Drupal is considered to be really secure and this was the reason for its popularity. Drupal is an open-source CMS and is known to be robust. Being open-source, its source code is publicly visible. This is a goldmine for bug bounty hunters. Drupal suffered from the infamous “Pharma Hack” to “Kitty Cryptomining Malware” in the recent few months. Another infection on a rise is the “Drupal hack redirect” that redirects visitors of your website to spammy web pages.
In fact, such long is the list of vulnerabilities recently that Greg Knaddison, a Drupal security team member after the CVE-2018-7600 went on to say that “The only effective mitigation we are advising is to upgrade or second best is to put a rule into a WAF,”.
The Drupal redirect hack occurs after an attacker exploits the vulnerability in your website and modifies the site content to install malware. As a result, visitors to your website are redirected to spammy and questionable links. Website owners have complained that this malware redirects users to phishing and adult pages selling viagra or porn.
How does Drupal Hack Redirect Problem Look?
There are multiple types of this redirection infection:
- Website visitors are redirected to spammy pages on visiting your homepage
- Whenever a button/link is clicked, the page redirects to Fake Pharmacy pages selling Viagra, Cialis
To see if your Drupal site is infected with the second variant, you can use a Google dork. The following Google dork gives us an intro about what we are going to dive into.
site:your-website.com "viagra"
Here, this dork shows all the Drupal websites redirecting to viagra pages. However, you can search for more redirections by replacing the word viagra with other keywords like: ‘poker‘, ‘porn‘, ‘loans’ etc.
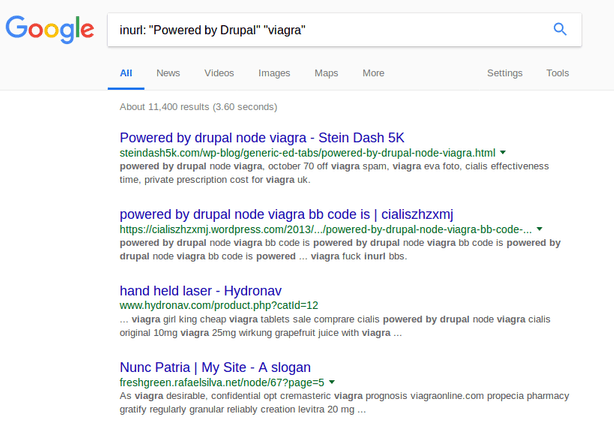
After clicking on the first website link produced the following errors.
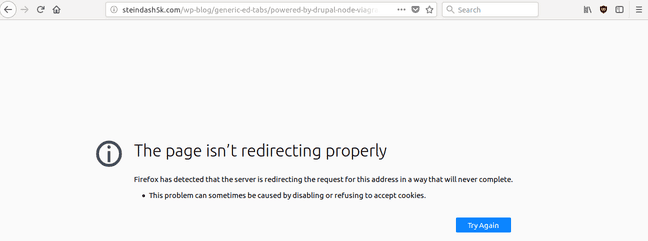
This means the attacker had exploited the website and it was redirecting. However, due to other factors, the redirect may not be working now.
Get the ultimate Drupal security checklist with 300+ test parameters
Types of Drupal Hack Redirect (HTTP Status Code) :
- 301 Redirect: This can also be called, a permanent redirect. When Google or any other search engine for that matter look at this URL. It will state that the URL has shifted to a new location so update all previous relations. Attackers are most likely to use this redirect because of the simplicity.
- 302 Redirect: The use of 302 is redundant now as it has been replaced by 303. A 303 redirect basically says that a document is temporarily available.
- 303 Redirect: It is a refined version of 302. A 303 redirect supplies a temporary page that might not exist on the same address in the future. It could be a credit card data form, temporary details generator, etc. This is least expected from the attacker unless it is a really sophisticated attack.
- 307 Redirect: It is a variant of the 303 redirect with a few differences. Further, there is a 308 redirect which is an experimental redirect. Highly unlikely to be used but the possibility can’t be ruled out.
Signs of a Drupal Malware Redirect:
- Abnormally high website traffic
- Unknown files added to your Drupal site
- New users with Admin rights created
- Clicking links on your website homepage redirect to spam
- Malicious ads or porn pop up on your website
- New previously unknown nodes, files, etc may appear
- Search engines might show spam content
- Security warnings or blacklisting by search engines like Google, Bing, etc.
Causes of Drupal Hack Redirect Problem:
The cause of Drupal hack redirect can be very diverse and cannot be summed up in one article. However, we can briefly look at the prime causes:
DNS Redirect
A DNS redirect happens when someone modifies the entries of your DNS Server. So when someone asks for your website, the DNS servers send the user to that entry. As a heuristic test, you can do a DNS lookup. Windows has default tool traceroute. It can be accessed with the command line tracert www.your-site.com Similarly, Linux users can use host www.your-site.com. If a DNS lookup returns the wrong IP address, then your problem is in DNS, not on your website. More advanced users can check for rogue DNS server entries.
Tampering files
The attacker could have tampered with the .htaccess and index.php files. Probably wanna look out for malicious code inside them. The code can be of the following format:
data:text/html,<html><meta http-equiv="refresh" content="0; url=http://malicious_site.com/process/route/1673246826.html?refresh=non-ie&bl=0"></html>
Here, this piece of code is redirecting the website to domain http://malicious_site.com.
Core Integrity
A thorough manual checkup of all such files is needed. You can’t possibly check inside all the websites manually. So the first step in this direction is checking for the core integrity value of installed files. Begin with:
mkdir drupal-8.3.5
cd drupal-8.3.5
wget https://github.com/drupal/core/archive/8.3.5.tar.gz
tar-zxvf core-8.3.5.tar.gz
This piece of code here creates a directory named Drupal-8.3.5 and then changes to that directory. Its third line then downloads original installation files from Github repository and the fourth extracts them. Now comes the crucial part of comparing them. diff -r core-8.3.5 ./public_html this command here would give us the changes in our files v/s the original installation. Go on in this format to check all the files.
Other Causes
- The first public discussion of SQL injection was written way back in 1998. There is a reason why it haunts websites till the day. The occurrence of an SQL injection is the result of unsanitized input. Skipping just a semi-colon in coding can lead to SQL injection vulnerability.
- Probably wanna lookout for fishy modules names like
modules/system/wxeboa.php. These are not a part of the original installation. - Google transparency report can be of great help while hunting for causes of Drupal hack redirect. It can tell you a lot about your website.
- Weak FTP or website passwords could be a cause of a Drupal hack redirect. If you are using default configurations change now!
Damage Control for Drupal Hack Redirect Issue:
Based on Referrer that Contains the Keywords
The thumb rule of cybersecurity is that you can never eliminate the possibility of attack, you can only delay it. In this direction, another clever trick is to edit the .htaccess file. The file can be so edited that even if infection occurs in the future, your website blocks users from accessing the spam. This will promote trust among users. So despite the infection, the search engines won’t’ blacklist you as you would be automatically blocking the spam. This would buy you some time and save your search rankings from plunging. Thus, it works as damage control.
<Limit GET>
order allow, deny
allow from all
deny from env = spammer
SetEnvIfNoCase Referer ". * (Poker | credit | money). *" Spammer
</ Limit>
This piece code block users from accessing the pages with links like poker, credit etc based on identifiers(HTTP referrers). As our website contains none of these, we can do away with blocking such words. This acts as a filter with wildcards.
Based on Its own Identifiers
The second method is blocking access based on its own identifier (HTTP REFERRERS)
Rewrite Engine On
RewriteBase /
# allow referrals from search engines:
RewriteCond% {HTTP_REFERER}!. * xyz \ .com /.*$ [NC]
RewriteCond% {HTTP_REFERER}! ^ Http: // ([^ /] +) google \ .. * $ [NC]
Continue replacing the phrase google with all the search engines like yahoo, bing etc. you wanna allow.
# Conditions for don`t wanted referrals
RewriteCond% {HTTP_REFERER} ^. * Loans. * $ [OR]
Continue replacing the word loan with the spam words like viagra, porn etc you wanna block. However, it is noteworthy here that Apache’s ModRewrite must be turned on for this to work. Moreover, you can also restrict certain IPs known publically for spamming.
Cleaning website infected with Drupal malware redirect.
Database Cleanup:
Checking users
First of all, we shall begin with probing for SQL injection. Look out for any fishy tables like Sqlmap. This table named Sqlmap is a result of junk query while using the automated pen test tool Sqlmap against a website. To show all tables simply use the command. show tables ;. The attacker might have also created new user entries and gained admin privileges. To check that use:
Select * from users as u
AND u.created > UNIX_TIMESTAMP(STR_TO_DATE('Oct 15 2018', '%M %d %Y '));
Here, it will display all the users created after 15 October 2018. You can tweak this line to date of your choice. In case you detect a rogue user or table, you can delete it using drop database database-name.dbo;.
Blocking users
Furthermore, you can block users or change passwords for every user. Use the following command:
update users set pass = concat('ZZZ', sha(concat(pass, md5(rand()))));
This SQL statement changes the user password in MD5 format. The MD5 format is a cryptographic security function. Never store your passwords in plain text format. It is quite easy for the attacker to extract plain text password from the compromised database. An MD5 value still gives an extra layer of security. As the word admin would result in the hash 86fb269d190d2c85f6e0468ceca42a20. Being a one-way function it is difficult to compute backward.
Files Cleanup:
- Rollback installation to a backup copy of the files.
- External modules can be used to scan for infection. The hacked module is one such popular product.
- Disallow access to sensitive files outside and root directory.
- Disable error reporting to plug in the leak of sensitive information.
- If your installation is outdated Update! Update! Update!
- Reset all the previously used API keys and FTP passwords. Make sure you use a strong password.
- Clear your cache using the following command:
drush cache-rebuild(Drupal 8) ordrush cache-clear all(Drupal 7). - Use some sort of WAF solution as a layer of extra security against Drupal redirect hack.
However, there is still lots that can go wrong and result in Drupal hack redirect. If you are still unable to figure out, contact experts. If cleaning manually seems too tiresome, so use automatic tools. Stay updated regularly from blogs, websites, etc about the vulnerabilities discovered in your CMS.

















[…] for Drupal, it is a popular and growing site, and thus a desired target for the web crawlers. Drupal redirect hack is another convenient yet unscrupulous way for the hackers to use this progressive site as a door […]