Lately, Magento has been in news owing to frequent notorious attacks on it’s payment security system. A recent case of Magento attack witnessed credit card scrapers targeting the payment security system of Magento stores in order to steal paramount credit card information. Consequently, Magento has been wary of vulnerabilities in its system and in a prudent attempt, regularly releases security patches as preventive measures against any future attacks.
In its latest, Magento has released a security patch code-named “SUPEE 9652” in order to address a critical vulnerability in the Zend framework 1 and 2 e-mail component. The vulnerability is deemed as critical with a severity scoring of 9.8 which is quite high.
The SUPEE 9652 patch is available for the Enterprise Edition 1.9.00 – 1.14.3.1 and Community Edition 1.5.0.11 – 1.9.3.1. It primarily addresses the issue of remote code execution using mail vulnerability, whereby an attacker exploits a vulnerability to execute a piece of malicious code in the Magento system, thus overtaking user privileges.
How do I know if I am vulnerable?
Although the vulnerability has been deemed as critical, only few systems have been affected until now. This is because in order to be affected by the vulnerability, the installation needs to:
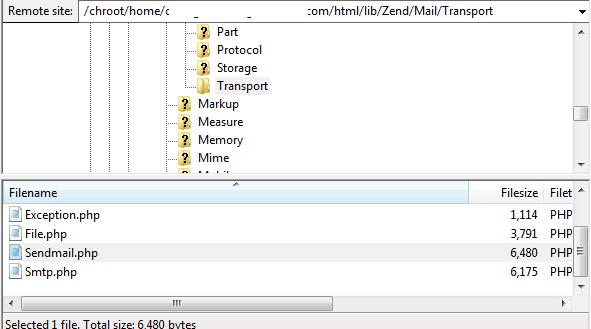
- Select and employ Sendmail as its mail transport option: If your server uses Sendmail as its mail transport agent, in that case the Magento site is prone to a remote code execution attack
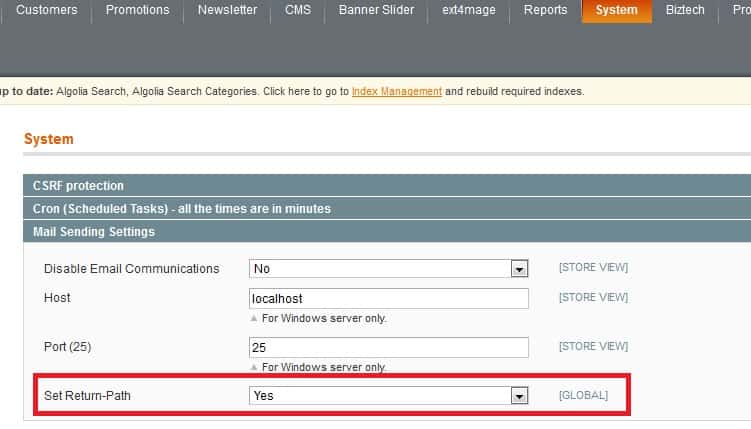
- Have non-default configuration settings: If ‘Set Return Path’ is set to a ‘Yes’, then your Magento store is highly vulnerable to an attack.
How can I protect myself?
The newly release Magento security patch SUPEE-9652 comes to the rescue. As soon as Magento releases a new patch, it’s highly recommended to install it as soon as possible. Moreover, it is advised to go over your mail sending settings too. Navigate to system settings used to control the “Reply to” address for emails sent from your Magento store:
- In case of Magento 1: Navigate from System-> Configuration-> Advanced-> System-> Mail Sending Settings-> Set Return-Path
- In case of Magento 2: Navigate from Stores-> Configuration-> Advanced-> System-> Mail Sending Settings-> Set Return-Path
In both of the above cases, switch the “Set Return-Path” setting to “No”.
To ensure your Magento store security, install all patches released by Magento as soon as they are released. A delay in enforcing preventive measures can give the attacker a chance to exploit the vulnerability as soon as he/she becomes aware of it. A periodic technical and security audit of your store can go a long way in securing your Magento store long time and update you with latest security patches.
















