Joomla is the second most popular CMS after WordPress & is regularly targeted by hackers. The below graph shows that XSS is the most common vulnerability exploited by attackers in Joomla like WordPress. Other reasons of Joomla hacked are Code Injection, SQLi, etc.
This guide is useful for you if you are looking for a resource to remove malware from your hacked Joomla website. Follow the below links if you are looking for
A hacked Joomla website can be acutely troubling. But, before we begin with the Joomla hack removal process, let’s quickly go through the symptoms a hacked Joomla site shows.
Signs of a Hacked Joomla Website
- A google search shows ‘This site may be hacked‘ in the meta description.
- Cryptocurrency mining in the background.
- Website redirecting to spam
- Index page defaced or replaced by a Joomla hack.
- Logging you out of admin account.
- New admins appear.
- Page loading gets slow or bulky.
- Previously non-existent spam starts to appear on your site.
- The site gets blacklisted by Google for ‘malware‘ or ‘phishing‘.
- This spam also includes ads and unwanted redirects.
- Unnatural traffic hike on your site. You can check all this using the Google webmaster tools.
- CMS or other software may be broken. Especially firewall!
Get the ultimate Joomla security checklist with 300+ test parameters
Joomla Hack & Malware Removal Process
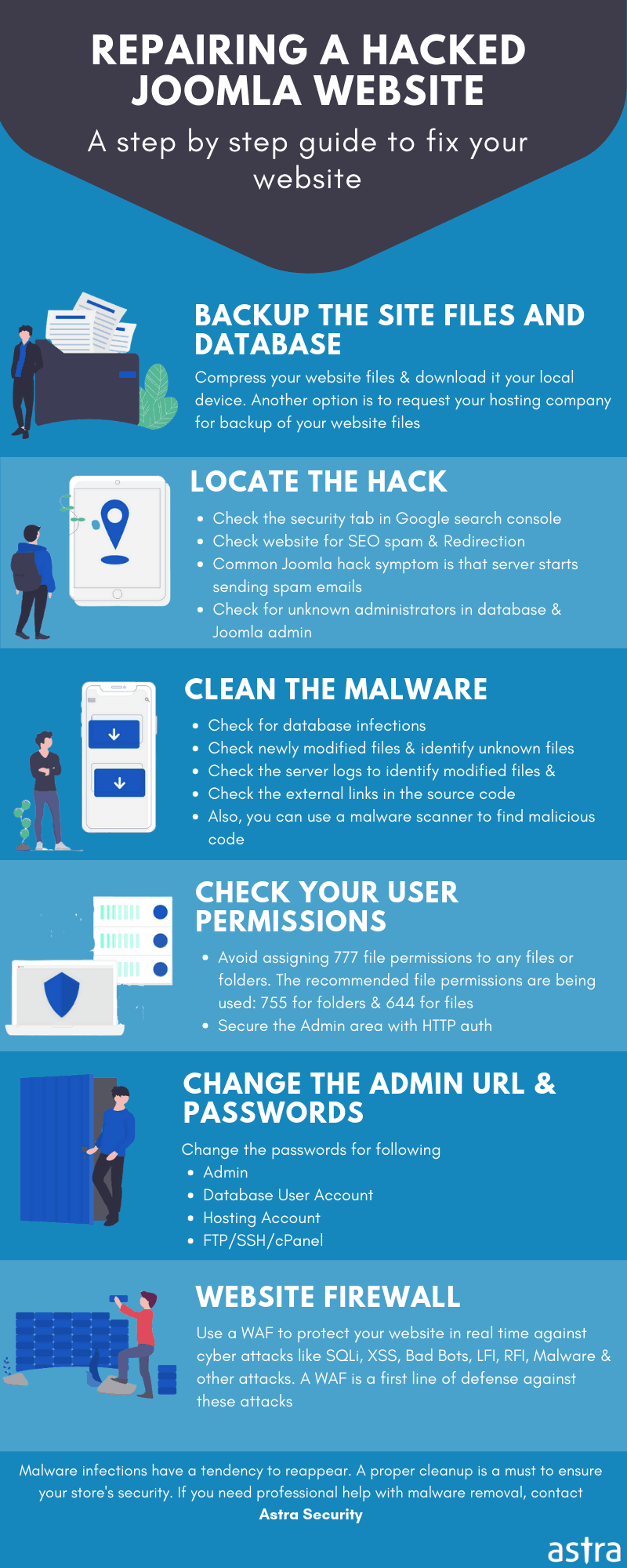
Certain common indicators like Blacklist warnings by Google and other search engines, abnormal browser behavior, modified files, and the presence of malicious new users in the Joomla dashboard exhibit a hacked Joomla website. Mentioned below is a guide to identify and clean your hacked Joomla site:
-
Identify hack
Scan your Joomla site to identify malware locations and malicious payloads. Astra’s integrated Joomla security ensures timely monitoring and identification of a hacked Joomla site.
Thereafter, check for any modified files including your core files. You can do so by manually check your files via SFTP.
Audit for malicious user accounts and administrators.
In case your Joomla site shows as blacklisted by Google or other website security authorities, you can check the security status of your Joomla! website by using their diagnostic tools. To check for Google transparency, visit the Safe Browsing Site Status website where you can view
- Site safety details which give information about malicious redirects, spam, and downloads.
- Testing Details which inform about the most recent Google scan which discovered the malware.
Make use of free security monitoring tools like Google Webmasters Central, Bing Webmaster Tools, and Norton SafeWeb to check security reports for your website.
Related Blog – Search Engine Blacklist
-
Fixing Joomla hack
On gaining information about potential malware location, compromised users and threat assessment, opt for a full website clean. Compare infected files with previous backups to assess the extent of modifications and remove malicious changes. Clean hacked Joomla database by using a database admin panel, such as PHPMyAdmin or tools like Search-Replace-DB or Adminer.
Next step would be to secure all user accounts. Often hackers leave multiple backdoors so as to again gain access even after a website has been cleaned. Backdoors are embedded in legitimate-looking files usually but located in the wrong directories. Therefore, it is imperative to thoroughly cleanse your files from backdoors else there is a threat of re-infection.
1. Database Cleanup
Firstly begin cleaning from that infected database. Joomla SQL injection can create new database users. To lookout for new users created after a specific date, use the following code:
Select * from users as uAND u.created > UNIX_TIMESTAMP(STR_TO_DATE('My_Date', '%M %d %Y '));Once rogue users are found. So, Delete them using the SQL statement
Drop User;.Not only this, to avoid future infections:- Sanitize the user input.
- Restrict database permissions to the account.
- Block Database error disclosure to locally only.
- Use type casting wherever possible.
2. Securing the Server
Even when the installation is secure, fault servers can cause a Joomla hack. Although there is a big list of Joomla security issues. Certain key points to remember are:
- Close any open ports.
- Remove the unused subdomains.
- Check regularly for configuration issues.
- If you are sharing a server go for subnetting. Or use a VPN.
- Block the error messages leaking info.
- Give strong and random passwords to FTP accounts and database!
- Make sure you use a firewall or some sort of security solution.
3. Setting Permissions
- Primarily, ensure that no user can upload executables like
.php.aspxetc. Only image files are to be uploaded on the server. - Now move on to set the file permissions for the server. Perhaps the most sensitive file is the .htaccess file. So, to set proper file permissions. Set your
.htaccesspermission to444 (r–r–r–)or maybe440 (r–r—–). - Also, ensure that your PHP files cannot be overwritten. Therefore you need to set
*.phpto444 (r–r–r–). - Most importantly use the popular file extensions. Joomla is a pretty big CMS so alternates are always there. Popular extensions get updates faster in case of vulnerability. So try most of the times to go with popular demand!
4. Check Modified Files in Joomla
Most of the time the hackers modify your files to inject spam. It can cause a real mess in yourinstallation. You might need a fresh installation. To avoid all this ensure you always keep abackup. While analyzing the files after a Joomla Hack, the diff command comes handy. Ithelps to check for modified files. All the Joomla files are available publically on Github.This can be used for comparison. To check core file integrity with SSH commands:$ mkdir joomla$ cd joomlaFirstly, we created a directory named
joomlaand switched over to that.$ wget https://github.com/joomla/joomla-cms/releases/download/3.6.4/Joomla_3.6.4-Stable-Full_Package.tar.gz$ tar -zxvf Joomla_3.6.4-Stable-Full_Package.tar.gzThe
wgetcommand downloaded Joomla files from GitHub. The second line of codethen extracts them.
$ diff -r joomla-3.6.4 ./public_htmlFinally, the diff command here is comparing the contents. This time we are looking
at the
public_htmlfile. Similarly, you can check multiple files. Moreover, the filescan be manually checked. Just log in using any FTP client and check files. SSH
enables you to list file modifications.
$ find ./ -type f -mtime -15
Here this SSH command reveals the files modified in last 15 days. Similarly, youcan change the time stamp. Look out for any recently modified files!
5. Check User Logs
System logs are the best tool to identify the cause of a Joomla hack. System logs recordall the previous activities that took place. So whenever an XSS or SQL injection takes place,
there is always a record of the request. Furthermore, hackers tend to create new admin accounts. If you wish to check for any suspicious users, then:
- Firstly Login your Joomla Dashboard.
- Now, click on Users and select Manage.
- Here check for suspicious users. Especially those recently registered.
- Now proceed to Remove any unknown users.
- Also, check the Last Visit Date.
- Find out where the server logs are stored. Use it to identify Joomla SQL injection etc.
- If you see users logging from unknown IPs, remove them.
Moreover, use google diagnostic report to find the cause. It gives you a comprehensive view
of your site. If your site is blacklisted work closer with Google. The diagnostic report will give
you the cause for blacklisting. Use it to find and weed out the infection!
What to do post Joomla hack removal?
Update
Most of the time a Joomla hack takes place due to unpatched files. Hence, the first step to follow post cleaning the hack is a Joomla update. Updates essentially remove vulnerable extensions and fill in security holes thus providing you with a secure environment.
Currently, the Joomla version 3.x is the most stable major version. Those using 1.x and 2.x branches should immediately switch to 3.x.
Other than major version update, also update all Joomla core files, components, templates, modules, and plugins.
Reinstall
Post-hack, it is also advised to reinstall all extensions to ensure they are functional and malware residual free. Further, remove defunct/deactivated themes, components, modules, or plugins from your web server. Sometimes, we forget to delete the files related to these abandoned modules & plugins, this may still leave loopholes. Thus, make sure to get rid of the files too as they may contain serious vulnerabilities
After cleaning your hacked Joomla site, make a backup. Having a good backup strategy is at the core of the best security practices. Store your backups in an off-site location, as storing them on a server can also lead to a hack.
Lastly, it is advised to scan your system with a good antivirus. There is a possibility of system compromise if a user with an infected computer has access to your website. Protect your site using a website firewall which basically shields your site from any malicious users or malware threats from the web. Astra’s Web Application Firewall mitigates against any online threats and keeps malware at bay.
Reset
Reset all passwords to avoid reinfections. Ensure that you’ve set up two-factor authentication on user accounts. Also, practice the least privilege and give limited access to people who need to do a particular job.
Joomla Post hack security tips
Implementing the following security practices will protect your Joomla site from the majority of attacks:
-
Regularly update Joomla Version, Extension & Plugins:
A secure Joomla site is one which is updated regularly. Every version update is released with security enhancements and bug fixes. An outdated version of Joomla or any other outdated extensions/plugins can sneak in hackers.
-
Use Strong Passwords:
Weak credentials can be ultimately leaked through Brute Force and act as common security holes, thus leading to compromised security. Easily guessed passwords and default admin accounts make it easier for perpetrators to gain illegal access to your Joomla website, thus exposing it a host of malicious activities. A long length password with multiple characters makes it for a secure passcode than a shorter one.
-
Periodic backups:
Regularly backing up the archives of your files and databases saves your back in case anything goes wrong. Some extensions like the Easy Joomla Backup provide automatic scheduled backups which can later be restored in case of data loss resulting from a hack.
-
Restrict access to Admin Page:
Perpetrators often resort to brute force attacks on easily guessed admin login pages. Thus it is imperative to restrict access to your administrator area. It is advised to not use a default admin login page URL, rather replace it with a specific name. Moreover, the admin panel must be password protected. Extensions like Admin tools, RSFirewall, etc allow a Joomla site owner to change their login page URL
-
Security Extensions:
Using security extensions go a long way in securing your Joomla site. These extensions, when configured with your site properly, allow you to block any kind of malicious activity and cover-up security holes. extensions allow you to block hacker attacks and close security holes of your Joomla site.
-
Using Two-factor Authentication:
A two-factor authentication code (commonly known as the One time password: OPT) makes your Joomla site even more secure. Even if your password is guessed or leaked, one still has to go through an authentication code to gain illegal access of your account.
-
Be wary of corrupted downloads:
Never download premium extensions, plugins or any items for free from unauthenticated or unofficial sources. Plugins from an unknown source may be corrupted or contain malware, which may harm your site. Do not consider saving money here, rather spend on authentic sources.
-
SSL Certification:
Whenever a user logs into a site, his/her credentials are sent to a server sans encryption. By using an SSL certificate, these credentials will be encrypted before sending to the server. In this way, an SSL certification provides an additional layer of protection to your Joomla website.
-
Disable FTP Layer:
FTP layer is generally not needed in Joomla and it is disabled by default. It is necessary to keep it so, as an enabled FTP layer is a major security hole in Joomla sites.
-
Proper File and Directory Permissions:
Always manage permissions to files and directories, and never give full access of permission 777. Never give full access or permission 777, but rather use 755 for folders, 644 for files and 444 for configuration.php files


















[…] vulnerabilities have been exposed in Joomla this year. If left unpatched it makes multiple Joomla installations […]
[…] However, being popular also makes it a target for spammers and hackers. Often users complain about Joomla hacked sending spam on the community forums. These attacks are fairly common due to the sheer bulk of […]
[…] this CMS is user-friendly. Joomla is also popular due to the wide variety of extensions it offers. Multiple vulnerabilities have been uncovered in Joomla this year. These ranges from Joomla XSS, File intrusion to Joomla […]