary. The following are some of the common intentions behind a WordPress website attack:
-
To Spamvertize:
Sometimes attackers use hacking and black hat SEO to redirect traffic to their illicit or spammy domain. We have seen scores of these cases on WordPress sites where an attacker plants a malicious link on the victim domain. This, sometimes, is done through spams sent via your website. It is a huge benefit for them as your website can get them higher CTR (Click Through Rate) and therefore higher website traffic.
-
To Malvertize:
Once attacked, hackers can plant malicious/obscene/redirecting ads on your website. This plantation of a malicious advertisement on websites is known as “Malvertising“. Not to say, content like pornography, illegal drug sales or other spam content could risk your customer trust and hurt your brand name in the long run.
-
To Steal Important data:
Obviously, your website contains data that are valuable for hackers. Here data may mean something as basic as customer’s email to something highly sensitive as personally identifiable information or credit card details. Stealing this data can bring the attacker high returns for he could use these emails to send spams, credit card details to make illegal purchases or he could simply make money by selling this data in the black market.
-
To Attack Other Websites:
It could also happen that the attack on your website is a part of a much bigger plan. Sometimes attackers use multiple smaller website to get to a giant one. After compromising your website, a hacker can use your site to attack WordPress security issues of other websites. Your website may eventually become a part of the malicious nexus of hacker’s domains.
How do attackers exploit WordPress Security Issues?
Till now, we have learned the what and the why of what is attacking you. Let us then quickly proceed to the how of the exploitation of WordPress Security Issues.
Before actually attacking you, the attacker wants to know two things-
- The kind of software your website is running &
- The versions of that software
He then cross-checks this information with the already available databases on the net. These databases list all the versions and the found vulnerabilities in them. After getting this info right, the attacker executes it as the following –
-
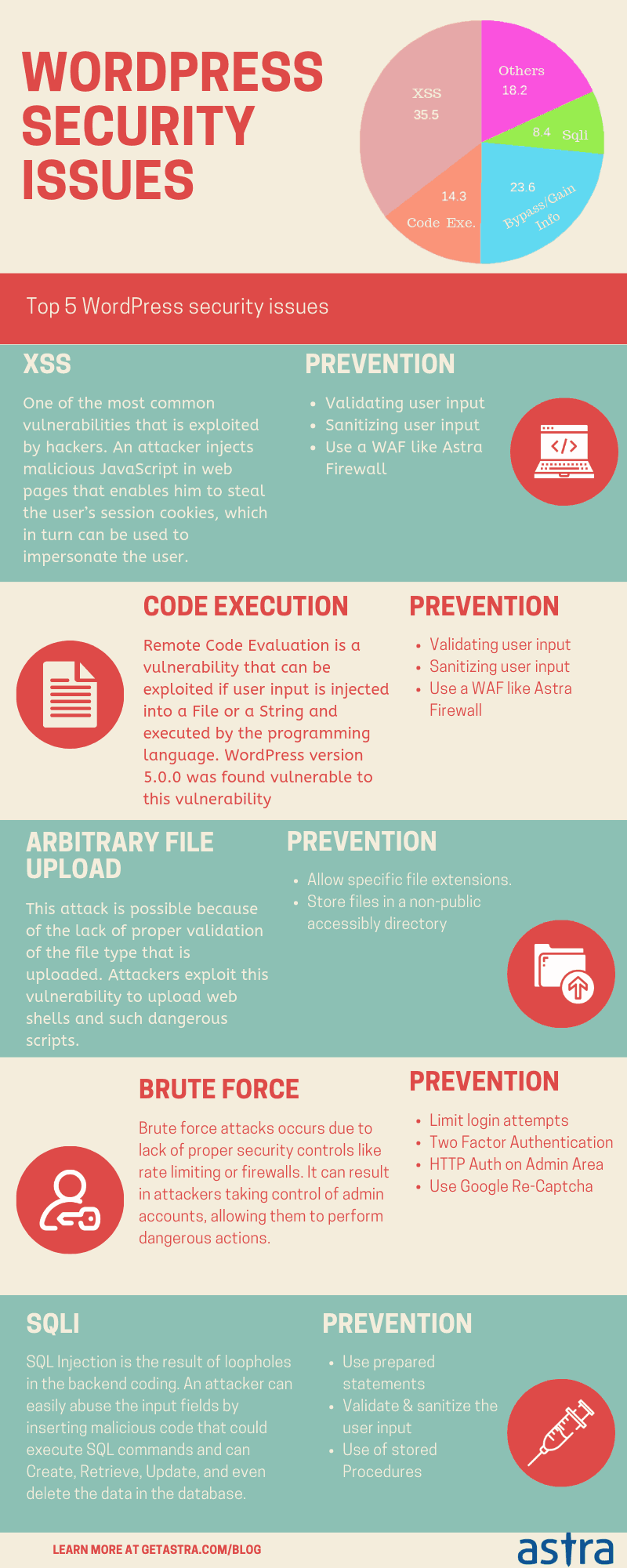
Brute-force security issue in WP
Automated bots can try different combinations of username and passwords at a freaking speed. This trial and error method to get through a website’s login page is called “Brute-force attack”. Brute-force attacks are the simplest way an attacker uses to get access to a website.
What can you do?
You can limit login attempts to discourage brute-force on your website. There are several plugins like Loginizer, WP Limit login attempts, etc which serves the purpose in WordPress.
Further, two-factor authentication is also a good security practice to stop brute-force.
Another practice is to use ReCaptcha to differentiate humans login attempts from that of bots. -
Cross-Site Scripting Attack (XSS) in WordPress
In a cross-site scripting attack, an attacker injects malicious JavaScripts in the web pages. These JavaScript lets him steal the user’s session cookies, which in turn can be used to impersonate the user. With active cookies in hand, an attacker can log into the wp-admin panel and exploit as he wishes. Cross-site scripting is the most common way an attacker exploits WordPress websites. For instance, the recent exploitation of the WordPress Live Chat Support Plugin also had XSS at the cause.
What can you do?
You can indulge in Input Validation to protect your websites from XSS. Installing a firewall also blocks XSS. To know more XSS prevention measures follow this article.
3. SQL Injection Issue in WordPress
Sometimes hackers creep into your website through the various forms on your website like the login form, register form, demo form, etc. They insert an SQL query in those entry fields, which skips validation and sanitization in case of websites with WordPress security issues. An SQL injection attack can steal, modify or delete your website’s database. This makes it particularly threatening.
What can you do?
Often SQLi is a result of poor sanitization rules. Safer sanitization codes can work wonders in this case. Use wpdb->prepare to sanitize user input. Secure your cookies as discussed in this article here.
4. File Inclusion Vulnerability Issue in WordPress
An attacker can also compromise your website by uploading malicious files on your server. This attack is possible because some scripts allow “include” or “require” attributes. Hackers fool the website’s poor validation to inject alien files in targeted scripts. Moreover, there are two types of File Inclusion attacks – Local File Inclusion (LFI) and Remote File Inclusion (RFI).
What can you do?
You can secure your website from File inclusion attacks by writing more secure codes. Also, scan your website regularly for common vulnerabilities. Here is an in-depth blog on LFI & RFI for you.
5. Cross-Site Request Forgery (CSRF) Issue in WordPress
Cross-Site Request Forgery is an attack where any hacker with a user authentication can run malicious JavaScript, XMLHttpRequests by means of specially-crafted image tags, hidden forms, etc. The next step he takes is to get the targeted user to click some malicious link containing JavaScripts. If clicked on, the scripts let the attacker access & exploit the website without the victim’s knowledge.
What can you do?
Opt for Same-origin policy, it ensures that the response from the server is sent to the authentic application and not to an attacker-controlled application. Learn all about CSRF and more safety measure here.
6. Privilege Escalation Issue in WordPress
Privilege escalation is when an attacker gains higher-level permission through unfair means. For example, you got into a website through the register page, but you manipulate it to gain the admin’s level permission. For example, the exploitation in popular WordPress plugin GDPR Compliance was done through the Privilege escalation.
What can you do?
You can prevent privilege escalation on your website by defining roles and their respective permissions on your website.
Entry Points of Hackers in WordPress
When a WordPress site is attacked, there are several main entry points or attack ‘vectors’ that are used:
-
Login page:
The brute force attack is an attack targeted at this entry point. If successful, this entry point will give hackers complete access to your website’s backend. Moreover, your WordPress login page is the most common entry point for hackers.
-
PHP code on your site:
Another entry point is the PHP code. On examination, attackers learn about the PHP code running on your website. They will try to find and exploit vulnerabilities. The PHP code extends to codes in your WordPress core, your themes, your plugins, and any other active application.
-
Register Form:
Your website’s register or demo form may serve as another entry for an attacker. From here on, he can get more advanced permits, like access to your admin panel by Privilege escalation.
-
Outdated web applications:
Most expired items are risky. No exception for plugins and applications. Your older and un-updated apps might contain serious vulnerabilities. These WordPress security issues, if exploited can cause you unanticipated grave harm.
Third-Party Applications
There are scores of plugins on WordPress, but if you download absolutely anything from any source there is trouble waiting for you. These plugins often contain vulnerabilities and poor security structure. Attackers find these under-secured third-party plugins as a perfect entry for your WordPress website.
Temporary Files and User Cookies:
Your website creates several temporary files that are public by default. This can be used to get into your website.
In addition to this, the server saves session cookies, which as we discussed is used to execute XSS on your website.
Source Code Repository Config Files:
The ‘git’ and ‘Subversion’ source control tools create directories and files that can contain sensitive information. Allowing public permission to these files can help an attacker to enter your website.
A shared server is generally a low price hosting solution. And, most budding and medium-sized websites are hosted on a shared server. However, apart from being a budget-friendly solution, the shared server does little for your website. Even if you take every security measure seriously, it is hard to say you will not be infected on a shared server. Here is a detailed blog on shared hosting and its security issues.
How can you mitigate WordPress Security Issues?
Here are the gospels of security that you must follow to get rid of these WordPress security issues-
- Invest in the right web hosting from a reputed and well-known hosting provider.
- Make a habit of taking backups of your WordPress installation. A backup can be a boon in despair.
- Use a strong password and use reCAPTCHA to secure important files.
- Limit login attempts and use two-factor Authentication for login.
- Change the WordPress Login URL and Default Username.
- Define permissions for different WordPress user roles.
- Change the WordPress default username.
- Keep WordPress user logs updated.
- Uninstall or delete unused Plugins or Themes.
- Set .htaccess Rules.
- Deny access to sensitive files in WordPress.
- Use .htaccess to harden security.
- Hide WordPress version.
To implement all the above points, please read our Step by Step WordPress Security Guide
Conclusion: WordPress Security Issues
By taking care of the above mentioned WordPress security issues, you mitigate the risks. Apart from that, having a security solution to monitor your website and its coming traffic always helps. Astra’s firewall makes it possible with its intelligent signature mapping formula. It blocks attacks like SQLi, XSS, CSRF, Bad bots, Owasp top 10, and 100+ other threats from infecting your website.
In addition to this, Astra’s malware scanner automates malware scanning for you. You can scan your website for malware whenever and as many times as you prefer.
Did you like this post? Go ahead and share it on Facebook, Twitter, LinkedIn.

















I have 10 years+ experience on building WordPress website for SME. One thing I realized is mask login area is the simplest yet effective to avoid brute force attack.
I highly recommend every single WordPress admin out there to do it.