For years OpenCart has been a popular choice for e-commerce websites due to its ease of use, simple installation, and minimal investment. Popularity comes at a price – OpenCart has been target to malware, credit card skimming, backdoors and very targeted exploits.
We work with OpenCart store owners round the clock in cleaning malware injections and the reasons for being hacked are always the same.
The top reasons for you OpenCart store being hacked:
1. OpenCart Version Has Never Been Updated
Since many of the OpenCart stores have been customized by changing the core files, developers avoid updating the OpenCart version and lose out on critical security patches.
It is good practice to use a Modification System to update your OpenCart Store:
- For OpenCart 2.X – Use the default system called OpenCart Modification System (OCMOD)
- For OpenCart 1.5.X – Use vQmod modification system
If you have made all your modifications using any of the above modification systems, you can update your OpenCart store without any hassle in future. This will ensure that latest security patches are installed and your store is malware free.
2. Plugins With Weak Security Practices
As a thumb rule, only install extensions from trusted developers. Plugins that do not follow the security best practices, may leave critical vulnerabilities which are commonly exploited by hackers.
3. No Website Firewall or Bad Bot Protection
Due to automation, it is very easy to find and exploit vulnerabilities. Use of a Website Firewall like Astra is very important to fight hackers and bad bots. Such firewalls scan all incoming requests and block all hack attempts and OpenCart malware.
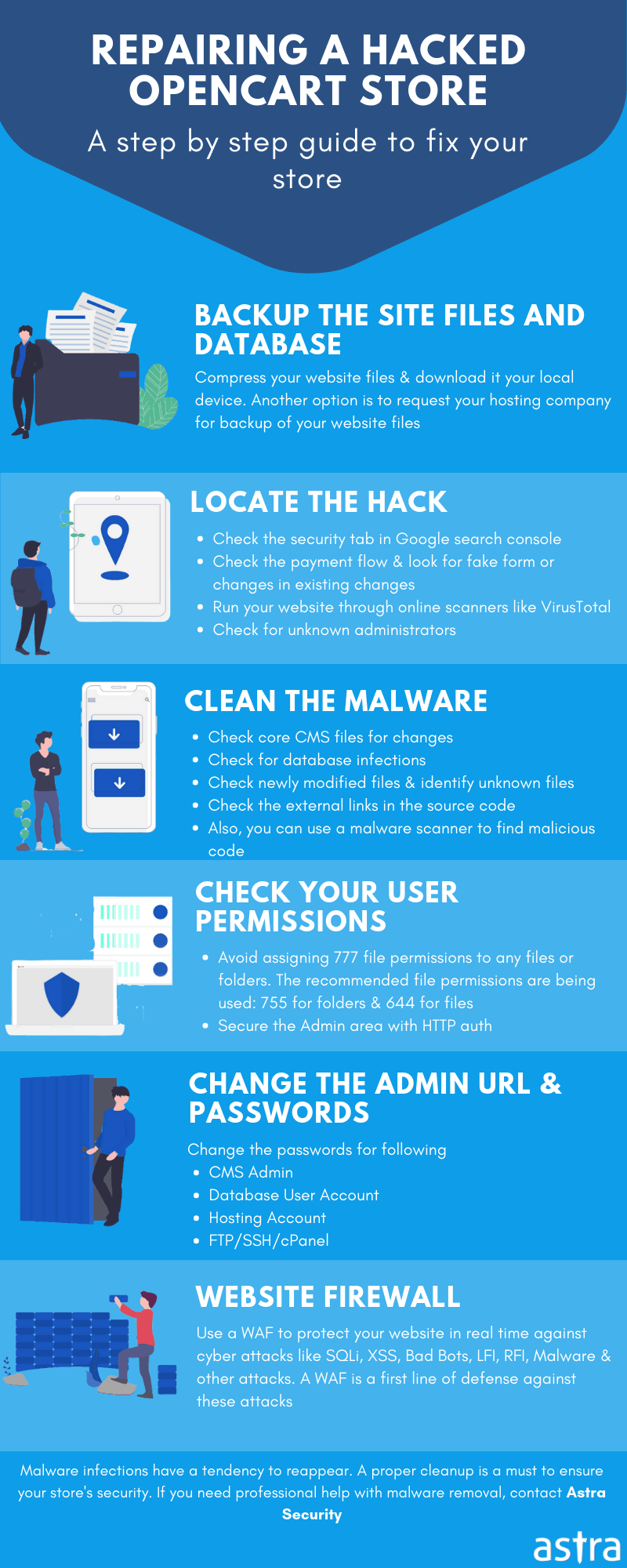
4. Unrestricted File Uploads & Unsanitized User Inputs
Some older versions of OpenCart were vulnerable to input field manipulation and could be used to inject malicious payloads. Custom developed features usually lack proper input sanitization like XSS removal, data validation & encoding before storing in the database. An example payload can be seen below.
Consequences of OpenCart Malware
Without necessary security mechanisms, hackers are able to run their malicious code on vulnerable websites like. The consequences of OpenCart Malware Injection can be fatal:
- Google Safe Browsing Blacklisting
- Theft of Customer Data
- Theft of Transaction Records
- Unwanted Redirects to Malicious Sites
- Spamvertizing
Google regularly runs malware scans and notifies Google Search users if any malware is found on your OpenCart store. This will result in a loss of reputation for your store and customers may not feel safe performing transactions. “This Might be Hacked” warning from Google looks like this:
How You Can Avoid OpenCart Malware Injection
Since OpenCart is Open Source, attackers have a better idea of the software you’re running and any publicly known security issues. Use the following proactive security tips to secure your store from OpenCart malware:
- Delete the “/install” directory after setup is complete
- Set the correct file permissions for files and folders
- Folders should have 755 permission
- Files should have 644 permission
- config.php and admin/config.php should have 444 permission
- Regularly update your OpenCart version
- Use a modification system like OCMOD or vQmod to make changes to the OC core
- Only install extensions by Trusted Developers
- Change the Admin URL by renaming the ‘admin’ folder. It should be a secret word that only you should know.
- Disable Directory by adding this code to your .htaccess file
Options -Indexes - Use of a Website Firewall like Astra to fight hackers and bad bots
If you’ve faced similar problems because of malware, tell us in the comments section below. We may be able to help!
Also, check the case study of Dim-el, E-commerce store powered by Opencart and how Astra firewall secured it from the attackers.


















So if I don’t want to use paid services what other free open source options I have to secure myself
Kanishka, as mentioned in the article it is advisable to work on OpenCart configurations to lock-down all the possibilities by which a hacker/malware can enter the website. The thing is, sometimes OpenCart by default does not comes with best security configurations. So, as a developer/store owner one should go the extra mile to ensure OpenCart configurations & server lock down is in place.
However, Open Source security tools like Mod Security can help here to flag users with malicious intent.
Way cool! Some very valid points! I appreciate you
writing this post and the rest of the site is extremely
good.
What a stuff of un-ambiguity and preserveness of valuable experience concerning unpredicted emotions.
Attractive section of content. I just stumbled upon your weblog and in accession capital to assert
that I get in fact enjoyed account your blog posts.
Anyway I will be subscribing to your feeds and even I achievement you access
consistently quickly.
I’m not sure where you’re getting your information, but great topic.
I needs to spend some time learning more or understanding
more. Thanks for wonderful info I was looking for this information for my mission.
I have been exploring for a little for any high quality articles or weblog posts in this kind of house .
Exploring in Yahoo I eventually stumbled upon this website.
Studying this info So i’m happy to exhibit that I have an incredibly
excellent uncanny feeling I discovered just what I needed.
I so much indubitably will make sure to do
not omit this site and provides it a look regularly.
Incredible points. Great arguments. Keep up the amazing work.
If you are going for most excellent contents like I do,
simply pay a visit this website every day because
it gives quality contents, thanks
Somebody necessarily assist to make significantly posts I might state.
This is the very first time I frequented your web page and
to this point? I amazed with the research you made to create
this particular publish incredible. Magnificent process!
Hi my loved one! I wish to say that this article is awesome, nice written and include approximately all vital infos.
I’d like to peer more posts like this .
Mʏ brotһer suggеsted I might like this
blog. He was totally right. This post trսly made my
day. You can not imagine just how much time I had ѕpᥱnt for this
info! Thanks!
Awesome blog! Do you have any recommendations for aspiring writers?
I’m planning to start my own site soon but I’m a little lost on everything.
Would you suggest starting with a free platform like WordPress or go for a paid option? There
are so many options out there that I’m completely overwhelmed ..
Any tips? Thanks!
[…] the application layer of web applications, where developer faults are more probably. Take the Opencart Malware Injection for example. Attackers circumvent security measures at application end to run their malicious […]
[…] the application layer of web applications, where developer faults are more probably. Take the Opencart Malware Injection for example. Attackers circumvent security measures at application end to run their malicious […]
I don’t even know how I stopped up here, but
I thought this post was great. I don’t understand who you’re
but definitely you are going to a well-known blogger in the event you aren’t already.
Cheers!
I want to express my love for your kind-heartedness in support of folks who require assistance with this particular situation. Your special commitment to passing the message all over appeared to be
wonderfully practical and have continuously helped others like me to
achieve their targets. Your personal invaluable help signifies a
great deal to me and even more to my mates. With thanks; from each one of us.
Hi, It is very unfortunate that I found out that my website have been injected with the following malware. This happened when I suddenly noticed OC went into an error 503. After 7-8 hours of slow, crappy service from my provider they finally managed to bring it up but I couldn’t access any other subdomains I have. Suspicious I ran a scan and found out the above mentioned malware. Can I know if there is a way for me to clean it up? Are the backup still safe to run as I haven’t backed up my data for awhile? Thanks… Read more »
Yes there is a way to clean it up. Please assure you check all you payment API’s first of all, as we have seen a huge rise in malware directly aiming to steal your customer payments. Assure that there are no JS files which you do not identify with (we saw a case where a JS file was copying all the card information to hacker servers. Additionally, assure that PHP files have no extra hex encoded code or base64 encoded code appended within them.
If you need any assistance, feel free to reach us.
Hi there, all is going perfectly here and ofcours every one is sharing data, that’s actually
excellent, keep up writing.
Der Artikel ist wirklich gut. Das Thema hat mich schon lange interessiert und ich konnte hier noch einiges ergänzendes finden. Ich kann es kaum erwarten, weitere Neuigkeiten zu
lesen. Danke und Grüße aus Heidelberg Marco Feindler