Article Summary
Sites using PHP are widely targeted by hackers as one exploit can work across all of them. Often clever techniques are deployed to work maliciously behind the scenes. PHP web shell backdoor is one such malicious script or program designed to infect your website secretly.
These days, PHP is the main engine powering almost any popular CMS like Prestashop, WordPress, Magento, etc. This server-side scripting language is so popular that it powers almost 80 percent of websites on the internet today. However, sites using PHP are also widely targeted by hackers as one exploit can work across all of them. Often clever techniques are deployed to work maliciously behind the scenes. PHP web shell backdoor is one such malicious script or program designed to infect your website secretly.
We have somewhat more security reports than some other languages out there. A lot of these things are basically local exploits, in the sense that you have to be on the machine and you have to be able to write code in PHP.
According to Rasmus Lerdorf, the founder of PHP
What is a PHP web shell backdoor & Why would it infect me?
PHP web shell backdoors are basically malicious scripts and programs that are designed to perform a variety of malicious actions on your site. Simple web shells are command-based scripts. A PHP web shell allows attackers to manage the administration of your PHP server remotely. The attackers can access it using a URL on the internet. More complex web shells can also directly access the memory.
Often, these infections reoccur even after cleanup as they are designed for maintaining persistent access. Most of the backdoors use various obfuscation techniques to evade detection. Some even implement complex algorithms to hide directly in memory.
There are many ways a PHP web shell can reside on your website. However, a few common security issues which allow this infection:
- Weak or default Passwords.
- Unrestricted PHP file upload.
- Poor coding of the PHP site which allows invalidated input.
- Outdated PHP version.
- Improper PHP configurations.
- Weak file permissions of sensitive files.
- Improper error reporting and disclosure of code.
Related article – Resolving Security Issues in PHP
What can a PHP web shell backdoor do?
A generic PHP web shell backdoor allows attackers to run commands on your PHP server much like an administrator. At times, the attackers may also attempt to escalate privileges. Using this shell, the attackers can:
- Access any type of data on your server.
- May use your server to mine cryptocurrency.
- Can turn your server into a bot that obeys instructions from the attacker to chunk out large amounts of spam.
- And may more evil things!
Related article – The Ultimate PHP Security Practices and Malware Removal Guide
PHP Web Shell Backdoor: Code Analysis
A generic PHP web shell backdoor works through the following steps:
The first step is to initialize the system variables. While doing so, the web shell ensures that no errors are printed out to evade detection. This is done by creating an x_die function. Whenever there is an error, messages regarding the issue are passed through this function. This function then uses the die() function of PHP to exit the current script.

The next step is to check if the web shell can execute commands on the PHP server. For this, the generic PHP web shell checks various executing functions of PHP like the exec(), system(), etc.

Thereafter, the PHP web shell verifies the system configurations and checks if those can be altered by the web shell. In case the configuration functions are not present, it simply passes a ‘can not config‘ message to the x_die() function.

Thereafter, it also checks for safe mode on the PHP server. Safe mode of PHP is often deployed on shared servers. This is a feature which verifies that the process which has opened a particular file is run by a verified user. In case safe mode is enabled, the web shell stops further execution.
if(x_ini_get(‘safe_mode’)){x_die(‘can not exec: safe mode active’);}
Once all these conditions are satisfied, the web shell uses the Superfetch service of windows systems to run commands.

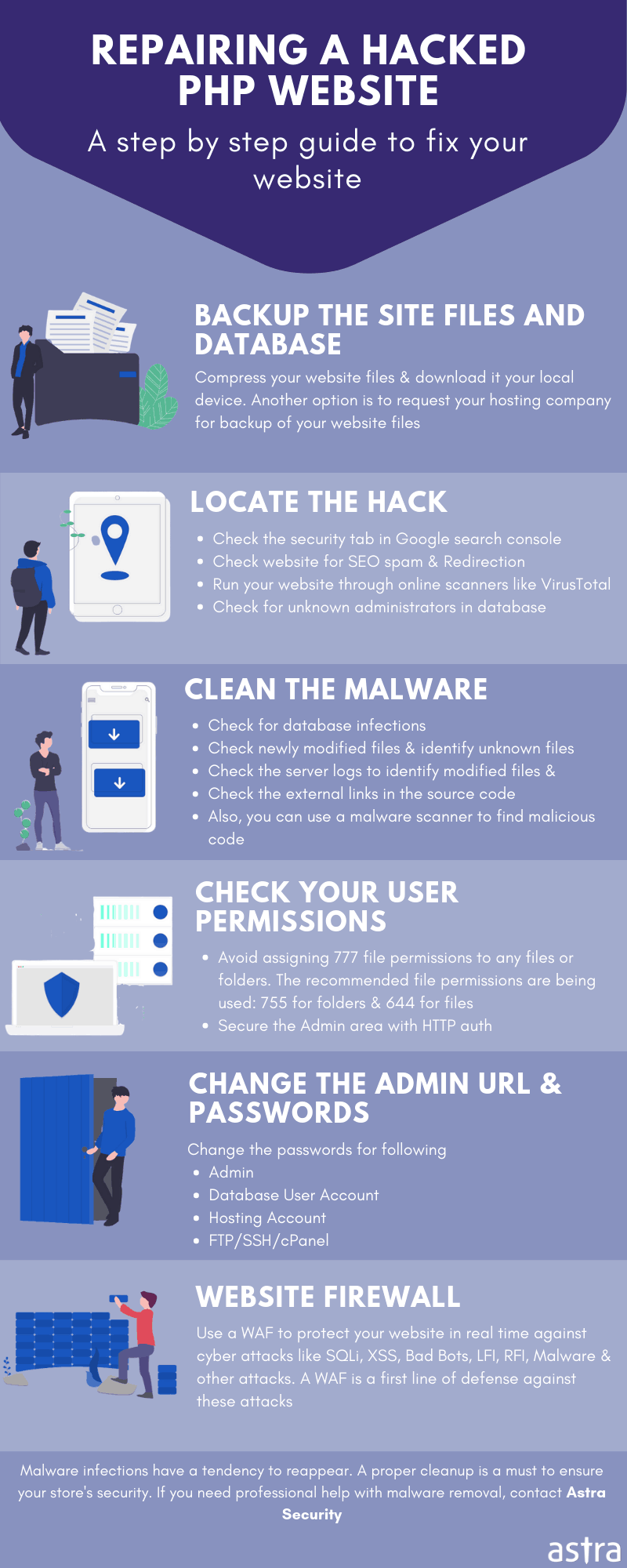
PHP Web Shell Backdoor: Detection and Cleanup
- Check if you have been infected with the generic PHP web shell backdoor by looking at the source code of all your PHP files.
- If searching manually is difficult then use the
Grepcommand. - Use the grep commands to search the dump of the web shell code inside your folders by this code:
grep -r "dump of web shell" /folderToSearch/ - Using this method, the generic web shell can be detected. However, this method has its own limitations as it can search only for one type of generic web shell.
- To search for other web shells you need to know the source code. To overcome this problem, you can use web shell detecting tools available for free on GitHub.
- Don’t forget to check logs for any suspicious HTTP requests to detect the PHP web shell. Delete the web shell once you have found it.
- In case the dump of a PHP web shell is found in any sensitive files, comment it out and contact the experts for further malware removal and analysis.
PHP Web Shell Backdoor: Mitigation
- Keep your PHP version up to date.
- Avoid using default or weak passwords.
- Always check for any site misconfigurations.
- Make sure file permissions are never set to 777 as it can allow anyone to edit your files!
- Make sure secure coding practices are followed while developing your PHP file.
- Go for a comprehensive penetration testing to discover vulnerabilities in your PHP site.
Conclusion
Deleting the web shell is not merely enough to secure your site. The attackers can still upload a new shell using the vulnerability on your site. For an average user, detecting this vulnerability may not be easy. So, it is recommended to use a security solution to automate this process.
Astra Security’s automated malware scanner detects a large number of PHP web shells and malware on a click. Further, Astra Security firewall monitors your website and blocks coming security threats. Choose a plan according to your needs and get started today!

















thanks best content