WP maintenance plugin has been found to be vulnerable to CSRF and stored XSS. On November 15th, WordFence reported the vulnerability to WP maintenance plugin’s developers. Following which the plugin developers (Florent Malliefaud) urgently patched the vulnerability in just a day.
Version 5.0.6 is free of vulnerabilities. We recommend you update your plugin from any previous version to this.
About WP maintenance Plugin
As its name suggests, the WP maintenance plugin enables you to put your website on maintenance mode. It also enables you to customize your website maintenance page extensively.
This is how the WP maintenance plugin looks in the WordPress repository.
As you can see, there are as many as 30, 000+ active installations of this plugin. Its features include custom texts, logo, picture, CSS, etc on the maintenance page. You could even insert a countdown timer on your site maintenance page.
Vulnerability Details
According to WordFence, this vulnerability allows attackers to put your website in maintenance mode and inject malicious codes in your websites. Primarily the customization features are at a flaw in the plugin. The customization settings do not check nonce key of users before updating the settings. This could lead to a serious CSRF attack.
Also, there is a lack of proper code sanitation in the settings input field, which allows hackers to inject dangerous codes in your website.
More technicalities are in the next section.
Technical Details
WP maintenance facilitates a large number of customization features. It turns out excessive customization features needed better surveillance. WP maintenance lacked in this with limited nonce protection and Input/Output Sanitation on values. These overlooked areas resulted in Cross-Site Request Forgery (CSRF). The CSRF then led to Cross-Site Scripting (XSS) vulnerability in WP Maintenance.
Look at this code:
/* Update des paramètres */
if( isset($_POST['action']) && $_POST['action'] == 'update_general' ) {
if( isset($_POST["wp_maintenance_social_options"]['reset']) && $_POST["wp_maintenance_social_options"]['reset'] ==1 ) {
unset($_POST["wp_maintenance_social"]);
$_POST["wp_maintenance_social"] = '';
}
update_option('wp_maintenance_social', $_POST["wp_maintenance_social"]);
update_option('wp_maintenance_social_options', $_POST["wp_maintenance_social_options"]);
update_option('wp_maintenance_active', $_POST["wp_maintenance_active"]);
$options_saved = wpm_update_settings($_POST["wp_maintenance_settings"]);
$messageUpdate = 1;
}Here the update_general AJAX function does not verify the nonce token, leaving it vulnerable to CSRF. Also, the update_option() & wpm_update_settings() functions do not have input sanitization. This could allow an unauthorized user/attacker to inject malicious scripts as a stored XSS, which when called could cause redirection, crypto mining, data stealing, etc on your site.
By and large, all settings in the plugin were vulnerable to CSRF & XSS.
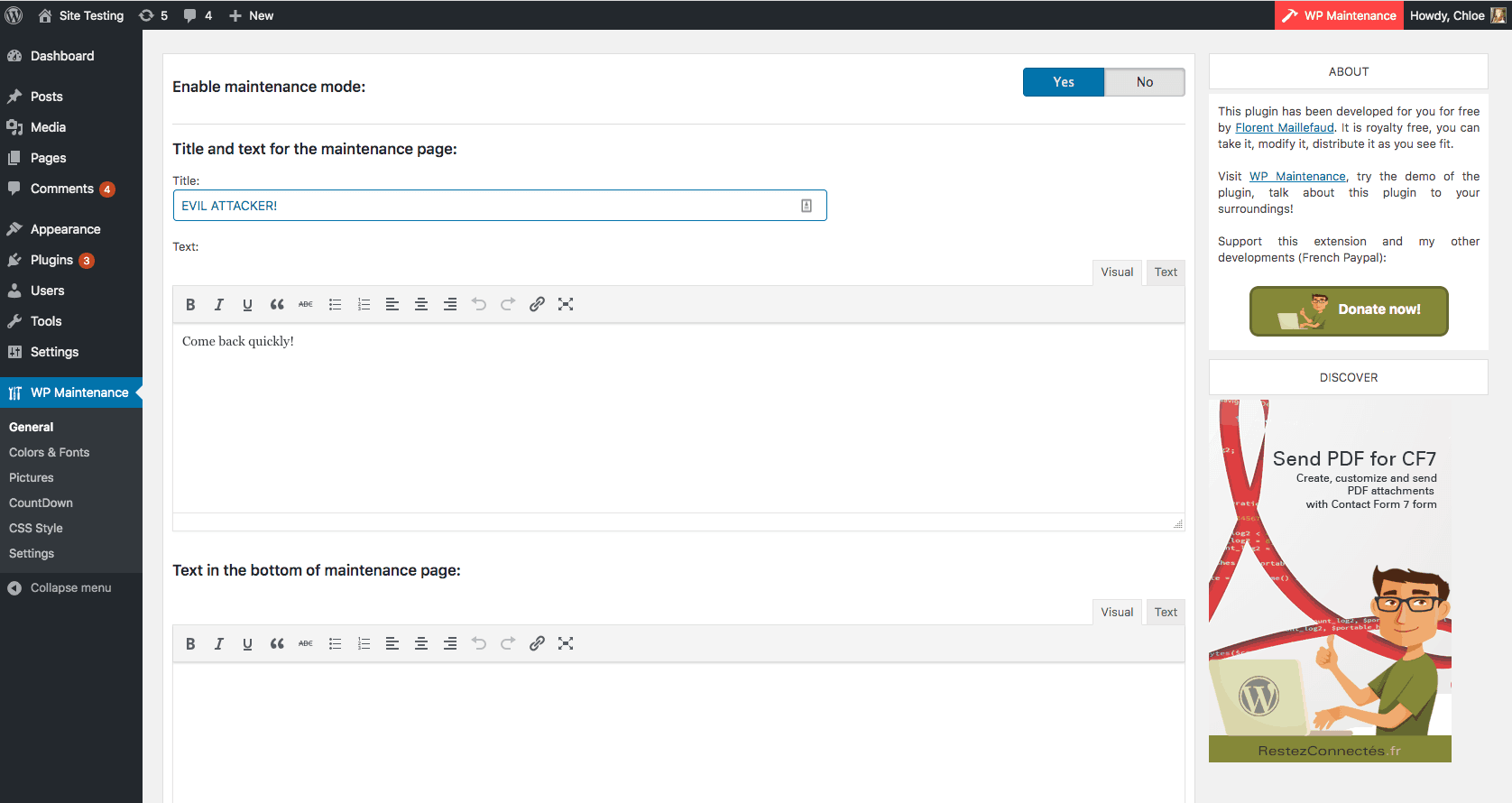
The General Settings window in WP maintenance has two input fields. The title and the text field.
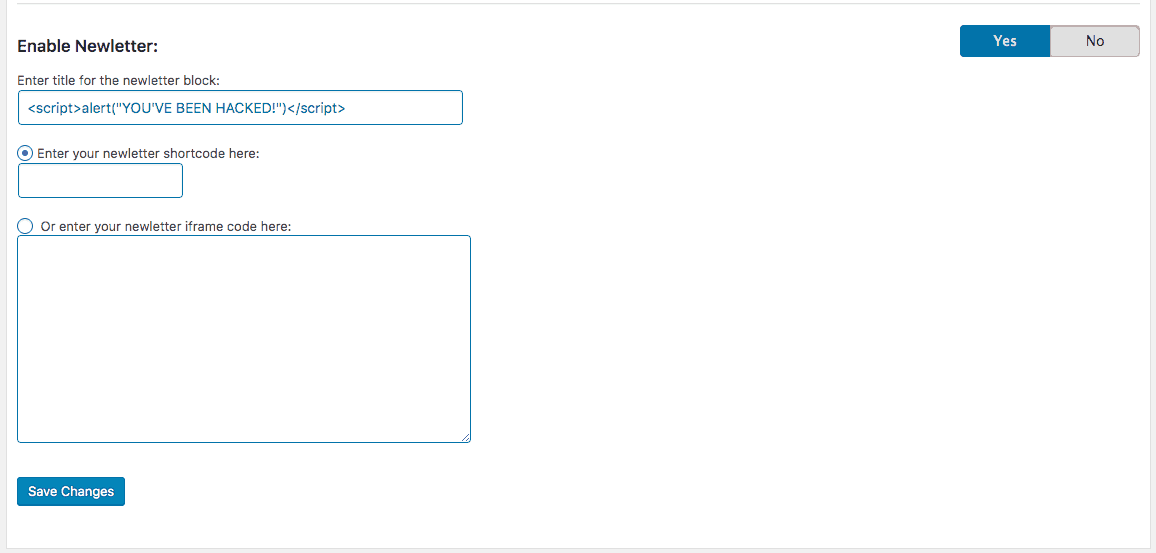
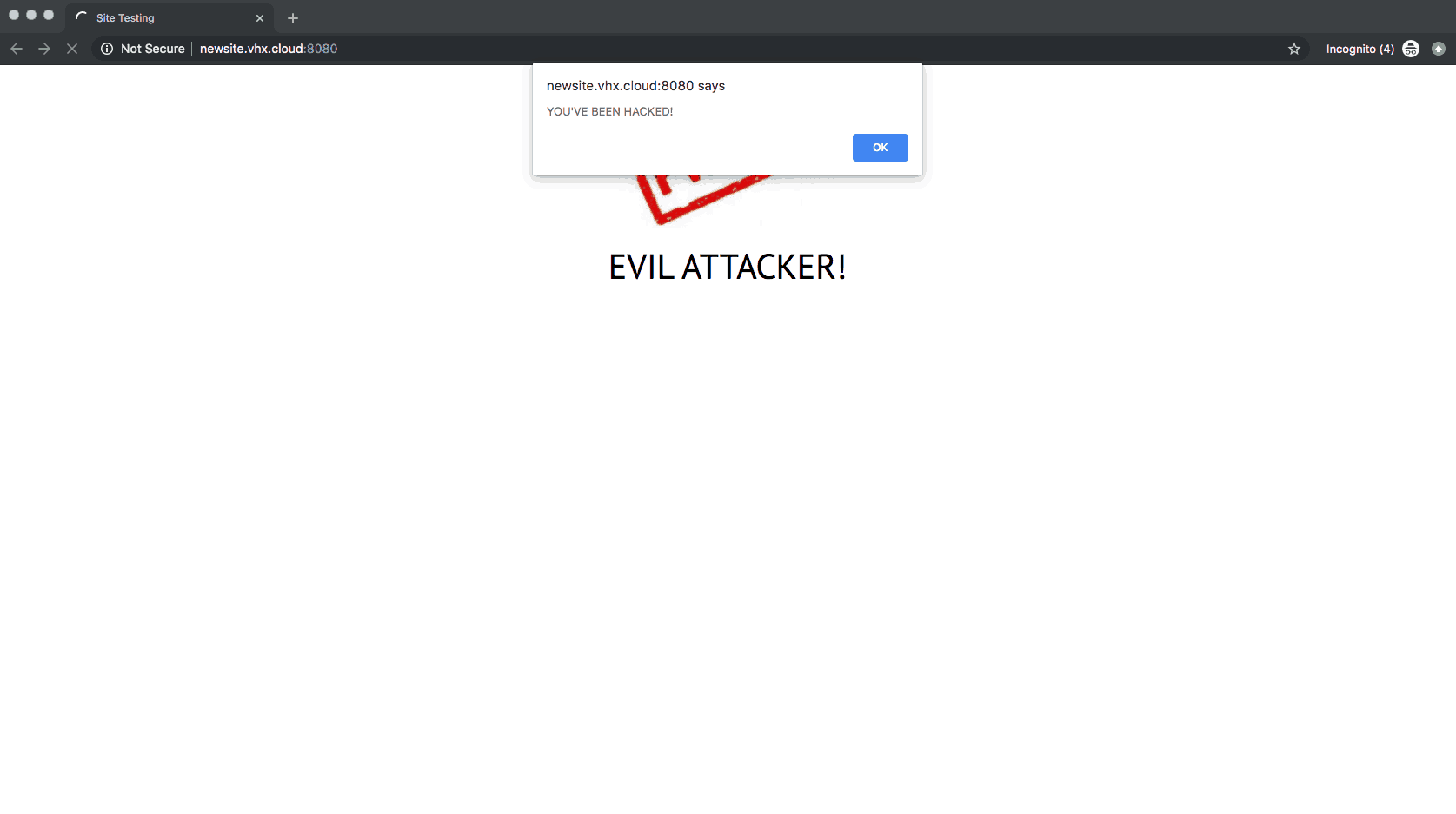
Due to flawed Validation and Sanitization, malicious codes skip parsing and gets stored as a stored XSS vulnerability. See the following example on the “Enable Newsletter” field of WP maintenance:
The codes pass sanitization and it gets executed.
Update to Mitigate Risk
Simply update the plugin to the latest version (5.0.6) to mitigate risks.
Also, improper security maintenance remains a serious issue in lots of WordPress plugins. The best way you can ensure the security of your website is becoming choosy. Where WP maintenance was quick in patching the vulnerabilities, not many plugins do that.
Download only the plugins that have an active support and development team. This you can know by checking plugin reviews or looking for them in forums.
Astra Security at Help
Having a secure plugin does help, but do you know what helps even better than relying on plugin’s security? Having your dedicated security system of your own.
Astra security is a complete security suite for your WordPress website. You can sit back and chill when Astra is taking care of your website’s security. It offers numerous features such as a web application firewall, malware scanner, malware cleanups, security audits and more for your website. You can check our reviews here.
Take the Astra demo and know for yourself.
Shoot your security questions in the comment box below, we’ll make sure to answer 🙂
Or you can also get in touch with security experts on the chat here.